Achieved 100% detection in 2023
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
A cybersecurity playbook is a detailed framework that outlines organization-specific procedures for handling computer security events and incidents. It includes predefined courses of action that provide guidance on detecting, analyzing, and responding to potential cybersecurity threats.
By standardizing response strategies, a playbook ensures a coherent and coordinated response during a security breach, reducing reaction times and minimizing damage.
Cybersecurity playbooks are tailored to the needs and risks of the organization, incorporating industry standards and best practices. They are regularly updated in response to new threats and organizational changes, helping IT security teams manage cybersecurity risks.
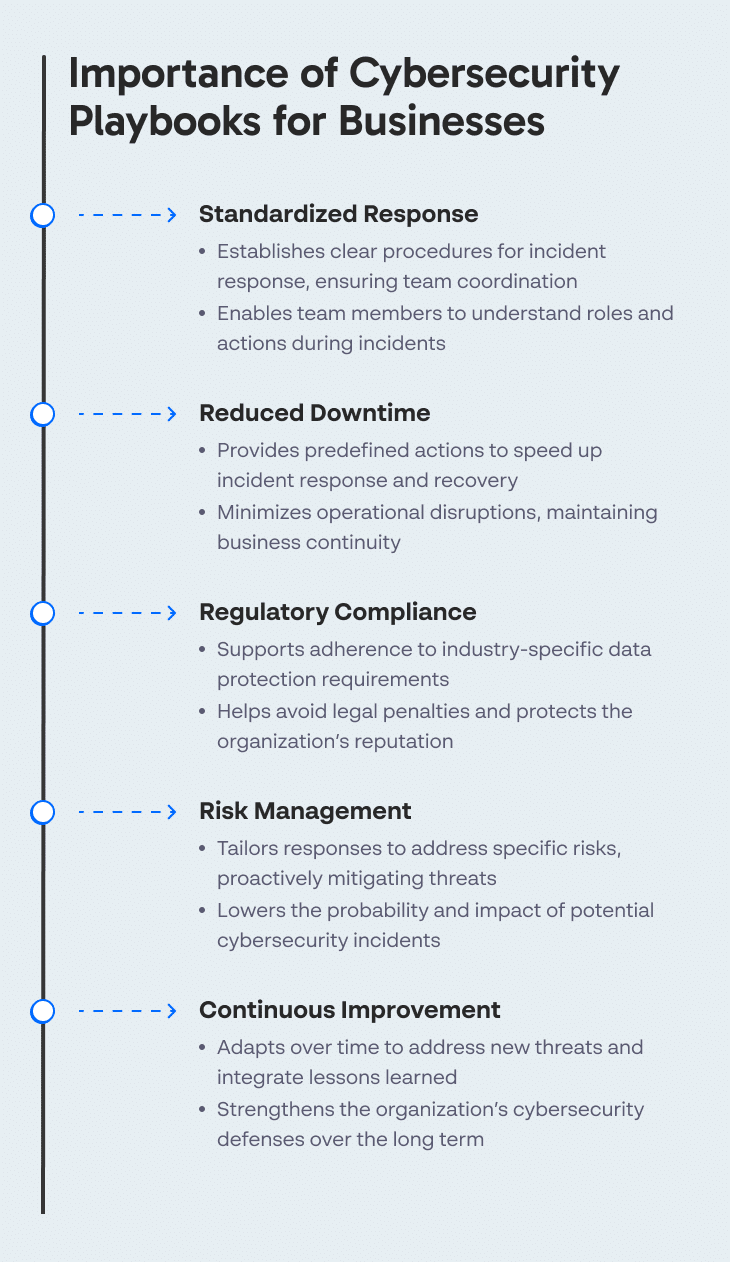
Given the reliance on digital systems for business operations, many organizations face an increasing number of cyberthreats. A cybersecurity playbook helps provide several capabilities to address these threats:
Manual cybersecurity playbooks rely on human intervention for detecting, analyzing, and responding to incidents. They typically consist of documented procedures and guidelines that incident response teams follow during a cybersecurity event. While manual playbooks can be tailored to specific scenarios and allow for expert judgment, they often result in slower response times and are prone to human error. Manual processes also require significant time and resources for training and coordination.
Automated cybersecurity playbooks use software tools and technologies to execute predefined response actions automatically. These playbooks integrate with various security systems, such as intrusion detection systems (IDS), security information and event management (SIEM) solutions, and endpoint detection and response (EDR) tools, to enable real-time threat detection and response. Automation can significantly reduce response times, improve accuracy, and ensure consistent execution of procedures.
Automated playbooks have several important benefits over manual playbooks:
A cybersecurity playbook can include different combinations of techniques and procedures. Here are some of the main processes that are typically included in a playbook.
Threat detection involves the identification of malicious activity aimed at obtaining unauthorized access to information systems. Automated systems, such as intrusion detection systems (IDS) and security information and event management (SIEM) solutions, aid in continuously monitoring and analyzing data traffic for signs of anomalies.
Early detection of threats helps in minimizing potential damages. Playbooks specify workflows for rapid escalations, ensuring that detected threats are quickly communicated to the relevant personnel for immediate investigation and response.
Incident classification categorizes detected threats based on their nature and severity. This determines the urgency and type of response needed. Common classifications might include malware attacks, data breaches, or phishing attempts, each requiring different resources and response strategies.
The classification process helps in prioritizing incidents, ensuring that resources are allocated efficiently, and that high-impact threats are addressed with the urgency they require. This systematic segregation helps in creating targeted responses that can reduce the impact of the incident on organizational operations.
The response section in a cybersecurity playbook outlines the actions to be taken after incident identification and classification. It guides incident response teams on containment methods to prevent further spread, eradication of threats, and recovery of the system to regular operations.
Playbooks ensure that every action taken is in line with legal requirements and best practices for cybersecurity, maintaining data integrity and system resilience. This orchestration is important for minimizing downtime and the economic impact of incidents.
Communication guidelines specify how information about incidents should be communicated within an organization and to external stakeholders. This includes who must be notified, the information that should be shared, and the timeline for communications to maintain transparency and trust. In an automated playbook, communication can occur via alerts, automated emails, or integration with communication tools like Slack.
Effective communication is critical in managing the propagation of the incident while mitigating any adverse public relations or legal issues. Internal communications are focused on coordinating response efforts, while external communications might involve notifications to affected customers or regulatory bodies in compliance with data breach laws.
Post-incident analysis involves reviewing how an incident was handled and identifying improvements for future responses. This stage helps adjust the playbook and improve the organizational security posture over time. Teams assess what was done correctly, what mistakes were made, and how procedures can be tweaked for better future response.
Through lessons learned, organizations can implement stronger measures, improving detection and responses to attacks. This cycle of continuous reassessment and refinement helps in building resilience against future cybersecurity threats.
Tips From the Expert
In my experience, here are tips that can help you optimize the creation and implementation of cybersecurity playbooks:
The following process illustrates how to build a manual cybersecurity playbook. When using tools to automate playbooks, these tools will typically provide an existing library of playbooks and provide a user experience (UX) to define new playbooks.
The first step is to clearly define the purpose and scope of the playbook, ensuring that it is focused and relevant to the organizations needs and challenges. This involves:
A thorough risk assessment aids in understanding the specific threats and vulnerabilities facing the organization. This step involves:
Learn more in our detailed guide to cyber security assessment (coming soon)
Establishing detailed policies and procedures is essential for ensuring a consistent and effective response to incidents. This step includes:
Learn more in our detailed guide to cyber security policy (coming soon)
Clear definition of roles and responsibilities is crucial for an effective incident response. This involves:
A detailed incident response plan is a central component of the playbook. This plan should include:
Regular training and education help ensure that all employees understand the playbook and their role in it. This involves:
Continuous improvement helps keep the playbook relevant and effective. This involves:
Cynet provides a holistic solution for cybersecurity, including the Security Orchestration, Automation & Response (SOAR) which can automate your incident response policy. Users can define automated playbooks, with pre-set or custom remediation actions for multiple attack scenarios. Cynet automated playbooks also help detect threats to ensure that you only implement a manual response when it is necessary.
Cynet SOAR can address any threat that involves infected endpoints, malicious processes or files, attacker-controlled network traffic, or compromised user accounts.
Search results for: