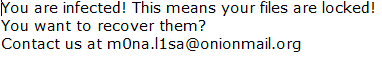Monthly Ransomware Activity
Written by: Maor Huli
In February, we introduce the following types of ransomware:
- Crysis
- LockDown
- MonaLisa
- Phobos
EXECUTIVE SUMMARY
Bleeping computer is the most up-to-date website that summarizes the newest ransomware variants. Orion team is an integral department of Cynet’s research team. We in Orion’s team are working around the clock, tracking threat intelligence resources, analyzing payloads, automated labs to ensure that our customers are most protected against the newest ransomware variants.
In this article, we have summarized ransomware variants from February based on bleepingcomputer.
We will present the recent ransomware and how Cynet 360 platform detects and prevents it via several mechanisms.
CYNET 360 VS RANSOMWARE
- Observed since: Early 2016
- Ransomware encryption method: AES.
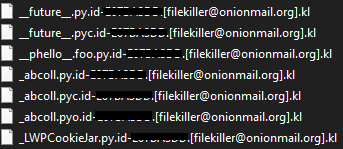
- Ransomware extension: .id-[0-9A-Z].[[email protected]].kl
- Ransomware note: info.txt | .hta
- Sample hash: 8f2bb3a4089e637c0cf28611bda511dd00b783307d1b61f9ccdd45aa8e902fa4
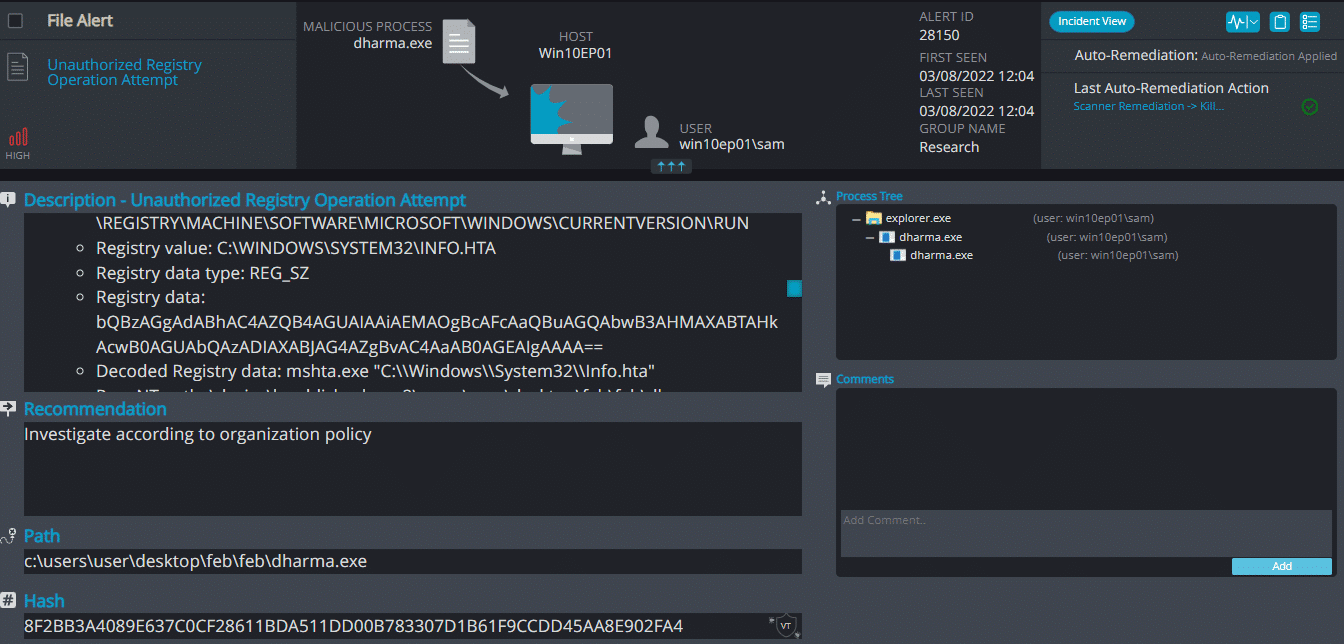
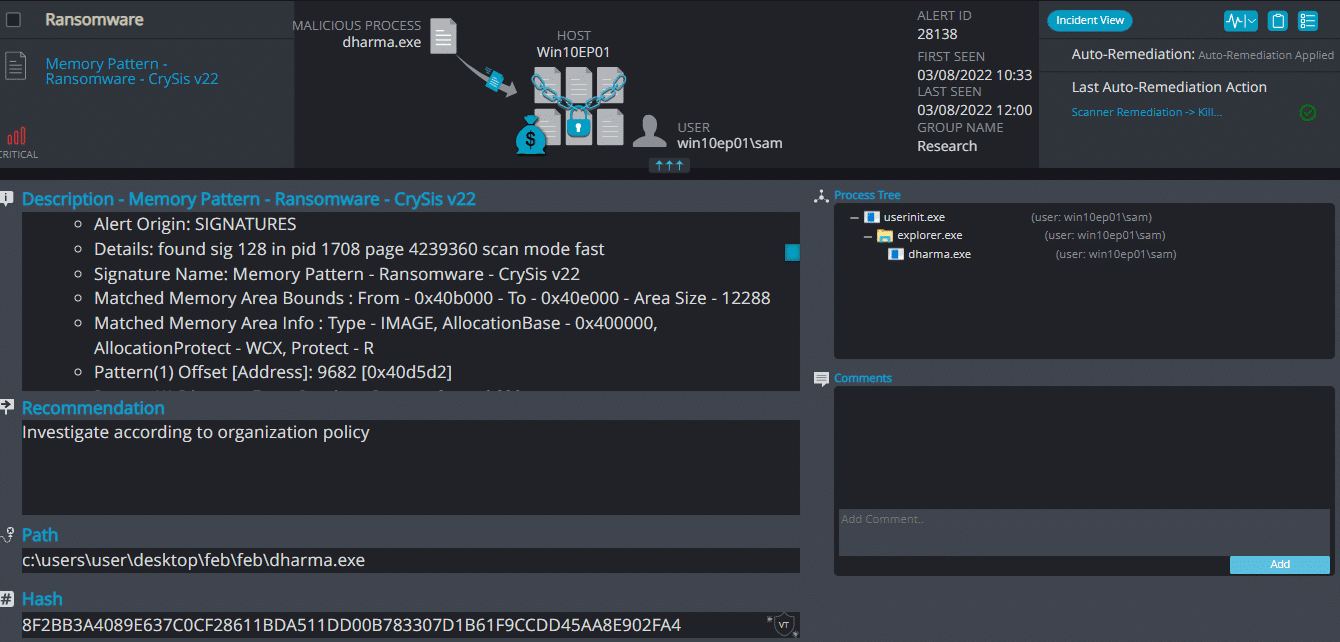
Cynet 360 Detections:
Crysis ransomware renames the encrypted files with .kl in the extension:
Once a computer’s files have been encrypted and renamed, it drops a note as info.txt.
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains the ID of the host and the amount of the files that were encrypted
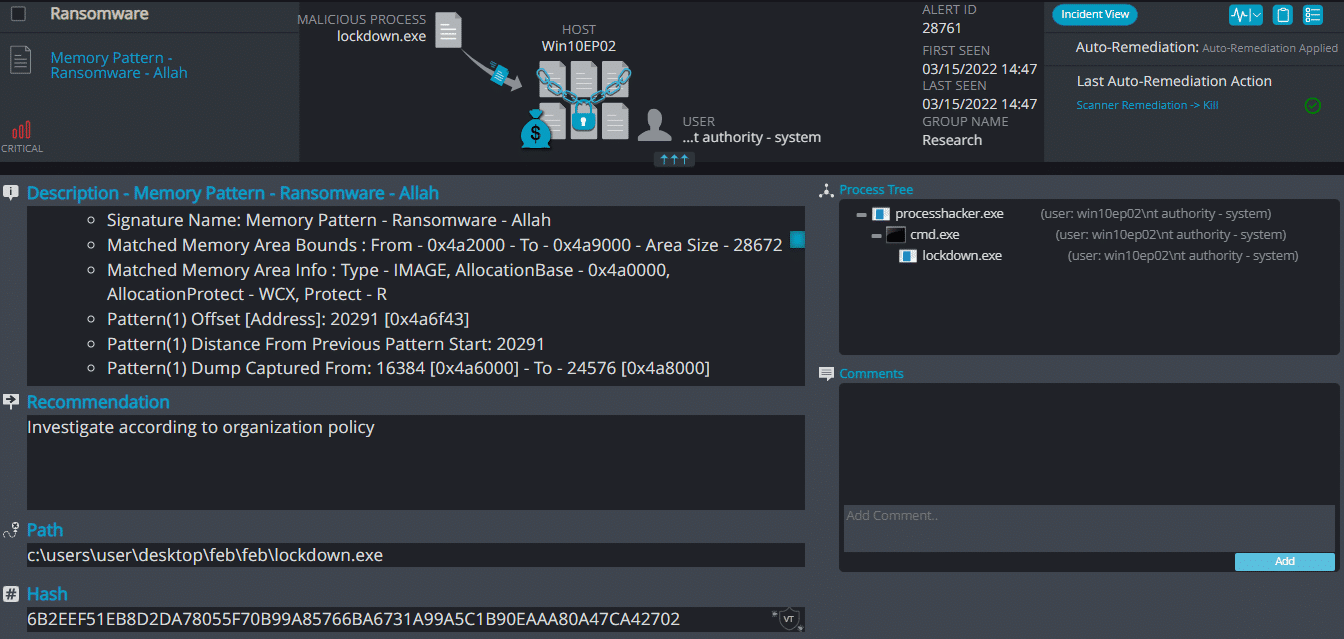
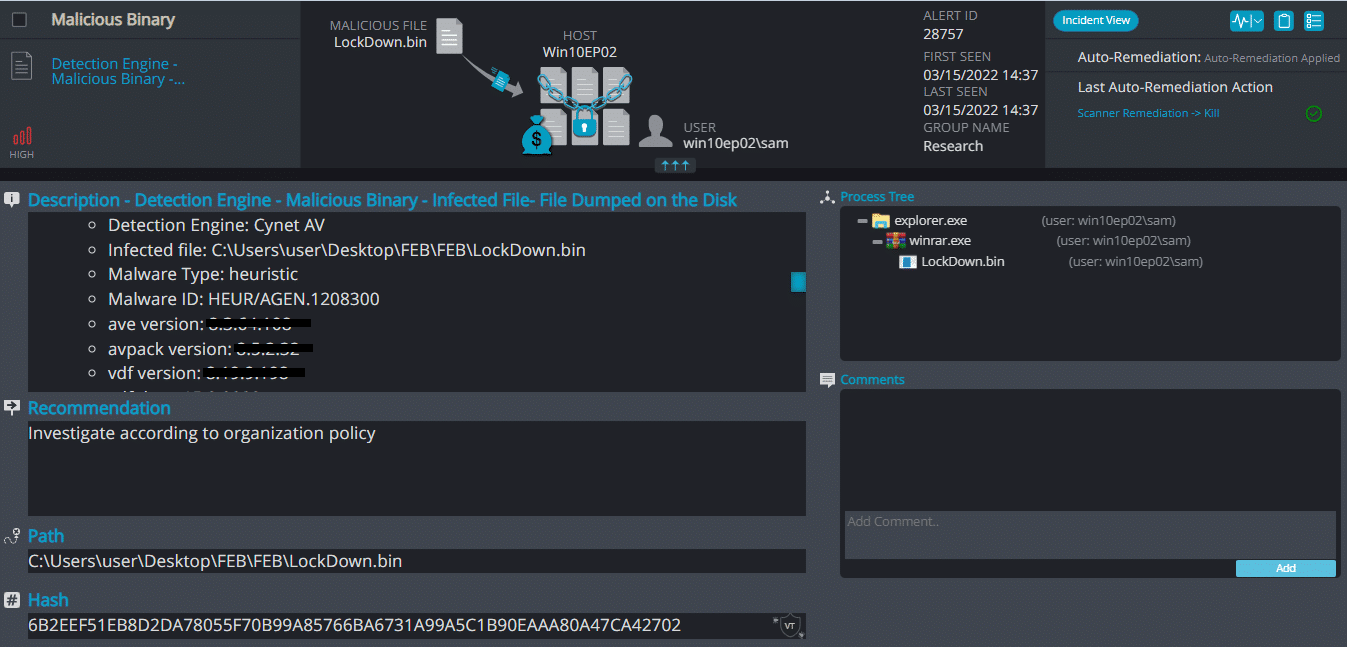
LockDown Ransomware
- Observed since: Late 2020
- Ransomware encryption method: AES + RSA.
- Ransomware extension: .Cantopen
- Ransomware note: HELP_DECRYPT_YOUR_FILES.txt
- Sample hash: 6b2eef51eb8d2da78055f70b99a85766ba6731a99a5c1b90eaaa80a47ca42702
Cynet 360 Detections:
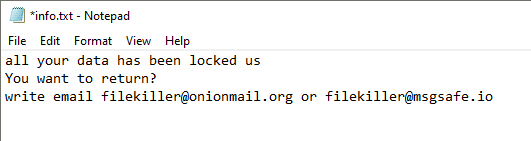
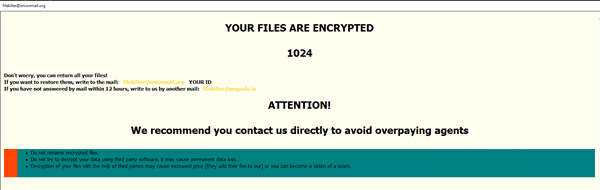
LockDown ransomware renames the encrypted files with .Cantopen in the extension, Once a computer’s files have been encrypted and renamed, it drops a note as HELP_DECRYPT_YOUR_FILES.txt.
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains warnings and the attacker’s bitcoin address:
MonaLisa Ransomware
- Observed since: Dec 2021
- Ransomware encryption method: AES.
- Ransomware extension: .nekochan
- Ransomware note: info.txt | .hta
- Sample hash: ab668490afd212d8a5847a57c77e2c4dac6f8dd0c2d0b9c08ae833d7fa61988e
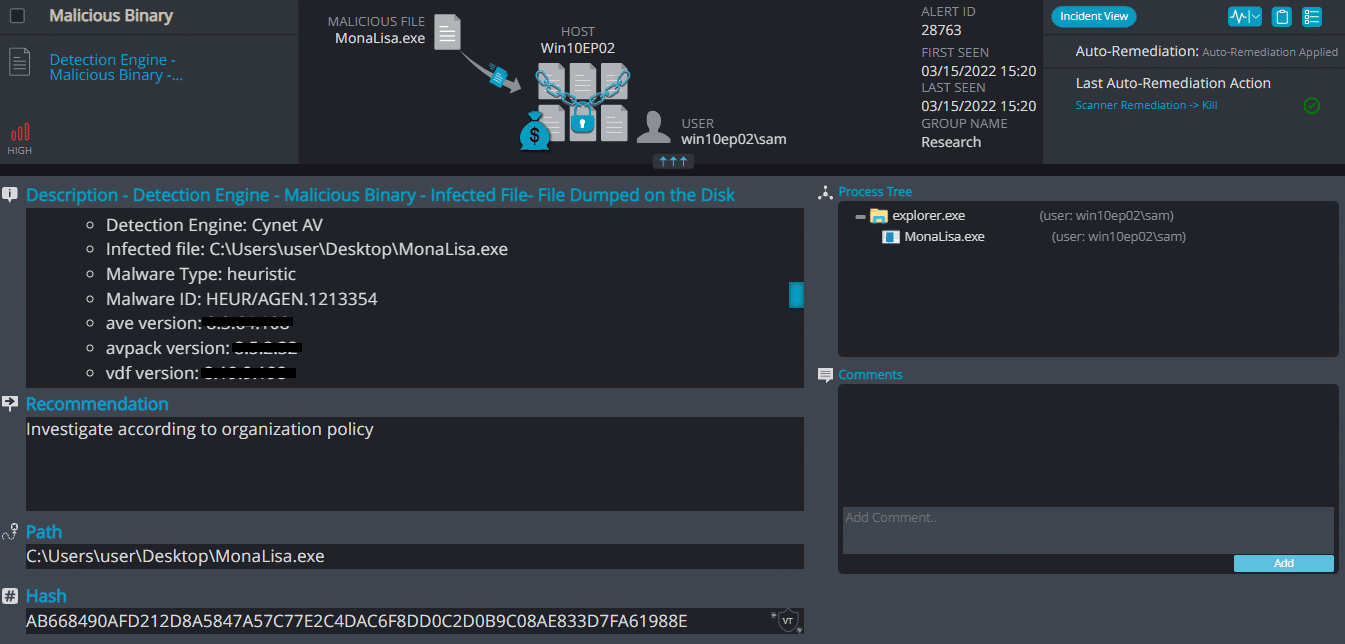
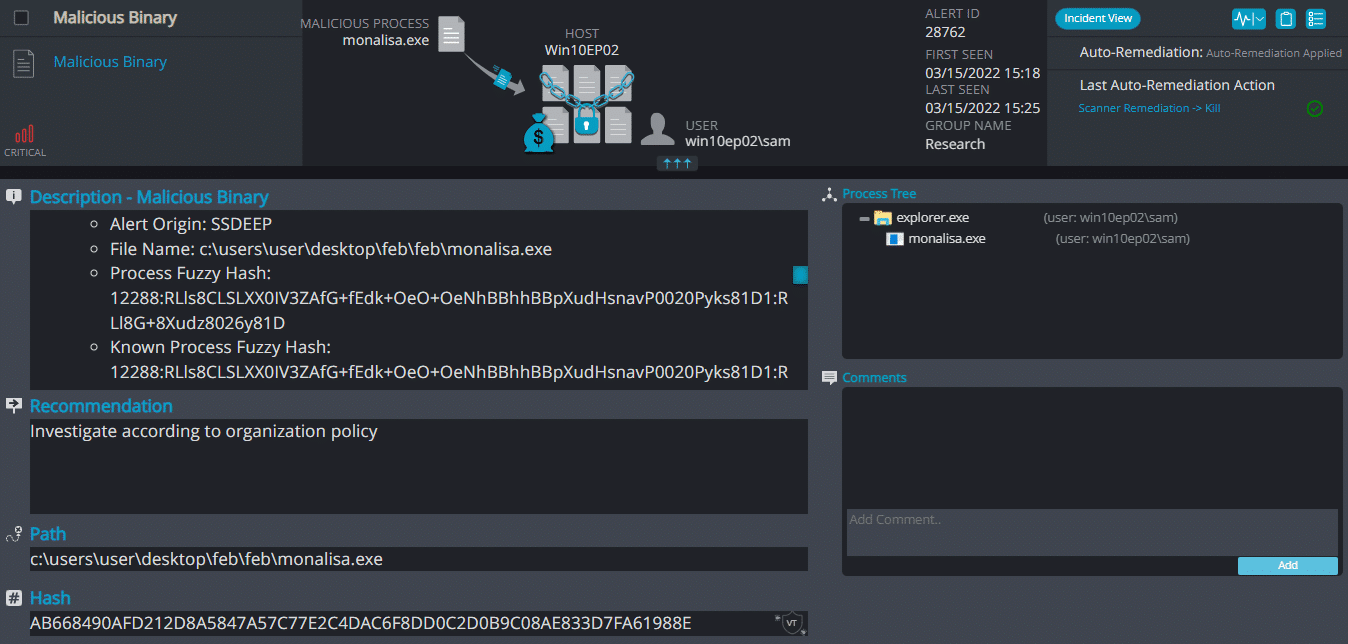
Cynet 360 Detections:
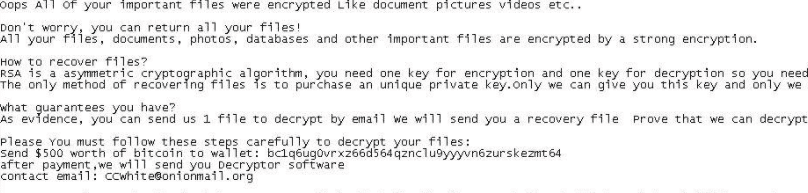
MonaLisa ransomware renames the encrypted files with .nekochan in the extension, Once a computer’s files have been encrypted and renamed, it drops a note as info.txt.
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains contact information:
- Observed since: 2018
- Ransomware encryption method: AES & RSA
- Ransomware extension: .ZOZL
- Ransomware note: info.txt | .hta
- Sample hash: b4965b7fb169577c87cc40e303a002e497fb4812a1376b73e9ba85813917c733
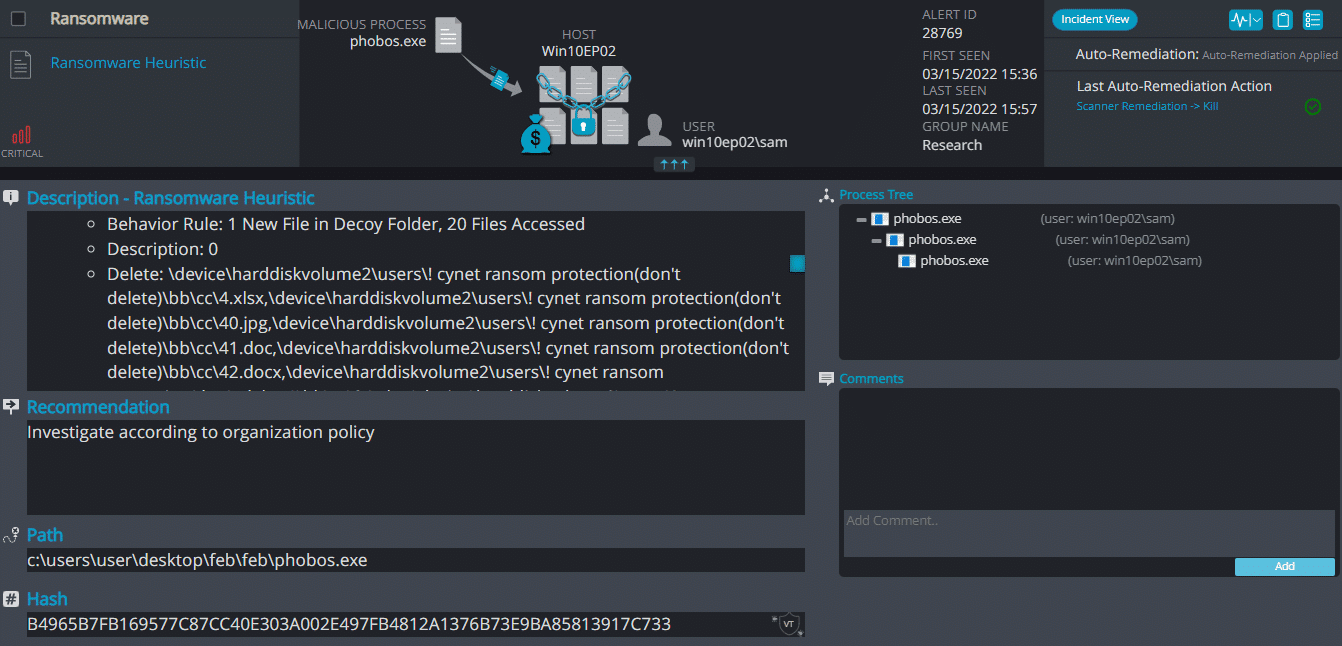
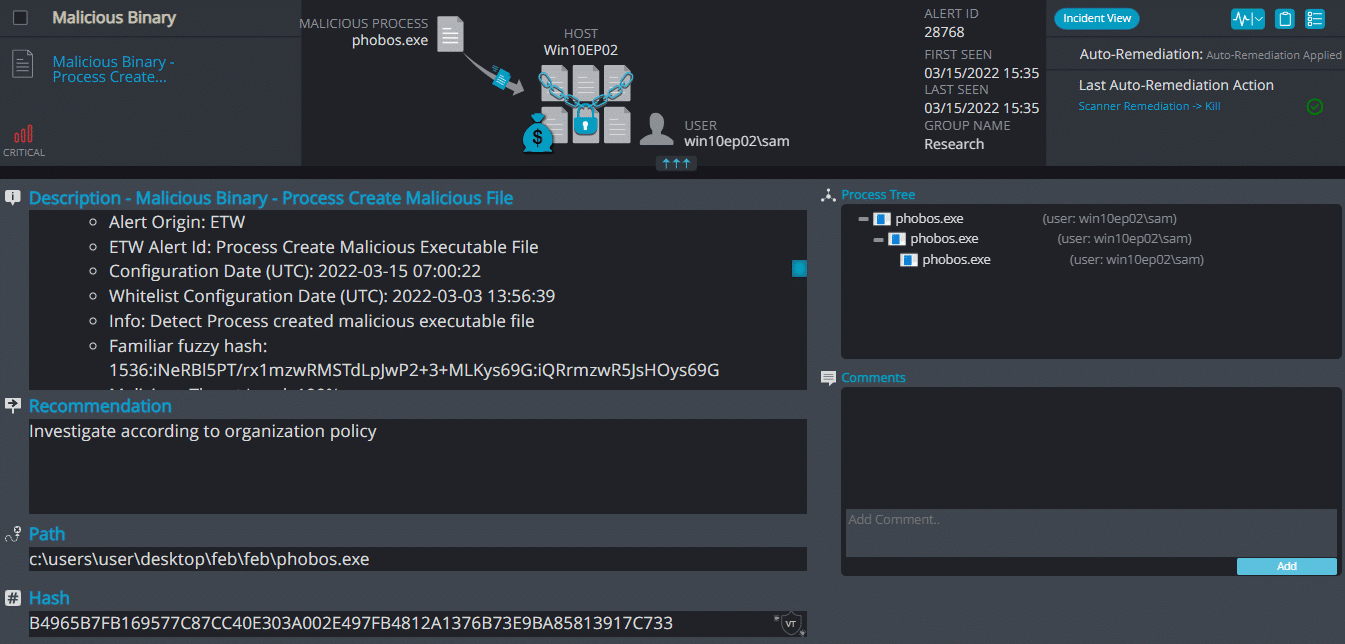
Cynet 360 Detections:
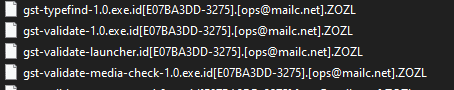
Phobos ransomware renames the encrypted files with .ZOZL in the extension:
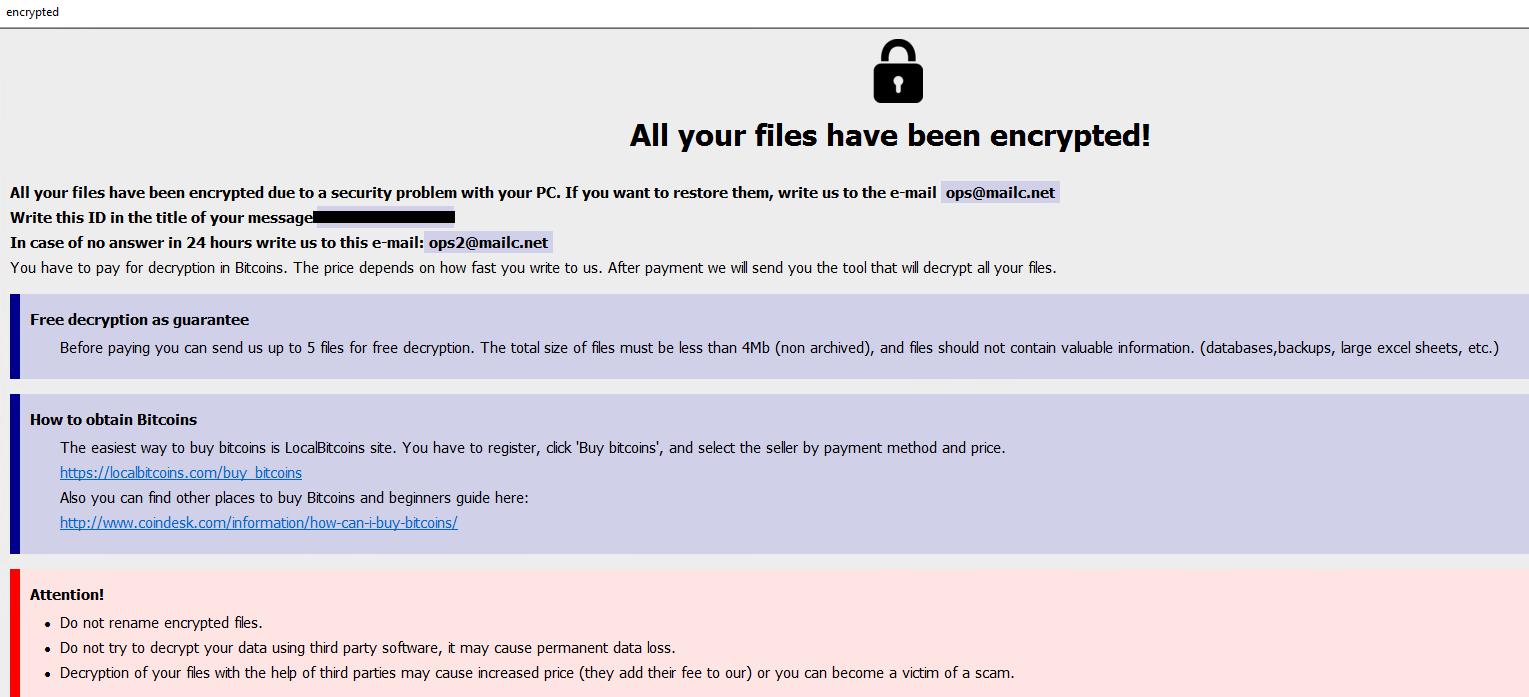
Once a computer’s files have been encrypted and renamed, it drops a note as info.txt.
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains instructions and the attacker’s bitcoin address: