Written by: Maor Huli
This report will split in two parts, that cover ransomware activities for September 2021.
Part one will introduce the following ransomware:
EXECUTIVE SUMMARY
What is ransomware?
Ransomware is a type of malware used to digitally extort victims into paying a ransom. It is also used to prevent or limit users from accessing their files or systems.
The most known targeted files by ransomware are: .doc, .xls, .jpg, .zip, .pdf, and other data files.
Ransomware has become more sophisticated over time. While the original ransomware was limited to encrypting a single endpoint, current variants have advanced distribution mechanisms.
Recently, attackers have targeted large corporations and we wanted to share a few examples of ransomware attacks that affected massive organizations:
- Ransomware attack hits owner of dozens of local news stations
- Accenture: Ransomware Attack Breached Proprietary Data
- Israeli hospital hit with ransomware attack
- Baby died because of ransomware attack on hospital, suit says
Who is targeted by ransomware groups and why?
We think that the easy answer is everyone, but the truth is that the answer is more complex. Keep in mind that Ransomware is a lucrative business model. Most of the threat groups that use ransomware are trying to infect as many computers as possible to hit an organization that will probably pay the ransom.
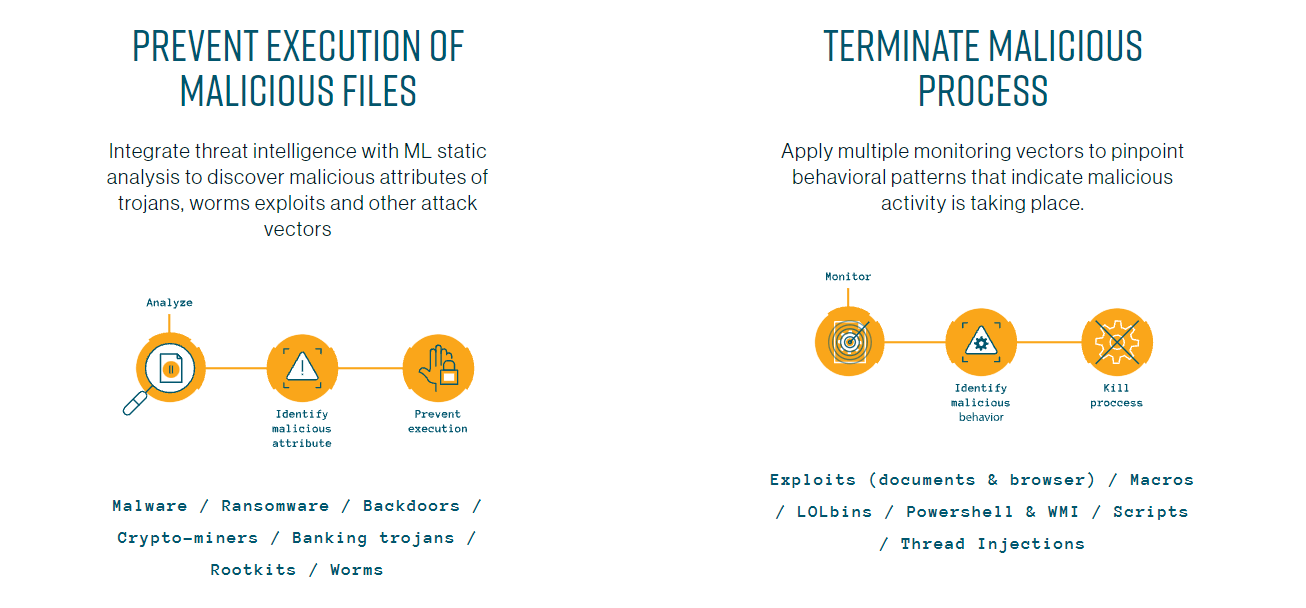
The Cynet 360 platform detects and prevents ransomware attacks via several technology mechanisms. Cynet NGAV integrates multiple prevention technologies to maximize the defense of our customers’ environments. Additionally Cynet’s threat intelligence utilizes over 30 live feeds of various Indicators of Compromise
- https://www.cynet.com/attack-techniques-hands-on/cynet-detection-report-maze-ransomware/
- https://www.cynet.com/attack-techniques-hands-on/cynet-ransomware-report-mespinoza/
- https://www.cynet.com/attack-techniques-hands-on/cynet-detection-report-ragnar-locker-ransomware/
- https://www.cynet.com/attack-techniques-hands-on/netwalker-ransomware-report/
- https://www.cynet.com/attack-techniques-hands-on/shelob-moonlight-spinning-a-larger-web/
- https://www.cynet.com/blog/threat-report-lockbit-ransomware
- https://www.cynet.com/attack-techniques-hands-on/malware-evolution-analyzing-lockbit-2-0/
BleepingComputer is the most up-to-date website that summarizes the newest ransomware variants.
The Cynet Orion Threat Research team is an integral department of Cynet’s research organization. The Orion team works around the clock to add more rules that strengthen Cynet 360’s detection capabilities. Part of Orion’s team tasks include following posts on BleepingComputer about new ransomware variants and threats. Our overall goal is to detect every threat that appears.
In this article, we have summarized ransomware variants from September based on BleepingComputer. We will present recent ransomware and how Cynet 360 platform detects them via several mechanisms.
CYNET 360 VS RANSOMWARE
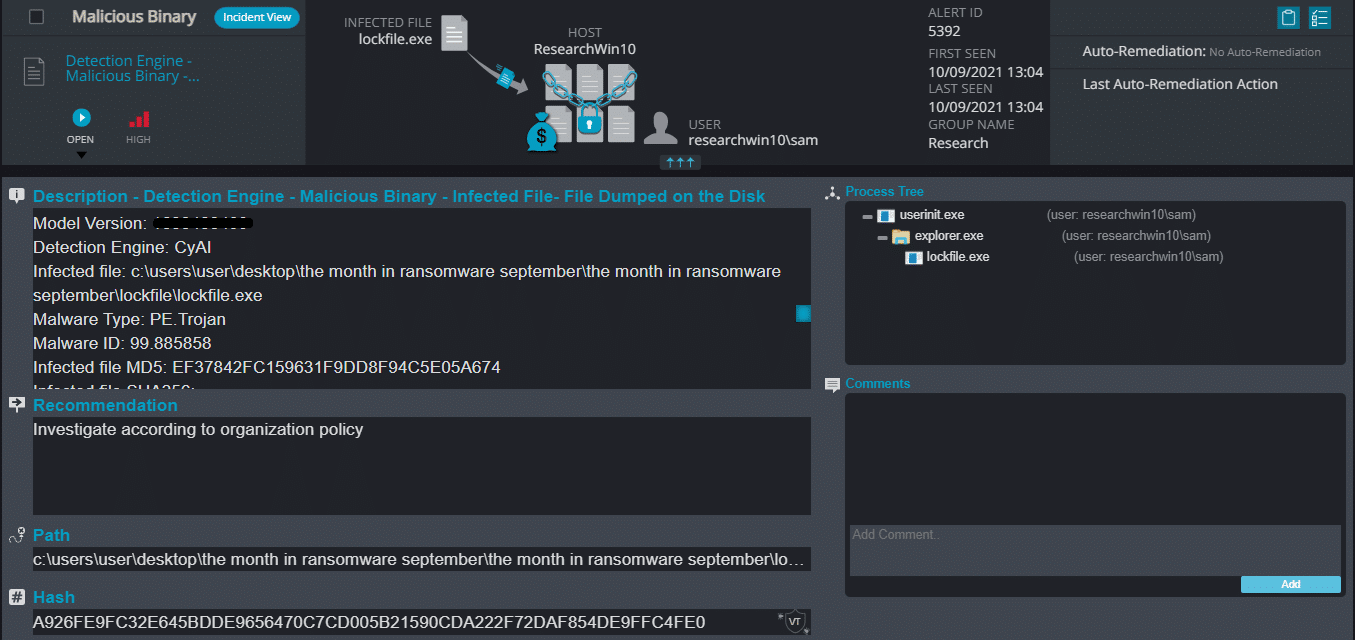
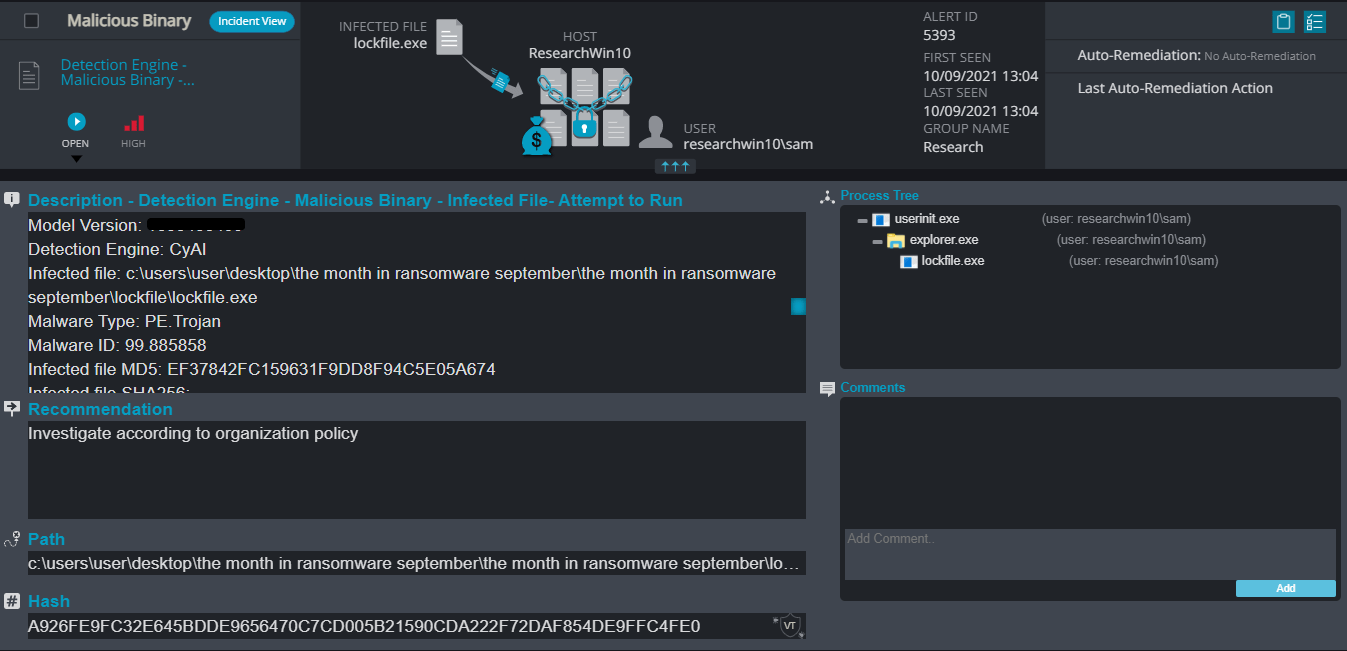
LockFile Ransomware
- Observed since: May 2020
- Ransomware encryption method: AES + RSA.
- Ransomware extension: .lockfile
- Ransomware note: [Hostname]-LOCKFILE-README.hta
- Sample hash: a926fe9fc32e645bdde9656470c7cd005b21590cda222f72daf854de9ffc4fe0
Cynet 360 Detections:
LockFile Overview
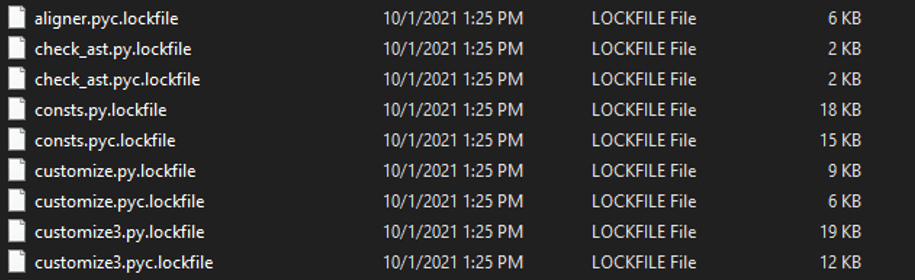
LockFile ransomware renames the encrypted files with a .lockfile extension:
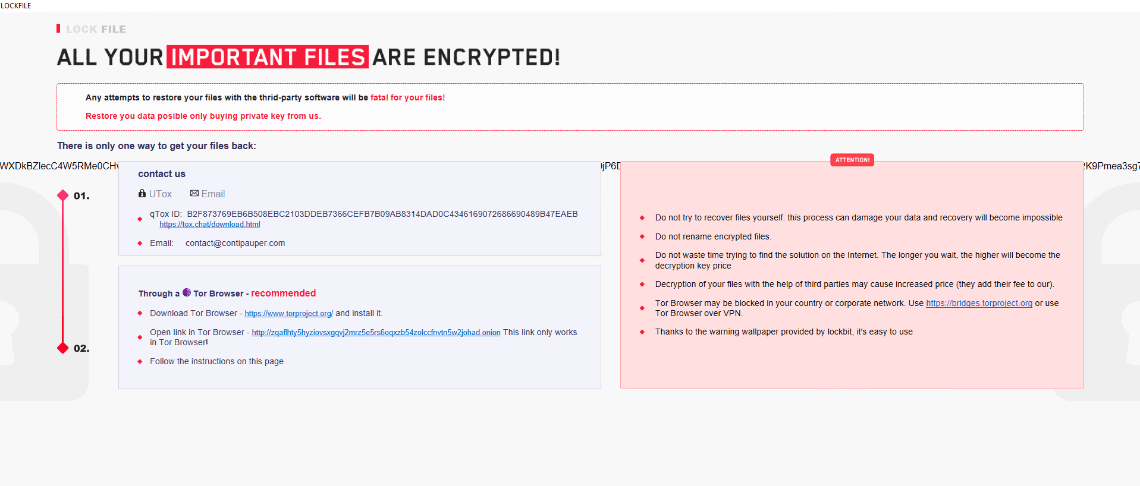
Once a computer’s files have been encrypted and renamed, it drops a note as an .hta file that also contains the hostname in it. Upon execution, it uses mshta.exe to open the ransomware note. The ransomware note has the email address of threat actors, the ransom demand and the instructions on how to pay the demand.
Locky Ransomware
- Observed since: October 2020
- Ransomware encryption method: AES + RSA.
- Ransomware extension: .odin
- Ransomware note:_[four numerics]_HOWDO_text.html
- Sample hash: e7ac6394525058f75cf83d7eacb23a49ef895ee88aca46e90adfee01bc876c77
Cynet 360 Detections:
Locky Overview
Locky ransomware renames the encrypted files with a .odin extension for each file:
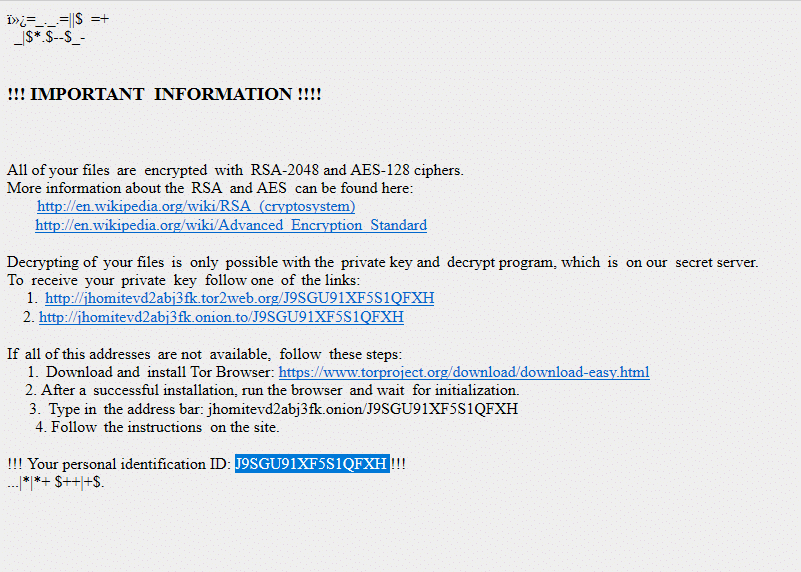
Once a computer’s files have been encrypted and renamed, it drops a note as an HTML file that contains random numbers and the string “HOWDO_text. Upon execution, it uses the default browser of the host to open the ransomware note.
The note itself contains two links to the attackers’ website with further instructions. The first link is for the “clear web” and the second one is for the “dark web”,
The note also contains the victim’s ID
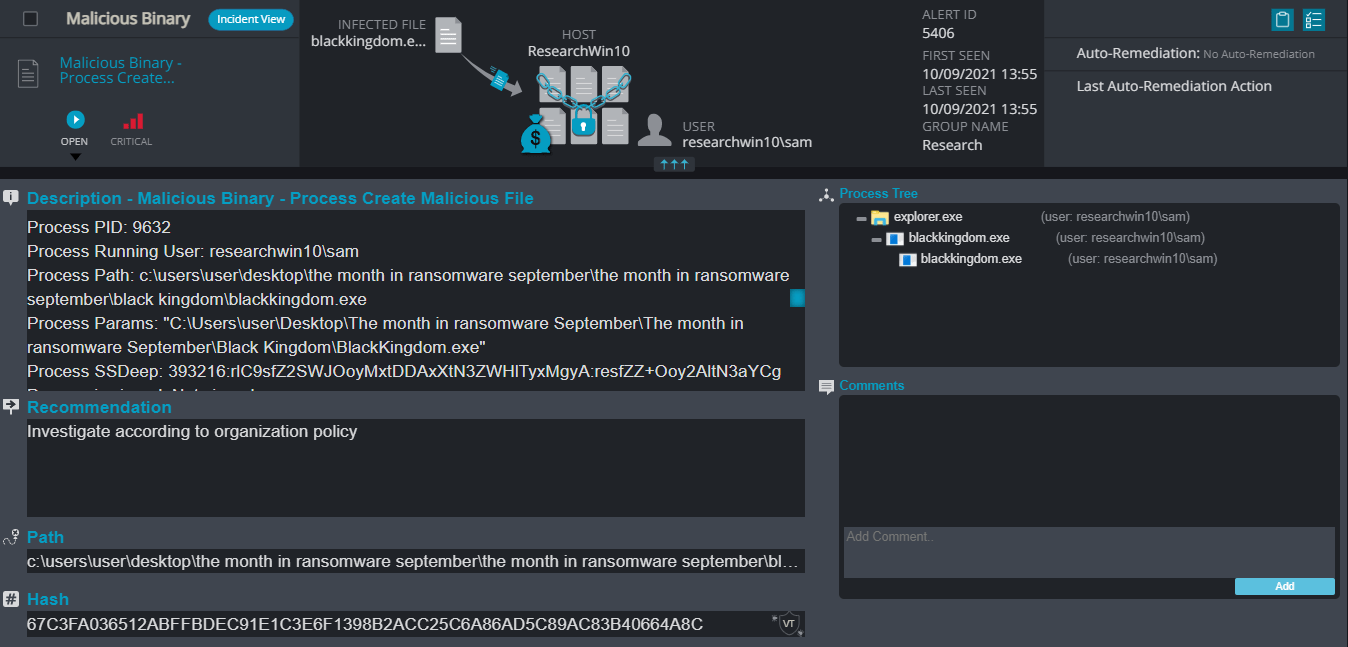
Black Kingdom Ransomware
- Observed since: February 2020
- Ransomware encryption method: AES.
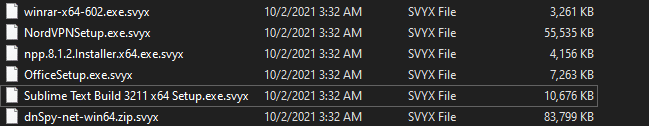
- Ransomware extension: .svyx
- Ransomware note: Readme.txt
- Sample hash: 67c3fa036512abffbdec91e1c3e6f1398b2acc25c6a86ad5c89ac83b40664a8c
Cynet 360 Detections:
Black Kingdom Overview
Blackkingdom ransomware mostly targets executables, pictures, and documents in folders such as Downloads, Documents, and the desktop. It renames encrypted files with a .svyx extension for each file:
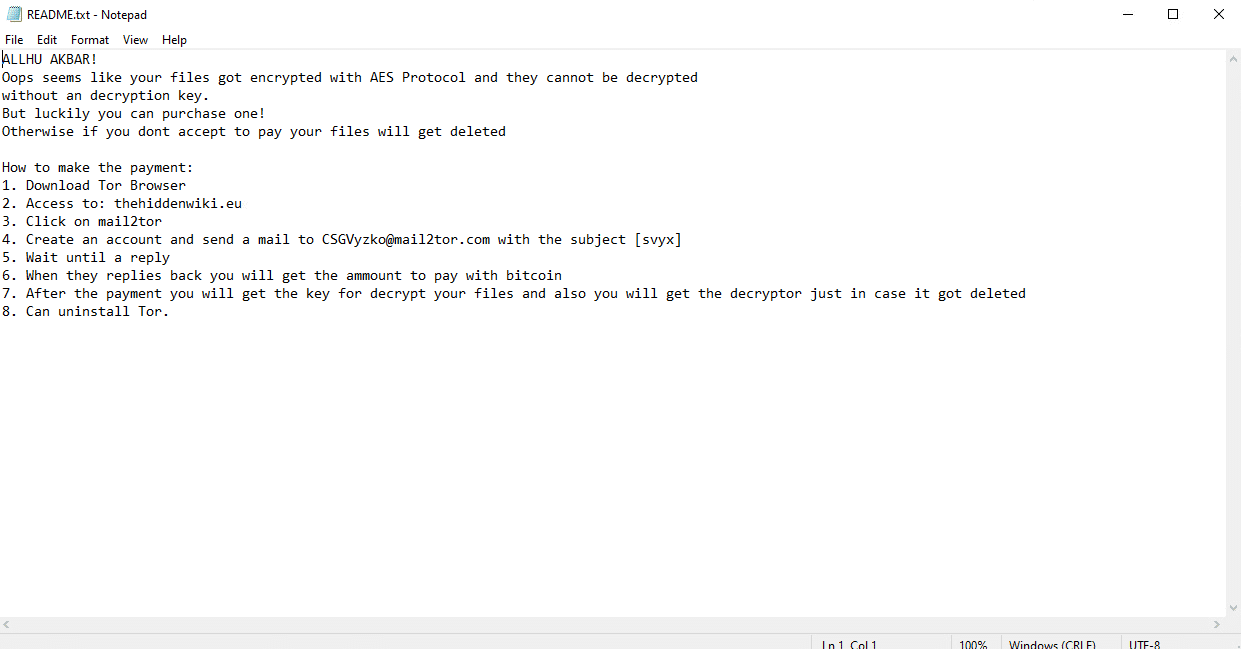
Once a computer’s files have been encrypted and renamed, it drops a note (.txt) file named README.txt. In the text file it writes instructions on how to pay to get the encrypted files back.
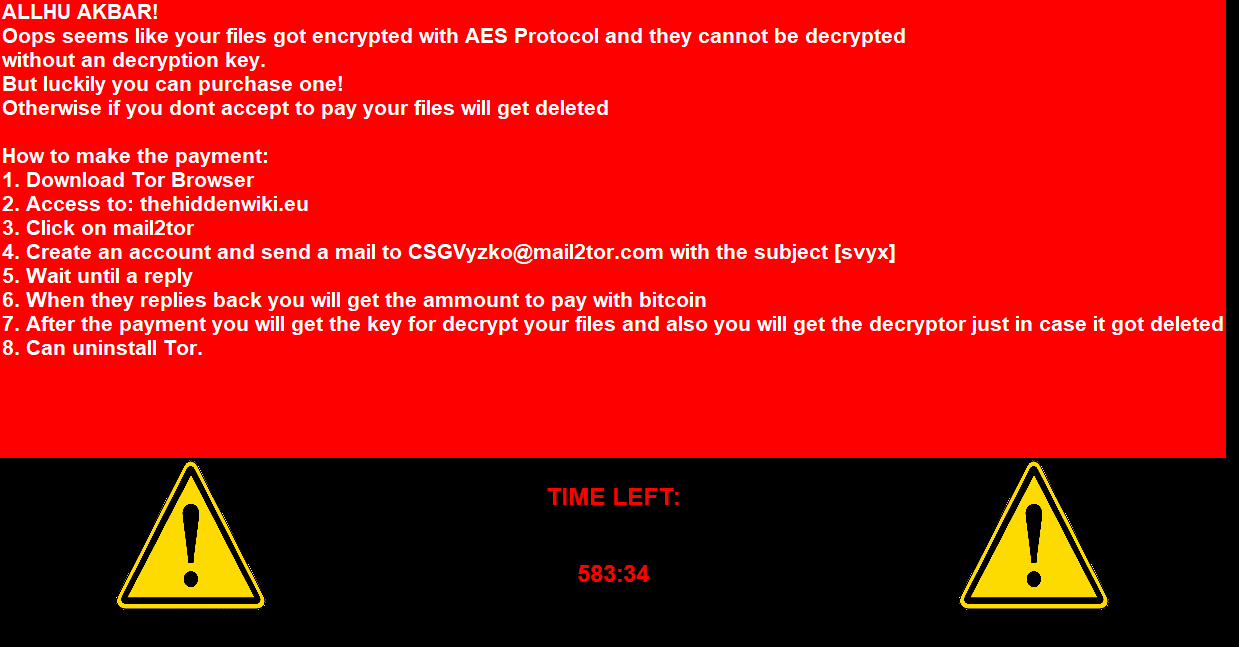
Also, the ransomware opens a process named “Tango Down!” that will always be on top of everything including the taskbar so the user might think it changed the background and eliminated the shortcuts on the desktop. Additionally, this process also contains a timer that the attacker promises to delete the files if the timer goes down to zero.
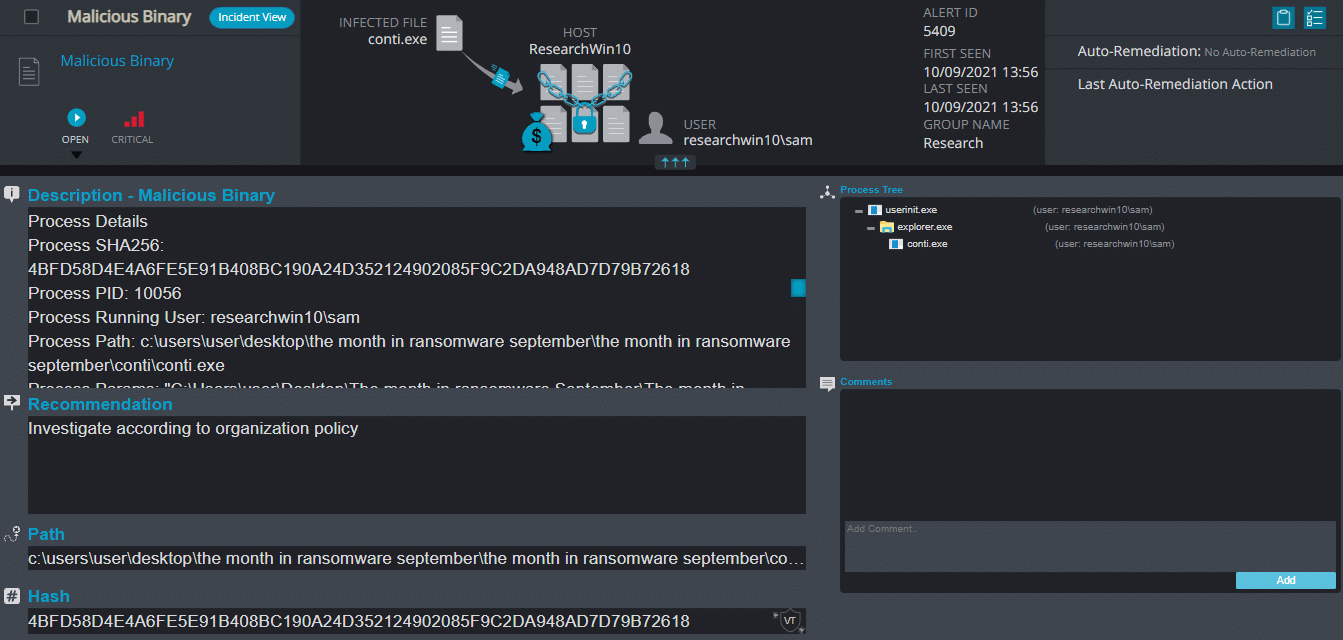
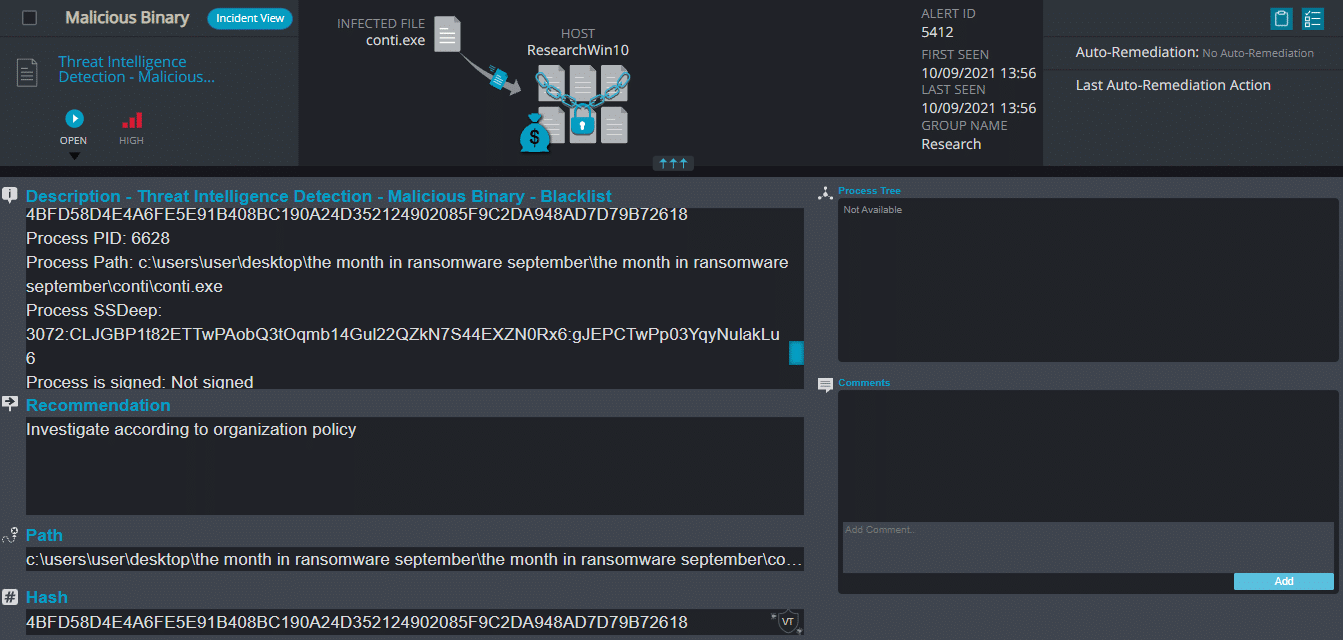
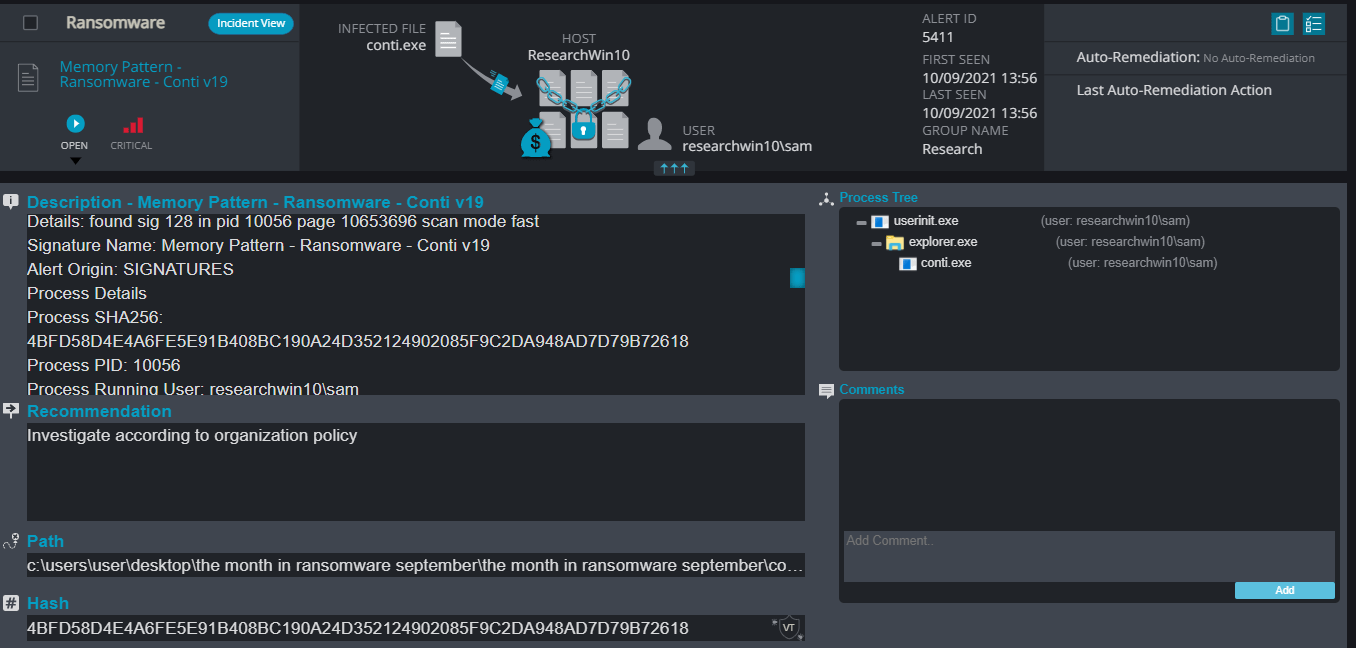
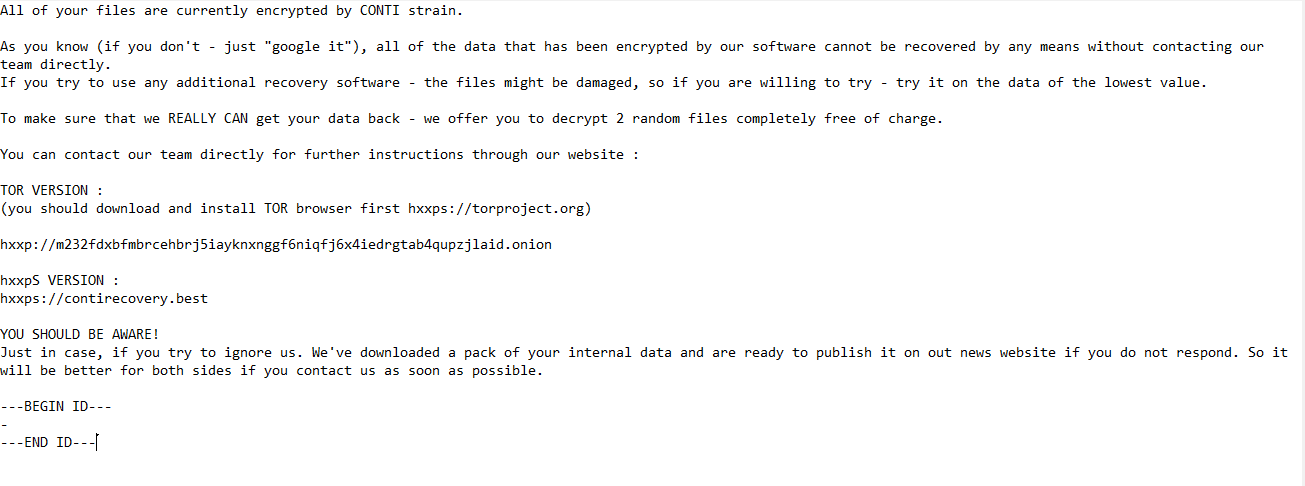
Conti Ransomware
- Observed since: May 2020
- Ransomware encryption method: ChaCha20.
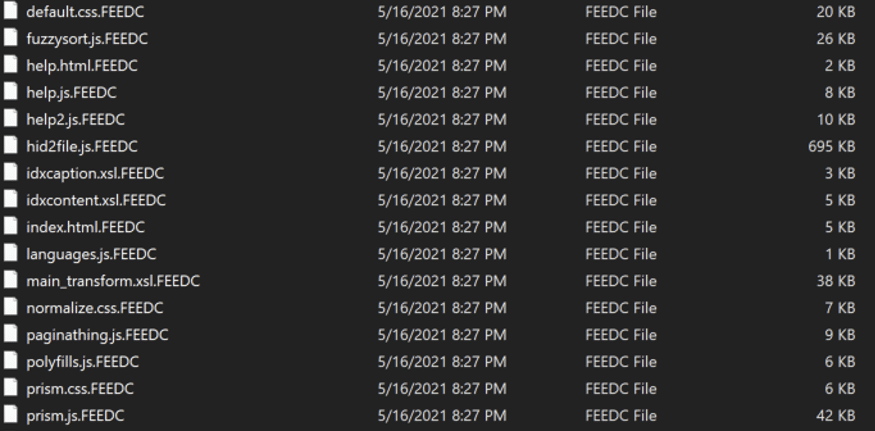
- Ransomware extension: .FEEDC
- Ransomware note: Readme.txt
- Sample hash: 4bfd58d4e4a6fe5e91b408bc190a24d352124902085f9c2da948ad7d79b72618
Cynet 360 Detections:
Conti Overview
Conti ransomware renames the encrypted files to a random extension with five different letters each time.
Please note that since we are running simulations in a virtual environment, some ransomware can distinguish between the real environment and a virtual one. In our case, the ransomware shuts itself down since it detected the virtual environment. The following screenshots are from different sources.
Once a computer’s files have been encrypted and renamed, it drops a note as a text (.txt) file named Readme.txt. In the text file it writes instructions on how to pay to get the encrypted files back.
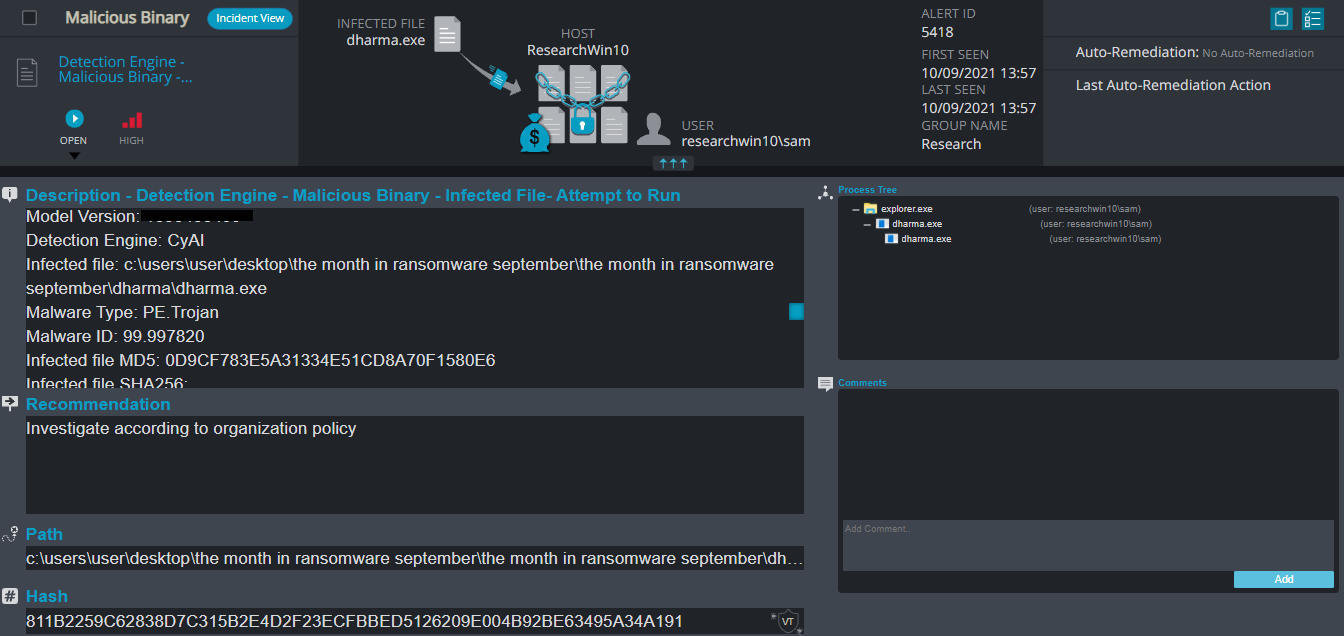
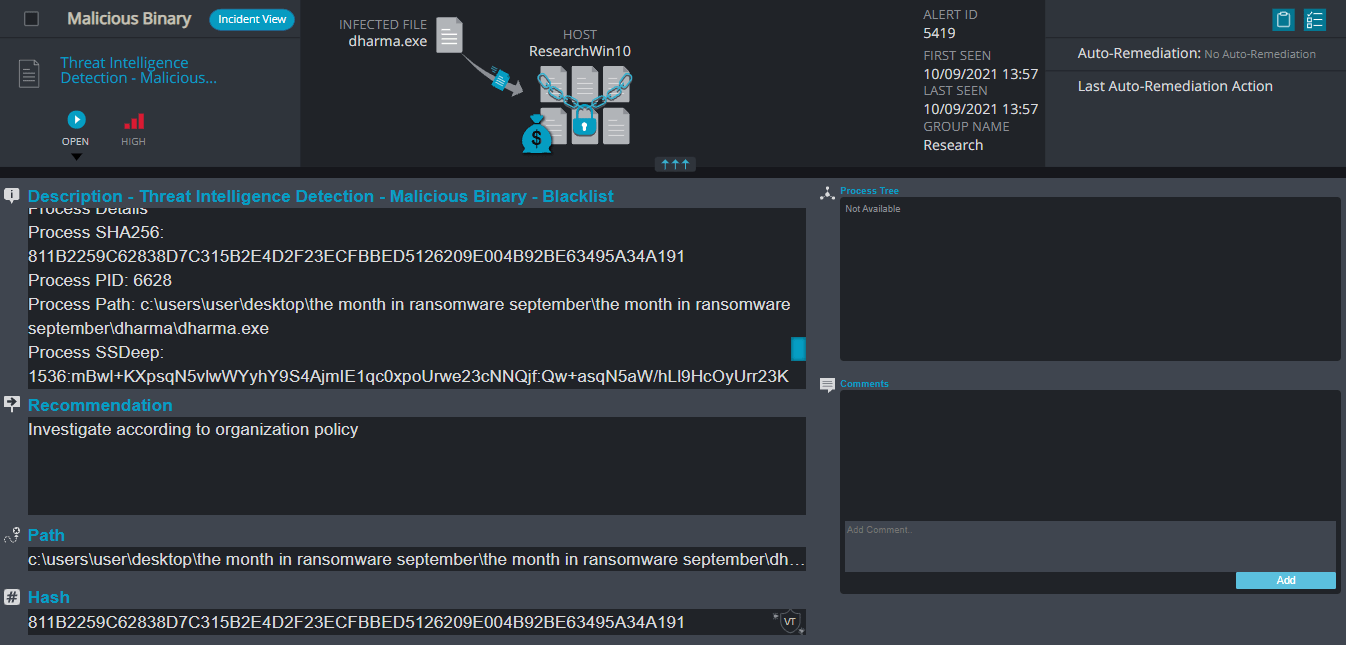
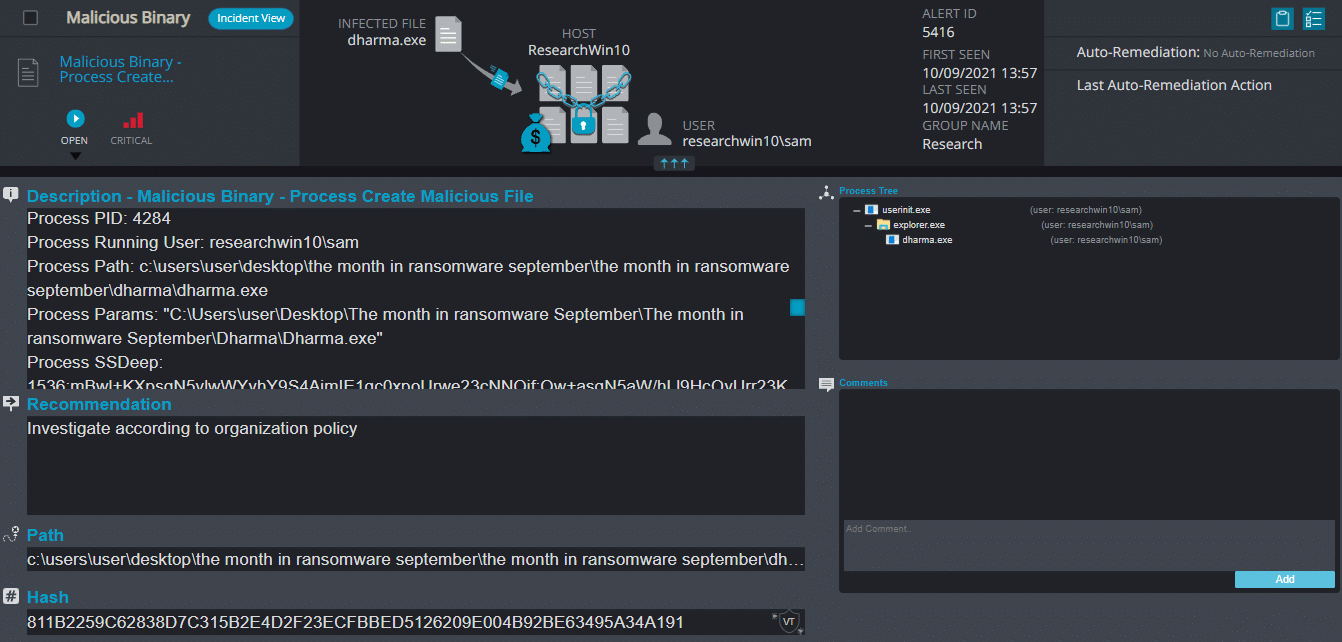
Dharma (Crysis) Ransomware
- Observed since: Early 2016
- Ransomware encryption method: AES.
- Ransomware extension: .dts
- Ransomware note: information appear in the encrypted files’ name
- Sample hash: 811b2259c62838d7c315b2e4d2f23ecfbbed5126209e004b92be63495a34a191
Cynet 360 Detections:
Dharma (Crysis) Overview
Dharma ransomware renames the encrypted files with a personal ID of the victim and the attacker email address and .dts extension for each file:
Once a computer’s files have been encrypted and renamed, the only way to communicate with the attacker is to send them an email by looking at the encrypted files as shown above.
Phobos Ransomware
- Observed since: Mid 2017
- Ransomware encryption method: AES.
- Ransomware extension: .PERDAK
- Ransomware note: info.txt
- Sample hash:0071a75d8bf5d67acb559c3d2d4b1b866a899bd8de837283e2d8e54863bd4765
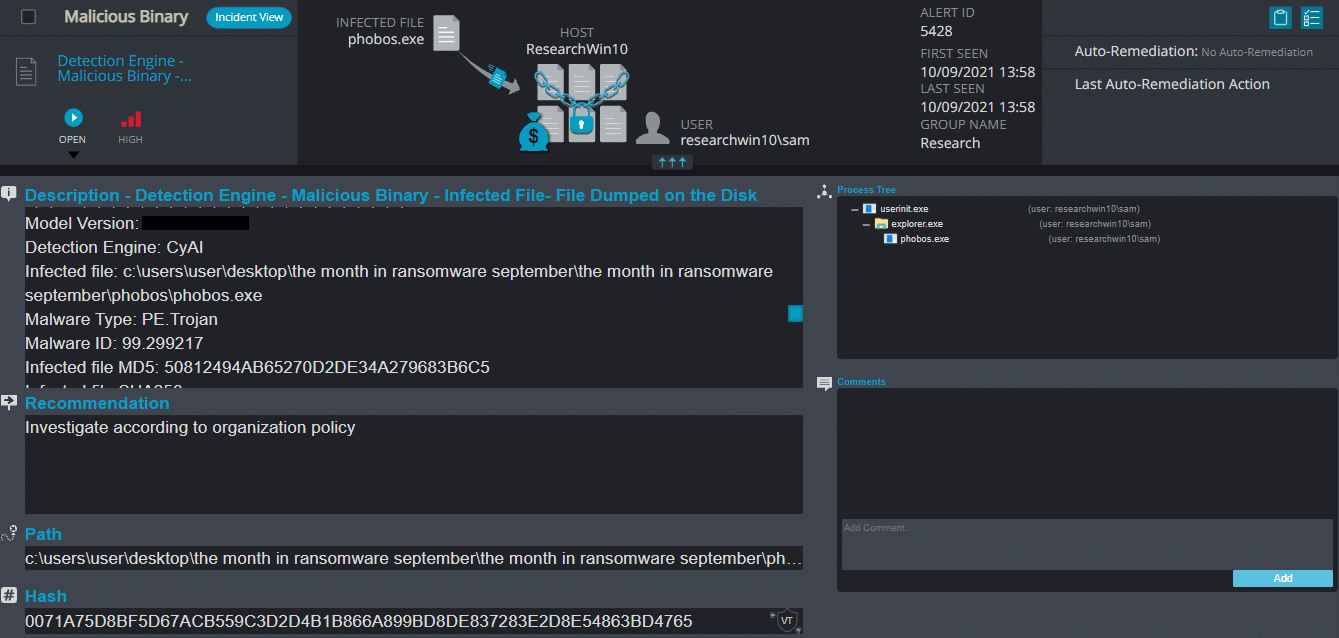
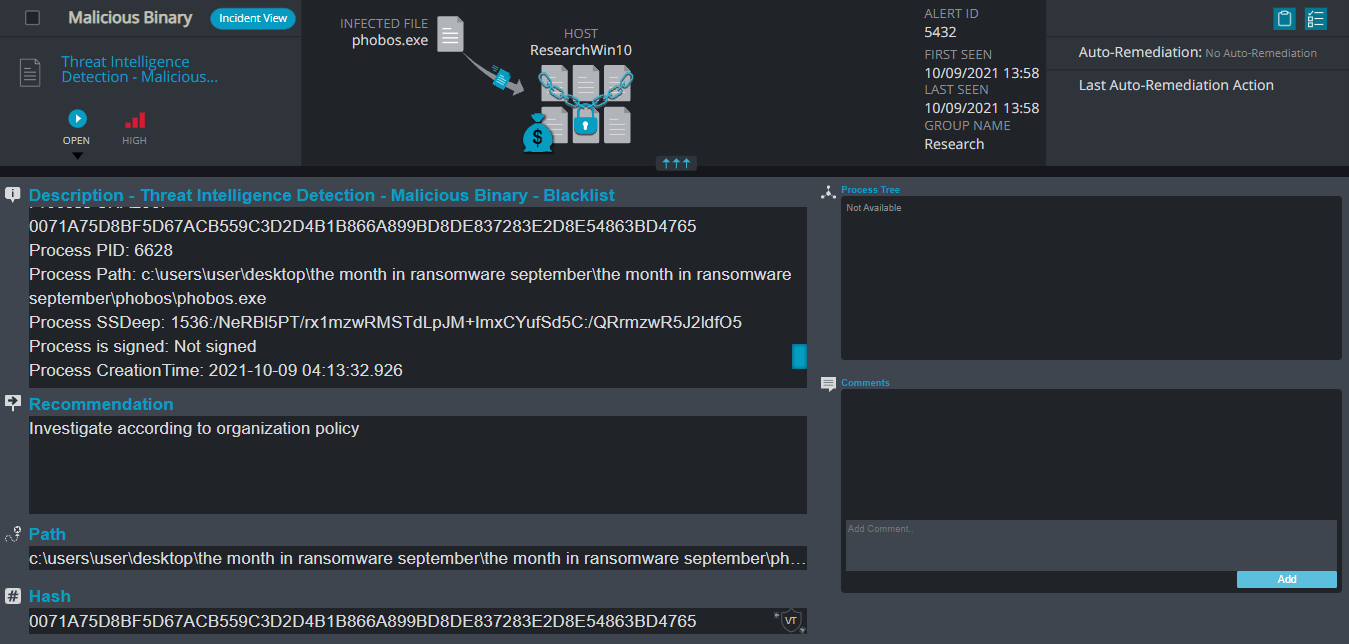
Cynet 360 Detections:
Phobos Overview
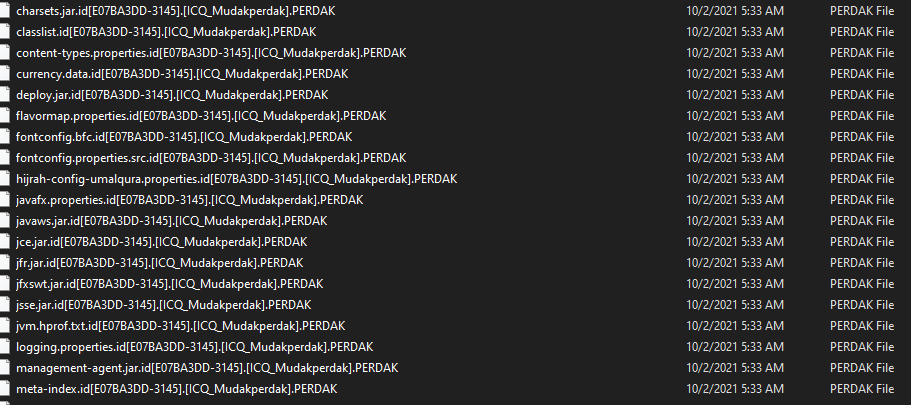
After execution, Phobos ransomware renames the encrypted files with the victim ID, the communication information, and the variant name in the extension for each file:
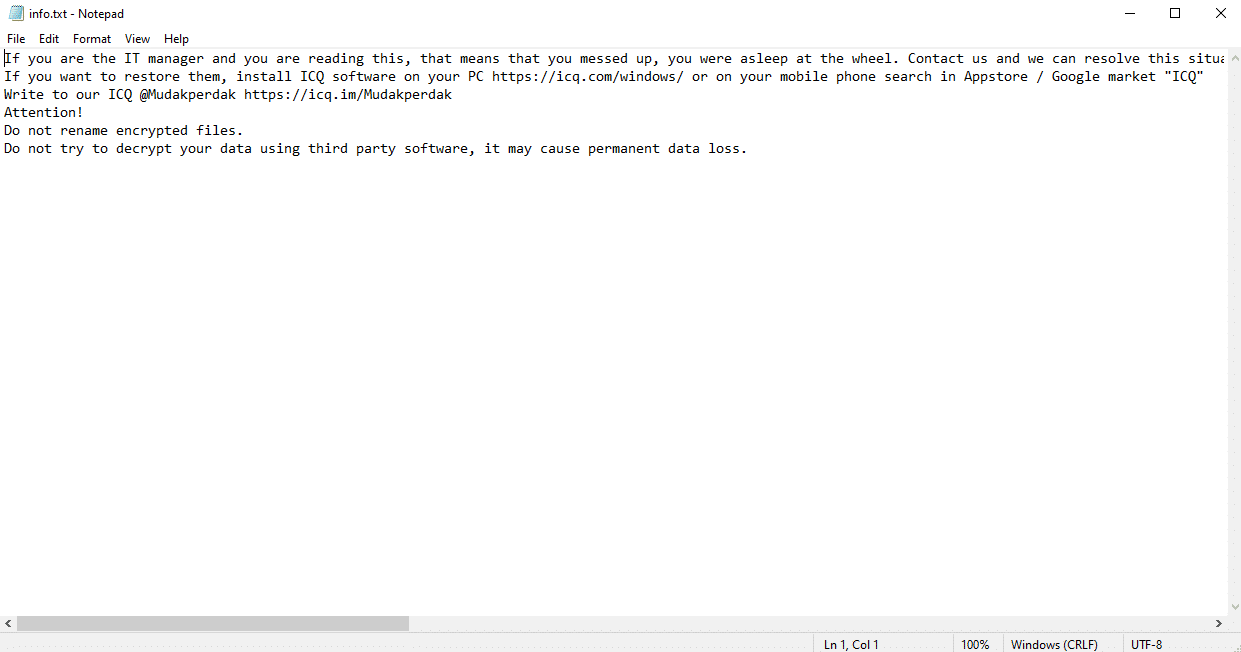
Once a computer’s files have been encrypted and renamed, it pops up a message with the ransomware note and the communication details. Additionally, it drops the ransomware note as a text file named info.txt on the victim’s desktop.
Sanwai Ransomware
- Observed since: August 2021
- Ransomware encryption method: AES + RSA.
- Ransomware extension: sanwai \ sanwai2
- Ransomware note: IMPORTANT.txt
- Sample hash: 9d6a780c9d7d1b3d95717fda1f4b388aef2d7282884b0c84714e3755dbabb71b
Cynet 360 Detections:
Sanwai Overview
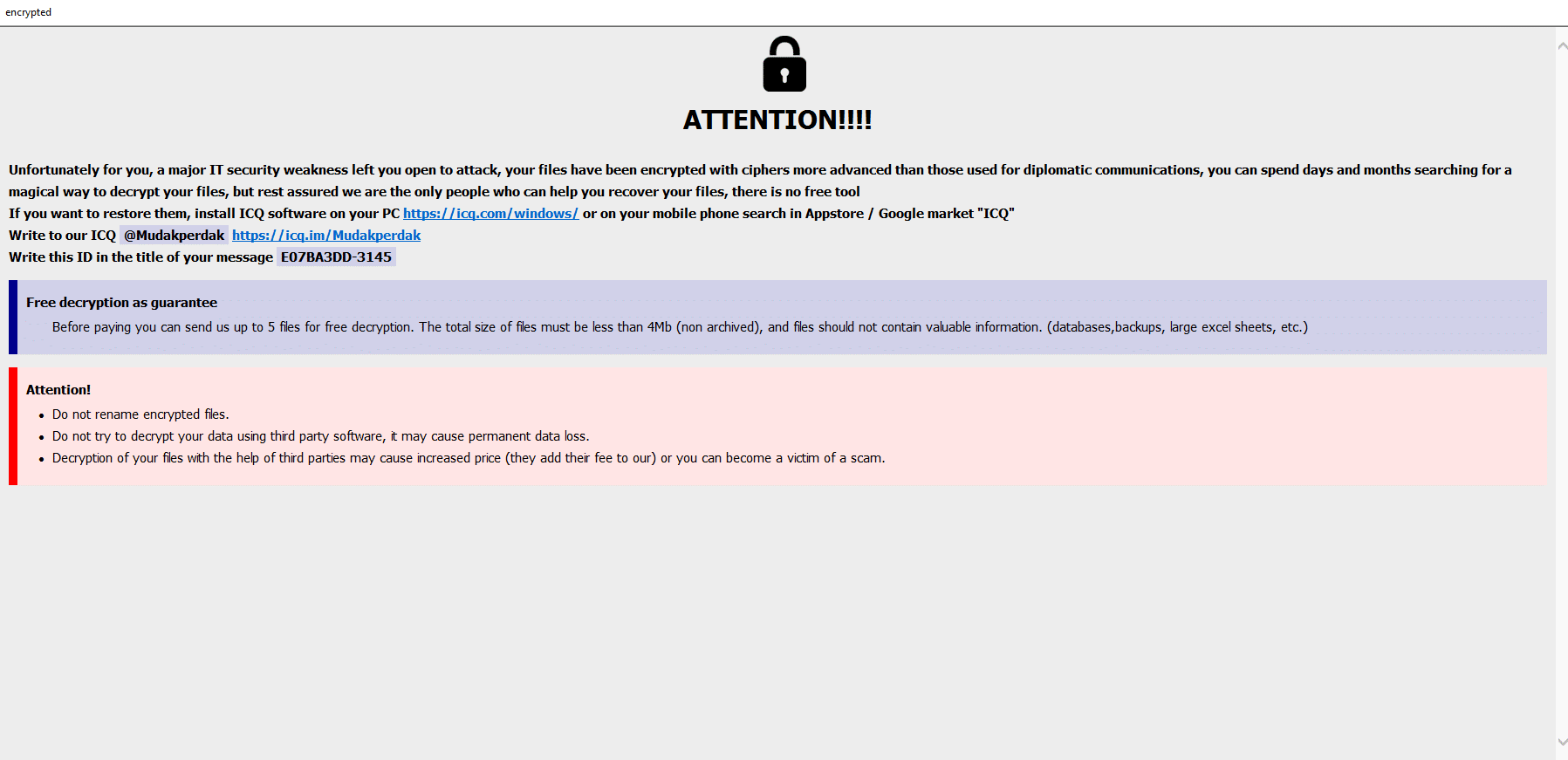
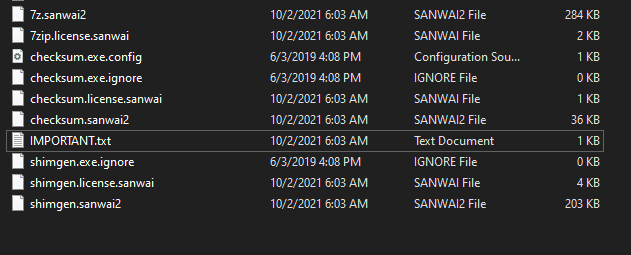
After execution, Sanwai ransomware renames the encrypted files with sanwai and random number in the extension for each file:
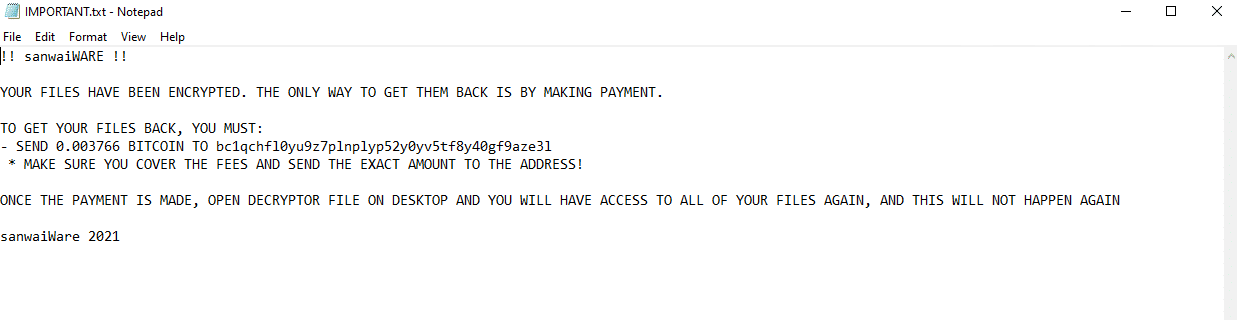
Once a computer’s files have been encrypted and renamed, it drops the ransomware note as a text file named IMPORTANT.txt in the victim’s encrypted folders. The note contains the price to decrypt the files and the attacker’s public address for the bitcoin wallet
STOP Ransomware
- Observed since: December 2018
- Ransomware encryption method: AES + RSA.
- Ransomware extension: .nusm
- Ransomware note: _readme.txt
- Sample hash: c5e7c2f3efd209636294e9ae666d8784f63025aae3a3ba437e4d0c975dc9366c
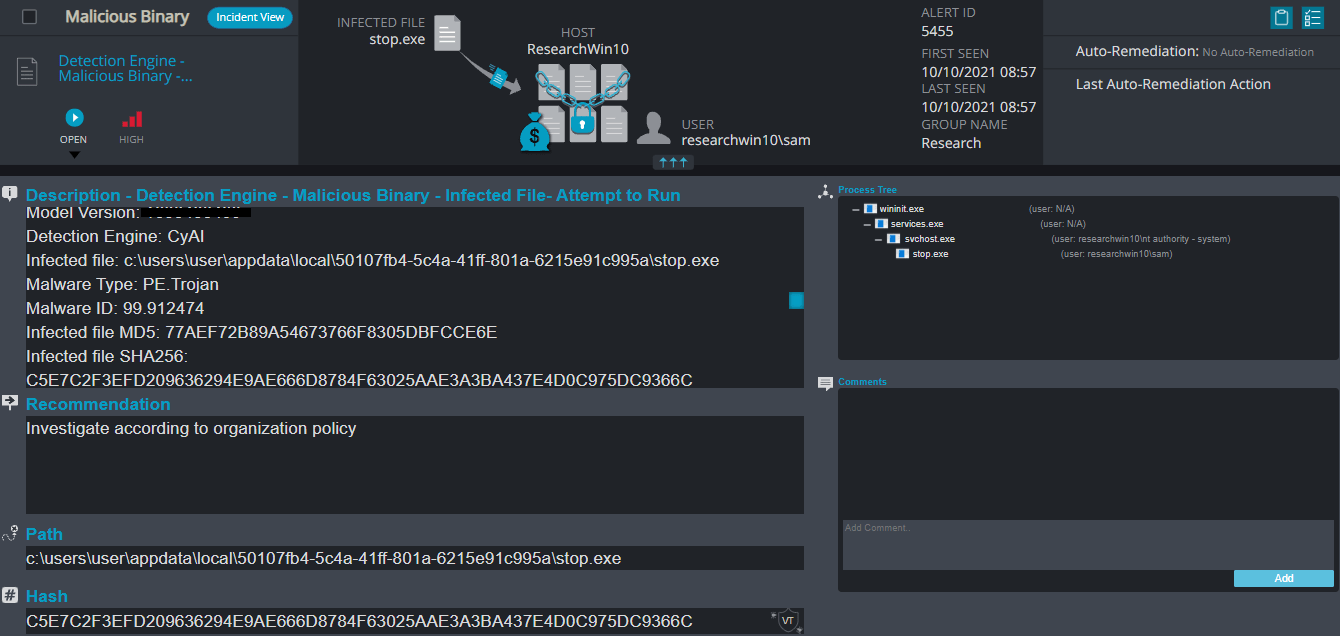
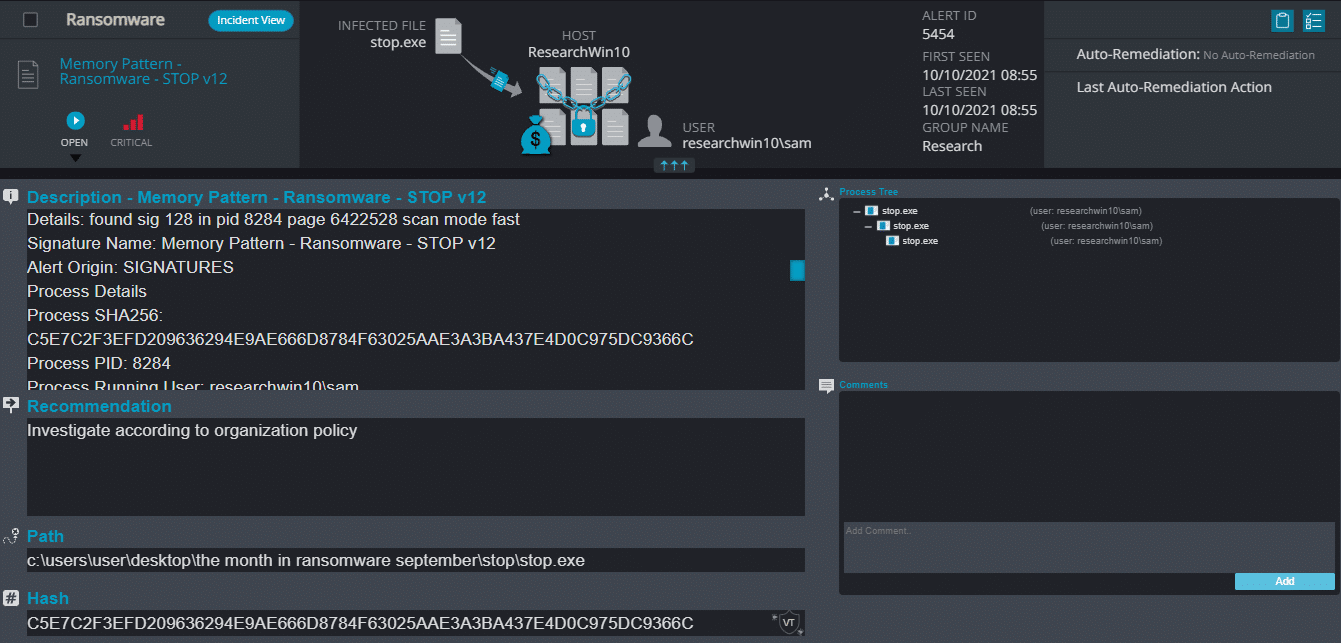
Cynet 360 Detections:
STOP Overview
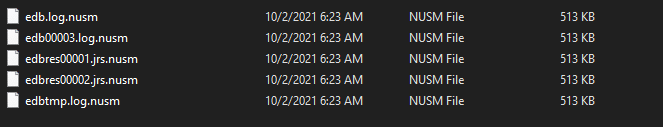
After execution, STOP ransomware renames the encrypted files with .nusm in the extension for each file:
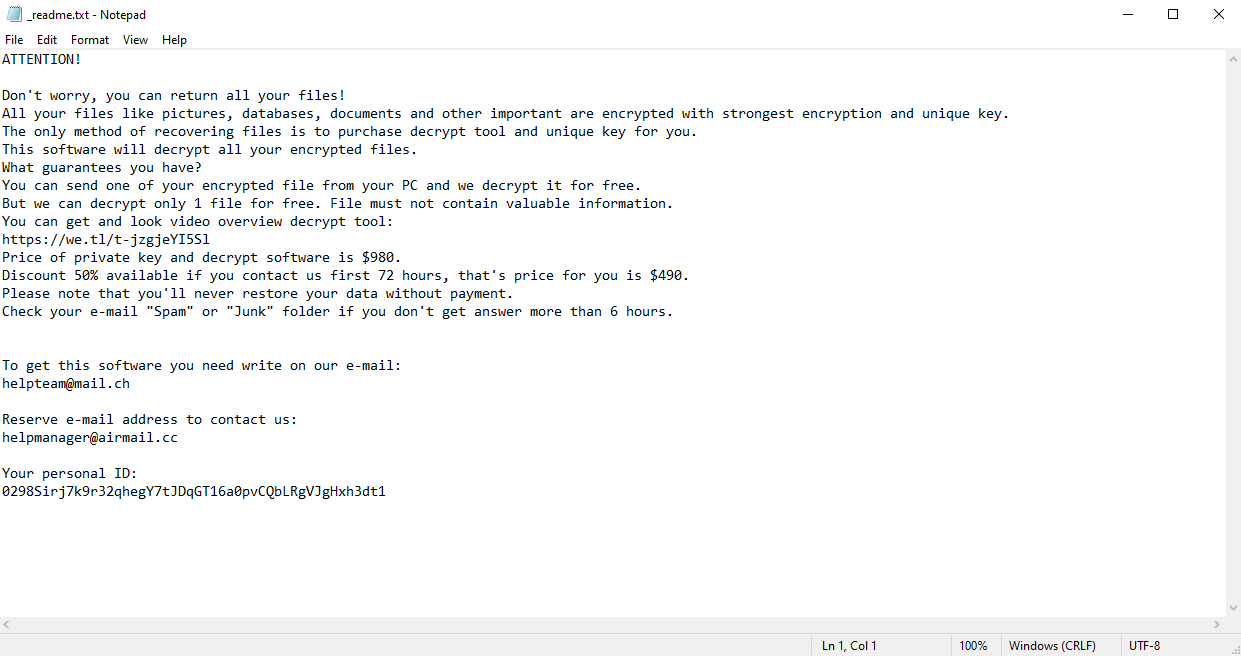
Once a computer’s files have been encrypted and renamed, it drops the ransomware note as a text file named _readme.txt in the victim’s encrypted folders, the note contains decryption instructions along with the price and the communication details
CYNET’S VARIOUS MECHANISMS
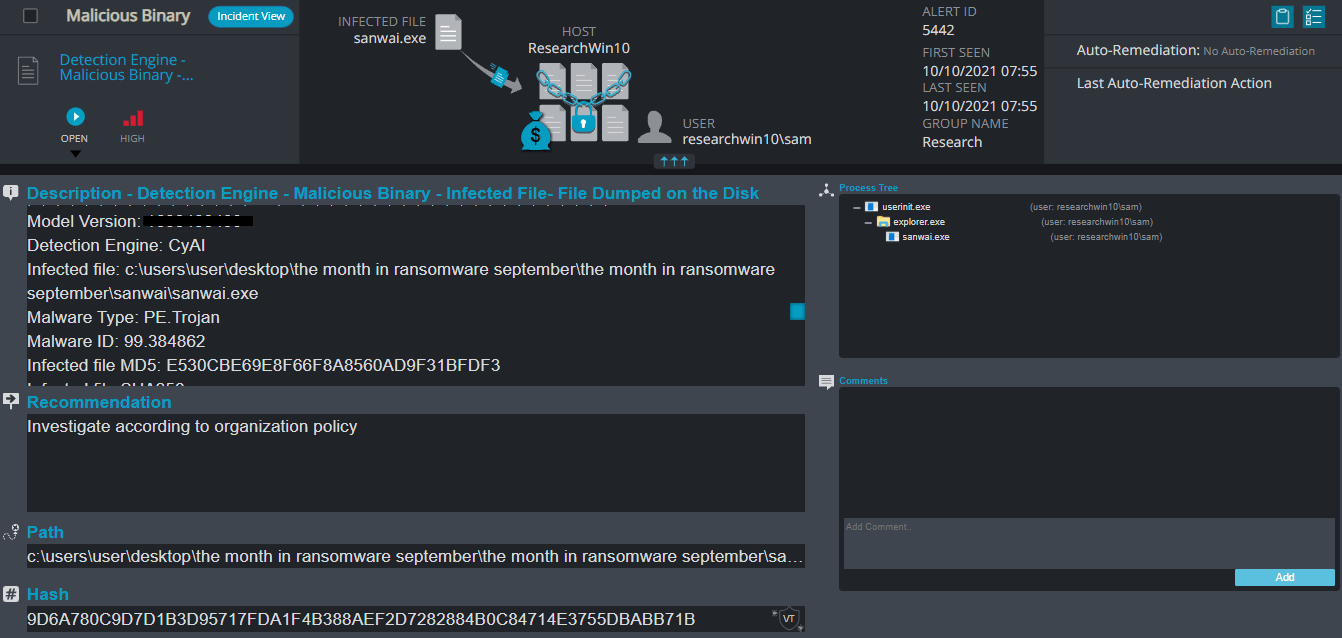
- AV/AI – This alert triggers when Cynet’s AV/AI engine detects a malicious file that was either dumped on the disk or executed
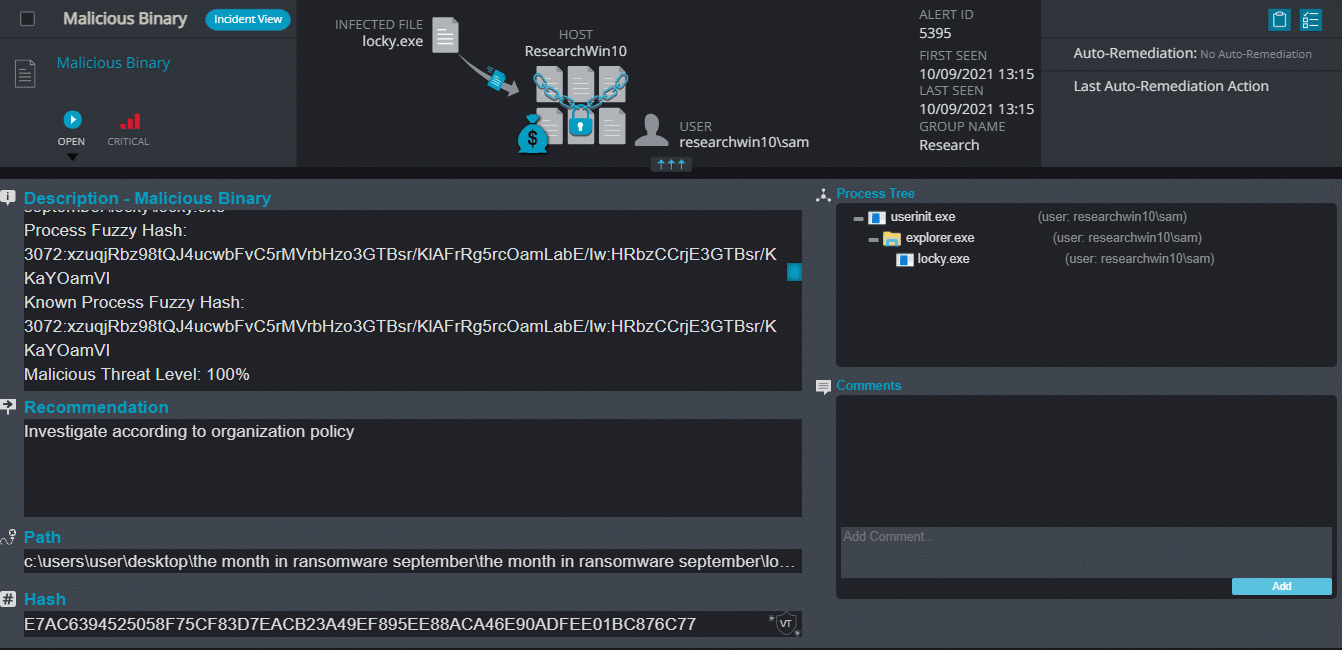
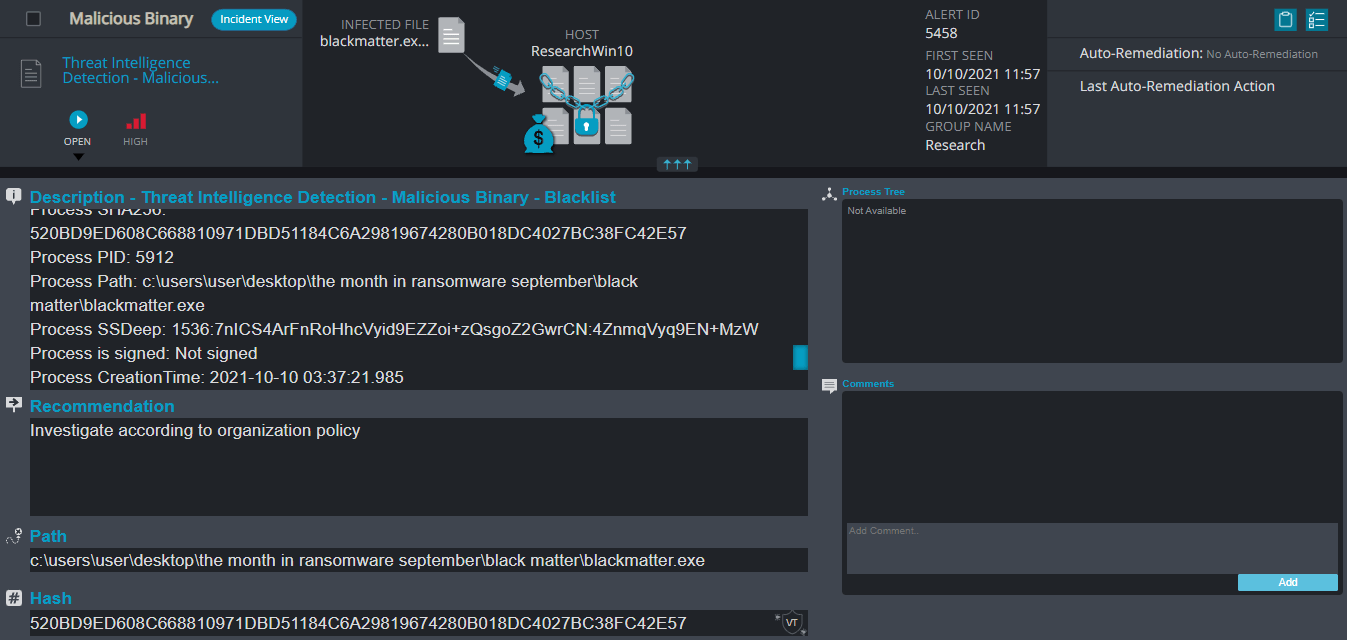
- Malicious Binary – This alert triggers when Cynet detects a file that is flagged as malicious in Cynet’s EPS (endpoint scanner) built-in threat intelligence database. This database contains only critical IoCs (such as IOCs of ransomware, hacking tools, etc.).
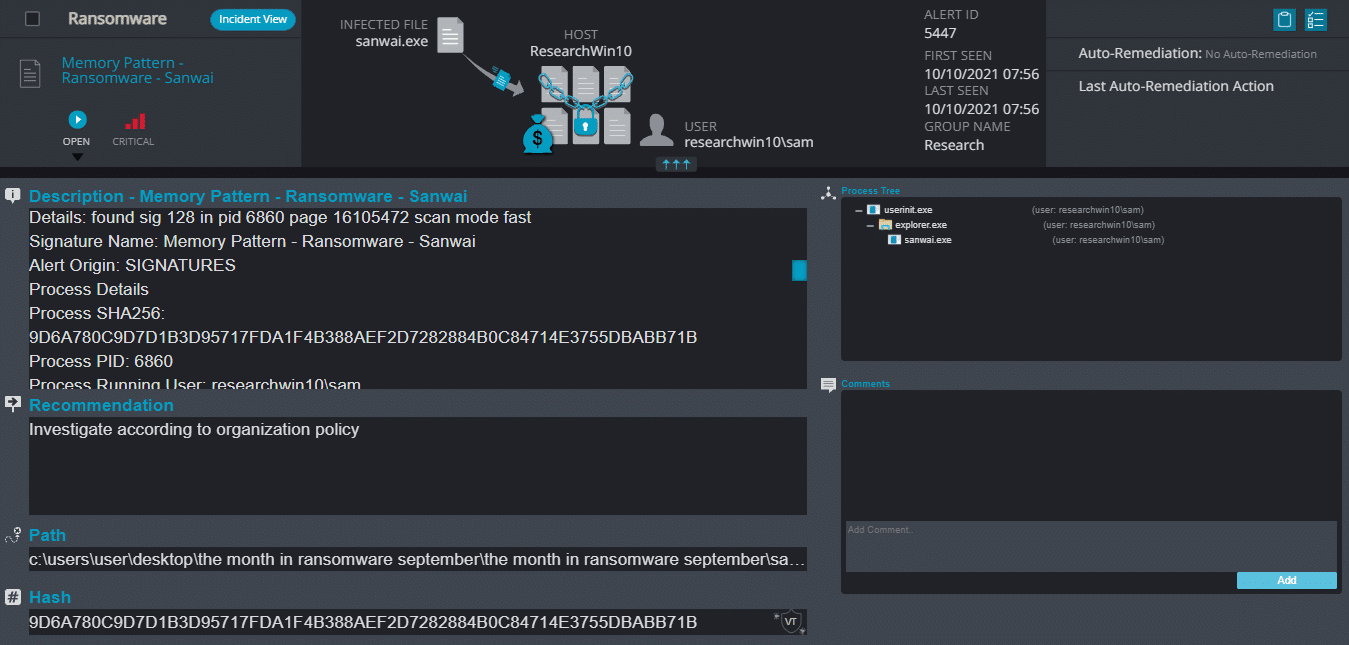
- Memory Pattern – This alert triggers when Cynet detects memory strings that are associated with Malware or with malicious files
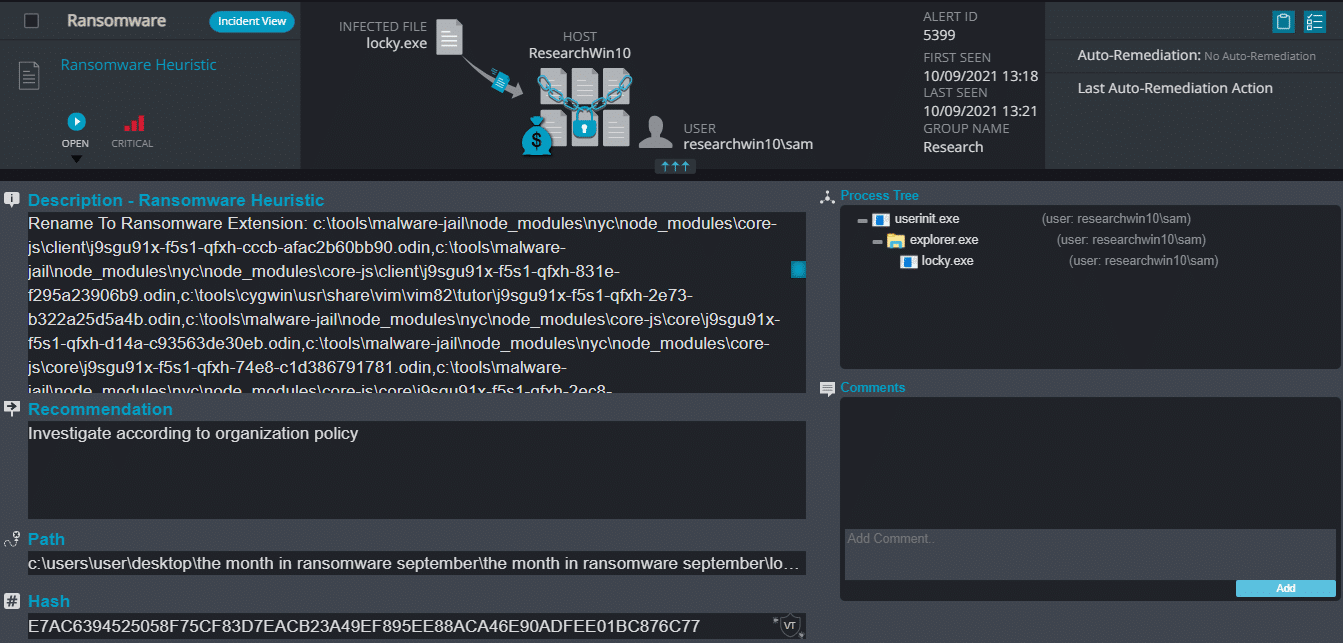
- Ransomware Heuristic – This alert triggers when Cynet detects suspicious behavior which can be associated with Ransomware (such as changing file extensions to “.Lock”).
- Malicious Binary – Process Create Malicious File – This alert triggers when Cynet detects a process that creates a file that is either flagged as malicious in Cynet’s Threat Intelligence database, or associated with suspicious patterns (such as loaded to sensitive directories).
- Process Monitoring – This alert triggers when a process runs with certain parameters which can indicate suspicious activity (for example, a vssadmin with suspicious parameters such as delete shadow copies).
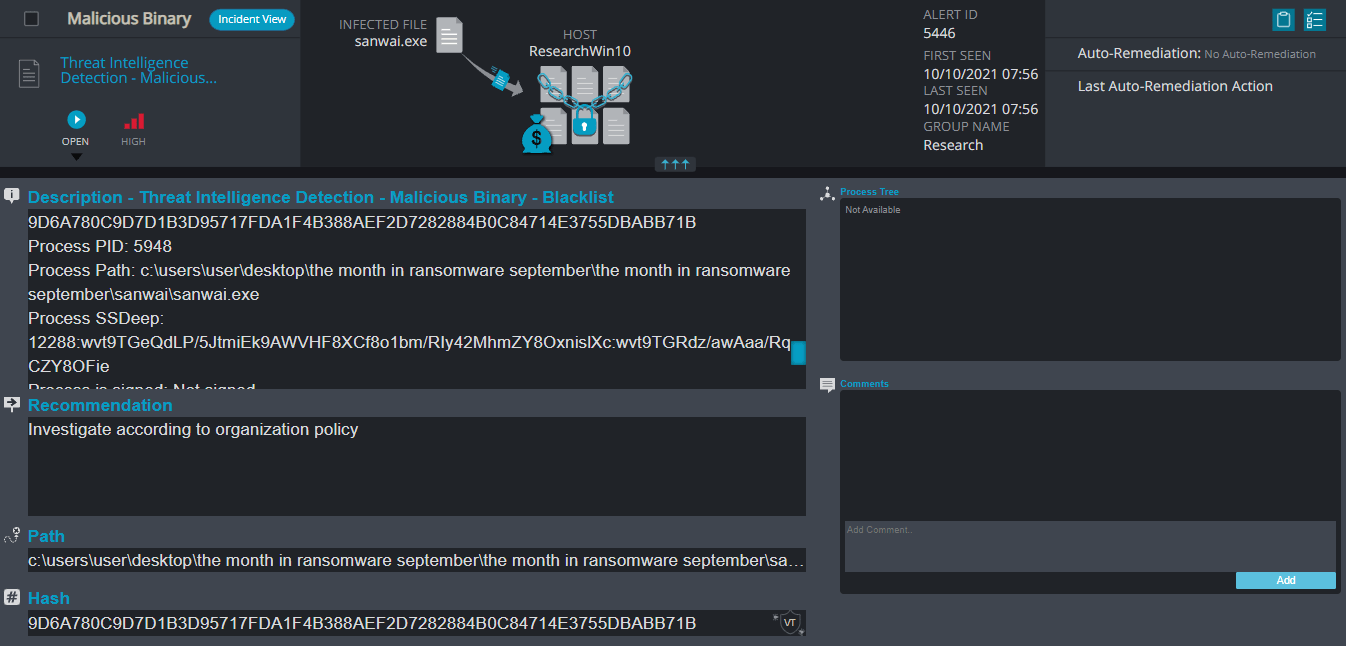
- Threat Intelligence Detection – Malicious Binary – This alert triggers when Cynet detects a file that is flagged as malicious in Cynet’s internal threat intelligence database.