What is the newest VMWare vulnerability?
As part of our ongoing threat intelligence efforts to discover emerging threats and vulnerabilities, the CyOps team would like to bring a new risk to your attention. The threat is associated with five vulnerable default plugins installed in VMWare vCenter Server. This vulnerability can be abused by threat actors to remotely execute arbitrary code.
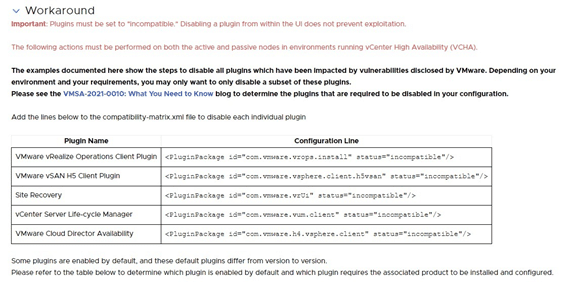
- Virtual SAN Health Check
- vRealize Operations Manager
- Site Recovery
- vSphere Lifecycle Manager
- VMware Cloud Director Availability
The vulnerabilities described above are assigned to the following CVEs:
- CVE-2021-21972 – VMSA-2021-0002 – vRealize Operations Manager Plugin
- CVE-2021-21985 – VMSA-2021-0010 – Virtual SAN Health Check Plugin
- CVE-2021-21986 – VMSA-2021-0010 – Virtual SAN Health Check, Site Recovery, vSphere Lifecycle Manager, and VMware Cloud Director Availability Plugins
All CVEs mentioned above allow a malicious actor to perform remote code execution on the hosting Operating System without privilege limitations. This can be achieved when an adversary has network access by using port 443 to infiltrate the vCenter Server.
Following VMware’s instructions, below is a summary of a workaround to temporarily prevent exploitation until a patch is released:
Apart from our recommendation to disable the mentioned plugins as described above, you can rest assured that the Cynet CyOps team is constantly monitoring your environment and will update if we observe and detect suspicious behavior or activities.