Protector™
Prevention, Detection, IT & Security Operations
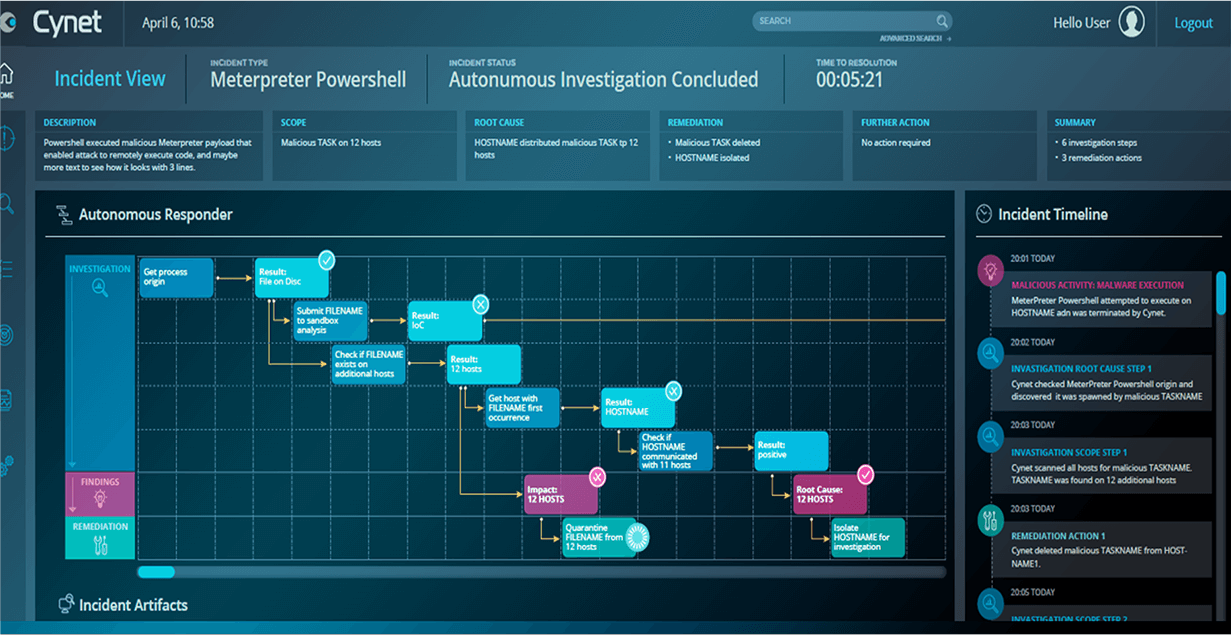
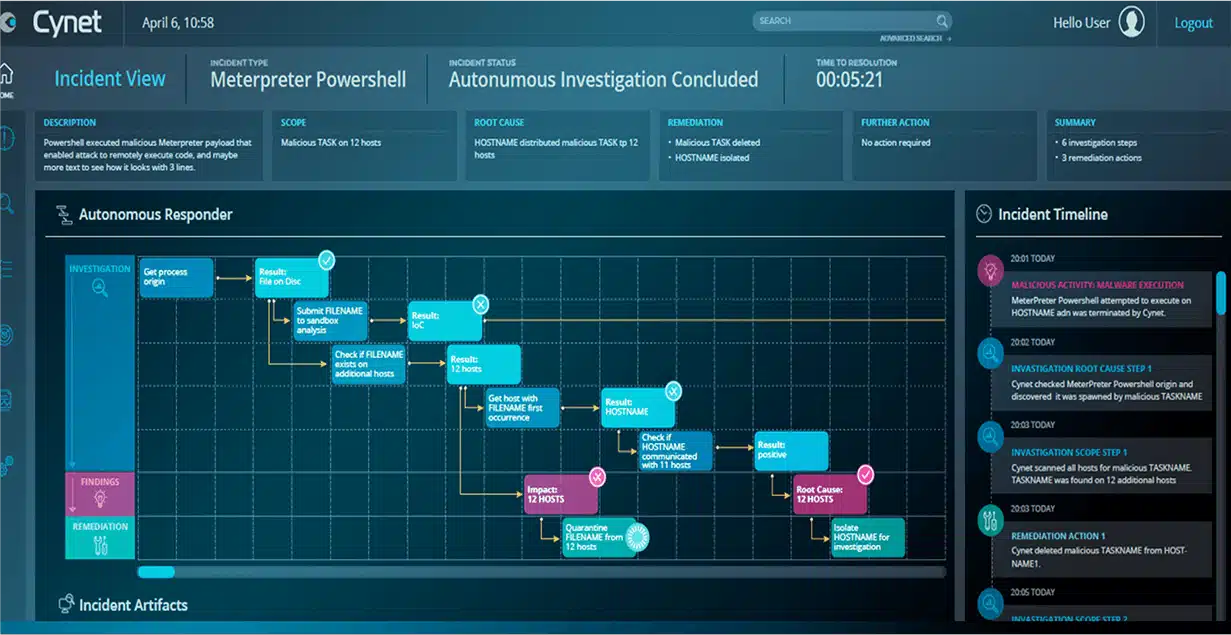
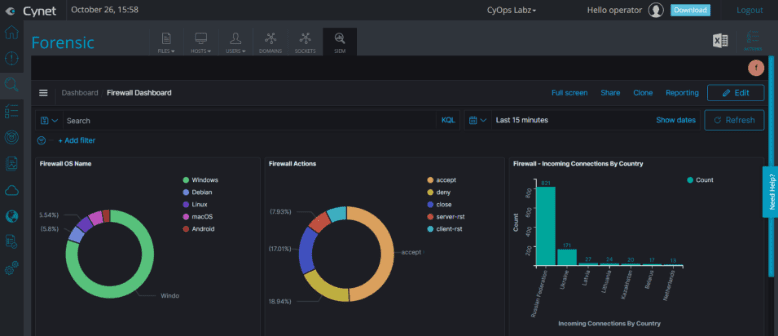
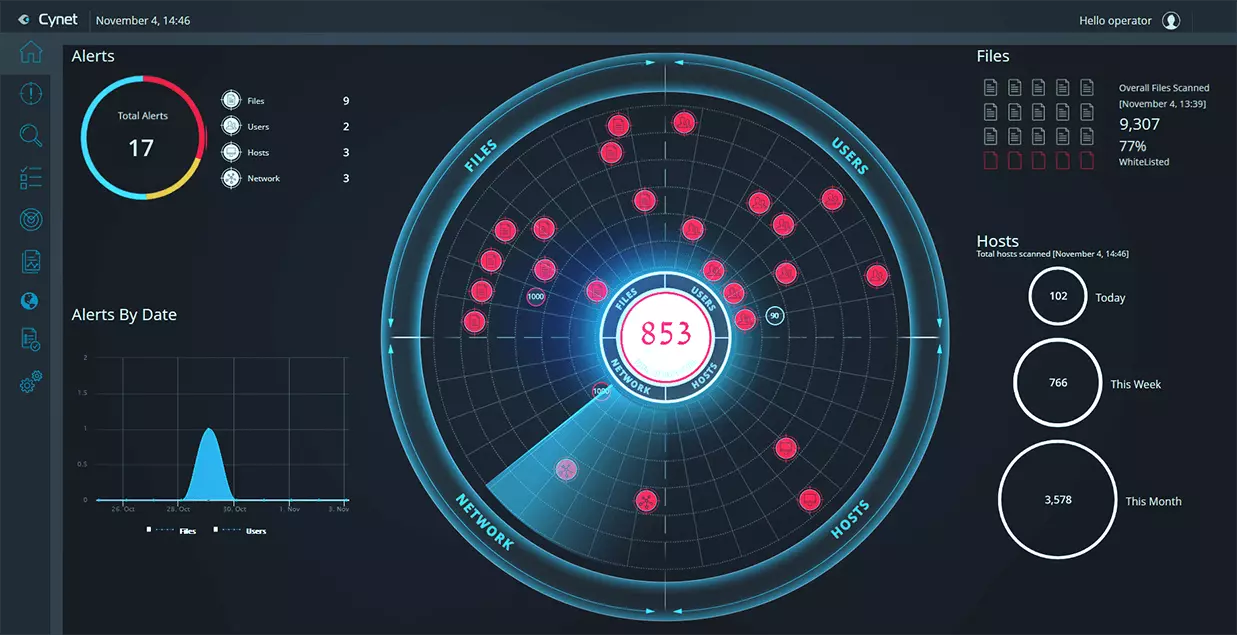
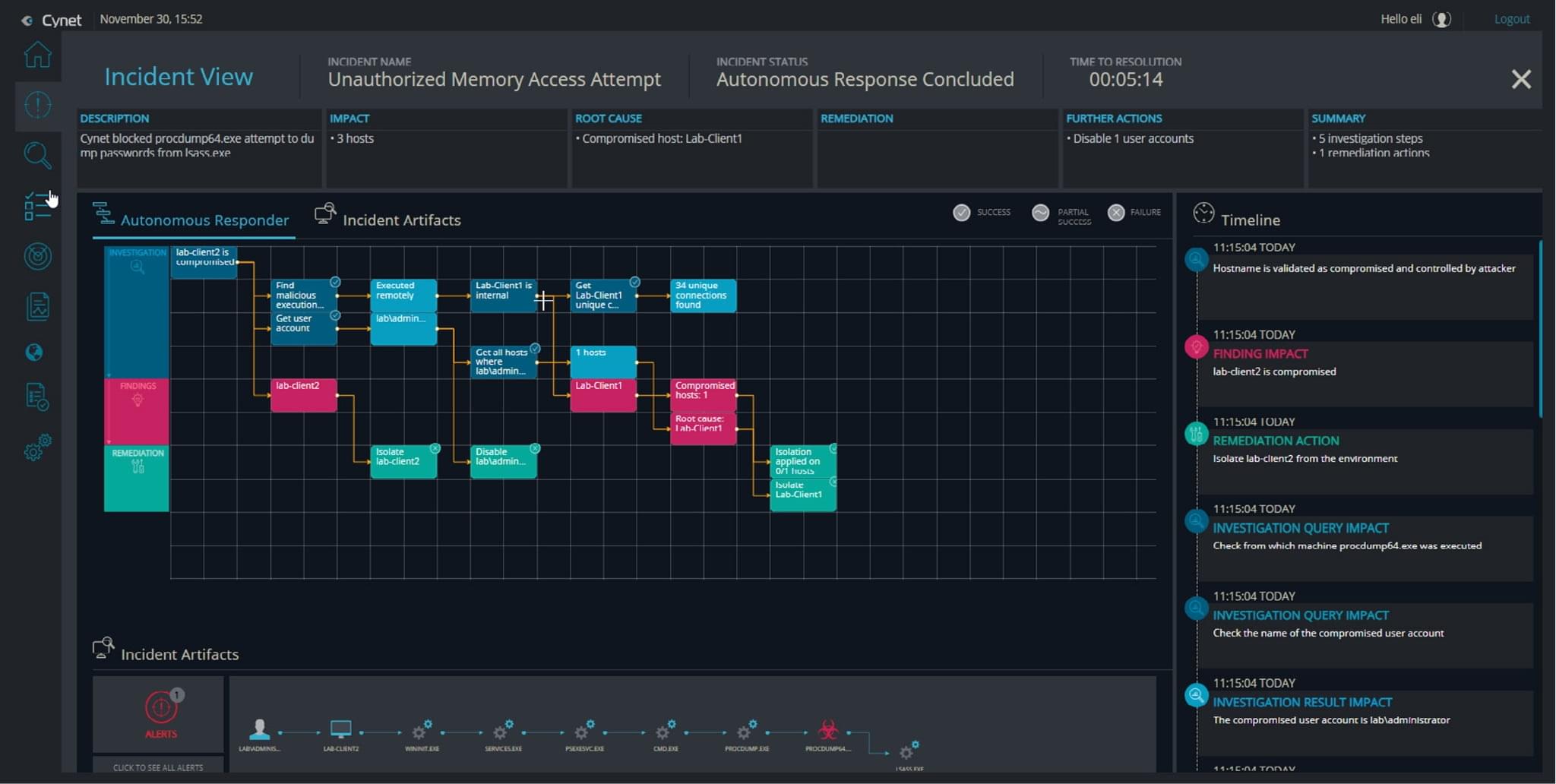
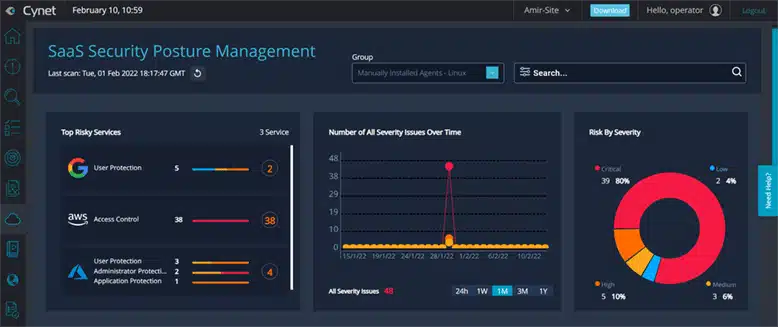
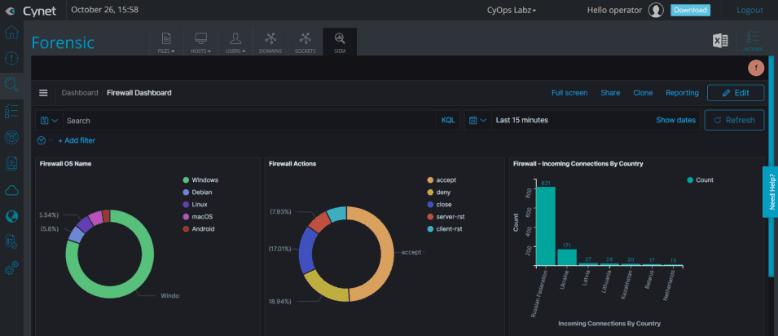
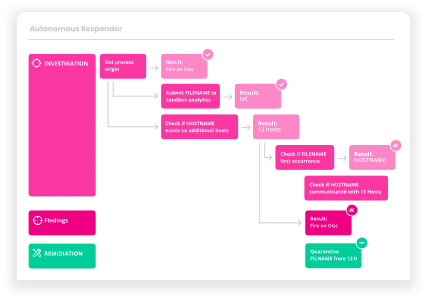
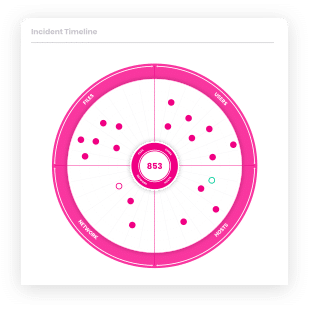
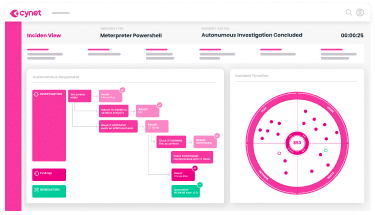
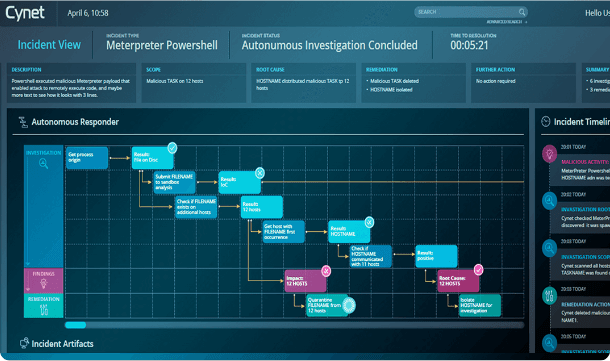
Cynet natively delivers all the prevention, detection and operational capabilities you need out of the box in a single, easy to use platform for end-to-end protection across your environment.