See Everything
Extended visibility to prevent and detect threats across your environment.
Search results for:
Introducing the modern approach to cybersecurity: All the prevention, detection, correlation, investigation, and response you need backed by a 24/7 MDR service – without the cost and complexity. Free your security team from constant pressure by automating their day-to-day cybersecurity operations.
Request a DemoExtended visibility to prevent and detect threats across your environment.
A 24/7 complementary MDR service proactively monitoring your environment and providing needed advice.
Collect and correlate alerts and related data to identify suspicious or problematic activity.
Ensure your SaaS applications aren’t introducing security risks.
Fully automate threat investigation and remediation actions across your environment.
All the protections you need out-of-the-box on a single, fully integrated platform.
Prevention, Detection, IT & Security Operations
Prevent and detect threats across your environment, reduce SaaS application risk, and have all operational capabilities you need out of the box in a single, easy to use platform for end-to-end protection across your environment.
Explore protector™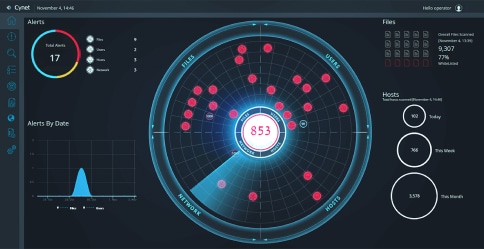
Natively monitor endpoints, networks, users, and decoy beacons to detect even the most stealthy threats.
Extensive operational functions natively included such as Sandboxing, Vulnerability Management, and Forensics.
Monitor and correct SaaS application configuration errors to eliminate SaaS security risks.
Prevent dangerous endpoint threats with NGAV and device control.
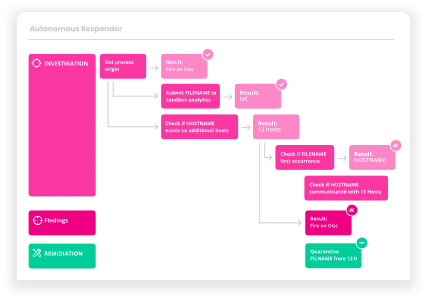
Automated Investigation and Response
Gain key capabilities of SOAR by fully automating all required response actions to reduce the burden and augment the skills of your overworked security team.
Explore Protector™
Automate comprehensive, multi-action responses across your environment for any attack scenario.
Eliminate malicious presence, activity, and infrastructure across users, network, endpoints, and other IT components.
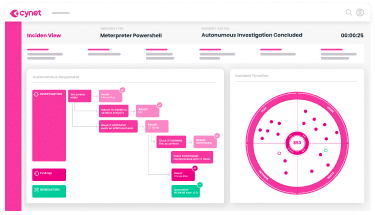
Automatically determine the root cause and scope of an attack across your environment.
Intuitive graphical timeline and layout of attacks, along with the automated investigation and response actions.
Log Management and Event Correlation
Gain the key capabilities of SIEM by integrating and correlating alert and activity data into actionable incidents to uncover threats across your environment.
EXPLORE CORELATOR™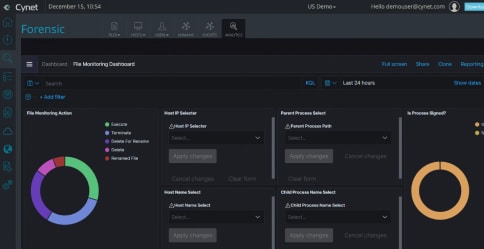
Centralize important log data to uncover hidden threats with full visibility and powerful analysis tools.
Integrate, normalize, analyze, and prioritize signals from native Cynet controls, system logs, and third-party controls.
Investigate threats and conduct threat hunting with instant access to forensic artifacts.
Gain full access to a world-class managed security service at no additional cost.
Explore CyOps™ MDRCyOps proactively monitors your environment, prioritizes, and notifies you of critical alerts.
CyOps searches for malicious artifacts and IoCs within your environment.
Dedicated help that provides you with speedy answers and also ensures that your systems will be kept secure after the incident.
All the reports you need including executive-level summary and overview of malware analysis performed.


“We don’t have to worry about that side of our security as much, which is a load off our minds and allows us to do what we need to do to help the firm” David Michel , Becker - CIOWatch Video
Let’s get started
Ready to extend visibility, threat detection and response?
Prefer a one-on-one demo? Click here
By clicking next I consent to the use of my personal data by Cynet in accordance with Cynet's Privacy Policy and by its partners