Search results for:
Endpoint Protection Platforms (EPP) are essential to defend your organization’s workstations, mobile devices, servers and containers. Modern endpoint security solutions include advanced preventative measures, such as Next-Generation Antivirus which can block both known and unknown malware, and active defensive measures known as Endpoint Detection and Response (EDR) .
In this page we’ll provide an introduction to endpoint protection, help you understand the criteria for selecting and evaluating EPPs, and review the top 6 EPP solutions, breaking down their capabilities into preventive and EDR features.
This is part of an extensive series of guides about data security.
Endpoint protection refers to the methods used to protect endpoint devices like desktops, laptops, smartphones, and tablets from cybersecurity threats. Organizations implement endpoint protection systems to protect the devices used by employees, in-house servers, and cloud computing resources.
All devices connecting to an enterprise network represent a security risk regarding endpoint vulnerabilities, which malicious actors could potentially exploit to infiltrate the network. Hackers routinely exploit endpoints as a convenient entry point to their target systems, installing malware and stealing sensitive information or taking control over the network.
Regardless of the device model implemented in an organization (i.e., BYOD, remote access, etc.), security admins must ensure the right tools are in place to identify and block security threats and to initiate a rapid response when a threat escalates into a breach.
Most endpoint protection solutions use one of the following deployment models:
Most vendors provide endpoint protection as a package of solutions called an endpoint protection platform (EPP). An EPP typically include multiple security tools including these primary components:
Next-Generation Antivirus (NGAV)
NGAV augments traditional signature-based antivirus with behavioral analysis that can detect new and unknown threats. It helps protect networks against zero day malware, fileless malware, ransomware, and other sophisticated threats.
Advanced detection technology
Advanced EPP solutions provide detection capabilities including file integrity monitoring (FIM) that can identify suspicious changes to files, behavioral analysis, vulnerability assessments, deception technology that creates decoys for attackers to target, and integration with threat intelligence.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a class of security tools designed to monitor and log activity on endpoints, detect suspicious behavior and security risks, and enable security teams to respond to internal and external threats. It gives security analysts visibility and remote access to investigate threats in real time, identify the root cause, and eradicate the threat.
Many organizations are adopting eXtended Detection and Response (XDR) , an evolution of EDR solutions that helps teams detect and respond to attacks across endpoints, networks, email systems, cloud environments, and more.
Managed Detection and Response (MDR)
Many organizations lack the expert security staff to operate EPP and EDR solutions. Therefore, many EPP vendors offer managed detection and response (MDR) services either directly or through a partner. These services provide access to the vendor’s security operations center (SOC). Outsourced SOC experts can perform threat hunting to proactively discover threats in the customer’s environment, and incident response to identify and react to security incidents as they occur.
EPP solutions include the following features and capabilities:
| Malware protection | Protects against known and unknown malware variants. |
| Protection from exploits | Prevents zero-day vulnerabilities and known software vulnerabilities |
| Email threats protection | Scans email attachments, detects and blocks malicious payloads |
| Downloads protection | Prevents unintentional user download of malicious files and drive-by downloads |
| Application Control | Enables whitelisting and blacklisting of applications on the endpoint |
| Behavior Analysis | Monitors behavior of the endpoint and uses machine learning techniques to identify suspicious activity |
| Endpoint Detection and Response (EDR) | Provides visibility into security incidents on the endpoint and gives security teams the tools to investigate and respond to them |
| Data Loss Prevention (DLP) | Prevents insider threats focused on data theft and exfiltration attempts by external attackers |
Learn more in our detailed guide to epp security.
Operating system support: Windows, Mac, Linux
Prevention features: Next-Generation Antivirus (NGAV) that blocks malware, exploits, LOLBins, Macros, malicious scripts, and other malicious payloads. Zero-day protection using User and Entity Behavior Analytics (UEBA) to detect and block suspicious activity. Asset management, endpoint vulnerability assessments and application control, with auditing, logging and monitoring. Deception technology lures attackers to a honeypot, gathering useful intelligence about attack techniques. Network analytics identifies lateral movement, suspicious connections and logins.
EDR features: Advanced endpoint threat detection predicts attacker behavior based on continuous monitoring of endpoints and behavioral analysis. Searches and reviews historic or current incident data on endpoints to help investigate threats and validate alerts, for faster remediation. Automatic response orchestration and manual remediation of threats on endpoints. Deployment across thousands of endpoints within two hours.
Operating system support: Windows 7, 8, 10, Windows Server 2012, 2016, 2019, MacOS, Azure, Amazon Workspaces, VMware WS, ESX, ESXi, XenServer, Oracle VirtualBox
Prevention features: Antivirus, firewall and intrusion prevention, application and device control including file, registry and device access, application whitelisting and blacklisting, automated device erasure, enforcing policy on hosts, system lockdown.
EDR features: Symantec Endpoint Protection offers Targeted Attack Analytics (TAA) with local and global telemetry, machine learning analysis of device behavior, threat intelligence. Assist with attack investigation, containment and resolution.
Source: Microsoft
Operating system support: Windows, Mac, Linux, CentOS
Prevention features: Built-in vulnerability management with remediation capabilities. Attack surface reduction by ensuring secure configuration and applying exploit mitigation techniques, next-generation antivirus protection for emerging threats. Automatic investigation capabilities that reduce the volume of alerts. Microsoft Secure Score for Devices helps identify the security state of the entire network and identify unprotected systems.
EDR features: Endpoint behavioral sensors, embedded in Windows 10, collect and process behavioral signals from the operating system and send it to a private cloud instance of Defender for Endpoint. The solution uses big data, device learning, and unique metrics from all Microsoft products and online assets, translating behavioral signals into detections and recommended responses. Integrates threat from Microsoft and data partners. Includes a managed threat hunting service that provides proactive hunting and prioritization to identify and respond to advanced threats.
Protection features: behavior classification for detecting zero-day threats, adaptive scanning for malware and other threats, next-gen anti-malware engine, safe browsing with web protection and filtering, prevents ransomware and grayware, integrated firewall blocks network attacks.
Endpoint detection and response features: threat data processing to minimize alert fatigue; improved observability with continuous monitoring and data collection; detection and response for advanced persistent threats (APTs); alignment with MITRE ATT&CK techniques and tactics alignment; Trellicts Insights feature performs proactive prioritization of threats, and predicting if existing protection measures are effective against them.
Operating system support: Windows, Linux, MacOS, Virtualization
Prevention features: Protects against trojans, worms, backdoors, fileless attacks, malicious documents (Office, Adobe, Macros, spear phishing), browser vulnerabilities (Java, JavaSCRIPT, IFrame, plugins), download protection, script-base attacks (PowerShell, WMI, PowerSploit), credentials-based and token attacks.
EDR features: Tracks all activity on endpoints, contextualizes and identifies suspicious activity in real time, enables rapid response and rollback to last known good configuration, advanced threat hunting with full context of security incident forensics.
Operating system support: Windows and MacOs
Prevention features:
EDR features (EDR offered as separate product):
Don’t take vendor claims as a given. Take your EPP solution of choice for a spin before you by. Try some of these to test EPP capabilities for yourself:
Cynet 360 is a security solution that includes a complete EPP offering, including NGAV, device firewall, advanced EDR capabilities and automated incident response. Cynet 360 is a complete security solution that goes beyond endpoint protection, offering network analytics, UEBA and deception technology.
Cynet’s platform includes:
Learn more about the Cynet 360 security platform.
Endpoint Protection: The Basics and 4 Key Technologies
Endpoint protection is a set of tools and practices that allow organizations to defend endpoints against cyber attacks. Any device connected to a network is considered an endpoint. Workplace devices such as servers and printers are endpoints, as well as bring-your-own-device (BYOD) items like laptops, mobile devices, and tablets. Cloud servers, Internet of Things (IoT) devices such as smart watches, medical devices, and ATM machines are also endpoints.
Understand how endpoint protection works and discover four key technologies that make up modern endpoint protection: NGAV, EDR, response automation, and XDR.
Read more: Endpoint Protection: The Basics and 4 Key Technologies
Gartner Endpoint Protection: Quick Takeaways and MQ Vendors
The Gartner Endpoint Protection Magic Quadrant covers the endpoint security market, and in particular endpoint protection platforms (EPP) , which deploy agents or sensors on organizational endpoints.
Get a summary of the Gartner Endpoint Protection Magic Quadrant and a quick review of vendors covered in the Magic Quadrant report.
Read more: Gartner Endpoint Protection: Quick Takeaways and MQ Vendors
Cloud Endpoint Protection: Protecting Your Weakest Link
In recent years, research has shown that a majority of cyber attacks start by compromising an endpoint, not by breaching an organization’s security perimeter. Many organizations are deploying endpoint security platforms that defend against endpoint attacks using next-generation antivirus (NGAV), endpoint detection and response (EDR), User Behavioral Analytics (UBA) and more.
Learn about the importance of endpoint protection for cloud workloads, and the threats facing endpoints in the private, hybrid, and public cloud.
Read more: Cloud Endpoint Protection: Protecting Your Weakest Link
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of data security.
Authored by Cynet
Authored by Cynet
Authored by HackerOne
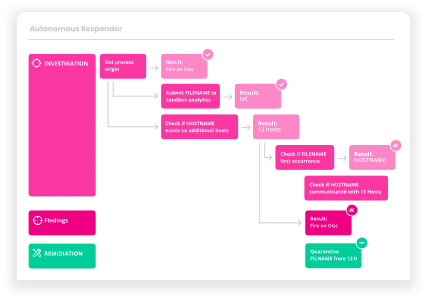
Let’s get started
Ready to extend visibility, threat detection and response?
Prefer a one-on-one demo? Click here
By clicking next I consent to the use of my personal data by Cynet in accordance with Cynet's Privacy Policy and by its partners