Cynet’s MITRE ATT&CK Evaluations Results
Enterprise Evaluation 2024
Enterprise Evaluation 2024
Cynet delivers 100% protection and 100% detection visibility with zero configuration changes and zero delayed detections.
77 of 77 Attack Sub-Steps
with no configuration changes
10/10 Malicious Steps
Blocked
77 of 77 Technique level Detections
with no configuration changes
0 of 20 Legitimate Sub-Steps Flagged as Malicious
Selecting the right cybersecurity tech for your organization isn’t easy. Fortunately, MITRE developed a testing methodology to objectively evaluate endpoint security solutions based on the MITRE ATT&CK framework.
The 2024 MITRE ATT&CK Evaluations focused on replicating the techniques of notorious adversaries, including groups like CL0P, LockBit, and DPRK (North Korea), providing organizations with valuable insights into how endpoint solutions handle advanced and evolving cyber threats.
MITRE doesn’t rank or score participant results. Instead, the raw test data is published along with some basic online comparison tools. It’s up to the vendor participants to analyze and present their results. MITRE does not interpret results or confirm participants’ evaluations of their results.
Use the MITRE ATT&CK results to help you
determine if a vendor can meet your specific needs.
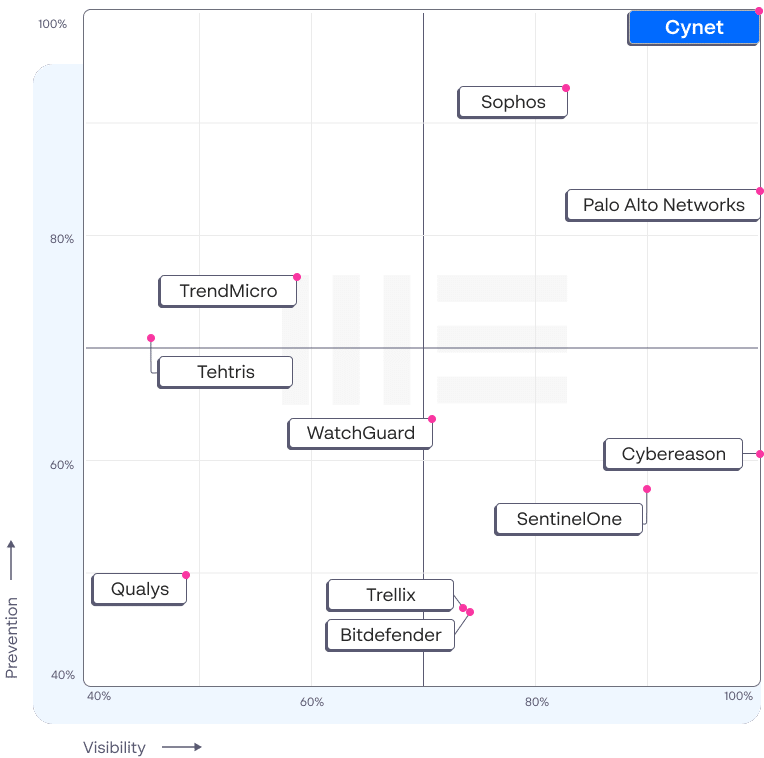
Cynet is the only vendor that delivered BOTH 100% Visibility and 100% Protection with no configuration changes!
Perfectly detecting every attack action using no configuration changes and no delays.
Blocked every one of the 10 attacks steps – allowing no malicious activity to execute!
Search results for: