Threats don’t wait. Neither do we.
Cynet is faster than
Cynet delivers the only unified, AI-powered cybersecurity platform backed 24x7 by MDR experts. Get complete protection, simplified operations, and peace of mind.
14-day Free Trial. No credit card required.
Three Years Running of Elite Performance in MITRE ATT&CK Evaluations
This year’s evaluation pushed vendors through rigorous adversary emulations and expanded across Windows, Linux, and AWS-cloud environment scenarios. Review the results and see how the industry’s top solutions stack up in visibility, speed, accuracy, and real-time protection.
Detection Visibility
Protection
Technique-Level Coverage
Detection False Positives
Industry Trusted. Customer Loved
Thousands of Organizations Secured
Recommended by 95%
-
4.8/5Overall Rating
-
4.8/5Product Capabilities Rating
-
4.8/5Ease of Deployment Rating
Outstanding results in 2025 MITRE

-
100%Detection Visibility
-
100%Protection
-
100%Technique-Level Coverage
-
0Detection False Positives
Top-tier performance according to our users
-
98%Score for Real-Time Detection
-
97%Score for 24x7 Support
-
98%Score for Automated Remediation



The Cynet Advantage
-
Unified
One platform, one agent, one console that consolidates tools and delivers full protection without complexity.
-
Human-Backed
CyOps 24x7 MDR security experts work as part of your team, ensuring no threat is missed and no organization is left unprotected.
-
AI-Powered
CyAI continuously learns and adapts to the rapidly changing attack landscape, automatically stopping 90% of advanced threats while improving operational efficiency.
-
Proven
Outstanding 100% detection, protection, and technique-level coverage results in MITRE ATT&CK evaluations and 95% CSAT proves what the industry already knows: Cynet delivers results.
Why Cynet?
Unified. Intelligent. Automated.
One AI-Powered Platform for Complete Protection.
Cynet consolidates critical cybersecurity functions into a single, AI-powered platform that simplifies protection without sacrificing performance.
-
Integrations and APIs
Orchestrate detection and response with hundreds of APIs and 80+ pre-built integrations across 50+ data sources.
-
CyAI
Our native machine learning engine automatically detects and remediates 90% of threats in under one second.
-
SOAR Automation
Pre-built playbooks and automated workflows that reduce manual effort.
-
CyOps 24x7 MDR
A dedicated team of security experts monitoring, investigating, and responding around the clock.
-
Simple Management
A single, intuitive, multi-tenant console provides full visibility and control across the organization.

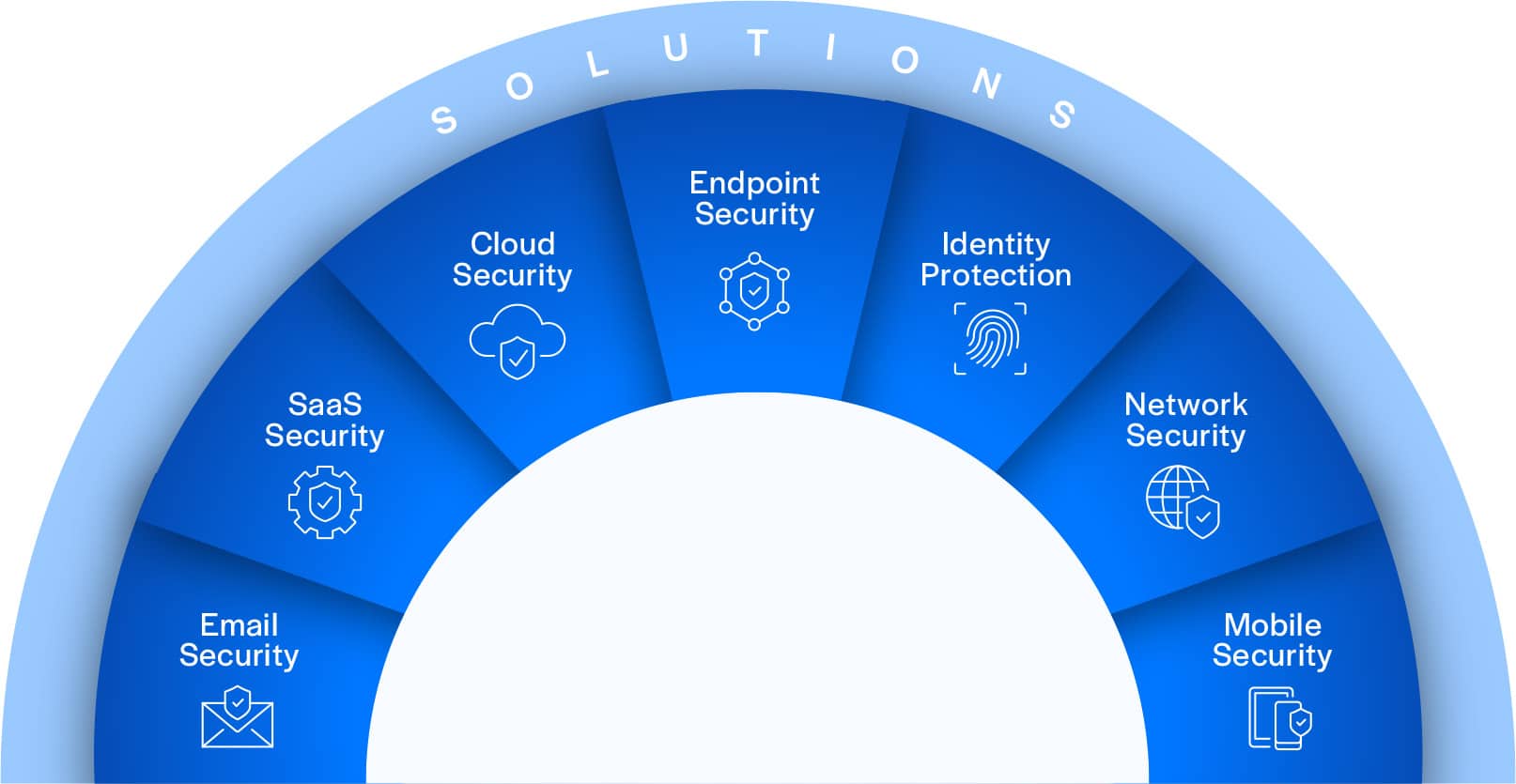
Solutions Purpose-Built for Every Threat
Attackers move faster than ever, continuously evolving their tactics to exploit any gap. Unified protection across all vectors is the only way to stop them.
-
Endpoints
Prevent, detect, and remediate threats automatically
-
Users & Identity
Stop credential theft and lateral movement
-
Email
Block phishing and malicious attachments
-
Network
Detect and isolate suspicious traffic instantly
-
Cloud & SaaS
Identify misconfigurations and risks before attackers do
-
Mobile
Extend protection to every device
Metrics
AI Speed. Human Precision. Real Results.
customer satisfaction
MITRE-Validated Detection, Protection, and Technique Coverage with zero false positives
of advanced threats remediated automatically
detection to full containment
The Always-On Security Team
24x7 MDR Security Experts
CyOps is Cynet’s global team of MDR security experts who monitor, analyze, and respond to threats in real time. Acting as an extension of your team, they provide 24x7 coverage, proactive threat hunting, and guided remediation.

The AI SOC Agent
CyAI is the brain of Cynet’s unified platform. It continuously learns from millions of real-world threat samples to predict, detect, and stop threats faster than traditional systems.
From identifying zero-days before they execute to automatically remediating complex attacks, CyAI delivers the precision and speed needed to outpace modern adversaries.
Built for Security.
Certified for Compliance.
Cynet helps organizations meet and maintain compliance with major standards including SOC 2 Type 2, ISO 27001, NIST CSF, HIPAA, PCI DSS, DFARS, CMMC, NIS2, and DORA.
Every Cynet capability is designed to strengthen resilience, simplify audits, and prove continuous protection.










Ready to Simplify Security and Amplify Protection?
See why organizations worldwide trust Cynet to deliver unified protection backed by 24x7 MDR experts.


