Secure every user. Protect every identity.
Identity Security
Real-time ITDR requires unifying identity telemetry across endpoints, cloud, mobile, on-prem, and more. Cynet unifies identity, cloud, and endpoint defenses in one platform, delivering instant detection and automated response that log-only systems can’t match.
of successful data breaches stem from compromised login credentials
breaches in 2025 involved AI-driven attacks
of cloud NHIs have no identifiable owner, making them incredibly vulnerable
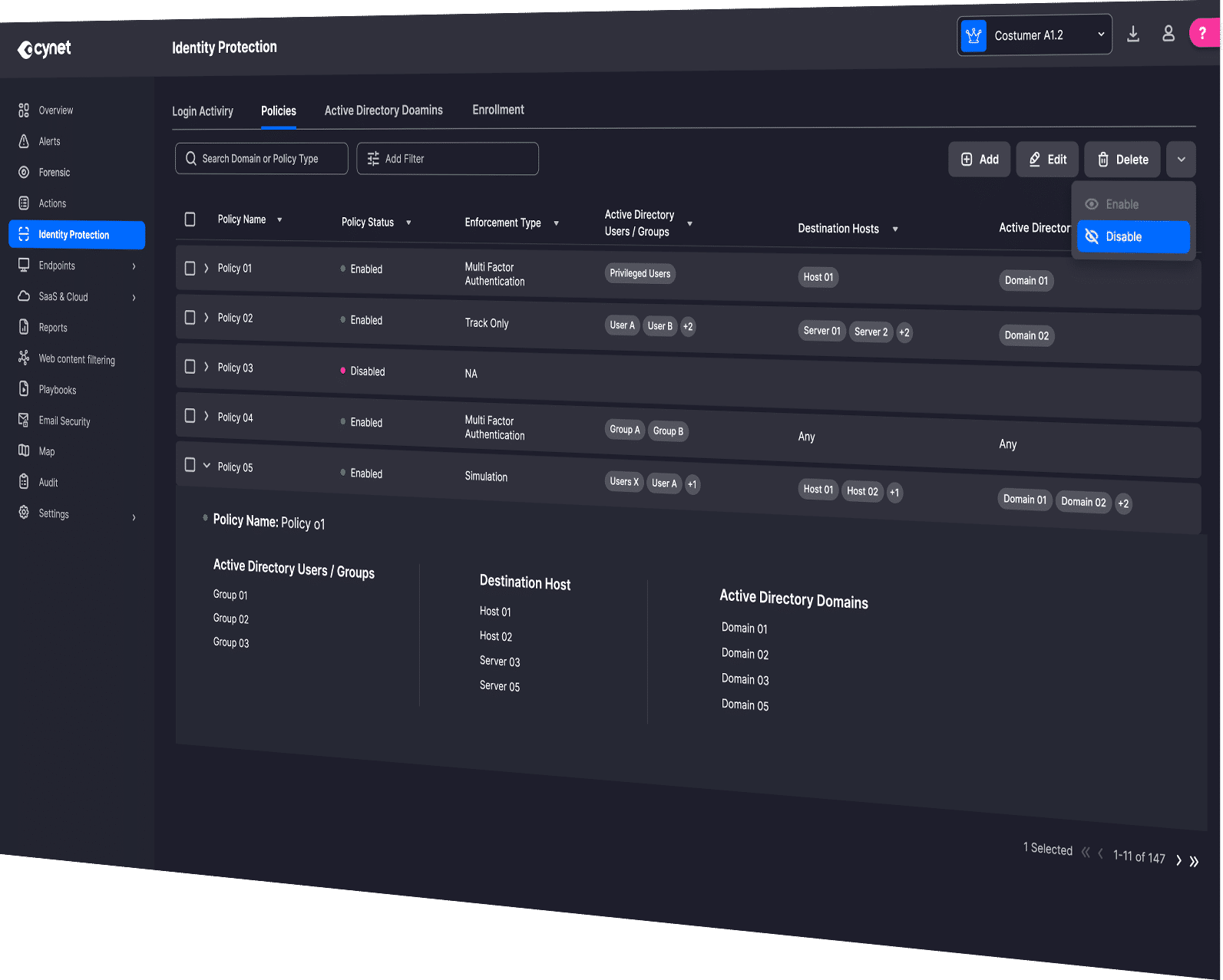
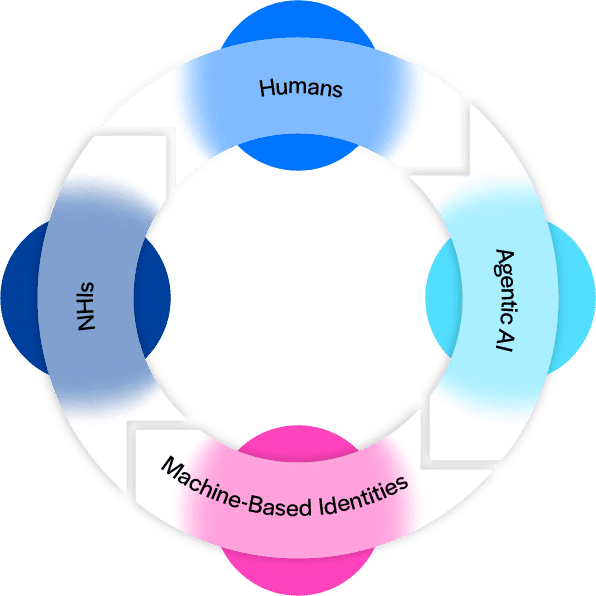
The Expanding Definition of Identity
Online identity is no longer just for humans. It now helps define non-human identities (NHI), AI agents, and machine-based identities.
And with each of these identity types, comes another endpoint and potential attack vector.
Identity Threat Detection and Response (ITDR)
Cynet leverages native endpoint and identity telemetry for instant detection and automated response, stopping privilege escalation and lateral movement before damage occurs.
One agent. One console. Complete protection.
-
Identity-Driven Security Insights
Correlates user, endpoint, and network behaviors to identify compromised accounts and malicious insider actions.
-
Behavior Anomaly Detection
Integrates identity data from Microsoft 365, Azure AD, Fortigate VPN, and other sources with endpoint and network telemetry for complete visibility.
-
Automated Response
Instantly disables compromised Active Directory or Microsoft 365 users and isolates affected endpoints through ProActive CyOps authorization.
-
Credential Theft Protection
Monitors for stolen credentials via Lighthouse Credential Theft Monitoring, notifying you before adversaries act.
-
Built-in Investigation Forensics
Automatically generates clear attack timelines, associated indicators of compromise (IOCs), and remediation steps through CyAI and CyOps workflows.
User Behavior Analytics (UBA)
Continuously monitors user activity to pinpoint suspicious behaviors that are indicative of compromised accounts and malicious insiders.

-
Deception
Deploy decoy users and monitor for unauthorized access.
-
User Visibility
Visibility into all user activity and login events
-
Malicious User Identification
Rapidly detect suspicious user activities such as lateral movement, C&C activity, accessing bad domains, etc.
-
Lateral Movement Detection
Detect the use of compromised credentials accessing network assets.
-
User Threat Level
Continuously correlate user activities against other events — on endpoints, files and external network locations — to provide holistic information to determine real-time risk levels.
-
Real Time Activity Context
Continuously correlates user activities against other events — such as endpoints, files and external network locations — to determine real-time risk levels.
-
Anomaly Detection
Detect abnormal user behaviors such as lateral movement, C&C activity, accessing bad domains, etc.
Protect human identities by safeguarding credentials, endpoints, and communication channels.
-
EPP + EDR
Blocks credential theft, ransomware, and lateral movement by isolating compromised endpoints before logins or data are abused.
-
UBA
Tracks user behavior to flag risky logins, privilege misuse, or insider threats, revealing hijacked or misused accounts early.
-
Email Security
Protects company emails from phishing and weaponized attachments using layered detection and behavioral analysis.
-
CyOps 24x7 MDR
24x7 MDR security experts monitor all environments around the clock to ensure dangerous threats are not overlooked and properly addressed.
-
SOAR
Automates response by disabling users, resetting credentials, or isolating infected devices the instant an identity risk is detected.
Secure NHIs by continuously monitoring behavior, network traffic, and access activity.
-
XDR
Correlates endpoint, network, and IAM activity to detect misuse of service accounts or API tokens, instantly flagging risky actions.
-
CyAI
Predicts and blocks threats by analyzing millions of benign and malicious samples to identify anomalies before they execute.
-
CSPM/SSPM
Scans cloud and SaaS environments for exposed credentials, and risks to high-value accounts, then auto-remediates insecure configurations.
-
NDR
Identifies abnormal network activity from bots, APIs, and AI agents for high-fidelity detection of stealthy machine threats.
-
CLM
Collects and analyzes priority logs to surface anomalous bot or AI-agent behavior and isolate threats in real time.
-
SOAR
Automates defense by disabling service accounts, revoking API keys, or halting rogue processes when misuse is detected.
-
MDR (CyOps 24x7 team)
Human-in-the-loop analysts monitor NHI activity, validate anomalies, and deliver expert remediation 24x7.
Peace of Mind, Built for Every Identity

