What security leaders should know about the critical zero-day vulnerability in Citrix NetScaler ADC and NetScaler Gateway
Hackers have been exploiting critical vulnerability in Citrix NetScaler ADC and NetScaler Gateway since late August 2023. This vulnerability, known as CVE 2023-4966, allows an attacker to disclose sensitive information, such as session tokens, and potentially hijack existing authenticated sessions.
Citrix NetScaler ADC is an application delivery controller that optimizes the performance, availability, and security of web applications. Citrix NetScaler Gateway is a VPN appliance that enables secure access to any application from any device and location. Together, they are intended to offer a comprehensive solution for delivering and accessing applications across hybrid and multi-cloud environments.
In this blog post, we will unpack CVE 2023-4966, assessing how hackers could exploit it, and advising steps to stop it from affecting your organization.
What is CVE 2023-4966?
CVE 2023-4966 is a critical information disclosure vulnerability in the web application firewall (WAF) of Citrix NetScaler ADC and NetScaler Gateway. It allows hackers to “trick” the WAF that blocks malicious HTTP requests and other threats.
By sending specially crafted HTTP requests, attackers can cause a buffer overflow and access more memory than allowed. They can also obtain data that should remain secure, such as session tokens later use to hijack an authenticated user’s session.
CVE 2023-4966 affects Citrix NetScaler ADC and NetScaler Gateway devices that are configured as a gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or a virtual (AAA) server. All versions before October 10, 2023, are vulnerable.
CNA (CVE Numbering Authority) gives this vulnerability a score of 9.4 (critical) because the attacker can compromise resources outside the device, while NIST (National Institute of Standards and Technology) gives it a score of 7.5 (High).
How Hackers Exploit CVE 2023-4966
Various threat actors have exploited CVE 2023-4966 in the wild since late August 2023. Recently, the Cybersecurity and Infrastructure Security Agency (CISA) has added CVE 2023-4966 to its known exploited vulnerabilities catalog.
To exploit this vulnerability, attackers follow four steps:
- Craft a malicious HTTP request that can cause a buffer overflow.
- Send this HTTP request to a victim device vulnerable to CVE 2023-4966.
- Get a response from the server with the expected data plus some extra leaked data from the memory, including a session token.
- Use this session token to hijack an authenticated user’s sessions.
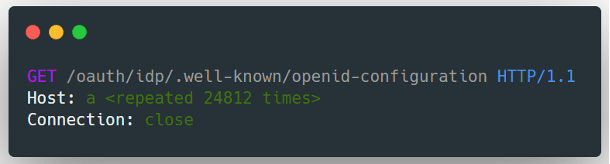
A Proof of Concept exploit of CVE 2023-4966 has surfaced. The POC started by setting the HTTP “Host header” to be a very long string of characters — “a” repeated 24,812 times. This made the buffer size too small for all the data:
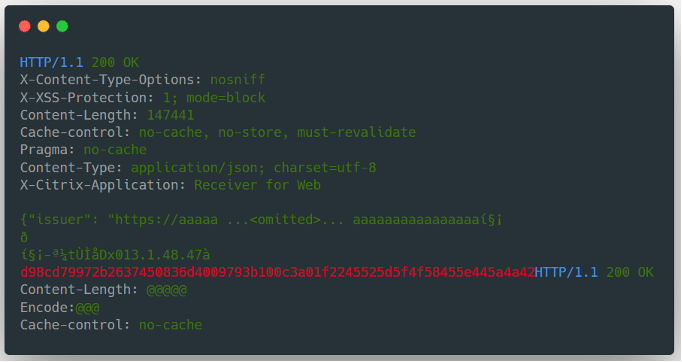
The request was sent to a vulnerable victim device, which responded with extra data from memory, including a session token (in red):
Eventually, they used the session token to hijack an authenticated user’s session.
Once an attacker hijacks an authenticated user’s session, they can perform many actions, including:
- Accessing internal resources and data.
- Stealing credentials, personal information or intellectual property.
- Moving laterally or escalate privileges within a network.
- Installing malware, ransomware or backdoors.
- Exfiltrating data or disrupt operations.
- Impersonating users and perform malicious actions.
Cynet employs a multi-layer logic approach, including static and behavioral rules, which should effectively detect and prevent any post-exploitation attempts.
However, it is imperative to mitigate this vulnerability as soon as possible.
How to Mitigate CVE 2023-4966?
The best way to mitigate CVE 2023-4966 is to apply the patches released by Citrix. These patches fix the buffer overflow vulnerability and prevent any unauthorized data disclosure or session hijacking.
However, more than patching alone is needed to ensure complete security. Citrix also recommends terminating all active and persistent sessions on the patched devices using the following commands:
kill icaconnection -all
kill rdp connection -all
kill pcoipConnection -all
kill aaa session -all
clear lb persistentSessions
These commands will invalidate any session tokens that may have been compromised by the exploitation of CVE 2023-4966.