Executive Summary
A threat actor observed exploiting CVE-2025-53770 and CVE-2025-53771 leading to remote code execution.
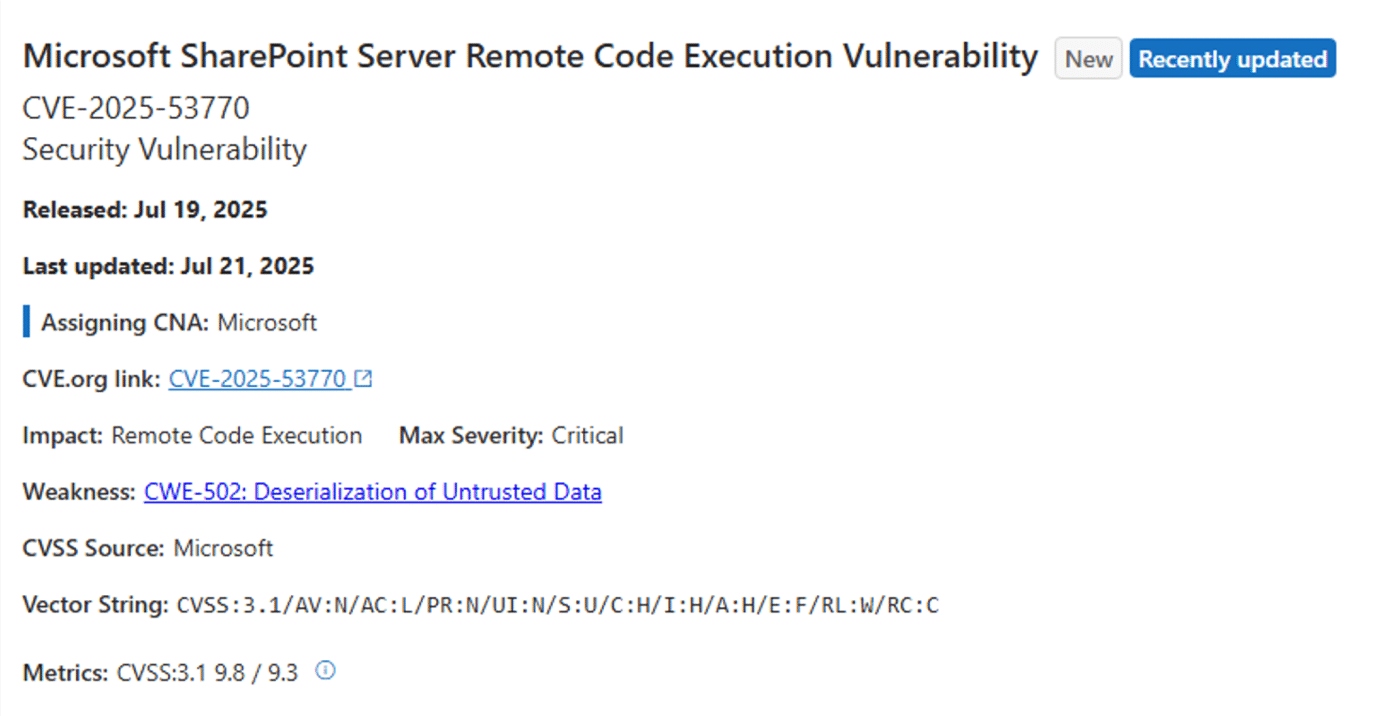
CVE-2025-53770 is a critical Remote Code Execution (RCE) Zero-Day vulnerability in on-premises Microsoft SharePoint Servers. It stems from the deserialization of untrusted data (CWE-502) and can be exploited remotely without authentication or user interaction, earning a CVSS score of 9.8. Microsoft has confirmed active exploitation in the wild, making this a high-priority issue for all affected organizations.
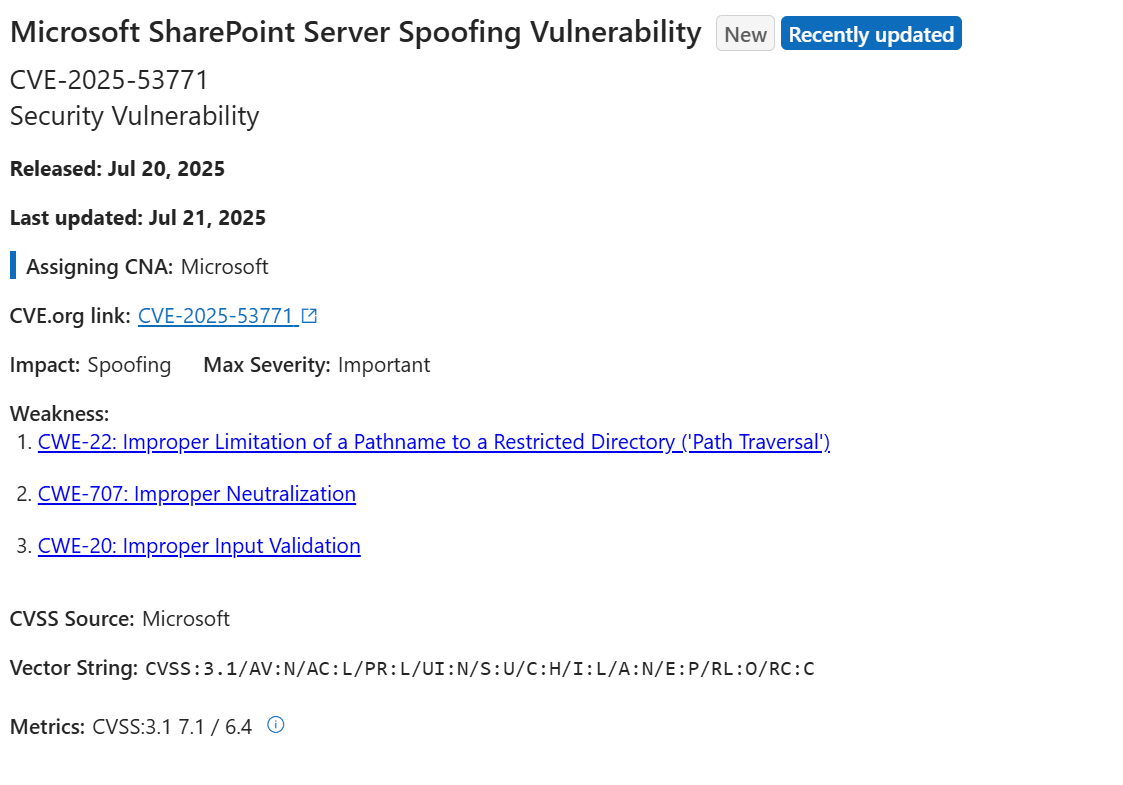
CVE-2025-53771 is a high-severity file write vulnerability found in on-premises Microsoft SharePoint Servers. This vulnerability arises from improper input validation, which can lead to a malicious dropping of a web shell (CWE-22, CWE-20). It can be exploited without any user interaction and has received a CVSS score of 7.1. Microsoft has confirmed that this vulnerability is actively being exploited in the wild, making it a high-priority issue for all affected organizations.
Impact & Risk:
- Severity: Rated Critical (CVSS 9.8) and High (CVSS 7.1).
- Affected Systems: Microsoft SharePoint 2016, 2019 and Subscription Edition (on-prem).
- Business Risk: Exploitation could lead to unauthorized system control, data exfiltration, and lateral movement within customer environments.
Cynet’s Response:
- Detections Deployed: The Research team, in collaboration with CyOps, has implemented enhanced detection across all protection layers to identify and alert exploitation attempts in real time.
- Active Monitoring: Continuous monitoring of customer environments is underway to detect any indicators.
Vulnerability Timeline
- July 19, 2025 – CVE publicly disclosed and initial guidance issued
- July 20, 2025 – Security updates released for:
- Microsoft SharePoint Server Subscription Edition
- Microsoft SharePoint Server 2019
- July 21, 2025 – Security updates released for:
- Microsoft SharePoint Server 2016
How CVE-2025-53770 and CVE-2025-53771 Work
CVE-2025-53770 is a critical, unauthenticated vulnerability with low complexity and high impact, enabling remote code execution in on-premises Microsoft SharePoint Server. This vulnerability is already being utilized in real-world attacks.
CVE-2025-53770 allows an unauthenticated threat actor to execute remote code by exploiting a deserialization vulnerability in the __VIEWSTATE field.
This vulnerability has been observed in the wild alongside CVE-2025-53771, which has been exploited in ways that provide complementary information to successfully exploit CVE-2025-53770.
CVE-2025-53771 is also an unauthenticated vulnerability with low complexity and high impact. It permits a threat actor to place a web shell in a web-accessible folder within the SharePoint server.
It is crucial to emphasize that threat actors are actively exploiting both vulnerabilities in the wild.
Threat Actor’s Activity and IOCs
This is a high-level explanation of the observed threat actor exploitation activity in the wild:
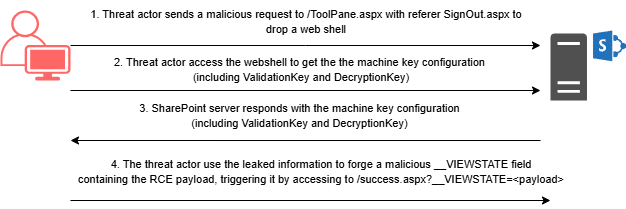
- The threat actor sends a malicious request to the ToolPane.aspx endpoint, triggering CVE-2025-53771 to drop a web shell. The referrer was set to SignOut.aspx to bypass authentication.
- The threat actor accesses the dropped web shell, which responds with the machine key configuration, containing among other things the ValidationKey and DecryptionKey, which are required to create a __VIEWSTATE.
- The threat actor generates a payload using ysoserial (that gets as a parameter the ValidationKey, DecryptionKey, and PowerShell payload) that drops a web shell named spinstall0.aspx to the web accessible layout folder and puts the payload in the __VIEWSTATE field.
Indicators of Compromise (IOCs)
- Web Shell File Creation Location:
- C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\15\TEMPLATE\LAYOUTS\
- C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\
- Known Web Shell Name:
- spinstall0.aspx
- Observed Malicious Process Tree
- w3wp.exe -> cmd.exe -> powershell.exe
- Malicious IPs:
- 107.191.58[.]76
- 104.238.159[.]149
- 96.9.125[.]147
- 45.77.155[.]170
- Malicious Web Shell File (SHA256):
- 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
- 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
- 27c45b8ed7b8a7e5fff473b50c24028bd028a9fe8e25e5cea2bf5e676e531014
- 8d3d3f3a17d233bc8562765e61f7314ca7a08130ac0fb153ffd091612920b0f2
- b336f936be13b3d01a8544ea3906193608022b40c28dd8f1f281e361c9b64e93
Cynet All-in-One platform provides Threat Hunting capabilities that allow hunting the above IOCs:
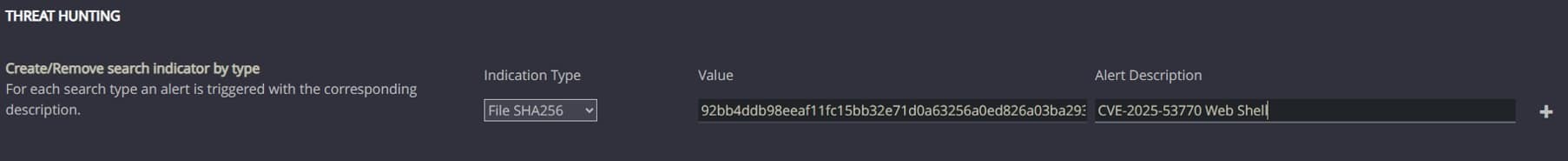
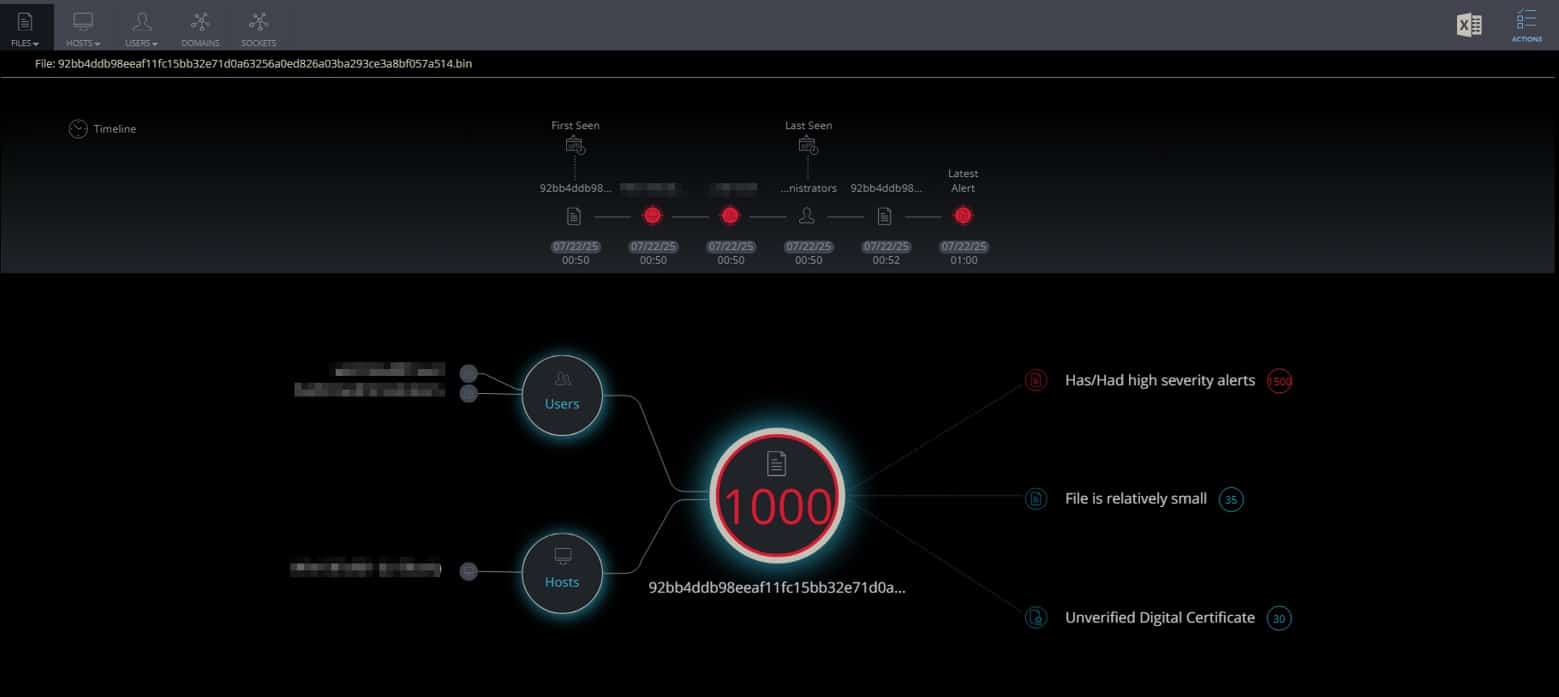
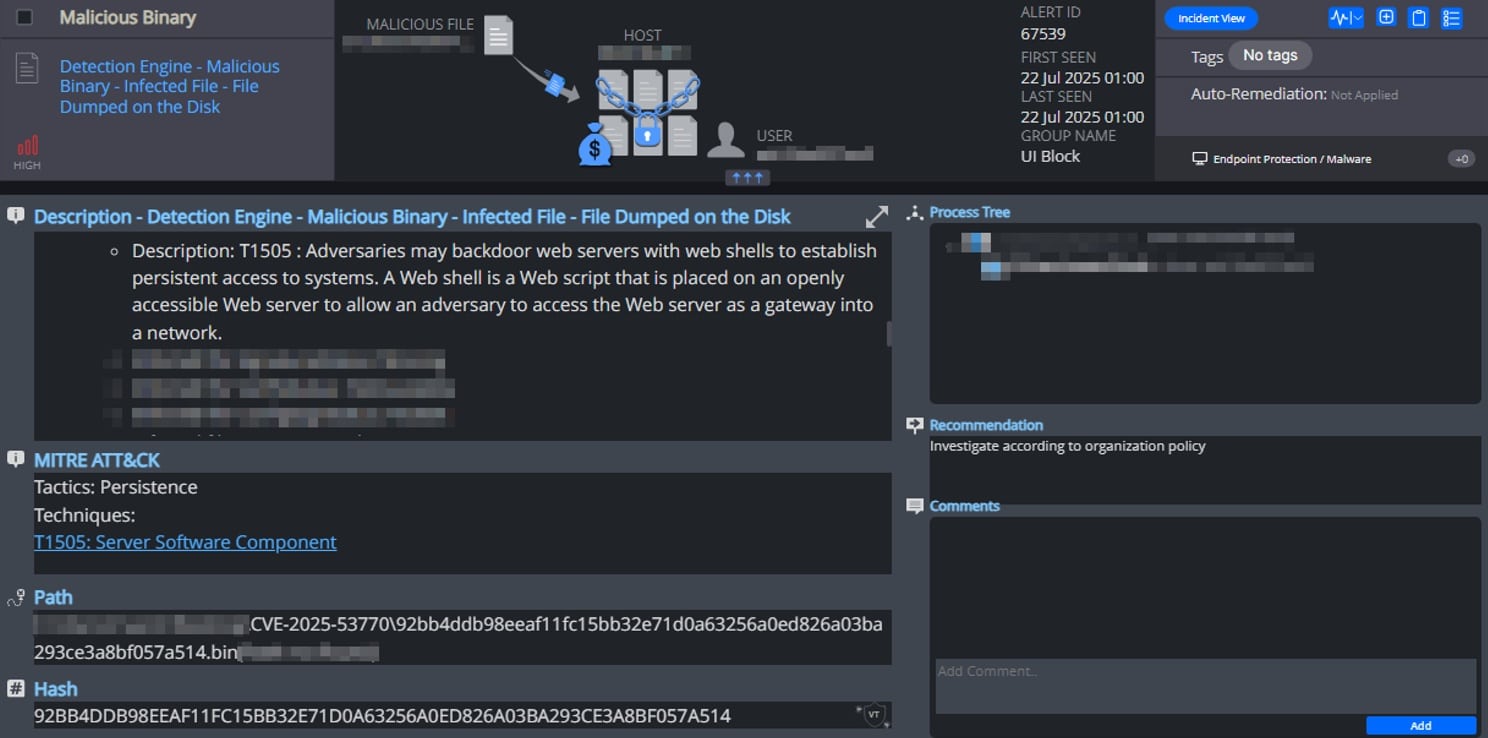
Cynet All-in-One Detection Alert
Cynet All-in-One detects malicious web shell file patterns related to CVE-2025-53770 – it immediately generates a high-severity alert mapped to MITRE ATT&CK T1505 (Server Software Component):
Mitigation Guidance
Microsoft and CISA recommend implementing the following:
- Apply July 2025 Security Updates for all supported on-prem SharePoint versions immediately.
- Enable AMSI integration with Microsoft Defender across all SharePoint servers. This blocks the exploit path and provides active detection.
- Disconnect SharePoint servers from the internet if AMSI cannot be enabled.
- Monitor Microsoft’s Update Guide for ongoing patches, especially SharePoint 2016.
Note: Microsoft 365 SharePoint Online is not impacted.
Are Cynet customers protected?
Yes. Cynet customers are protected as long as the Cynet agent is deployed on the affected SharePoint servers and protection settings are aligned with Cynet’s Best Practices. Cynet will continue to monitor the threat landscape and update detection logic as new indicators and techniques emerge, but here’s how Cynet helps:
- CyAI, Cynet’s AI-based threat detection engine, continuously analyzes activity for patterns associated with known and emerging threats targeting SharePoint.
- Behavioral protection – identifies malicious behavior patterns during exploitation attempts.
- Memory-based attack detection – detects in-memory techniques often used in SharePoint exploits.
- Exploitation technique prevention – blocks known exploitation methods proactively.
- CyOps, Cynet’s 24/7 MDR team, actively monitors signs of exploitation and will alert and assist customers in real time if any suspicious activity is detected.
Customers should ensure that the Cynet agent is deployed on all relevant SharePoint servers and that all detection mechanisms are enabled and updated in their security policy.

