Introduction: VPNs Under Siege
As remote work solidifies its place in the modern enterprise, VPNs have become the de facto gateway to corporate networks. This shift has made them a prime target for threat actors looking to bypass traditional security controls.
At Cynet, our CyOps team has observed a clear trend: attackers are increasingly focusing on edge infrastructure, especially VPN appliances, as a means of initial access.
Since the beginning of 2025, Cynet has witnessed an approximate 40% increase in attacks targeting SonicWall VPNs compared to 2024. Notably, a significant portion of these attacks involved the use of stolen credentials, highlighting the growing threat of identity-based attacks.
This post explores the broader implications of this trend and dives into two recent examples of critical vulnerabilities in SonicWall VPNs that illustrate the risks: one enabling session hijacking, the other bypassing multi-factor authentication. Together, they reveal how attackers are evolving their tactics, and why defenders must evolve their strategies in response.
We’ll also show how Cynet’s multi-layered XDR and ITDR (Identity Threat Detection and Response) capabilities help detect and mitigate these threats before they escalate.
What We’re Seeing at Cynet
Since the beginning of 2025, CyOps has witnessed a rise in incidents involving SonicWall VPN exploitation. These attacks typically involve:
- Direct access without user interaction, often exploiting misconfigurations or known flaws.
- Stolen credentials and Identity misuse and lateral movement within minutes of access.
- Attempts to disable endpoint protection or evade detection.
This is not about a single vulnerability, it’s about the strategic targeting of VPN infrastructure as a reliable entry point.
The following chart represents disclosed vulnerabilities from 2024 until today, as published by SonicWall.
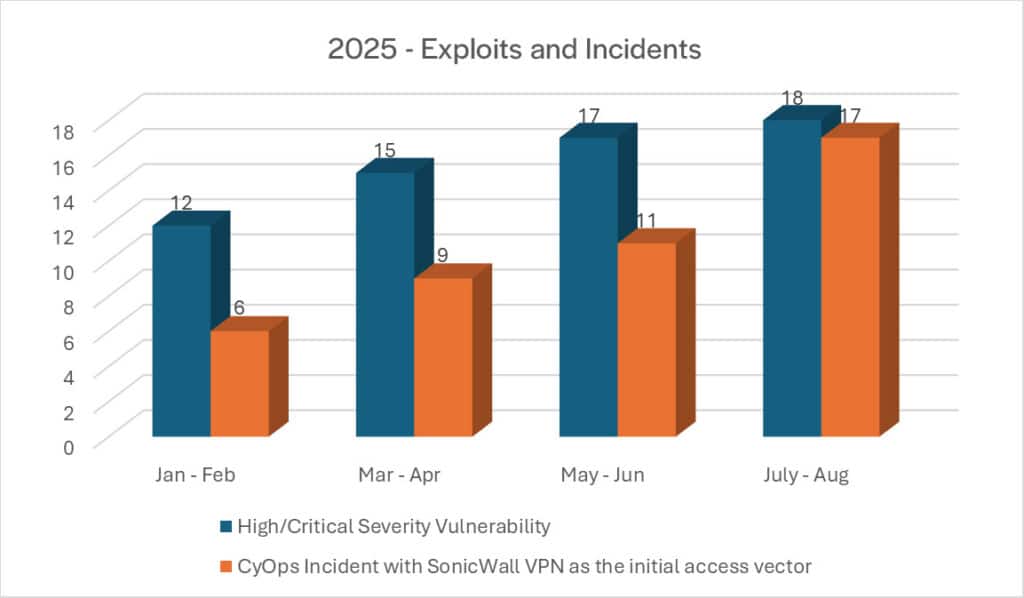
Understanding SonicWall VPN and Its Appeal to Threat Actors
SonicWall’s VPN solutions are widely used by organizations looking to secure remote access. But their popularity has also made them a tempting target. Researchers and attackers alike have recently uncovered flaws that put thousands of exposed devices at risk.
Why VPNs Are a Prime Target
Attackers favor VPNs because:
- They offer direct access to internal networks.
- They often lack real-time monitoring or anomaly detection.
- Misconfigurations and outdated firmware are common in smaller organizations.
- VPN logs are often limited or overlooked, allowing stealthy access.
- They are frequently exploited using stolen identities and credentials.
There are several vulnerabilities identified related to SonicWall, the following represent some of the most critical and high-priority issues currently observed:
CVE-2024-53704: Hijacking Sessions Without Logging In
This vulnerability allows unauthenticated attackers to hijack active SSL-VPN sessions by forging a specific cookie. Once inside, they can:
- View or modify user bookmarks
- Access VPN profiles
- Boot out legitimate users
- Pivot into the internal network
Security researchers from Bishop Fox released a detailed analysis and proof-of-concept, prompting a swift response from SonicWall.
CVE-2024-12802: A Clever Way to Bypass MFA
This one hits differently. This flaw targets how SonicWall appliances handle Active Directory authentication. When both UPN (user@domain) and SAM (DOMAIN\user) formats are enabled, attackers can bypass MFA entirely no one-time code, no warning – just waltz in.
What makes this even more dangerous is that VPN brute-forcing is a common initial access method. Some threat actors even offer VPN brute-force-as-a-service, making it easier than ever to exploit weak or reused credentials. Once valid credentials are obtained, this vulnerability allows them to bypass MFA and gain full access.
This is a textbook example of identity-based exploitation.
While there’s no public exploit yet, the vulnerability has a CVSS score of 9.1, and security teams should treat it as critical.
Why These Flaws Matter
It’s not just the severity of these bugs that’s alarming, it’s their nature. Here’s why they’ve captured the attention of cybersecurity teams everywhere:
- Authentication is bypassed, not broken, bypassed. That’s a big deal.
- No user action required, attackers don’t need phishing emails or stolen credentials.
- Silent entry, logs may not even show unusual activity.
- Thousands of devices remain exposed, especially in smaller orgs with limited patching windows.
- These aren’t theoretical; exploits are already active in the wild.
- They often involve identity misuse, making traditional defenses insufficient.
What You Can Do Right Now
Securing VPN infrastructure isn’t just about patching known vulnerabilities; it’s about recognizing that these systems are high-value targets and often blind spots in traditional security stacks.
If your organization uses SonicWall VPN or SMA appliances (or even if you’re using other vendors), you should take immediate steps to reduce exposure. The trend is clear: VPN infrastructure is being actively and increasingly targeted by threat actors, not just through zero-day vulnerabilities, but also through misconfigurations, weak authentication, and gaps in visibility.
To reduce your exposure, consider the following steps:
1. Treat VPNs as Active Threat Surfaces
VPN appliances should be monitored like any other endpoint. Ensure they are included in your asset inventory, regularly scanned for vulnerabilities, and monitored for behavioral anomalies.
2. Go Beyond Patching
While firmware updates are essential, they’re not enough. Many attacks exploit misconfigurations, weak credentials, or overlooked session persistence. Regularly review authentication policies, session timeouts, and exposed services.
3. Monitor for the Unseen
Many VPN exploits leave little to no trace in logs. This is where extended detection and response (XDR) platforms like Cynet can help, by correlating unusual access patterns, lateral movement, and privilege escalation attempts across the environment.
4. Assume Breach, Validate Continuously
Adopt a mindset of continuous validation. Use threat hunting, behavioral analytics, and automated response playbooks to detect and contain suspicious activity — even if the initial access vector goes unnoticed.
Cynet’s Multi-Layered Defense Approach
Cynet’s all-in-one XDR platform is designed to detect, prevent, and respond to these types of threats:
- Correlated detection of anomalous VPN usage
- Endpoint protection that blocks post-access tools like remote shells
- They often involve identity misuse, making traditional defenses insufficient.
- User behavior analytics
- Automated response & custom playbooks
This multi-layered approach ensures that even if a VPN is exploited, attackers are contained before they can cause damage.
Final Thoughts: A Moment of Reckoning for VPN Security
SonicWall is just the latest in a series of trusted vendors targeted by sophisticated attackers. But the message is clear: VPN appliances are not “set-and-forget” security tools – they are active battlegrounds.
Left unpatched, unmonitored, or misconfigured, they can become liabilities overnight, offering attackers a direct path into your environment.
This is a moment of reckoning for defenders: VPNs and identity infrastructure must be treated as critical assets, continuously hardened, monitored, and integrated into your broader detection and response strategy.
The threat is real, the trend is accelerating, and the time to act is now.

