CyOps Threat Alert: What you need to know about CVE-2023-23397
In an update on Tuesday, March 14, 2023, Microsoft released 83 security fixes, including for CVE-2023-23397.
CVE-2023-23397 is a Microsoft Outlook desktop app vulnerability. Microsoft Outlook web access (OWA) and Microsoft 365 are not vulnerable.
Remote hackers can exploit this vulnerability to gain targeted users’ Net-NTLMv2 credentials hashes. These hashes facilitate authentication in systems that support Net-NTLMv2, enabling the attackers to perform a relay attack. The vulnerability is particularly dangerous as a Zero-Touch exploit; no user interaction is needed. The exploit will work whether or not the recipient has seen or opened the message.
How does it work?
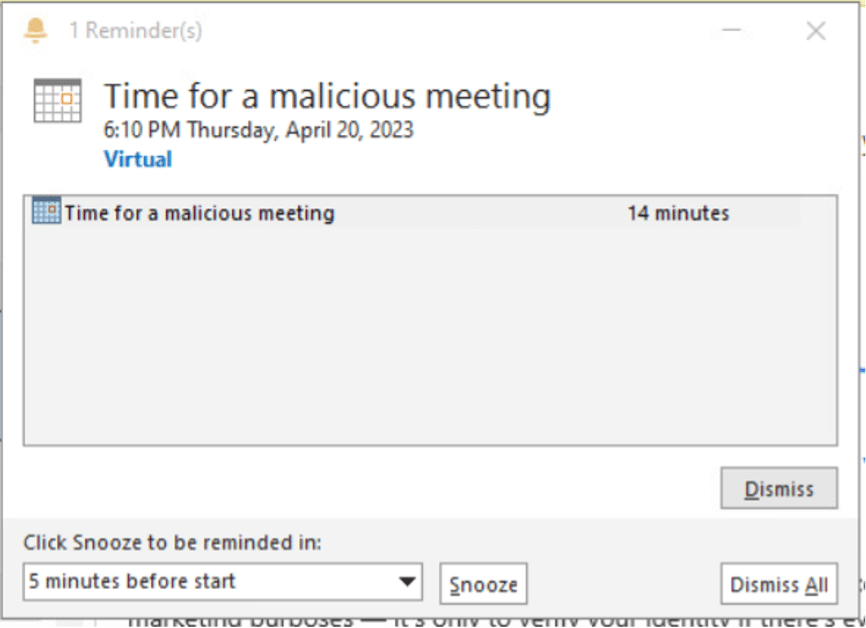
CVE-2023-23397 is a vulnerability in Microsoft Outlook that allows an attacker to send a malicious calendar invite, represented by a .msg file, to a victim, including a custom alert sound option for reminders.
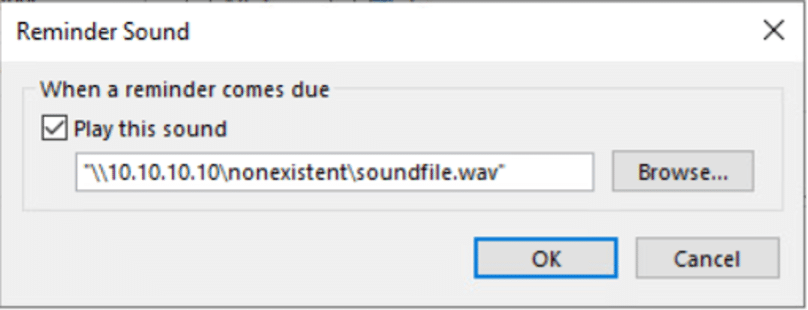
The PidLidReminderFileParameter is used to set a custom notification sound for items such as meeting notifications. However, in this case, the .msg file contains a Universal Naming Convention (UNC) path to a remote attacker-controlled Server Message Block (SMB) share.
The I.P. address is an example of the attacker-controlled SMB share.
Because Microsoft Outlook does not distinguish between legitimate and not legitimate UNC paths, it erroneously assumes the attacker-controlled SMB share is a legitimate network resource. When the victim’s system attempts to access the shared folder as specified in the UNC path, it inadvertently sends an authentication request to the attacker’s SMB server. This request contains the victim’s Net-NTLMv2 credentials in the form of a hash, which the attacker can use to authenticate themselves against other systems that support NTLM authentication. This type of attack, known as a relay attack, is particularly concerning because it requires no user interaction and can be carried out silently in the background.
This allows the attacker to exploit the vulnerability without the recipient opening the message, triggering the vulnerable API endpoint PlayReminderSound and gaining access to the victim’s system.
When the victim connects to the attacker’s SMB server, the victim’s system automatically sends a New Technology LAN Manager (NTLM) negotiation message to the remote server. This message can be exploited by the attacker to authenticate themselves against other systems that also support NTLM authentication.
Affected versions of outlook
Every version of the Microsoft Outlook desktop app is affected. Microsoft OWA and Microsoft 365 aren’t vulnerable.
Mitigations
Here are Microsoft’s mitigation and security updates:
And here you can find a script that checks exchange messaging items:
Cynet detections
Cynet 360 AutoXDR detection and prevention mechanisms are producing rules and policies to make sure our customers are protected from attempts to exploit CVE-2023-23397.