CyOps Threat Alert: Follina mitigated, the recent MSDT 0-Day Vulnerability Explained
By: Daniel Lippa – CyOps analyst
Follina in a nutshell
Disclosed on May 30th, CVE-2022-30190 is an abuse of Microsoft Office, allowing threat actors to launch the ‘ms-msdt’ URI protocol handler to execute commands such as PowerShell and CMD simply by opening the initiated Microsoft Office applications such as “.doc” or “.rtf” to initiate a remote command execution on an environment.
Cynet 360 AutoXDR™ detection and prevention mechanisms are already updated with rules and policies to make sure our customers are protected from attempts to exploit this vulnerability.
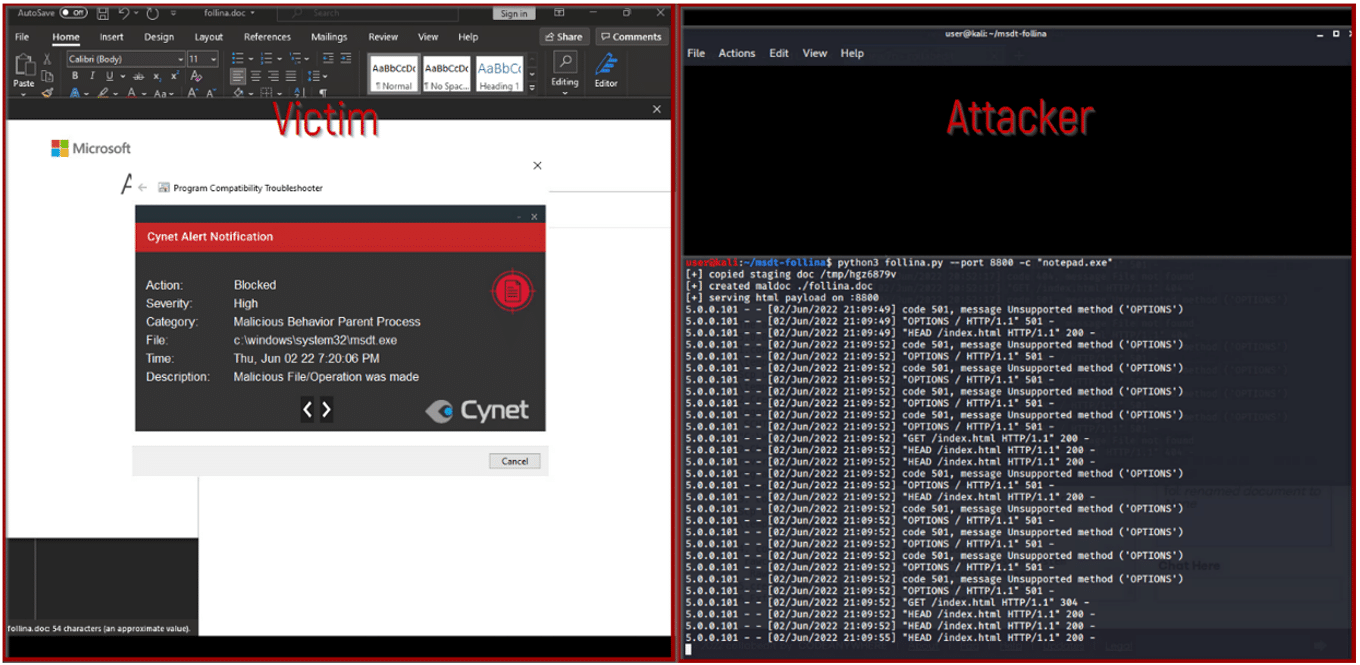
Alert from Cynet 360 AutoXDR user interface
What is MSDT?
The Microsoft Windows Support Diagnostic Tool (MSDT) is an application of Microsoft Windows operating system.
The msdt.exe is an executable file developed as part of Microsoft’s Windows Operating System and belongs to the Diagnostics Troubleshooting Wizard process.
An attack scenario
The attack is carried out quite easily. Requiring minimal interaction with the user, any executable or command execution can be triggered by simply opening the .doc/.rtf file without additional prerequisites.
If the malicious document is a “.doc” file, the user needs to click on it for execution. If the malicious document is a “.rtf” file, hovering over it for a preview is enough for execution.
Also, it’s easy to launch a malicious PowerShell command with -style “hidden” flag without exposing the user to the fact that a malicious payload was executed on their system, since the “ms-msdt” can run commands automatically without user interaction.
Which versions of Microsoft Office are affected?
The MSDT Remote Code Execution (Follina) vulnerability currently affects Microsoft Office 2013, 2016, 2019, and 2021, which has no official patch available.
Cynet to the rescue
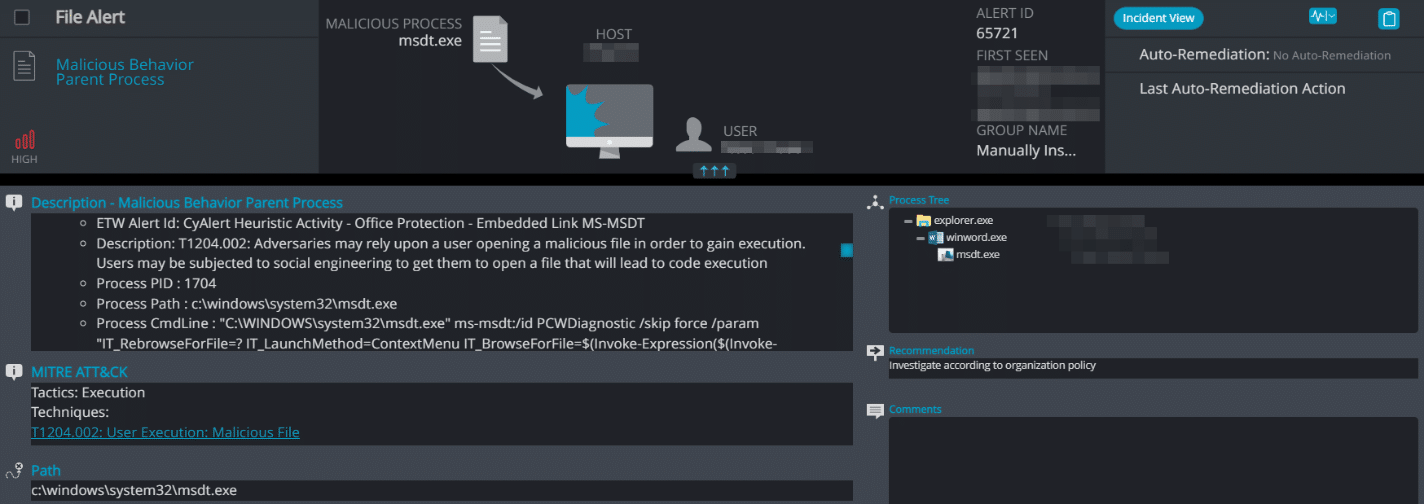
Since Cynet’s platform constantly monitors the memory address environment, Cynet 360 AutoXDR has many detection mechanisms related to parent processing and malicious script commands. Once Cynet detects that Microsoft Office is trying to initiate code execution through a third-party application, it will automatically detect and prevent the activity.
Also, since Microsoft Office utilities are not supposed to open the Diagnostic tool, which is meant for other processes, we have deployed a detection rule that will be triggered once Cynet detects that the diagnostic tool has a process appearance from the Office-related file.
This rule will also prevent the activity by killing the process immediately, blocking threat actors on the spot since they must have the process up and running to initiate code execution.
Exploitation attempt blocked on a host protected by Cynet 360 AutoXDR
Steps you can take right now to mitigate
Uninstalling the Windows Diagnostic tool
You can always simply uninstall the Windows Diagnostic tool by following these steps:
- If the file is a part of a software program, then it will also have an uninstall program. Then you can run the Uninstaller located at directory like C:Program Files>Microsoft Windows Operating System>Microsoft Windows Operating System >Diagnostics Troubleshooting Wizard> msdt.exe_uninstall.exe.
- Or, if the msdt.exe was installed using the Windows Installer, it can be uninstalled by going to System Settings and opening Add or Remove Programs Option.
- Then search for msdt.exe or the software name Microsoft Windows Operating System in the search bar or try the developer name Microsoft Windows Operating System.
- From there, click on it and select the Uninstall Program option to remove msdt.exe file from your computer. The software Microsoft Windows Operating System program along with the file msdt.exe will be removed from your computer.
Disabling the MSDT URL Protocol
Disabling MSDT URL protocol prohibits troubleshooters from being launched as links, including links within the operating system itself. These troubleshooters can still be accessed through the Get Help application and the system settings as supplementary or alternative troubleshooters.
Follow these steps to disable the MSDT URL protocol:
- Run Command Prompt as Administrator.
- Backup the registry key: Execute the command “reg export HKEY_CLASSES_ROOT\ms-msdt filename”
- Delete the registry key: Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”
How Cynet can help you
Cynet’s MDR team, CyOps, monitors our customers’ environments 24/7 and will contact you in cases where indicators of this vulnerability are detected in your environment.
The team is available to our customers for any issues, questions, and there to provide additional information around the clock.
Have questions about this vulnerability?
You can contact our CyOps team directly at:
CyOps Mailbox – [email protected]
Israel: +972 72-3369736
UK: +44 2032 909051
US : +1 (347) 474-0048