On July 22, 2025, international law enforcement agencies announced the seizure of the underground cybercrime forum XSS.is. The operation was carried out by the French Cybercrime Brigade (BL2C), Europol, and Ukraine’s SBU Cyber Department. It coincided with the arrest of the forum’s administrator, alias “Toha,” in Kyiv, Ukraine, abruptly ending the reign of one of the most influential hubs for ransomware operators, exploit sellers, and financial fraud groups.
XSS.is was more than just a forum. It was a marketplace and a coordination center for some of the world’s most destructive cybercrime campaigns, from ransomware extortion to data theft. Its takedown represents one of the most impactful blows against the cybercriminal underground in recent years.

Background on XSS.is
Founded in 2018, XSS.is quickly rose to prominence after the decline of earlier Russian-language forums such as Darkode, Hackforums, and Exploit. With over 50,000 registered members, it provided:
- Exploit and malware trading, including zero-days, proof-of-concepts, custom loaders.
- Initial Access Brokerage, such as credentials and footholds into corporate networks for later use by ransomware affiliates.
- Escrow and arbitration services, creating trust in a community built on crime.
- A cybercriminal knowledge base, including tutorials on phishing kits, obfuscation, and social engineering.
The Administrator: “Distribution”
The forum’s administrator, known online as “Toha”, is a 38-year-old Ukrainian national with nearly two decades of activity in cybercrime communities. His career began with the Hack-All forum in the mid-2000s, later moving on to Exploit.in, one of the most notorious Russian-language marketplaces for exploits and breaches. In 2018 he rebranded the community into XSS.is, which quickly became the go-to platform for ransomware operators and exploit brokers.
Under Toha’s leadership, XSS served as a hub for ransomware groups including REvil, LockBit, and Conti. Affiliates used the forum’s channels to advertise, recruit, and coordinate attacks. He also ran a secure messaging service, thesecure.biz, which was leveraged by ransomware gangs and access brokers to negotiate multi-million-euro extortion deals. Authorities estimate Toha earned at least €7 million personally from advertising revenue, escrow fees, and illicit services. His arrest therefore struck directly at the financial and operational backbone of the criminal marketplace.

The Takedown Operation
This takedown was not a sudden raid but the result of a multi-year investigation. In 2021, French authorities began monitoring thesecure.biz, intercepting encrypted communications that linked Toha to ransomware operators and identified his real identity.
The investigation, coordinated through Europol, culminated in July 2025 with French investigators deployed to Ukraine. Working alongside the SBU, they executed a synchronized operation:
- Toha was arrested at his residence in Kyiv.
- The xss.is domain was seized and replaced with an official seizure banner.
- Forum infrastructure was disrupted to prevent immediate recovery.
This dual strike, which removed both the individual and the infrastructure, was designed to cripple the trust and continuity of the forum.
Aftermath and Community Response
The arrest of Toha sent shockwaves through the underground. Within hours, users flooded Telegram groups and parallel forums with disbelief and panic. Some demanded proof that the forum was truly gone; others warned that new domains might be law enforcement honeypots.
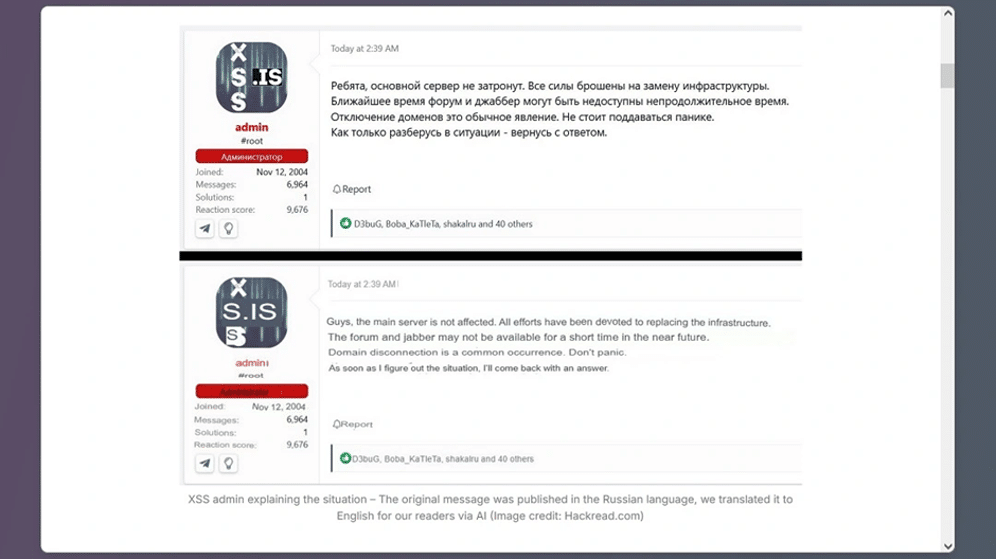
Despite attempts to resurrect the community under xss.pro and a new “.onion” domain, the collapse of escrowed deals and the loss of Toha’s arbitration role left many users stranded. Millions in pending transactions were frozen or lost, and long-standing trust networks disintegrated overnight.
The event was a direct blow to ransomware affiliates: without XSS’s infrastructure, many found it harder to recruit partners or move stolen data. This represents one of the rare moments where law enforcement disrupted not just infrastructure, but trust—the true currency of cybercrime.
Significance & Implications
For Cybercriminals
The takedown created uncertainty and fragmentation. High-profile groups like LockBit and Qilin lost their most prominent recruitment channel. The arrest of Toha proves that even seasoned operators are not beyond reach.
For Security Leaders
XSS.is was a goldmine for early intelligence, from exploit sales to ransomware affiliate recruitment. Its disappearance reduces visibility and forces defenders to expand monitoring to smaller forums and encrypted messaging apps.
For Law Enforcement
This was a strategic victory, targeting not only the platform but the career cybercriminal behind it. By removing Toha, agencies disrupted years of infrastructure and sent a chilling message to other underground administrators.
Conclusion
The seizure of XSS.is was not simply the removal of a domain – it was the downfall of one of the most embedded figures in the cybercriminal ecosystem. For nearly two decades, Toha enabled ransomware groups like REvil, LockBit, and Conti, facilitated illicit markets worth millions, and fostered one of the most dangerous communities on the dark web.
His arrest demonstrates the power of international cooperation and the vulnerability of even long-standing underground leaders. While successor domains have already emerged, the loss of Toha’s leadership and the shattering of community trust mark a turning point for the underground economy.