Mallox Ransomware Analysis
The cyber threat landscape is witnessing the emergence of a new ransomware variant known as Mallox. This pernicious malware (also known as “Target company” ransomware), which primarily targets unsecured internet-facing Microsoft SQL servers, uniquely appends the name of the targeted organization as an encrypted file extension. It is deployed through spam emails and impacts a wide range of sectors, including Manufacturing, Energy & Utilities, and I.T. services. Let’s delve into the intricacies of Mallox and review how Cynet effectively detects and neutralizes such threats.
Static Analysis
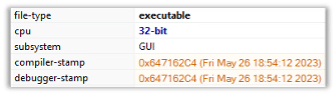
The malware is a 32-bit executable:
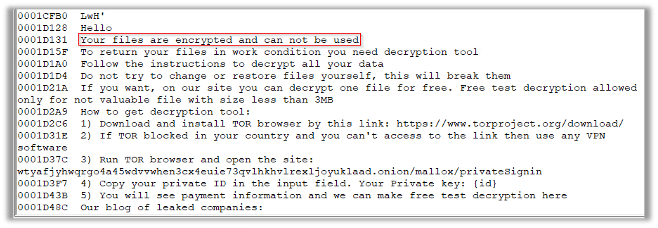
When exploring the strings inside the malware we find some string indicators that seem to be a part of a ransom note:
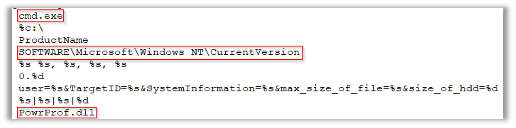
The following strings might be commands, registry keys and files that the malware will use once Initiated:
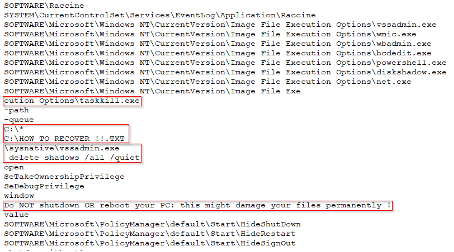
The following strings provide additional clues about additional commands the malware will execute and some suspicious file names that might be associated with the malware’s ransom note file:
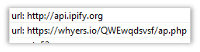
The following strings are network-based IOCs (Indicators of Compromise) that provide additional clues about the malware’s network activity:
Dynamic Analysis
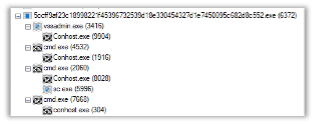
When initiating the malware, it opens the following process tree:
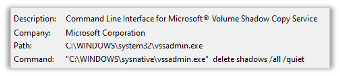
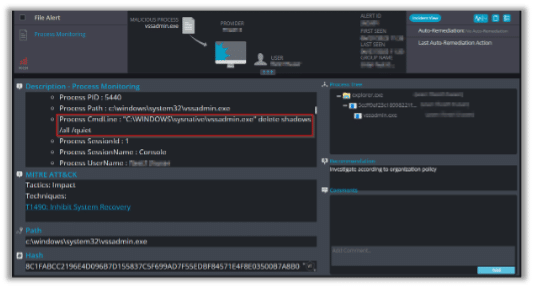
The first process the malware initiates is VSSADMIN:
VSSADMIN is a Windows command-line tool used to manage Volume Shadow Copy Service (VSS), and malware often uses it to delete shadow copies of files to prevent data recovery after a ransomware attack.
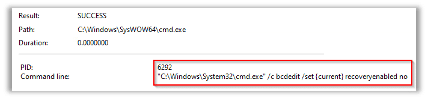
The ransomware initiated the following command:
This command changes the boot configuration so that the system will ignore all errors that occur during the startup process. Ransomware often use this command to ensure that the infected computer will continue to boot up despite possible errors or system failures caused by the malware’s activities.
Additionally, the malware initiates a sequence of commands that terminate and delete various services on the victim’s host:
The following command, which also was used by the ransomware, is disabling the automatic system recovery feature for the current Windows operating system, which means that Windows will not automatically enter recovery mode if a startup error occurs.
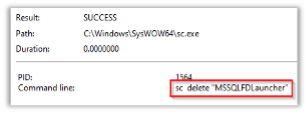
The malware initiated the following command to stop the service ‘MSSQLLFDLauncher.’ Ransomware often delete the “MSSQLLFDLauncher” service to disrupt the operation of Microsoft SQL Server databases, potentially hindering search functionalities and data recovery efforts, thus enforcing its control over the infected system.
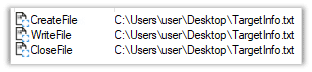
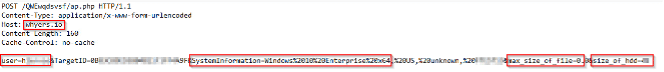
The malware creates a file named ‘TargetInfo.txt’:
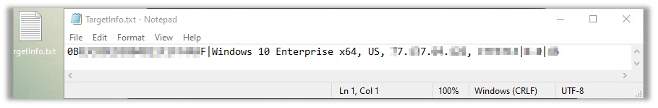
When investigating the file’s contents, we see that it contains information about the victim’s host, such as: OS version, IP address, username, etc.
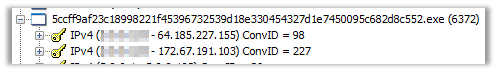
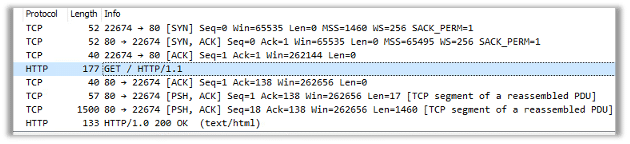
The malware initiated network connectivity:
After establishing the three-way-handshake the malware posts the data of the compromised host to the malicious domain:
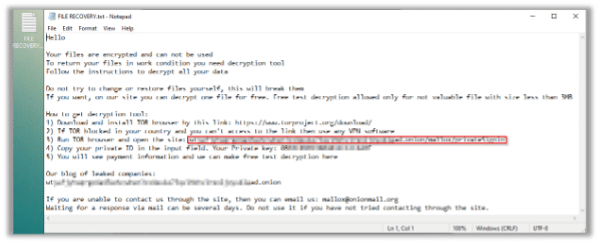
The ransomware scatters its ransom note all over the victims file system:
Once opening the file, we see that it is indeed a ransom note with the detailed payment instructions:
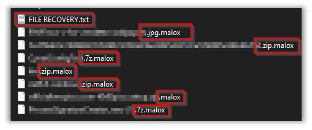
The malware encrypts files and adds a “.mallox” extension to them:
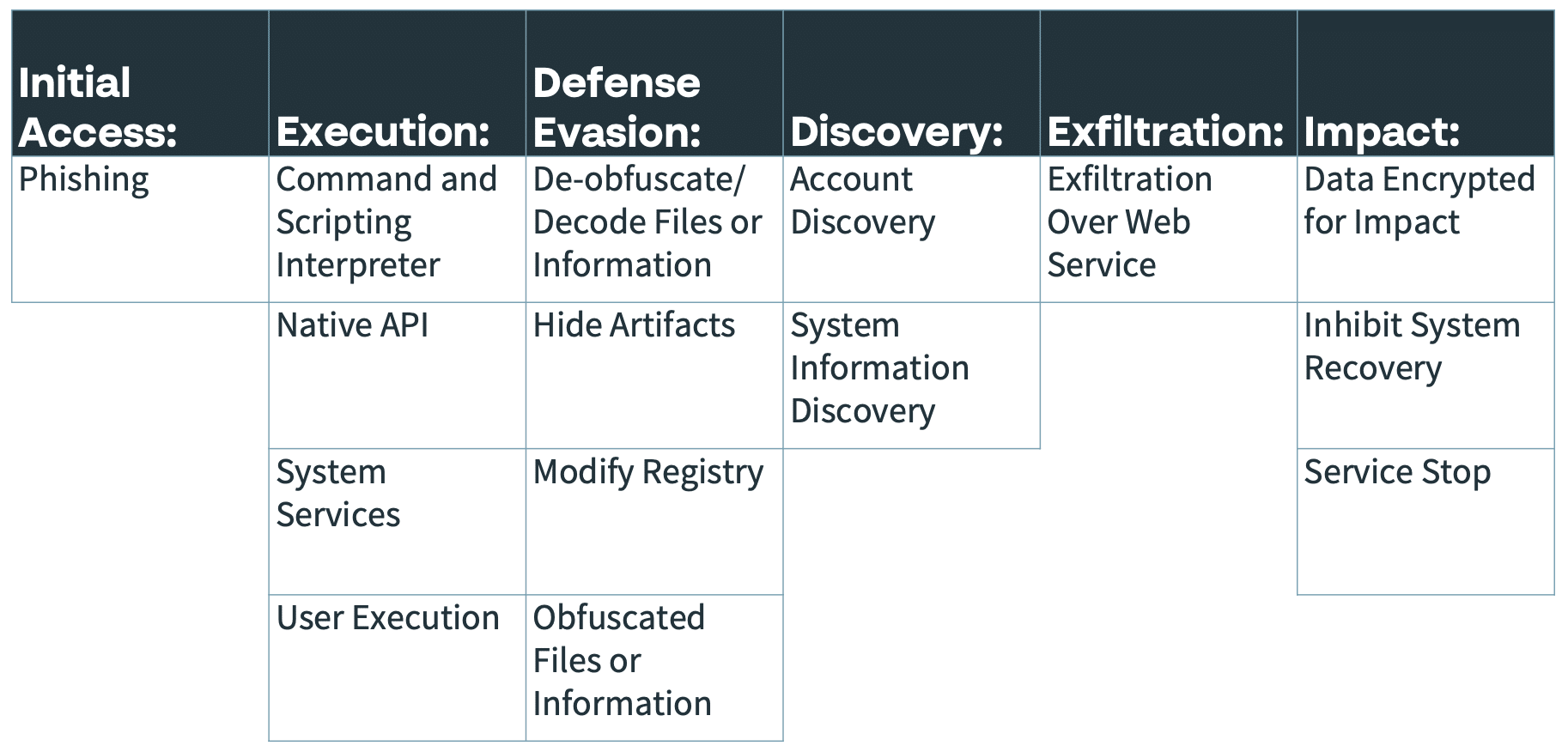
MITRE Attack matrix
Cynet VS. Mallox Ransomware
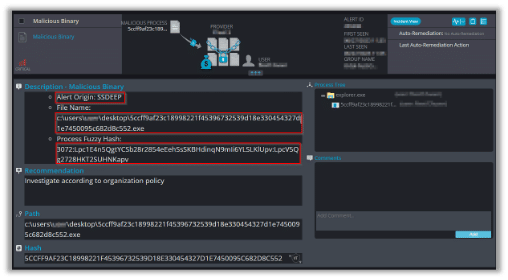
The following alert triggers when Cynet detect a file that shares a SSDEEP with a malicious file:
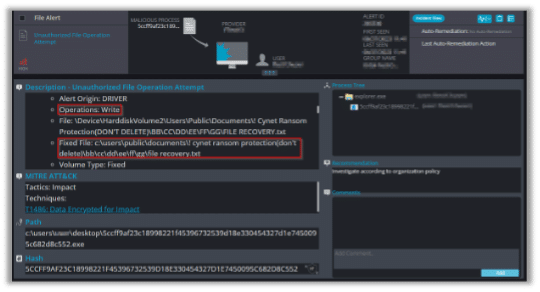
The following alert triggered when the ransom note of Mallox was created:
The following alert triggered when the ransomware Initiated the VSSADMIN command to delete the shadow copies:
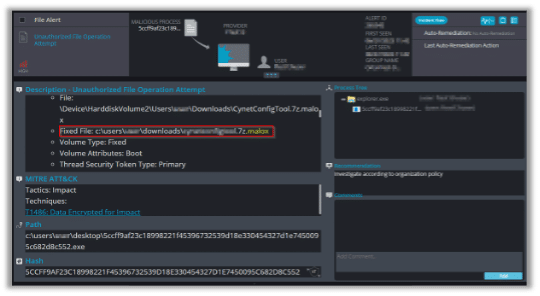
The following alert triggered once the ransomware started the encryption process:
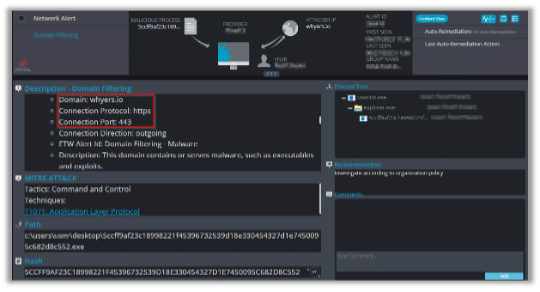
The following alert triggered once the malware initiated network connection with the malicious domain: