Megazord ransomware analysis
A new version of the Akira ransomware called “Megazord” emerged around August 2023. It changes the names of your files by adding “.Powerrangers” at the end. Several static and code similarities suggest that Megazord could be an attempt to give Akira a new look. Such alteration might be an attempt to rebrand the Akira ransomware since it has become familiar to widespread recognition throughout the cybersecurity community.
Interestingly, Megazord was created using a programming language called Rust. Megazord operators target multiple industries with little to no discrimination. This includes attacks on healthcare, education and government entities.
Initial access varies, with observed methods including spear phishing emails as well as the targeting of vulnerable services. Megazord operators use LOLBINS where possible and rely heavily on the existing target infrastructure to maximize dwell time.
Let’s analyze Megazord’s characteristics and effects. We’ll then demonstrate how Cynet automatically prevents the threat.
Static Analysis
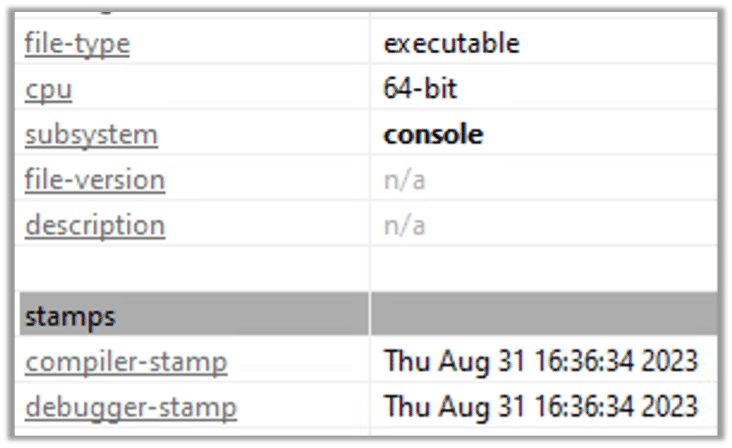
The malware, a 64-bit executable, was compiled on the 31st of August:
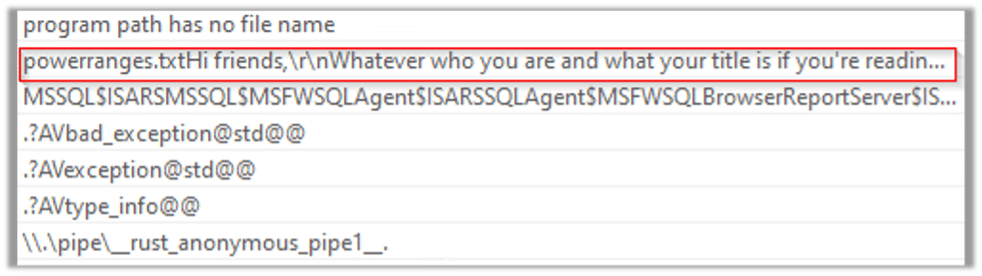
In the malware’s binary are strings that provide additional information about the malware’s possible activities. The following string seems like a possible ransom note that might be dropped upon execution:
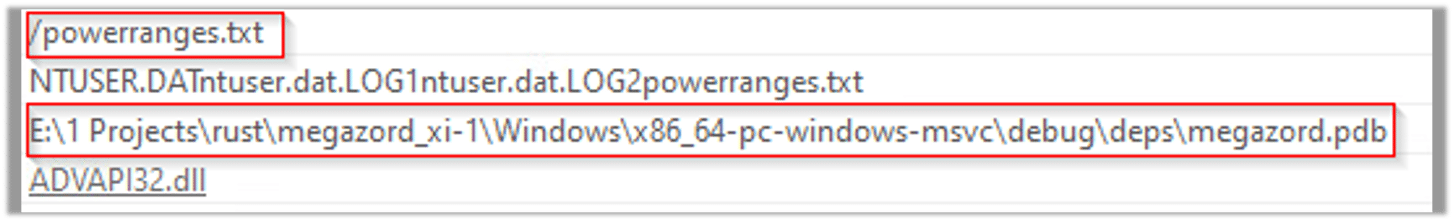
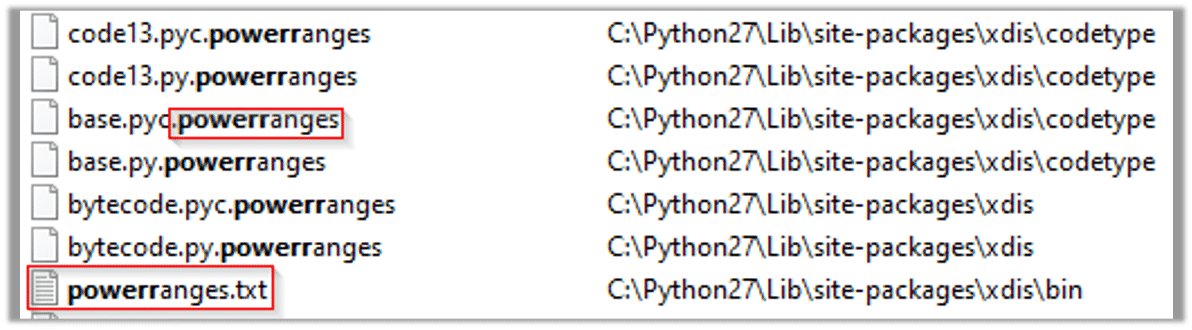
The following strings are additional host base IOCs. The string “powerrangers.txt” could be the file of the ransom note:
More strings that could be related to the malware’s functionality:
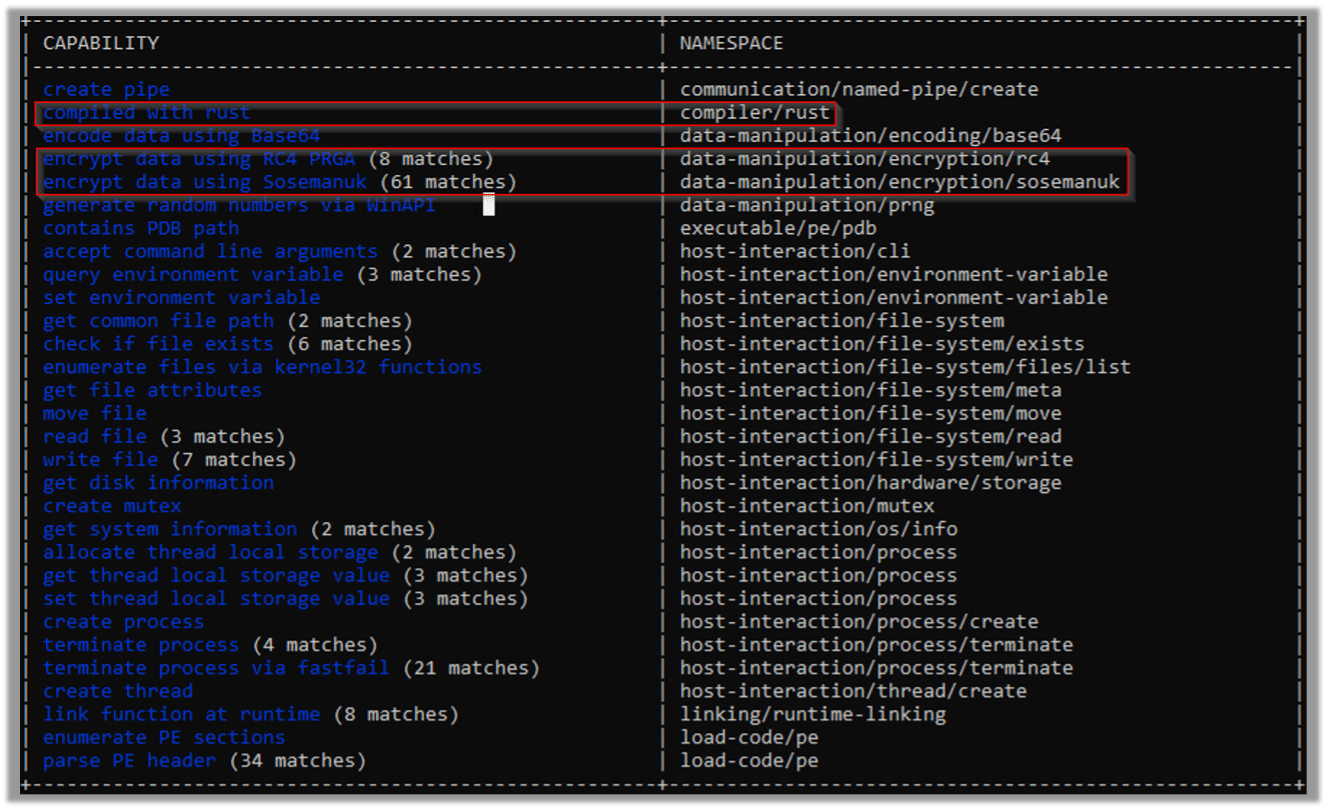
The following Capa output presents all of the malware’s capabilities, such as encryption. We can also see that the malware was complied with Rust:
Dynamic Analysis
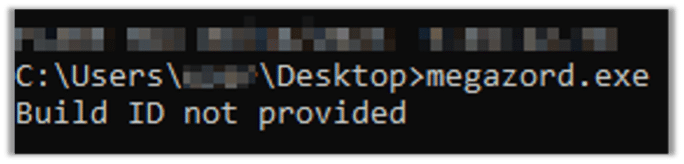
Efforts to initiate the malware show it won’t execute unless we will provide it the Build ID:
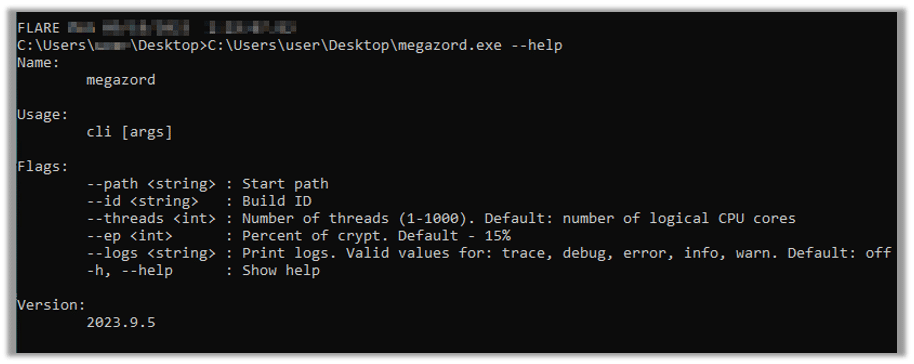
The malware’s binary takes command line arguments:
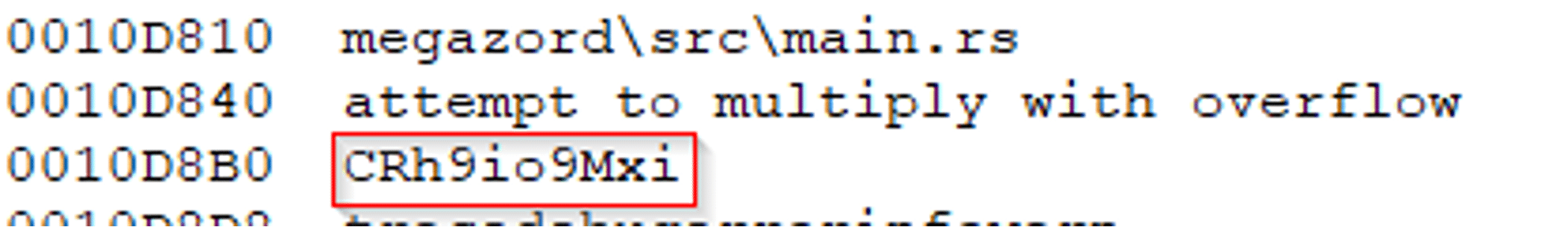
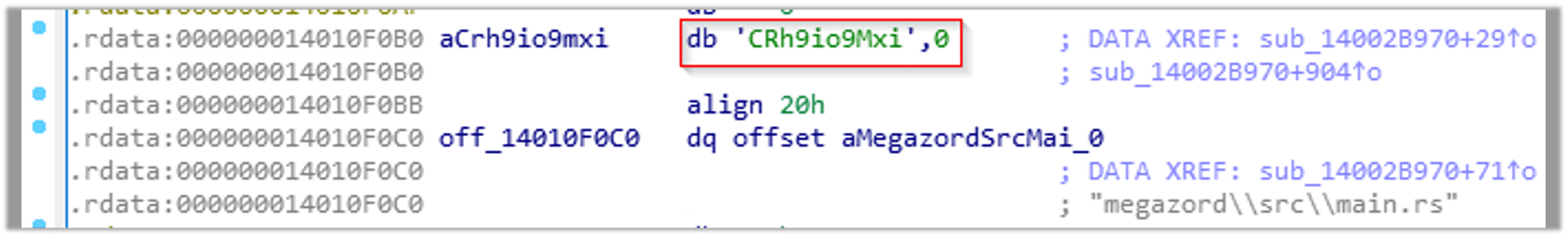
The string we detected in the static analysis section could be the Build ID:
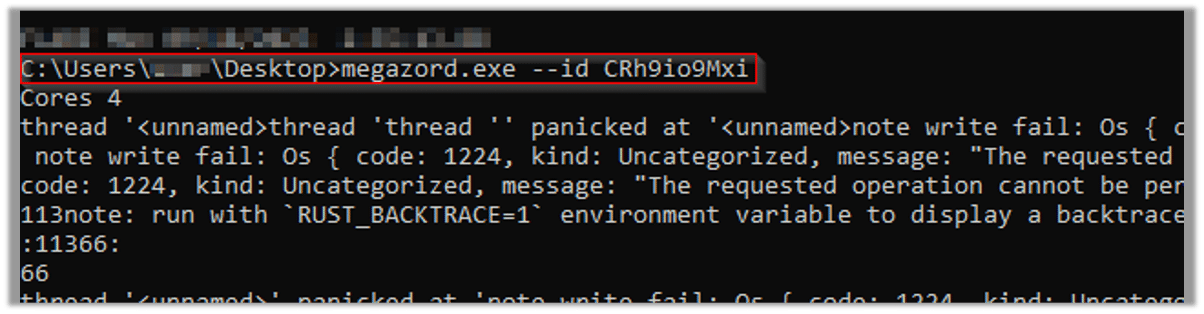
After using the embedded random string as the Build ID, we see that the malware starts its encryption process:
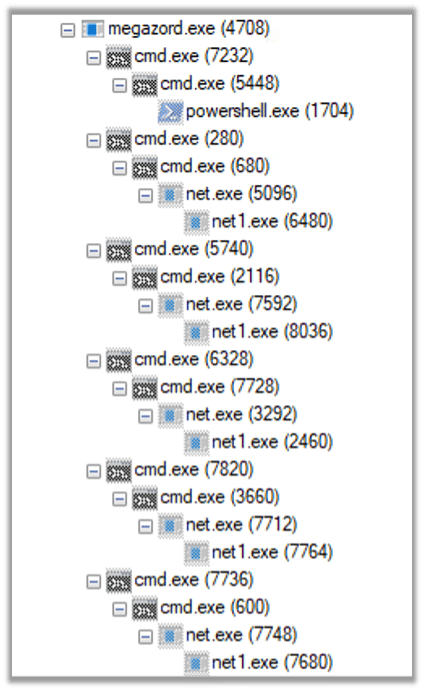
The malware then initiates the following process tree:
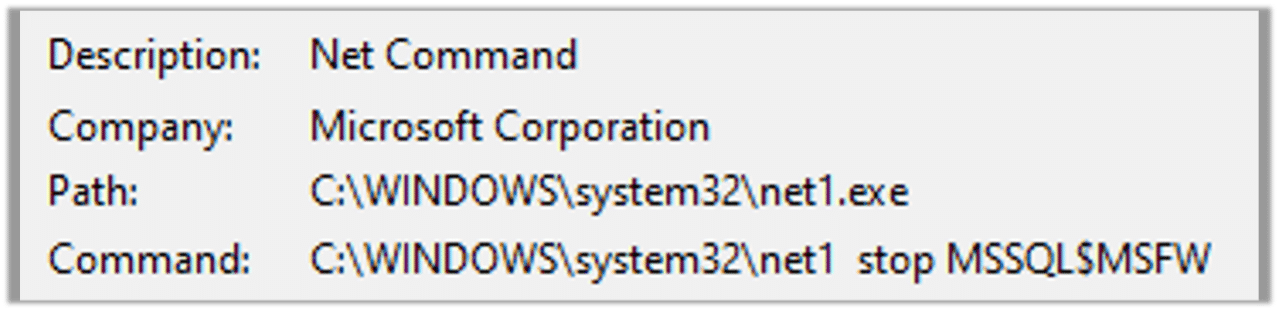
The malware terminates many significant services such as MSSQL:
The malware tries to terminate Windows Defender’s service as well:
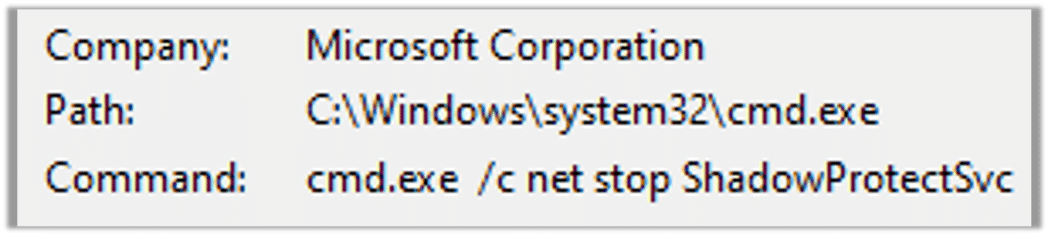
The malware tries to terminate ShadowProtect, a backup and disaster recovery solution used for creating and managing backups:
After trying to terminate many more critical services, the malware starts its encryption process. It adds “. powerrangers” extension to the encrypted files and drops the ransom note:
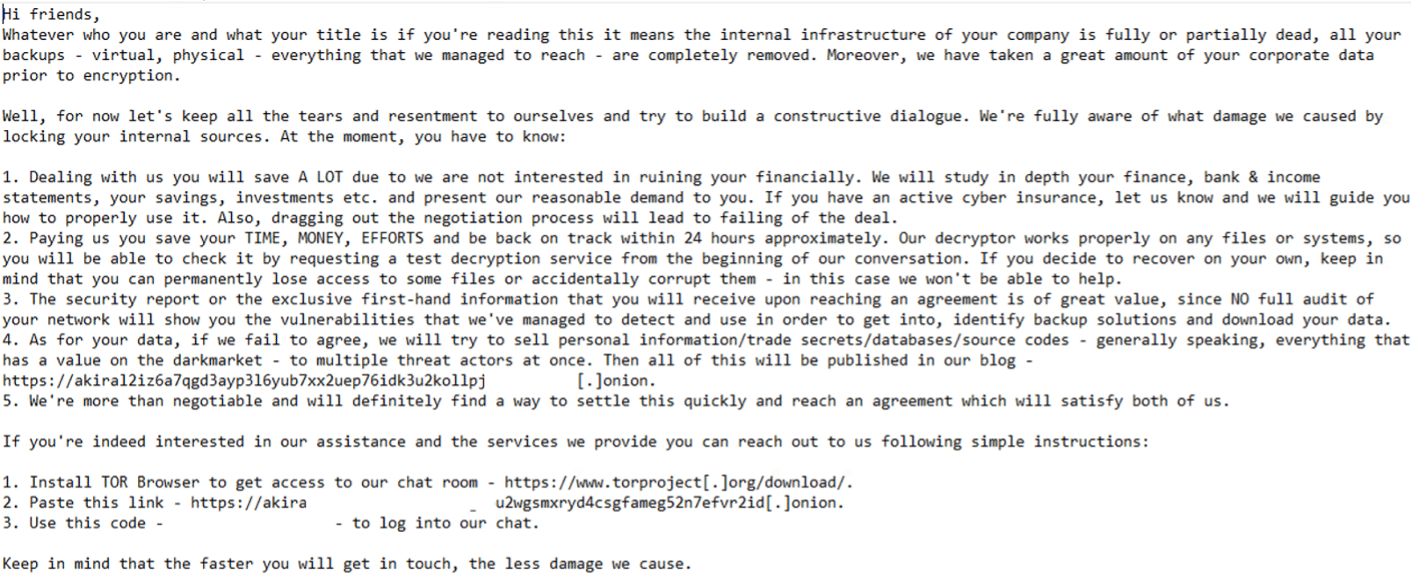
Megazord’s ransom note:
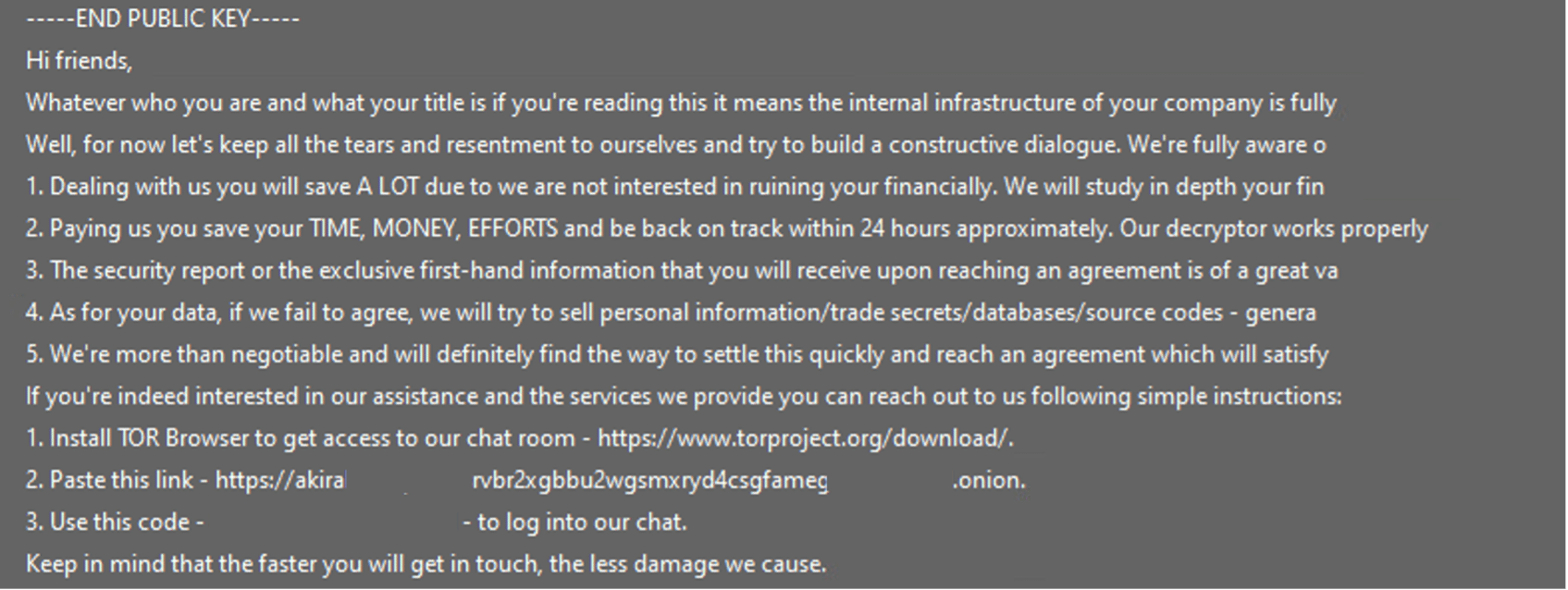
As we can see, the ransom notes of Akira and Megazord are almost identical. This is Akira’s ransomware:
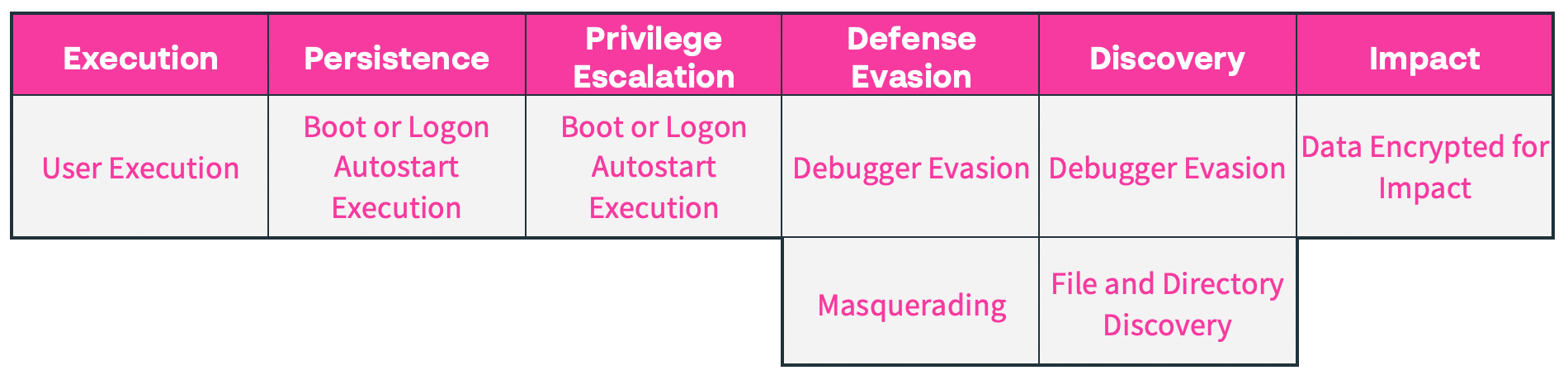
MITRE ATT&CK Tactics and Techniques:
Cynet vs Megazord
Note that during the execution simulation, Cynet 360 AutoXDR is configured in detection mode (without prevention) to allow the Megazord ransomware to execute its full flow. This lets Cynet detect and log each step of the attack.
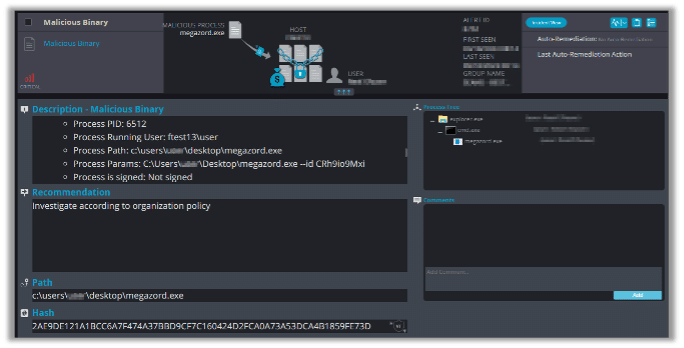
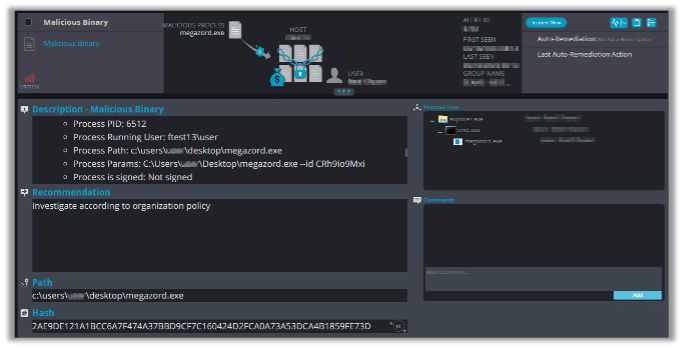
Fortunately, Cynet can detect and prevent this malware using multiple mechanisms. When we try to initiate Megazord, the following alert triggers:
This alert triggers when the malware tries to terminate critical services:
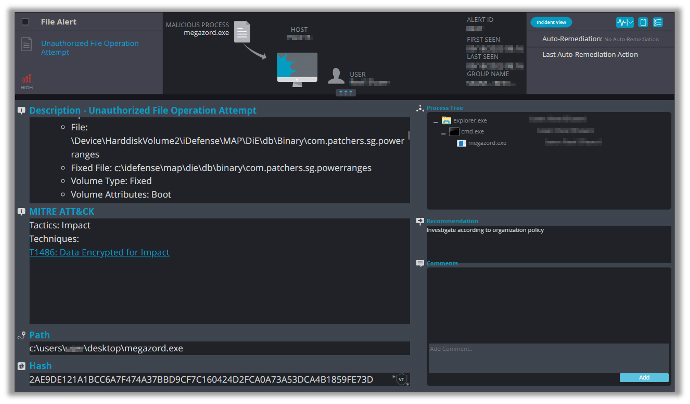
This alert triggers when the malware starts the encryption process: