Orion Threat Alert: Flight of the BumbleBee
By: Max Malyutin – Orion Threat Research Team Leader
Cynet’s Threat Research and Intelligence team recently discovered a new malware campaign called BumbleBee. The campaign is unique in its use of Initial Access Brokers’ (IAB) tactics to gain access to victims’ machines. In this post, we will cover what this campaign is, and how the IAB distributes the BumbleBee malware and its TTPs. We will also explain each TTP according to the MITRE ATT&CK model, and its purpose.
A new campaign in the wild: BumbleBee
From our initial analysis, BumbleBee is a custom new loader that is used by different IAB groups. This malware was observed injecting Cobalt Strike shellcodes in memory and using several tactics, techniques, and procedures (TTPs) in order to compromise the victim’s environment.
As part of the campaign, the threat actors abuse spoofed companies’ identities (like fake employee email addresses, fake websites, etc.) and use legitimate public storage services to deliver the malicious ISO image file. The ISO image file is responsible for luring the victim to execute the BumbleBee malware.
We’ve seen Living Off the Land Binaries (LOLBins) execution with rundll32, which allows threat actors to avoid defenses. BumbleBee also creates a scheduled task on the compromised host for persistence and executes a Visual Basic script via the scheduled task. The IAB relies on the user (victim) execution to execute the BumbleBee payload by luring the victim to mount an ISO image file and click on a Windows shortcut (LNK) file.
The malware name, BumbleBee, was chosen because of its unique user agent, “bumblebee,” that was used as part of the communication with the command and control server (C2).
Threat Analysis Group (TAG) shared observations on the financially motivated threat actor, EXOTIC LILY, that use the BumbleBee malware. In addition, TAG mentioned an interesting point of collaboration between EXOTIC LILY and the WIZARD SPIDER threat group.
Orion’s observations
This type of attack is new, and the cybersecurity community is still gathering data to glean more insights on the nature of this attack and its targets.
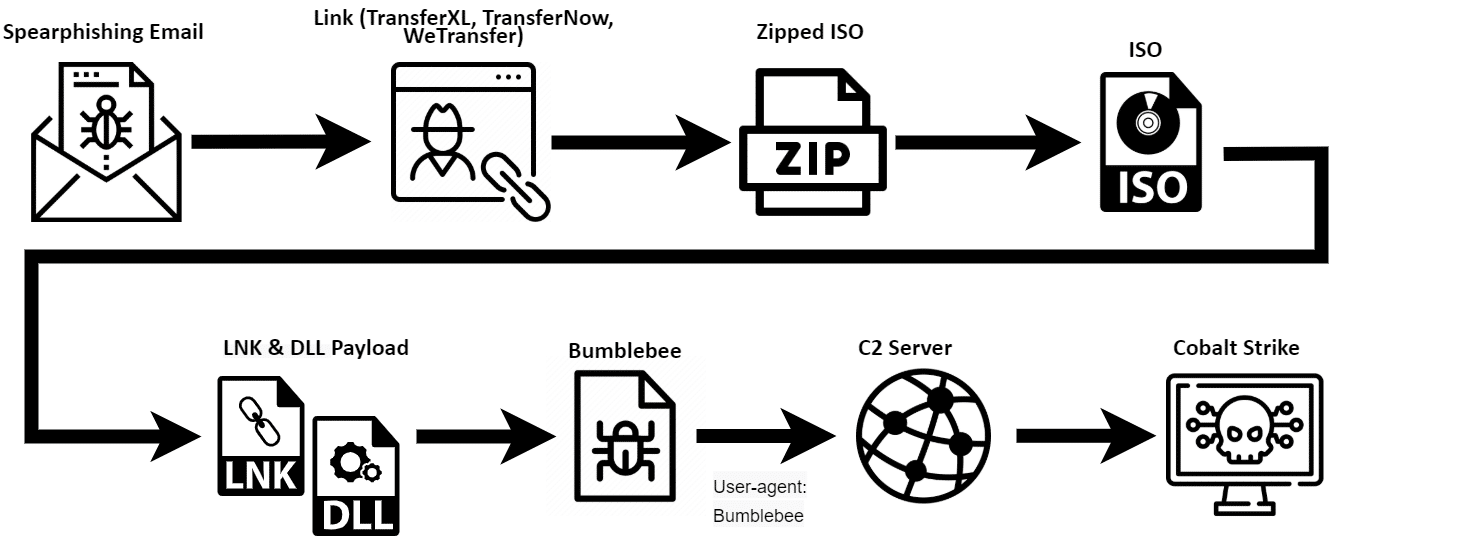
Orion found a high number of targeted companies based in the US with the following distribution method that delivers the BumbleBee malware: Spear phishing email > URL Link (TransferXL, TransferNow, WeTransfer) > Zipped ISO > ISO (contains the LNK file and the BumbleBee payload).
You can see the execution flow in the image below.
The infection flow
We’ve handled several incident response (IR) cases where threat actors distributed BumbleBee malware. After the initial infection, the threat actors inject Cobalt Strike shellcode in memory and execute discovery commands to collect info about the victim’s network. We believe that threat actors performed this data collection in order to execute the next stage of the infection.
The next stage is probably related to ransomware operations. We’re still investigating IR cases in order to find conclusive evidence that the next stage delivers ransomware.
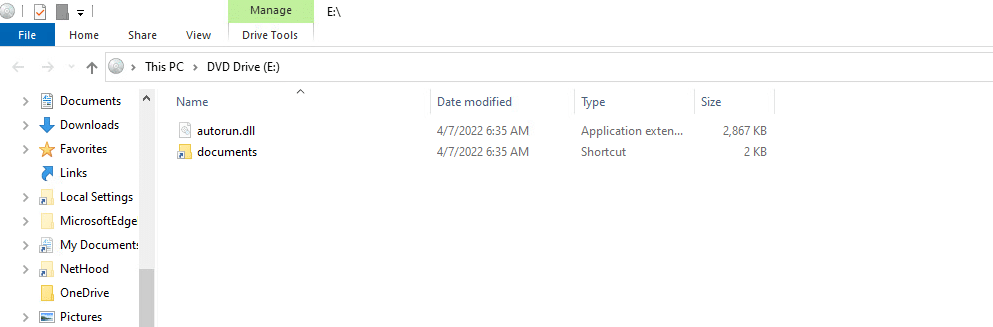
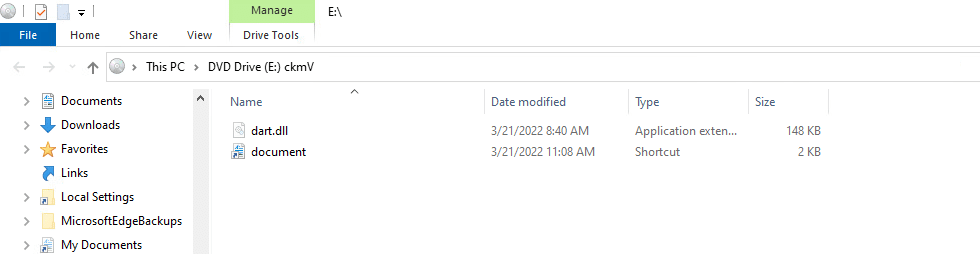
On April 12, 2022, the BumbleBee IAB group was spotted using IMG file format in addition to ISO file format.
You can see an example in the image below.
The IMG file, which contains LNK and DLL
Orion’s technical analysis
Initial Access
The BumbleBee payload was delivered via a spear phishing email that was sent from a spoofed email address. The email contains a URL link to the legitimate public storage service, TransferXL.
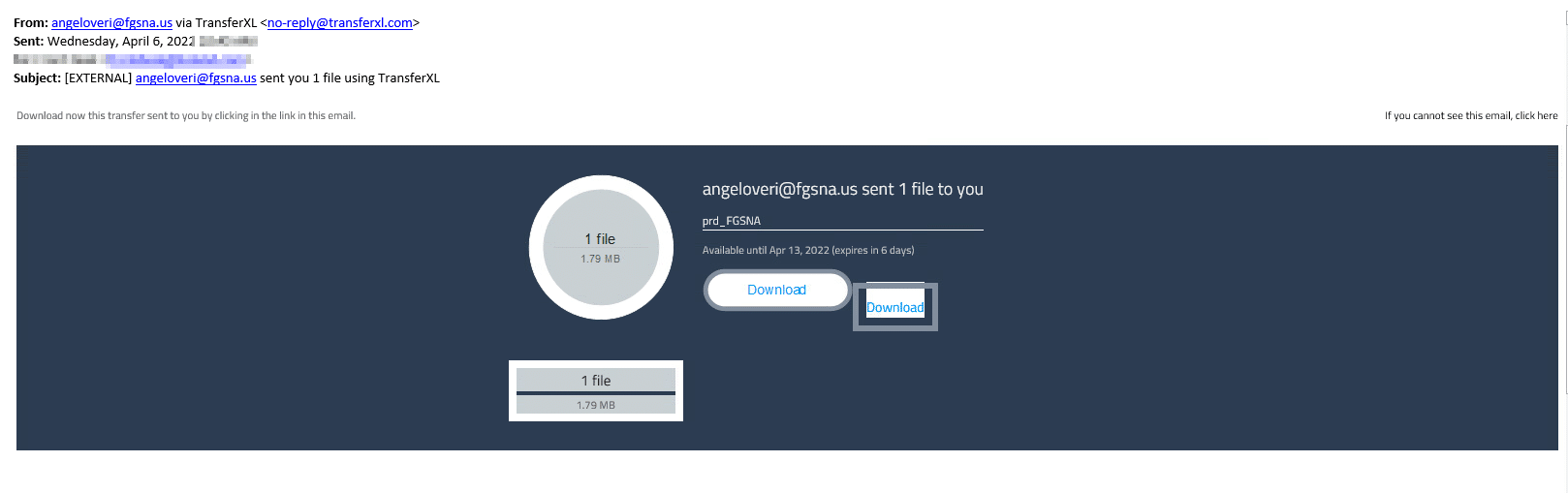
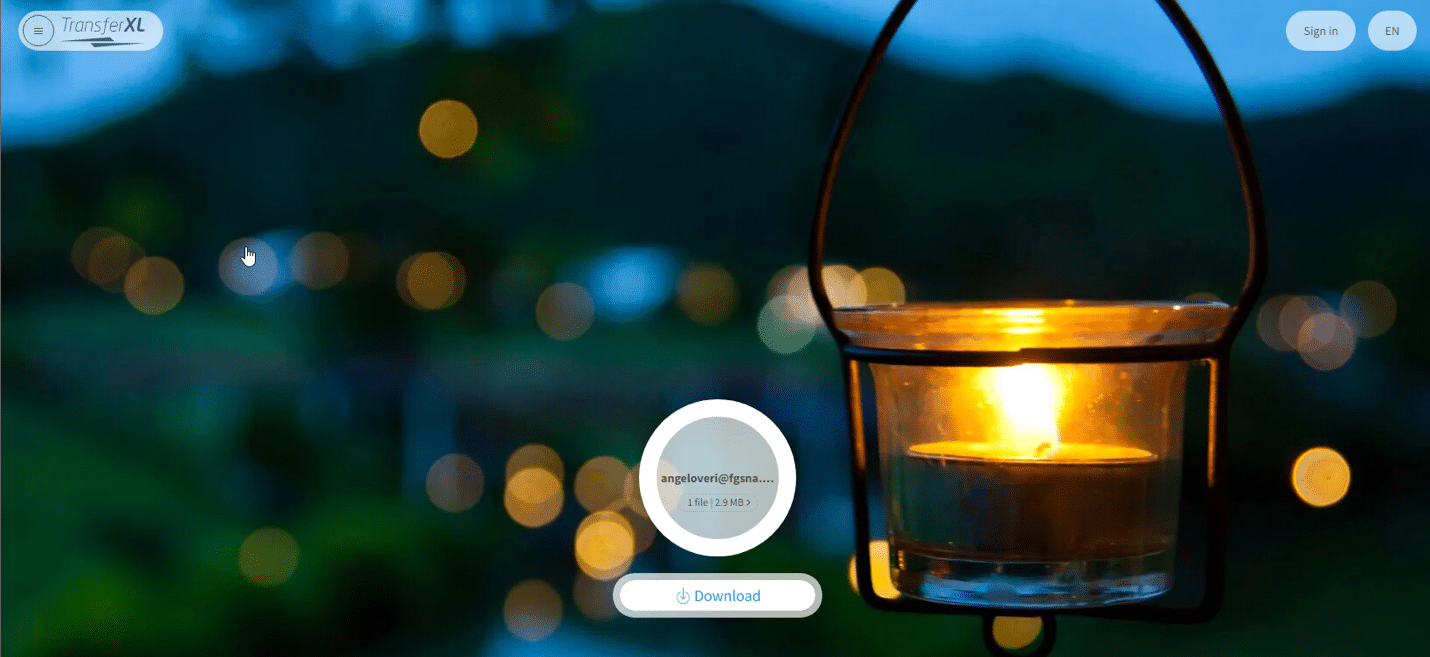
Below you’ll see the legitimate public storage site, which leads the victim to the link to the malicious file.
TransferXL legitimate public storage services
Once they click download, the victim receives a ZIP folder that contains the malicious ISO image files.
Spoofed company email address
Execution
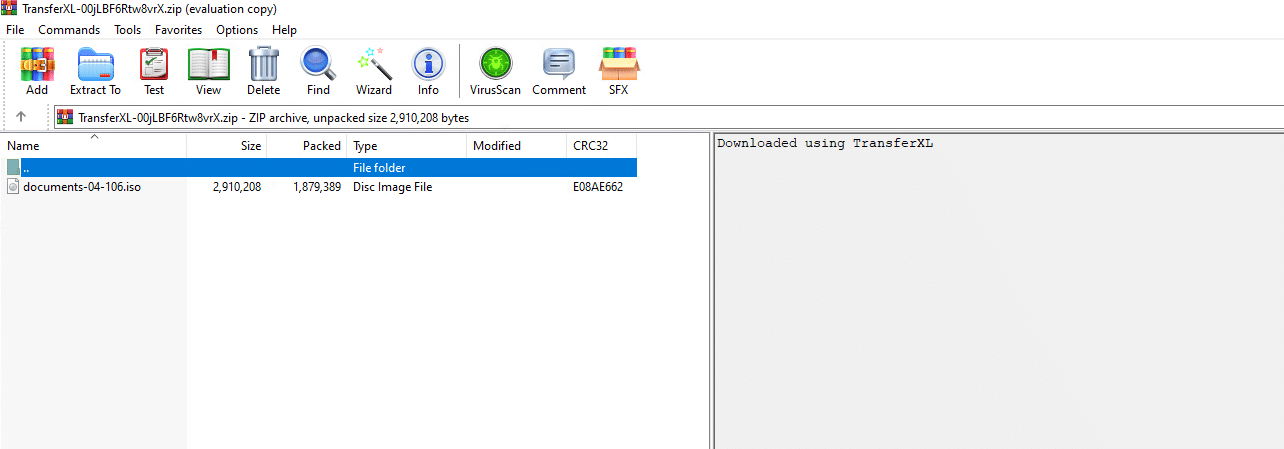
Below is an example of what the ZIP file from the TransferXL link looks like.
ZIP file download from TransferXL
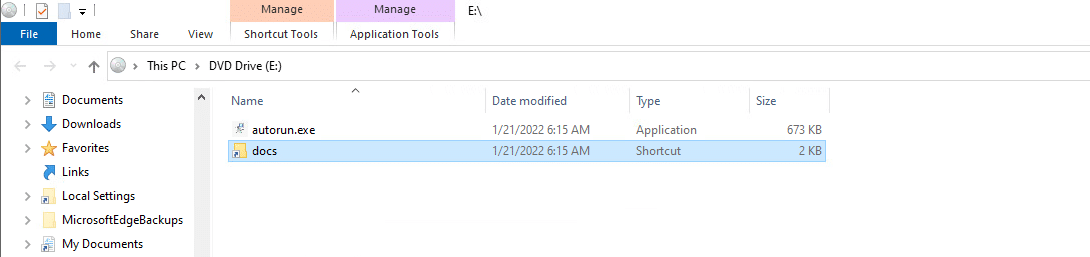
The ZIP file contains an ISO image file with the following name “documents-04-106.iso.” Note that the following ISO image file name pattern was used for all the files that we have analyzed:
- documents-[0-9]{1,4}-[0-9]{1,4}\.iso
ISO image file
From this step, threat actors rely on the victim (user) interaction with the ISO image file. The threat actors use a masquerading technique by setting the LNK file icon to be a folder icon in order to lure the victim to click on the LNK file:
ISO image file contains LNK and DLL
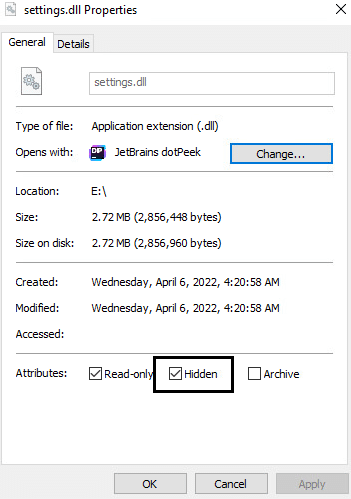
In addition, the DLL payload attribute is set as “Hidden” in order to hide the DLL payload from the user when interacting with the ISO image file:
Hidden attribute for the DLL
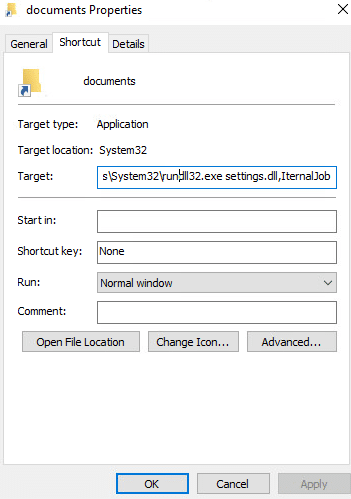
The masqueraded LNK file properties show that the execution target is as follows:
- C:\Windows\System32\rundll32.exe settings.dll,IternalJob
LNK executes the DLL via rundll32 command
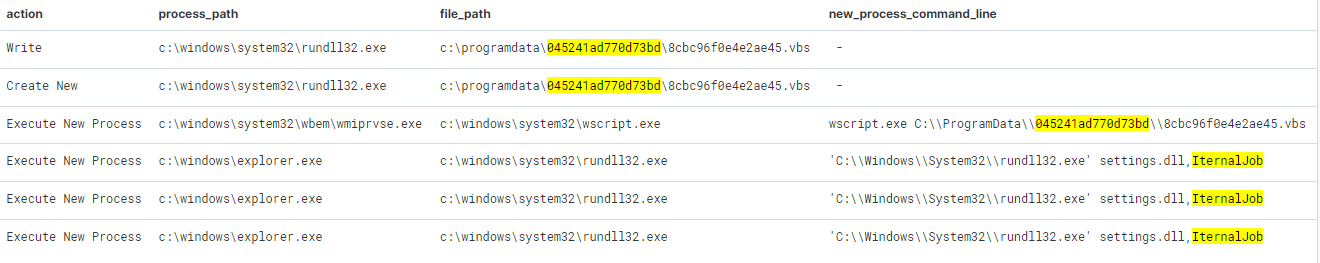
After the initial execution, the BumbleBee DLL is copied to the %programdata%/{RandomDir} directory. In addition to the DLL, a VBS script is also dropped to the same directory:
- [a-z]:\\programdata\\[a-z0-9]{16}\\[a-z0-9]{16}\.[vbs|dll]
TTPs indicators during the execution
We have other artifacts from different IR cases, where we have observed the following activity. The screenshot below shows an event that detected a creation of a payload in the %ProgramData%\{Random} directory the DLL payload is a copy of the initial BumbleBee loader that executed by Rundll32 from the ISO image file:
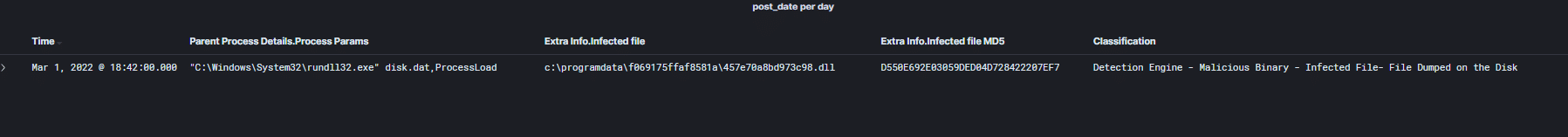
In other IR cases, we observed an execution flow that’s bit different. For example, a LNK that points to the following execution targets:
- cmd.exe /c start rundll32 neqw.dll,IternalJob
- rundll32.exe advpack.dll,RegisterOCX sysctl.exe
Persistence
We detected a scheduled task execution during the BumbleBee infection:
| Grandparent process:svchost.exe -k netsvcs -p -s Schedule
Parent process: wscript.exe [a-z]:\\programdata\\[a-z0-9]{16}\\[a-z0-9]{16}\.vbs Child process: rundll32.exe [a-z]:\\programdata\\[a-z0-9]{16}\\[a-z0-9]{16}\.dll,{Export} |
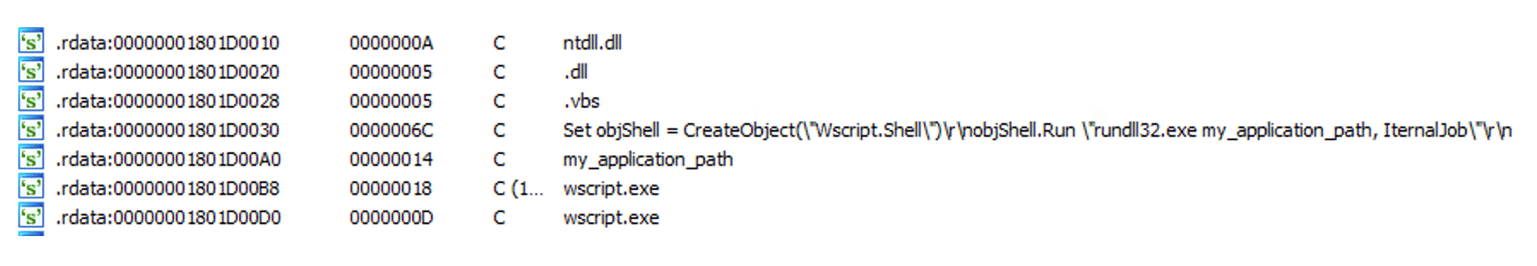
Strings from the BumbleBee loader show the VBS script and the execution method
We also observed WMI execution. The VBS file that was executed via a scheduled task, was also executed through WMI:
| Grandparent process:svchost.exe -k DcomLaunch
Parent process: wmiprvse.exe -Embedding Child process: wscript.exe [a-z]:\\programdata\\[a-z0-9]{16}\\[a-z0-9]{16}\.vbs |
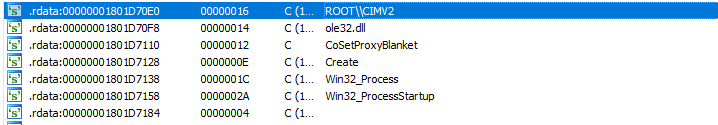
Strings from the Bumblebee loader show the WMI Win32_Process execution
Defense Evasion
In our labs, we observed that BumbleBee uses several anti-VM methods to avoid detection.
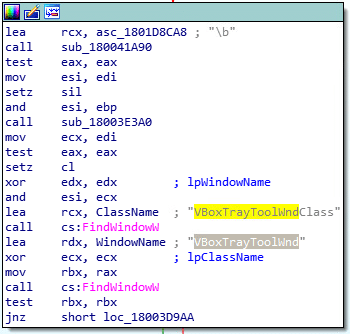
One of the anti-VM checks is related to the VirtualBox product:
Check for lpWindowName if matches VirtualBox
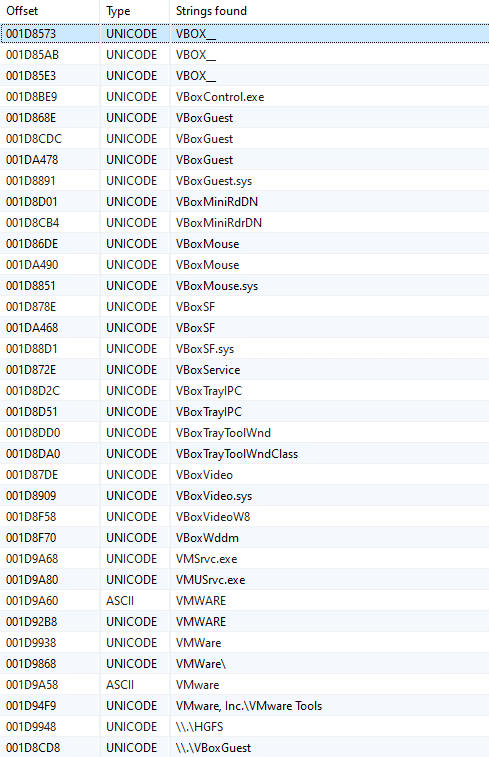
Other anti-VM artifacts were found after unpacking, as can be seen in the following strings:
List of strings that are related to VMware and VirtualBox
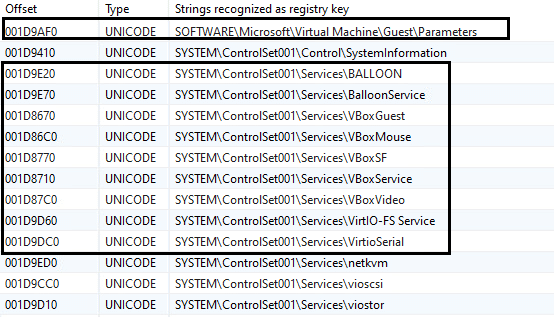
BumbleBee also detects if it is running within a VM by checking for known services that are related to different VM products:
List of services that are related to VM products
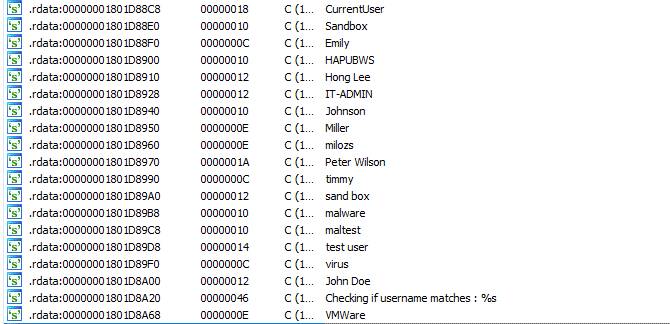
BumbleBee checks whether certain user names reside in the victim’s machine by comparing against a hardcoded list of user names. This allows BumbleBee to detect sandboxes and labs that are used for malware analysis:
List of hardcoded usernames which are related to sandboxes and labs
In addition, it uses WMI queries to collect system details and information:
- SELECT * FROM Win32_BaseBoard
- SELECT * FROM Win32_Bus
- SELECT * FROM Win32_ComputerSystem
- SELECT * FROM Win32_Fan
- SELECT * FROM Win32_NTEventlogFile
- SELECT * FROM Win32_OperatingSystem
- SELECT * FROM Win32_PnPDevice
- SELECT * FROM Win32_PnPEntity
Discovery
We found that the threat actors used the AdFind tool to enumerate and map the victim’s network. The ADFind tool was found in the %ProgramData% directory.
In the instance we observed, the following commands were used:
- adfind.exe -gcb -sc trustdmp
- adfind.exe -f “(objectcategory=group)”
- adfind.exe -f “(objectcategory=organizationalUnit)”
- adfind.exe -f “objectcategory=computer”
- adfind.exe -f “(objectcategory=person)”
Command and Control
After the initial execution, the BumbleBee process (Rundll32) communicated with the Command-and-Control server (C2). We’ve seen several C2 servers from different IR cases:
- IP: 23.82.19[.]208:443
- IP: 192.236.198[.]63:433
- IP: 45.147.229[.]177:433
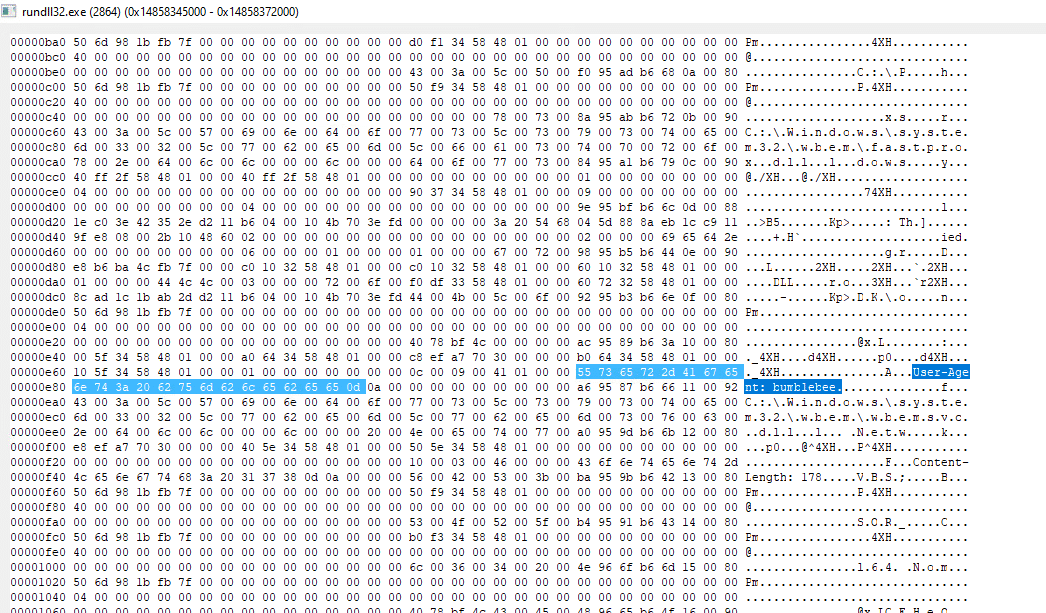
Example of the unique User-Agent: BumbleBee in the payload’s memory
Additional reference to the BumbleBee malware name
All the collected system and network information is sent to the C2 server, which sends back a response containing the next step/command to execute based on that info.
BumbleBee binary analysis
In this section, we will cover some interesting indicators and artifacts that highlighted the BumbleBee actions and heuristics. These artifacts also help us to identify the BumbleBee malware.
We analyzed several payloads and all of them had the same artifacts.
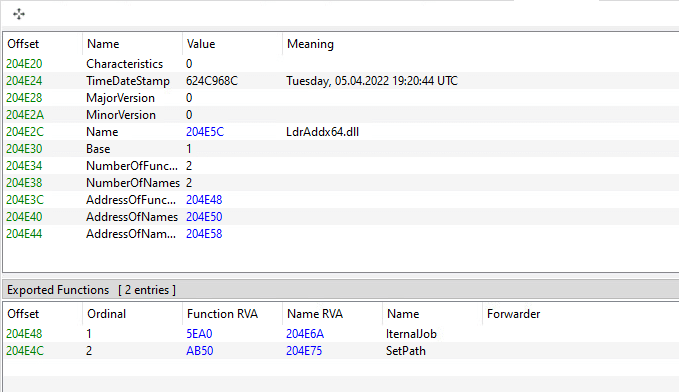
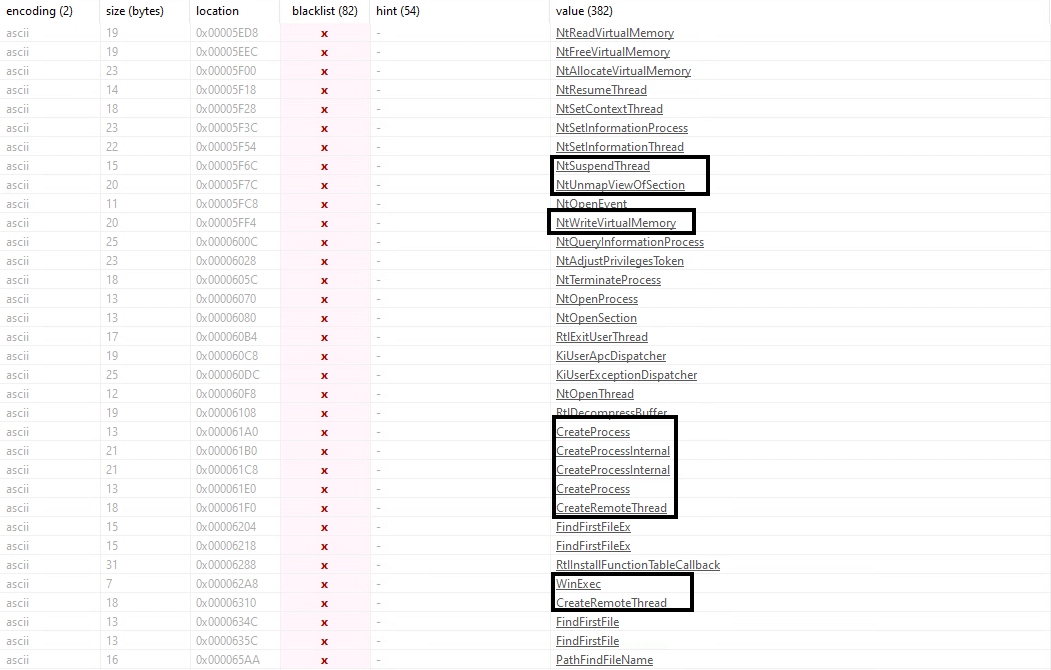
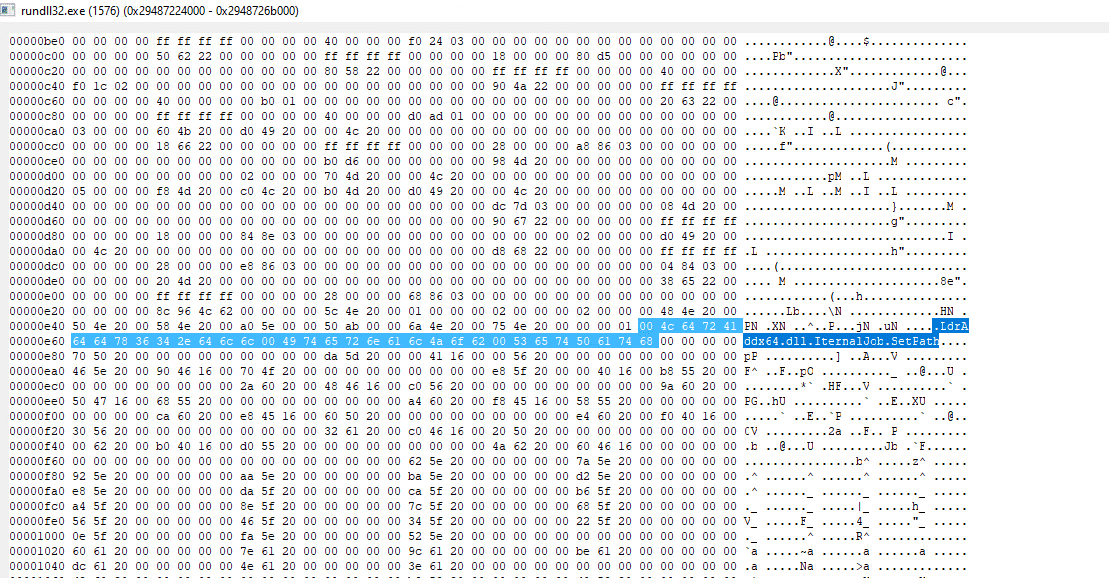
After unpacking the BumbleBee loader and by searching in the metadata of the unpacked payload, we identified BumbleBee’s internal name, “LdrAddx64.dll,” and two export functions – “IternalJob” and “SetPath.”
BumbleBee internal name, export functions, and TimeDateStamp
In the image below, we found the BumbleBee internal name and export function inside the process Rundll32.exe that executed the BumbleBee DLL loader:
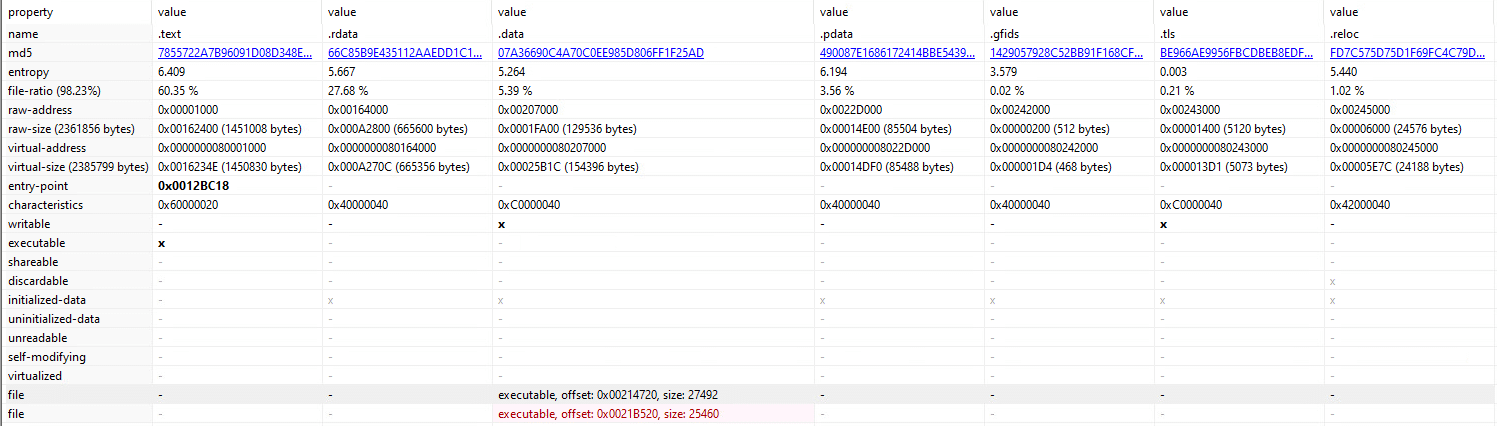
By inspecting the unpacked BumbleBee sections, we discovered that the .data section contains two executables:
PEStudio shows the unpacked Bumblebee section and highlighted the .data section
We extracted the two hidden payloads from the .data section by using Hex-Editor tool:
Hex-Editor shows 3 MZ headers: the first one is the Bumblebee, and the other two are additional payloads
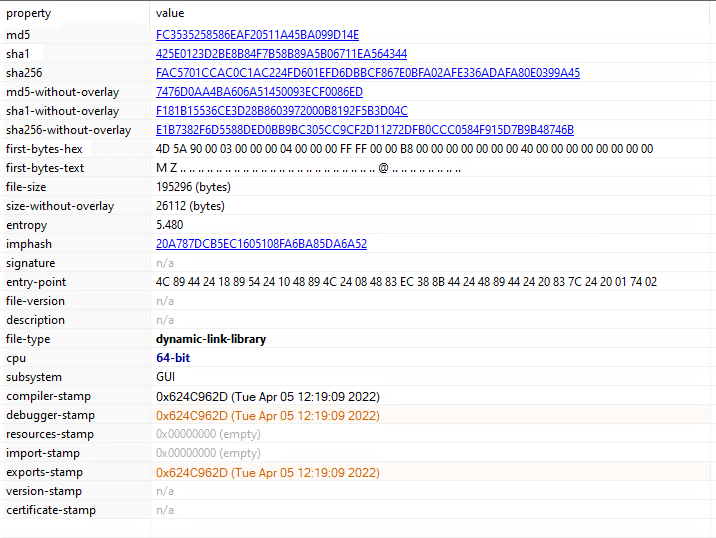
The first payload from the .data section is a 32-bit DLL payload:
PEStudio showing the payload’s metadata
We found a few interesting functions in the payload strings indicating that this payload has process injection capabilities. For example, “CreateProcess,” “NtWriteVirtualMemory,” “CreateRemoteThread,”and “WinExec.”
PEStudio showing the payload’s strings that could be related to process injection
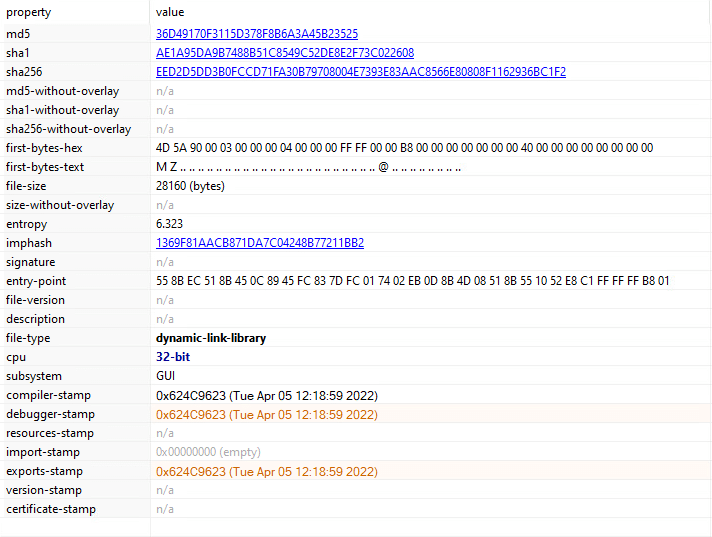
The second payload that we extracted from the .data section is a 64-bit DLL payload:
PEStudio showing the payload’s metadata
We analyzed the payload binary and noticed that this payload is responsible for communicating with BumbleBee’s C2 server:
In the strings we can see the C2 server’s IP address and port
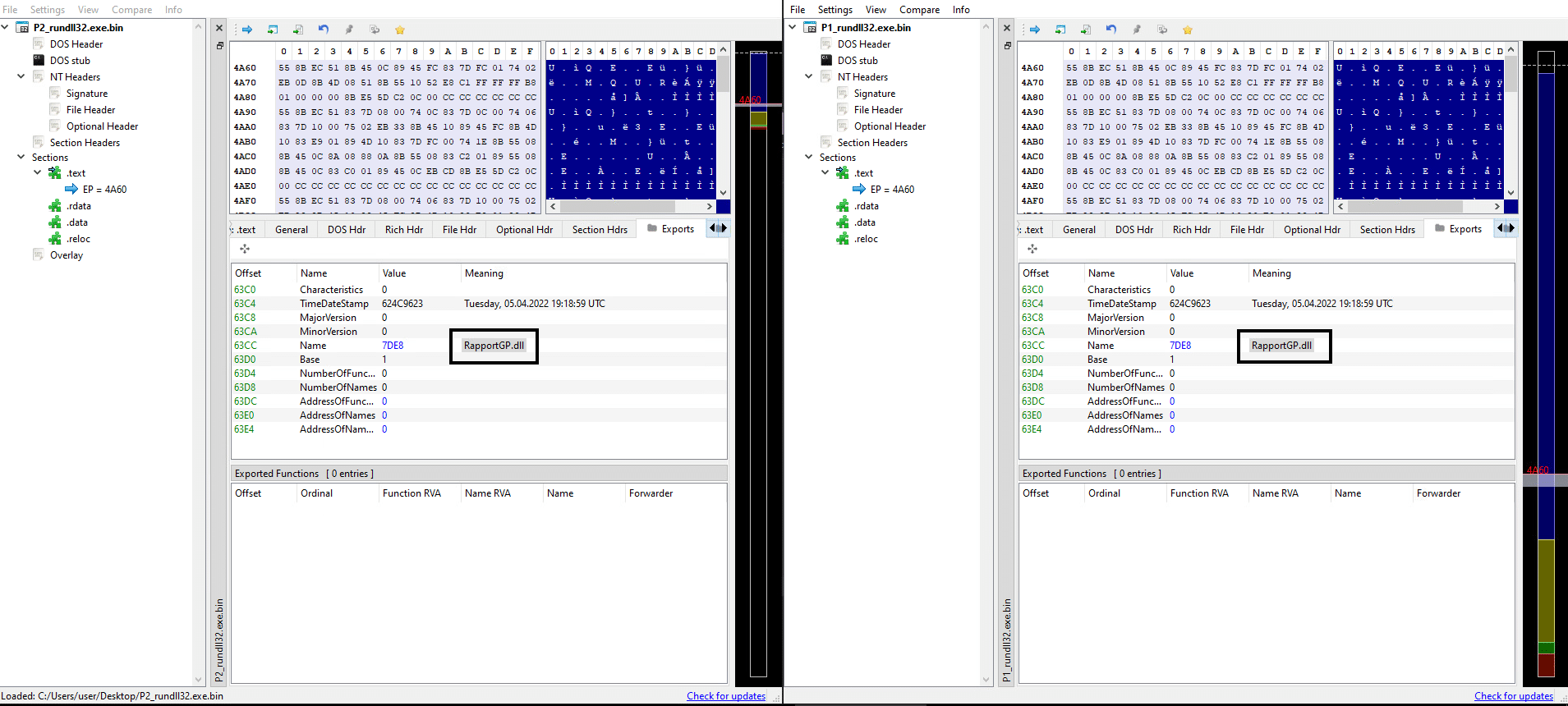
Both DLL payloads have the same internal name “RapportGP.dll.” An interesting point regarding the payloads internal name is that there is a legitimate DLL named “RapportGP.dll” that is part of a “Trusteer Ltd” product from a computer security division of IBM.
Payloads internal name and TimeDateStamp
Final notes
BumbleBee threat actors are not the first to change the initial access method from malicious office documents to malicious ISO image files. The ISO image file abuse was also seen a few years ago, but in recent months, we have observed an increase in “ISO campaigns.”
Different threat actors abuse ISO image files to deliver their payloads. For example, BazarISO deploys Bazarloader, and IcedID started to use ISO image files instead of MalDocs like in the two examples below.
Documents-17.iso (Bazarloader)
Invoice_pdf_1.iso (IcedID)
In most of the cases, we’ve seen that during different IR cases, the campaigns escalated to full-blown ransomware attacks. We believe that IAB groups work and collaborate with ransomware affiliates like CONTI, LockBit, AvosLocker, and more. For example, we observed an IcedID infection that leads to CONTI ransomware attack (Shelob Moonlight).
The Orion team is constantly monitoring BumbleBee and the IAB group’s activities closely and analyzing them to better understand their motivation. As we learn more, we will publish our findings and artifacts to share additional insights for BumbleBee infection to ransomware post-attack chain.
We’re expecting to see more malware campaigns that will use the ISO delivery method in the near future. So, stay vigilant.
As a final note, we’d like to share these indicators of compromise with you.
Indicators of compromise:
BumbleBee payload 88F5AE9691E6BCDD4065A420EAFAF3E3AA32C69605BF564A42FFD8ECD25C9920 4a49e2f06ba48d3a88fdeb83fb8021f3d165535e8ea5319b16a7ebe4da9c0751 08cd6983f183ef65eabd073c01f137a913282504e2502ac34a1be3e599ac386b 186145f84ed6a473ec6bc4afa66bff156057888938793b12afd17659041ddbba 4063fab9176db3960fa6014173b6c7ba52f19424887f5a6205ff73aa447ada61 53b3ebaa3c485772f8e6abaa0f366ef192137496a7064e015ced4e6fc204b3c8 d74a3f9b35d657516eb53d4e70582f93d22077d3e0936758cc4ef76d5171075d 8f47c3962a7c418bae71fec42bbca9524b72f8f0fd2dd81d1175138f7d20b2f7 c97b8bffcbe424cbc2a6e1135068d071c6f4e8f020fccd2db3dbee3aa80102ac BumbleBee C2 server IP: 23.82.19[.]208 Port 443 IP: 192.236.198[.]63 Port 433 IP: 45.147.229[.]177 Port 433 Cobalt Strike C2 server hojimizeg[.]com - 45.147.228[.]197 notixow[.]com - 23.19.58[.]154 rewujisaf[.]com - 142.234.157[.]176
We hope this was helpful. And remember to check our blog page and follow us on social media to see when we publish updates.
Have questions? Let us know.