PrintNightmare – Windows Print Spooler Patched Vulnerability Remains Exploitable
Introduction
On June 29th, security researchers demonstrated that the patch Microsoft released for a new vulnerability in the Windows Print Spooler service – which was classified as privilege escalation, and which provides authenticated attacker with the ability to perform RCE (remote code execution) in SYSTEM context – is in fact still exploitable.
The “PrintNightmare” remote code execution (RCE) vulnerability that affects Windows Print Spooler is different from the issue addressed by Microsoft as part of its Patch Tuesday update released earlier this month while warning about exploitation attempts targeting the flaw. Microsoft is tracking the security weakness under the identifier CVE-2021-34527.
CVE-2021-1675, originally classified as an elevation of privilege vulnerability and later revised to RCE, was remediated by Microsoft on June 8, 2021.
Microsoft noted in its advisory that PrintNightmare is distinct from CVE-2021-1675 since the latter resolves a separate vulnerability in RpcAddPrinterDriverEx() and that the attack vector is different.
On July 15th, Microsoft shared a security update guide on another vulnerability affecting the Windows Print Spooler service – CVE-2021-34481. This vulnerability can be exploited to achieve elevated privileges on the local machine.
Vulnerability overview
“PrintNightmare” – CVE-2021-34527 is a vulnerability that allows an attacker with a low-privilege domain user account to take control over a server running the Windows Print Spooler service, which is running by default on all Windows servers and clients.
The Print Spooler service is vulnerable due to the fact that it fails to restrict access to the RpcAddPrinterDriverEx() function, which can allow a remote authenticated attacker to execute malicious code with SYSTEM privileges.
In contrast to the recently patched ‘PrintNightmare’ vulnerability, the new shared vulnerability (CVE-2021-34481) is focused on gaining elevated privileges locally.
The privilege elevation vulnerability can be exploited once the Windows Print Spooler service inappropriately performs a privileged file operation. Prior to the exploit, the attacker must have access to the local machine to take advantage of this vulnerability. From the moment the attacker manages to successfully exploit this vulnerability, they can run arbitrary code with SYSTEM privileges. They could then view, change or delete data, install programs, or create new accounts with full user rights.
Vulnerability patch
MSRC has released a patch that fixes the RCE “PrintNightmare” vulnerability. You can find the patch here.
As of now, MSRC hasn’t released an official patch for the CVE-2021-34481 vulnerability. You may follow our recommendations to mitigate this vulnerability through Cynet360 Console.
Cynet protection and recommendations
Protection
The Cynet research team already deployed new detection rules aimed to detect and prevent exploitation attempts of this vulnerability, and is currently working on additional detections to increase the visibility around it.
The CyOps team monitors our customers’ environments 24/7 and will be in contact in case any indicators of this vulnerability are detected in your environment.
Recommendations
We highly recommend disabling the Print Spooler service on all domain controllers (DC) within the organization. Additionally, we recommend disabling this service on assets where it’s not essential to maintain regular business operations.
Please follow these simple steps:
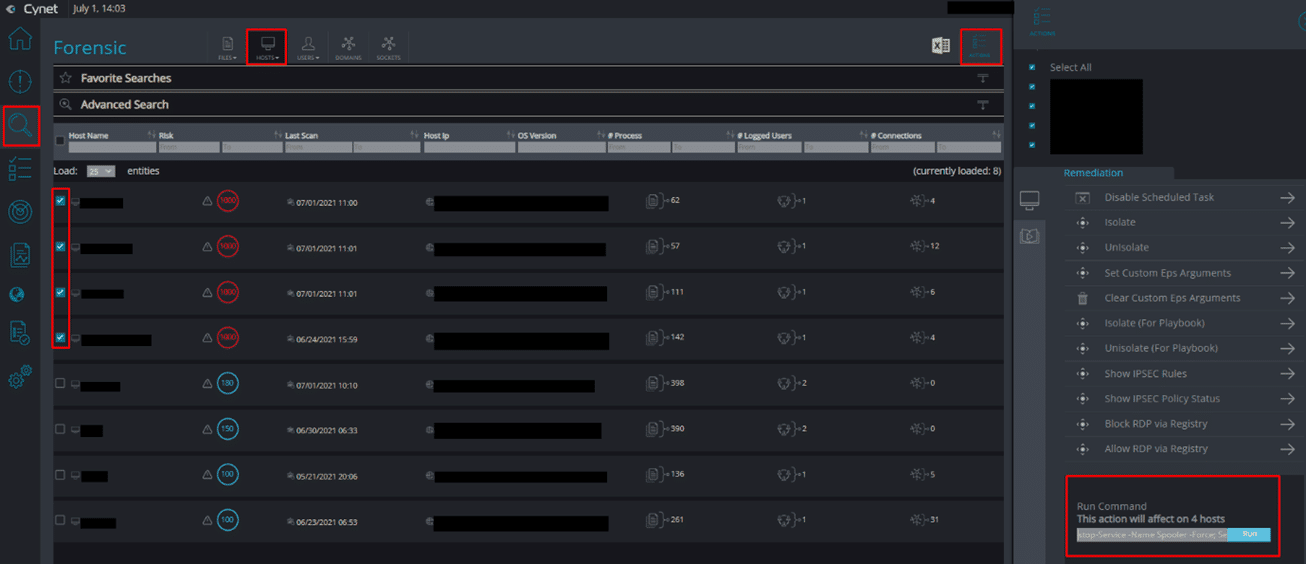
Forensics → Hosts → Tick all domain controllers → Actions → Run Command →
Powershell.exe Stop-Service -Name Spooler -Force; Set-Service -Name Spooler -StartupType Disabled
Forensics
Cynet360 Forensics can search for artifacts that can provide strong indicators of exploitation attempts of this vulnerability based on the POCs observed in the wild. The following path has been observed while using the POCs as a part of the exploit. The path can be used to store malicious dll’s which in turn are being loaded by spoolsv.
Please follow these steps to find artifacts using Cynet360:
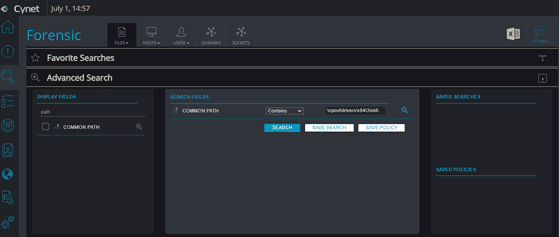
Figure 01: Forensic → Files → Advanced Search → Common Path → Contains → \spool\drivers\x64\3\old\ → Save Policy/Search
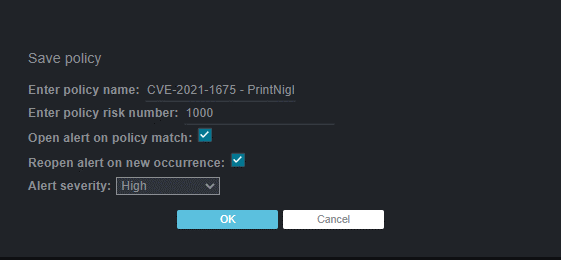
Figure 02: Fill in the fields as shown below:
- Policy name: CVE-2021-1675 –PrintNightmare
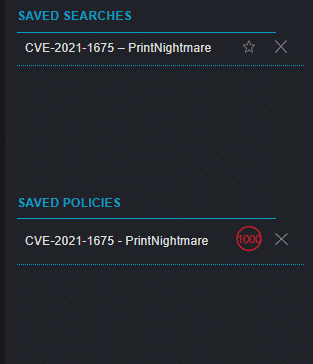
Figure 03: You can find the saved policy/search in the Advanced Search of the Forensic:
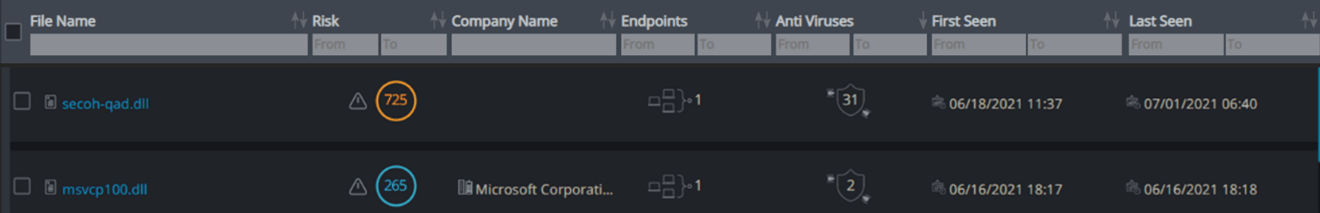
Cynet360 allows you to automatically investigate the dll’s by presenting the risk score, company name and the number of vendors which classified it as malicious in VT (presented under the “Anti Viruses” field, the shied icon is clickable and allows you to navigate to the virustotal website).
If one of the detected dll’s do not exist in VT or have a high-risk score and are unfamiliar to you, please feel free to contact the CyOps team.