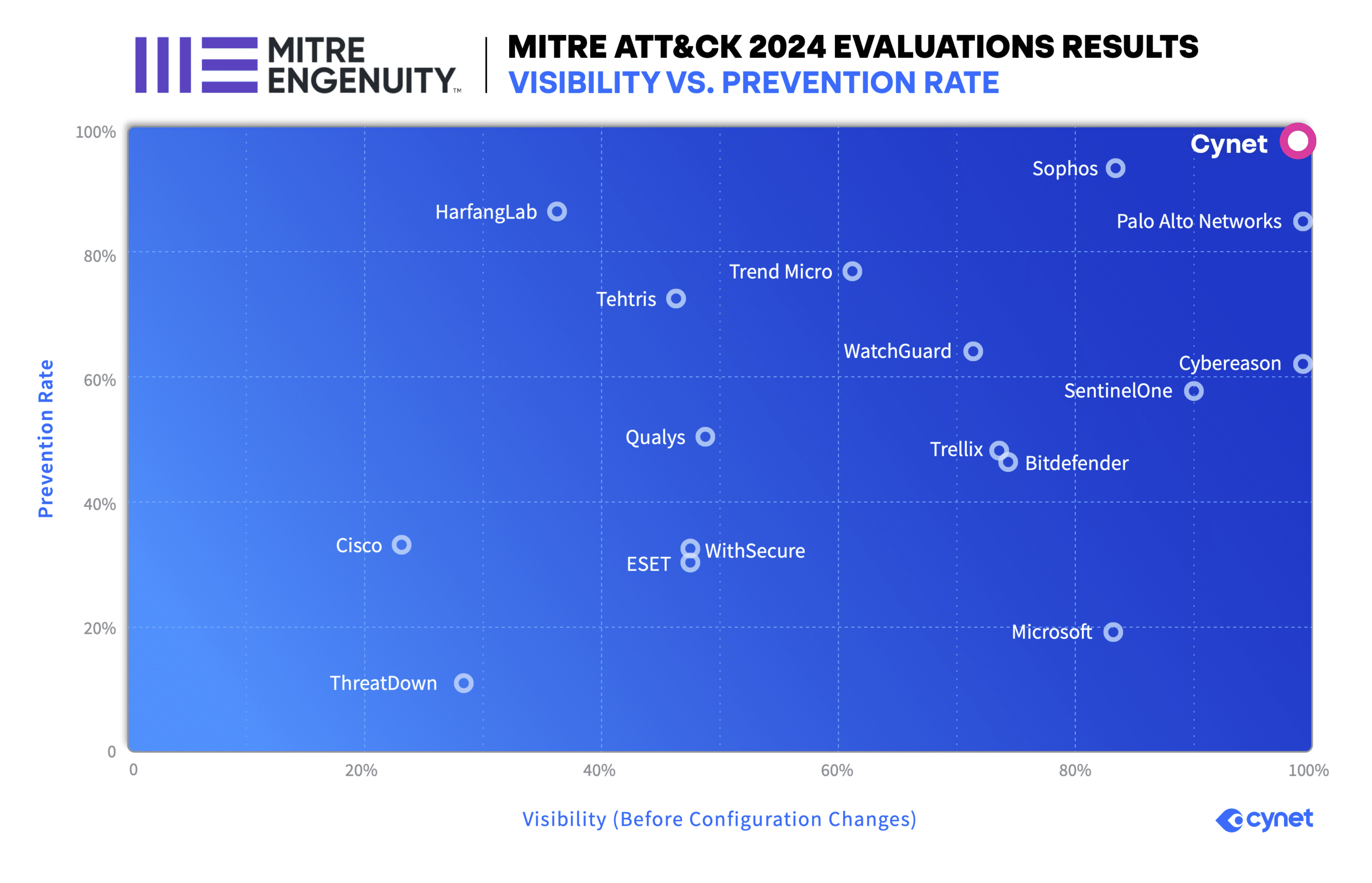
100% Protection & Detection in the 2024 MITRE ATT&CK Evaluation
Across small-to-medium enterprises (SMEs) and managed service providers (MSPs), the top priority for cybersecurity lea… Read More
ALL

Across small-to-medium enterprises (SMEs) and managed service providers (MSPs), the top priority for cybersecurity lea… Read More

The ransomware group Babuk claims to have breached the French telecommunication company Orange, and its… Read More

Key points ClickFix is a relatively new social engineering tactic by which threat actors trick users… Read More

Cynet’s Orion Threat Research Team has tracked a large-scale campaign to distribute the Lumma Stealer… Read More

Cost savings and business benefits were quantified in “The Total Economic Impact™ of Cynet All-in-On… Read More

The Qualys Threat Research Unit (TRU) uncovered the CVE-2024-6387 vulnerability, also called regreSSHion…. Read More

The notorious hacker group ShinyHunters is back in the news after claiming responsibility for separate hi… Read More

LabHost Phishing Platform Shut Down by Global Authorities Cybercriminal techniques constantly adapt to e… Read More

Students aren’t alone in having their skills tested in K-12 schools. Education-sector IT teams face mou… Read More
Search results for: