Executive Summary
Cynet CyOps security experts detected an active exploitation of Wing FTP server instance that allowed anonymous connections. CVE-2025-47812 represents a critical authentication remote code execution (RCE) vulnerability in Wing FTP Server, that impacts both its user and administrative web interfaces. Here’s a breakdown of the exposure, and Cynet’s recommendation for patching, remediation, and how you’re protected with Cynet’s All-in-One platform:
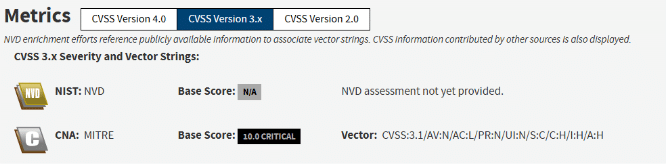
- Vulnerability: CVE-2025-47812 is a post-authentication remote code execution flaw in Wing FTP Server affecting both its user and administrative web interfaces.
- Attack Vector: An attacker with a valid user or even anonymous login capability can inject null (%00) bytes into the username parameter of specially crafted HTTP requests. This bypasses standard input validation and embeds arbitrary Lua code into server session files.
- Privilege Escalation: Injected Lua commands execute with SYSTEM privileges on Windows and root privileges on Linux, granting full control of the affected server.
- Ease of Exploitation: Only requires a valid (or anonymous) login plus a single malformed request, earning a CVSS 3.1 base score of 10.0.
Timeline:
- May 14, 2025: Wing FTP Server published an advisory and released a patched version 7.4.4.
- June 30, 2025: Public proof-of-concept details released.
- July 10, 2025: CISA added CVE-2025-47812 to its Known Exploited Vulnerabilities.
Recommendation: Immediately upgrade all Wing FTP Server instances to version 7.4.4.
Cynet customers are fully protected against CVE-2025-47812 by our Zero-Trust framework. Cynet’s All-in-One Cybersecurity Platform continuously monitors exploit attempts and immediately flags any unauthorized SYSTEM-level shell processes. We’ve also released a public scanner that organizations can run to identify any remaining vulnerable Wing FTP Server instances in their environments. Customers who follow Cynet’s Best Protection Practices have these protections enabled automatically, so no additional action is required..
The CyOps team is available 24/7 for any questions or concerns and will gladly assist with a timely resolution to any issue.
Cynet’s Response
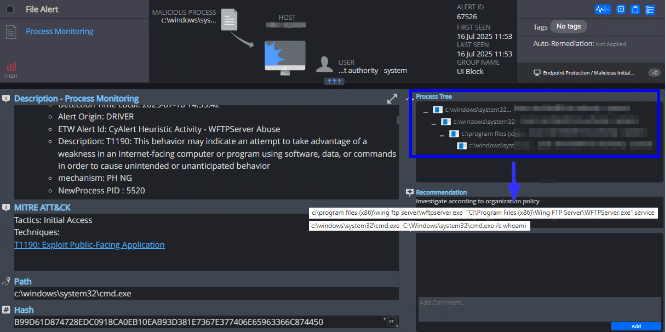
Cynet All-in-One Detection Alert
When Cynet’s All-in-One Cybersecurity Platform detects any activity matching the CVE-2025-47812 exploit pattern – specifically null-byte injection into Wing FTP Server, followed by the spawning of a SYSTEM-level shell with wingftp.exe as its parent process—it immediately generates a high-severity alert mapped to MITRE ATT&CK T1190 (Exploit Public-Facing Application).
Proactive Detection Scanner
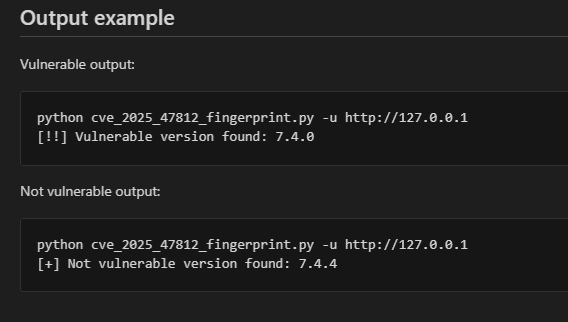
As part of Cynet’s response to the vulnerability, a specialized Python scanner was created to safely check whether a Wing FTP server is vulnerable or not. The scanner is appended in the Appendix section with technical setup and execution details.
The scanner is able, with a single HTTP request, to acquire Wing FTP’s version and determine whether it is vulnerable or not, without executing the vulnerability or posing any risk to the user.
To use the scanner, the user needs to install Python 3 and then perform the following operations:
- Unzip “Cynet_CVE_2025_47812.zip” to “Cynet_CVE_2025_47812” folder
- Open a CMD in the “Cynet_CVE_2025_47812” folder
- Run the following command: “python -m pip install –r requirements.txt”
- Once the command is finished, you can run “python cve_2025_47812_fingerprint.py -u “http://myurl” and replace “http://myurl” with your Wing FTP server URL.
- After you run the script, it will print whether this server is vulnerable or not.
Technical Information
The vulnerability is caused by not sanitizing the user’s input, leading to a serialization parsing error that eventually leads to Lua code execution.
The flow begins when a user triggers authentication by submitting their credentials to the loginok.html endpoint:
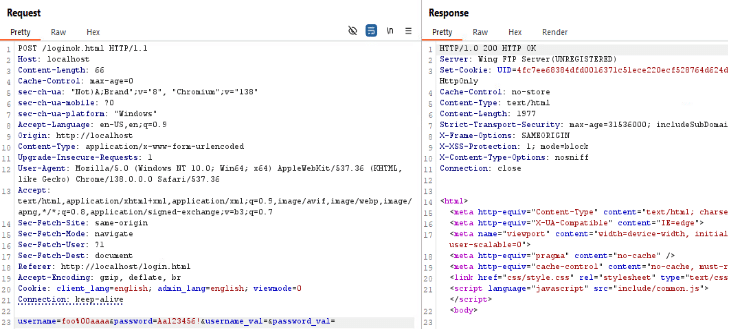
When we add “%00” to the input, the user can authenticate successfully. This reveals a flaw in the sanitization of user input. The presence of “%00” indicates the end of the string, which means that any characters following are ignored during validation.
This is particularly interesting because the session files are saved in Lua format:
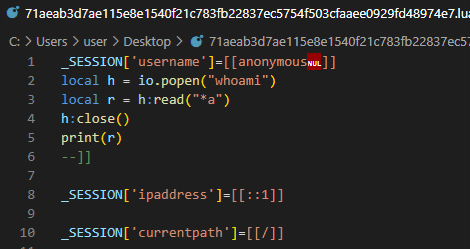
This is an example of a payload using anonymous login to execute the command “whoami” and print the response.
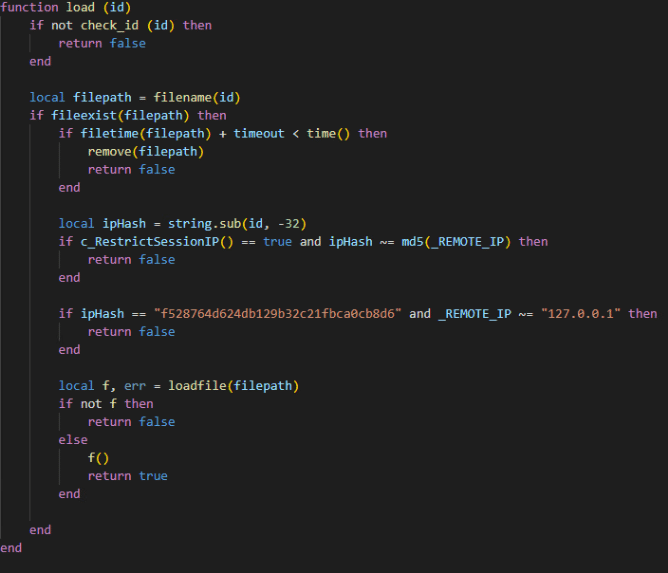
This is the logic that uses the session file: Whenever anyone is using the session file (for example, accessing endpoints that require authentication), the session file is loaded via the load file function and then executed to load the code.
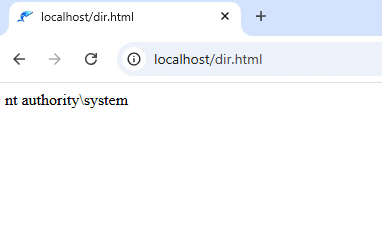
As we can see, once the malicious session file is loaded, the user that runs the server (NT Authority\System) is returned, and code execution is achieved.
Recommended Mitigation
Cynet recommends updating the Wing FTP servers to version 7.4.4, which is not vulnerable. The update process can be either via downloading version 7.4.4 from Wing FTP’s official website or from Wing FTP’s administrator’s panel:
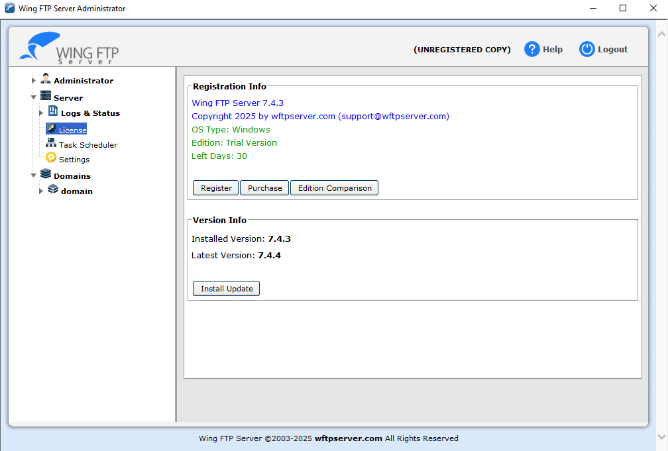
- Log in with your administrator to Wing FTP Server Admin
- Click on “Server” and then on “License”
- Under “License”, you will see the “Version Info” segment and see that you can update to version 7.4.4.
- Click on the “install update” button to update.


