Stop Network Threats. Block Malicious Domains.
Network Security
Attackers exploit network blind spots to move undetected. Cynet eliminates those gaps with a unified, AI-powered platform that automatically detects, isolates, and neutralizes threats across your entire network, backed 24x7 by CyOps security experts.
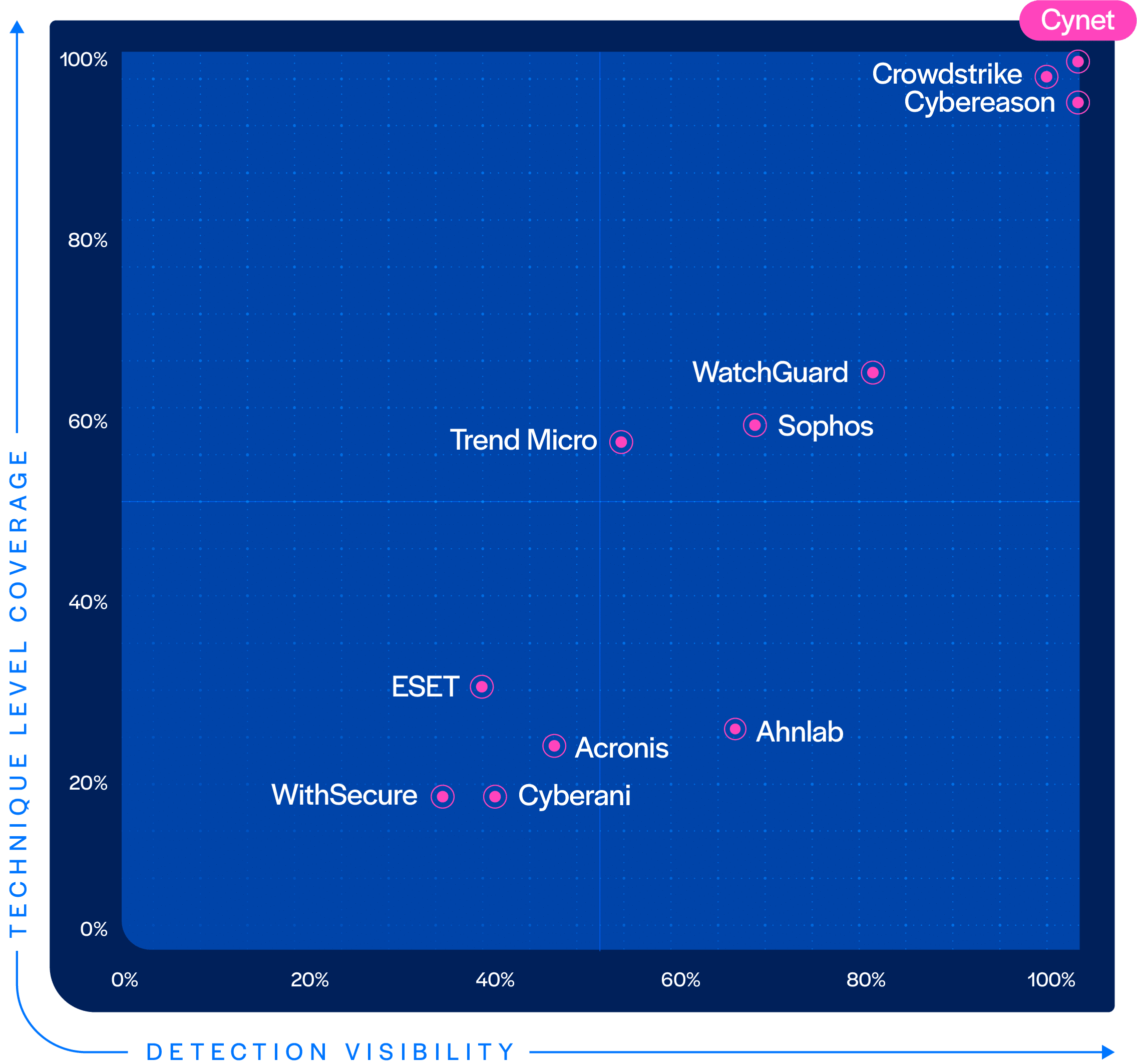
Top MITRE ATT&CK Performance
The 2025 MITRE ATT&CK Evaluations included assessments of Endpoint Operating Systems across Windows and Linux environments. Cynet’s EDR, EPP, and ESPM capabilities delivered exceptional results with 100% Detection Visibility, 100% Protection, and 100% Technique-Level Coverage, with zero false positives, and zero configuration changes in the Initial Run.
Not a single vendor performed better than Cynet.
Cynet detects stealthy threats and anomalous behaviors across your network, analyzing interactions with devices and users to provide high fidelity threat detection. Network signals are combined with other Cynet native telemetry for unparalleled threat visibility and detection accuracy.
01

Network Scan Detection
Identify patterns of activity indicative of malicious network scanning activity.

DNS Attack Detection
Identify a variety of attacks targeting the DNS infrastructure.

Deception
Deploy decoy hosts and servers, and monitor for unauthorized access.

Tunnel Exfiltration Detection
Protect against exfiltration of sensitive data even through encrypted communication pathways.

Risky Connection Detection
Identify active communication with malicious sites to protect against malware distribution, phishing, and known C2C based communication.

External Attack Surface Management
Identify vulnerable ports and suspicious port scanning activities to minimize the risk of adversary exploitation.

Domain Filtering
Prevents endpoints from connecting to malicious or compromised websites.

Domain Category Filtering
Configure and enforce granular policies based on domain categories, allowing or blocking website access based on content (e.g., gambling, social media, etc.).

Flexible Security Controls
Choose between detection and prevention modes to either alert or block connections to malicious domains, providing adaptable security measures.

Monitor Windows Endpoint Browsers
Monitor all Windows-based endpoint browsers and processes regardless of endpoint location or connection (in/outside the corporate firewall).

Network Protocol Protection
Protect across all browsers and network protocols (ex., HTTP, HTTPS, TCP).

Configurable Allowlists
Allowlists for safe domains and alerts are configurable.
This capability restricts access to specific domains and leverages domain categorization to block entire categories of potentially harmful websites.
02
Create precise, category-based web policies for enhanced control over internet access. Configure which categories to track or block, directly from the Cynet UI.
03
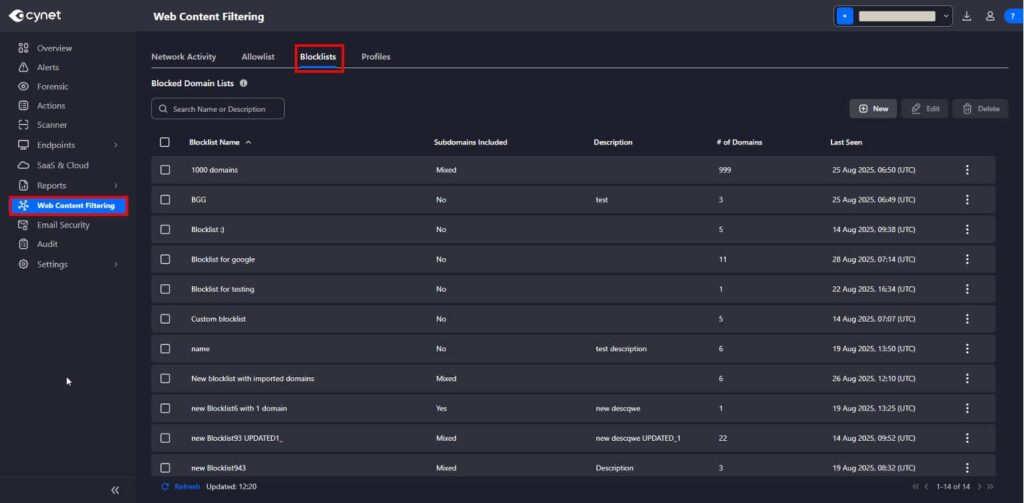

Block Custom Domains
Choose from existing content filtering categories or create custom domain-based blocklists applied at the profile level, or applied to groups.

Restricted Site Warnings
Displays a pop-up alert when a user tries to access a blocked website, showing the domain, category, and reason for restriction.
See Cynet’s Security Solutions in Action
Experience how Cynet unifies, automates, and accelerates security.