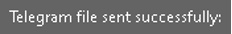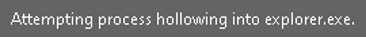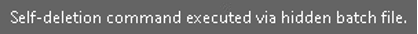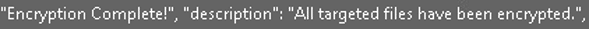BQTLock is a sophisticated ransomware variant operating within the Ransomware-as-a-Service (RaaS) ecosystem. It specifically targets Windows-based environments.
Upon infection, it systematically encrypts user files and appends the “.bqtlock” extension, rendering data inaccessible without a decryption key.
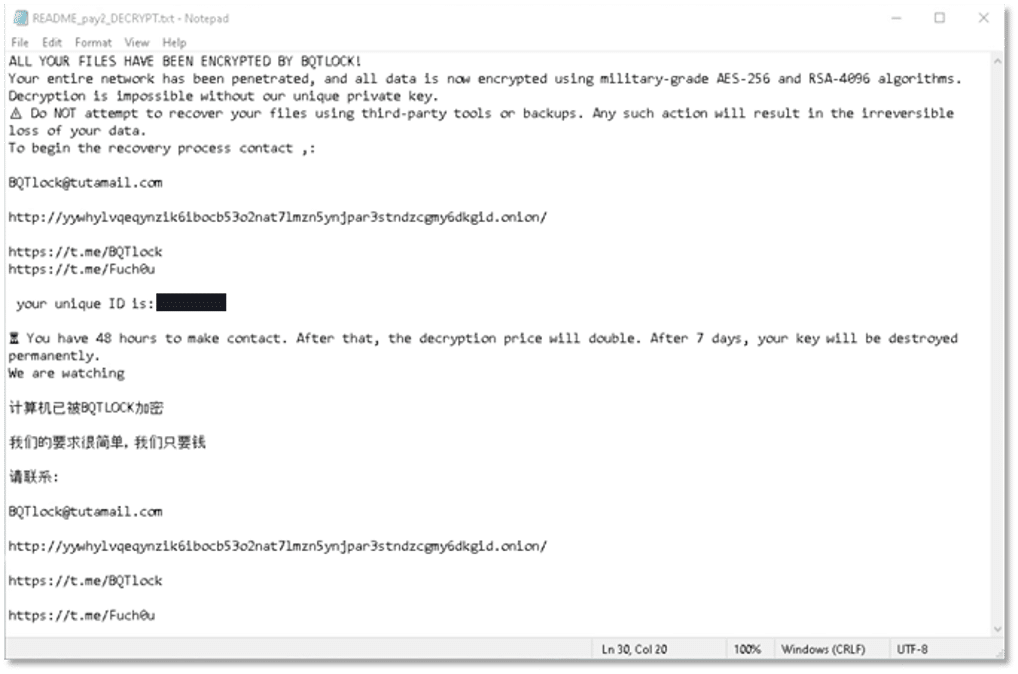
The attackers’ primary objective is financial extortion, pressuring victims to pay a ransom to regain access to their data. Notably, the ransom demand escalates if payment is delayed, doubling after a set period.
The threat actors further intensify the sense of urgency by warning that after seven days, all decryption keys will be permanently destroyed, along with the encrypted data, effectively eliminating any chance of recovery. This aggressive timeline and punitive escalation strategy are designed to coerce rapid compliance and maximize profit.
Static Analysis
Through static analysis of this file and its strings, we can understand BQTLock’s functionality and capabilities.
Reviewing the file’s strings data shows that the file may use the “Sleep” API function. This function may be abused by threat actors to delay the execution of potentially malicious commands thus avoiding sandbox detection by triggering their timeout set for file scanning.

The API function “IsDebuggerPresent” may be used by the file, allowing it to detect whether a debugger is currently running on the host. Malware uses this function to find whether the file has attempted to be analyzed, and if so, usually results in it behaving differently than intended to avoid detection and analysis. For example, the file may alter its behavior to mask itself as benign, terminate itself, or even delete itself from the host entirely.

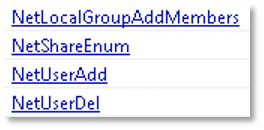
The presence of the following strings indicates that the file may leverage Windows API functions to perform operations such as enumerating shared network resources, creating user accounts, adding users to local groups, and removing existing users.
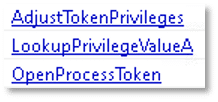
The executable demonstrates the ability to access and manipulate process-level access tokens, modify associated privileges, and retrieve the Locally Unique Identifier (LUID) corresponding to specific privilege names on the system. These capabilities are commonly leveraged by malware to facilitate process injection and escalate privileges within the target environment.
The file may use the following API functions to suspend threads, allocate virtual memory, and write to the memory of a process, resulting in process injection. This method is commonly used by malware to evade security measures and potentially escalate privileges.
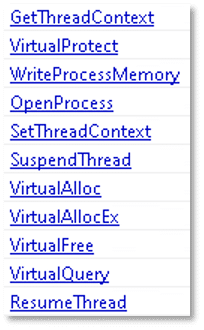
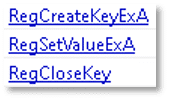
The file exhibits functionality to create registry keys, assign values to them, and properly close handles to specified registry paths. These capabilities may be indicative of attempts to establish persistence or modify system configurations.
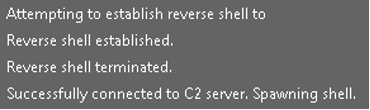
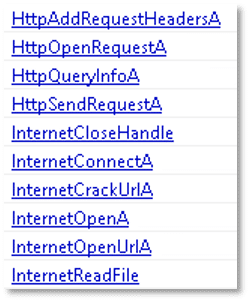
The presence of the following strings suggests that the file is capable of initiating HTTP requests to a remote server. It also demonstrates functionality for establishing HTTP and FTP sessions with specified sites, reading data via handles obtained through “InternetOpenUrl” API function, and closing internet handles. These capabilities are commonly associated with command-and-control (C2) communication and data exfiltration.
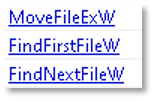
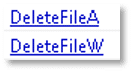
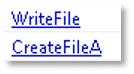
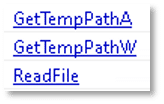
The file has the capabilities to search for, create, modify, and delete files, as well as retrieve the path to the system’s temporary directory. This behavior may indicate an intent to create or manipulate files on the system and locate the temporary directory, which is often used by malware for additional installations.
The following API function suggests that the file may perform encryption.

Among the file’s strings, several interesting entries were found:
- Indicators of Reverse Shell and Command-and-Control (C2) Communication Capabilities:
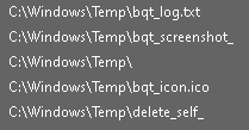
- Potential Files Created by the Executable:
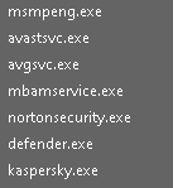
- The executable may attempt to detect and terminate processes associated with various security products to evade detection and disable protective measures:
- The executable may utilize Telegram as a channel for data exfiltration, potentially enabling remote communication and unauthorized transfer of sensitive information:
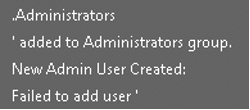
- Strings potentially indicating the creation of an Administrator user account:
- Strings potentially suggesting the executable’s intended functionality or behavior:
- Strings indicating completion of the encryption process:
Dynamic Analysis
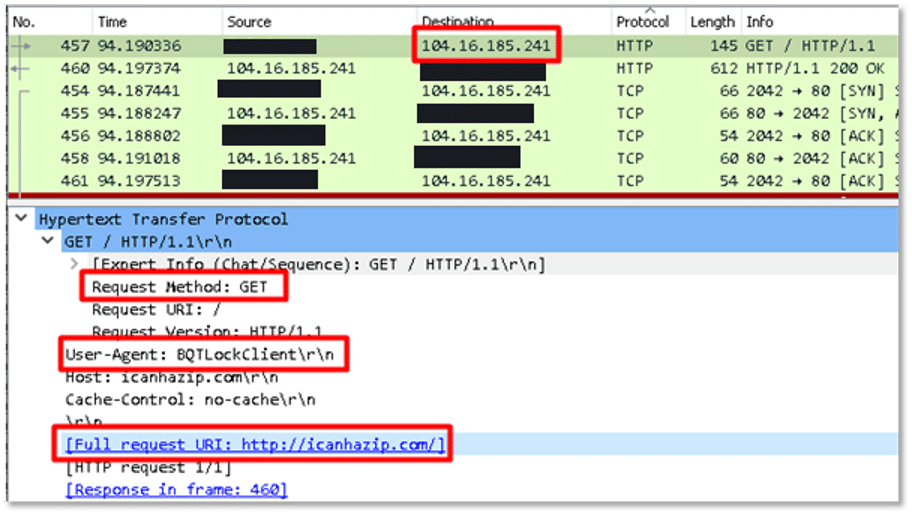
Upon execution, the ransomware attempted to contact the IP address “104[.]16[.]185[.]241” over HTTP. The request included a custom User-Agent string: “BQTLockClient”, indicating the ransomware variant. It also reached out to the domain “hxxp[:]//icanhazip[.]com”.
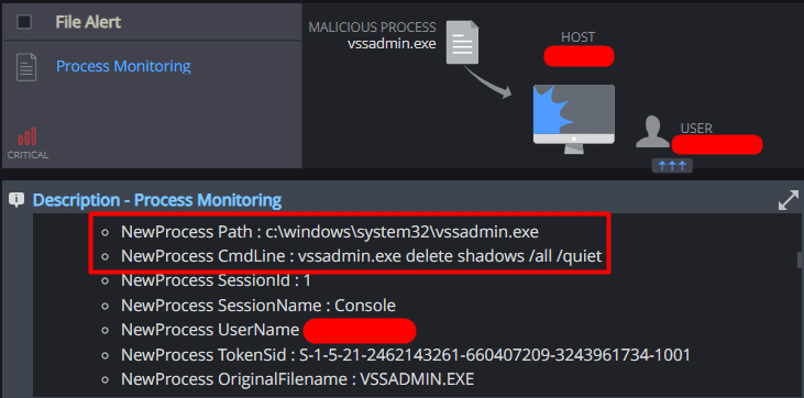
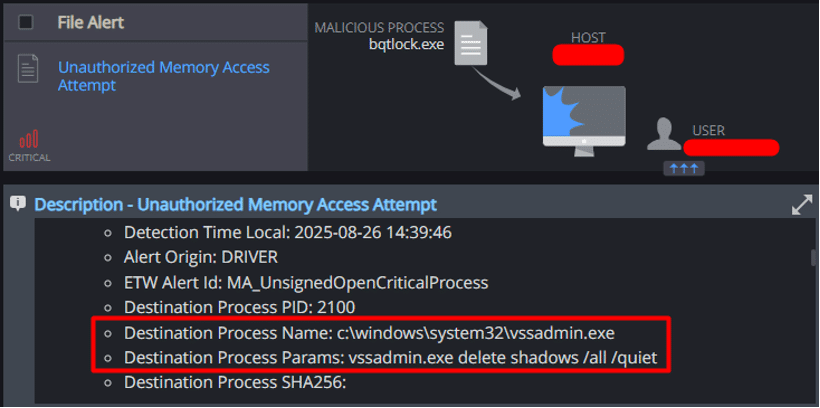
The process attempted to use “vssadmin.exe” and “wmic.exe” to delete all existing shadow copies. This behavior is consistent with ransomware tactics aimed at preventing system recovery and obstructing forensic analysis.
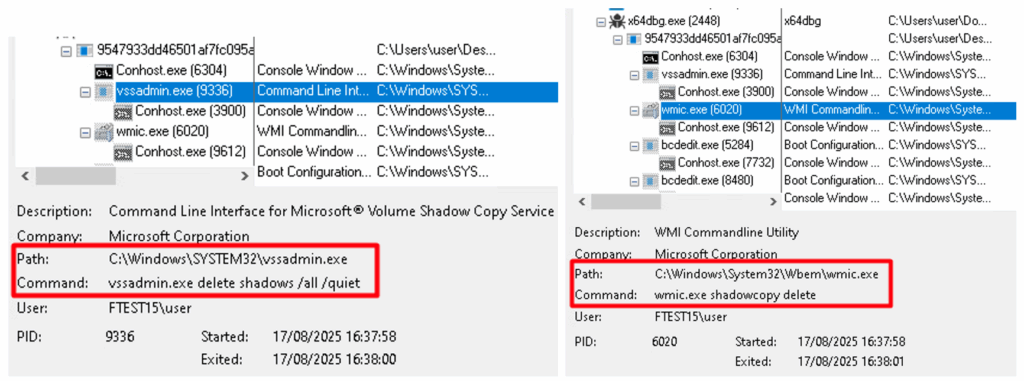
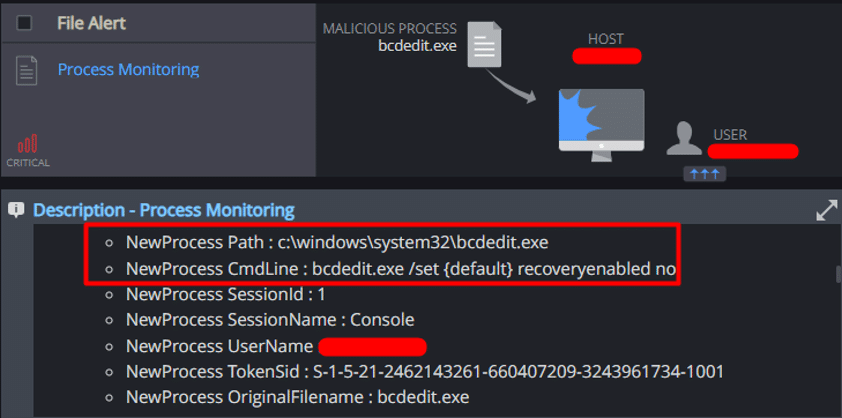
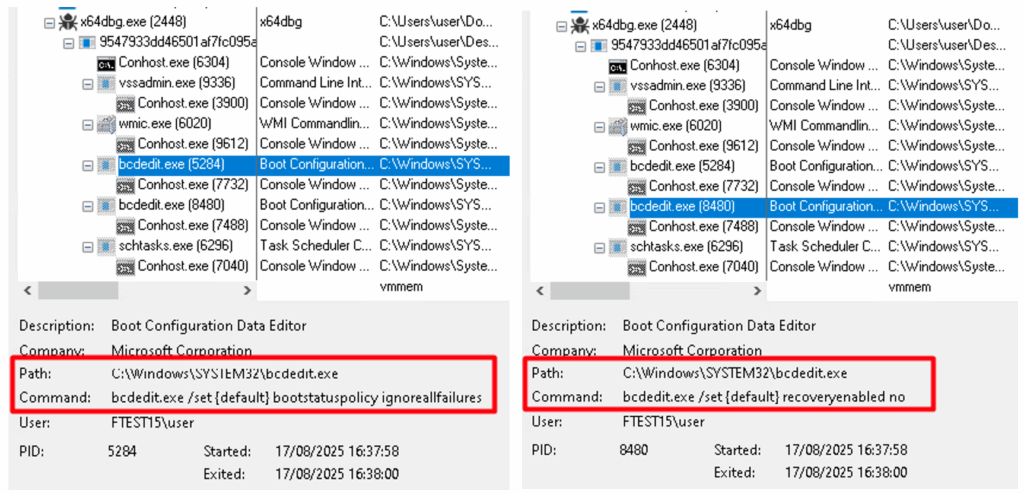
Additionally, it spawned “bcdedit.exe” as a child process to modify boot configuration settings. Specifically, it attempted to disable Windows boot failure detection and recovery mechanisms, likely to prevent the system from entering recovery mode and to ensure uninterrupted execution post-infection.
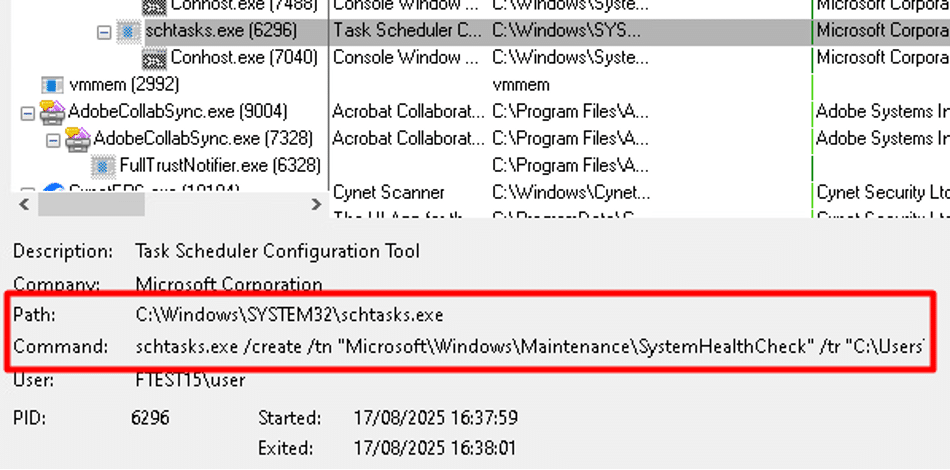
To maintain persistence, the ransomware attempted to execute the command below using “schtasks.exe” to create a scheduled task named “SystemHealthCheck“. This task was configured to run at user logon with elevated privileges:
- “schtasks.exe /create /tn “Microsoft\Windows\Maintenance\SystemHealthCheck” /tr “C:\Users\user\Desktop\9547933dd46501af7fc095a3513e48b81178e344b86e075b679259875f0fd5a7.exe” /sc onlogon /rl HIGHEST /f”.
The process created the following files in the path: “C:\Windows\Temp\”:
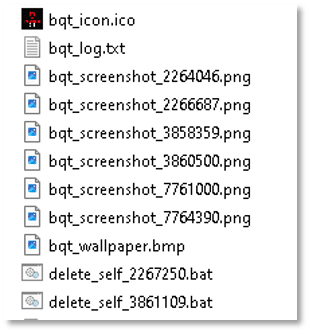
Among the files created are screenshots taken of the host’s desktop. Below is one of the images it generated in our test environment during execution:
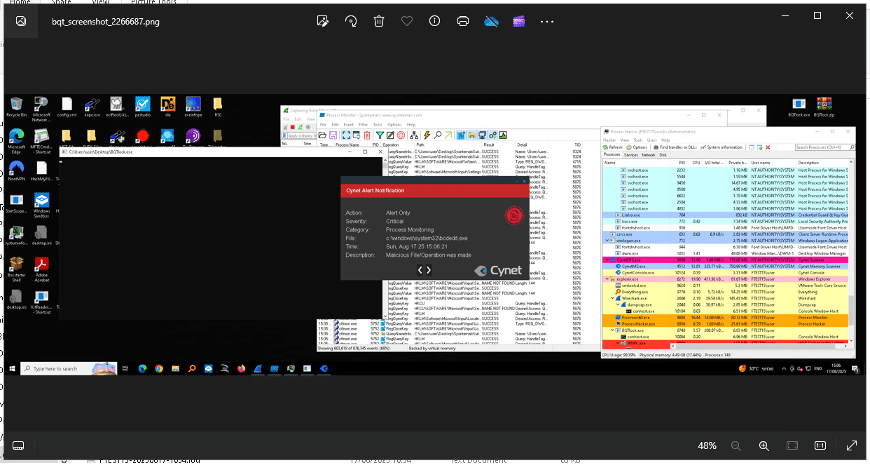
In addition, the malware dropped a self-deletion “.bat” script designed to remove both the initial executable and the batch file itself. This technique is commonly used to eliminate forensic artifacts and hinder post-infection analysis.
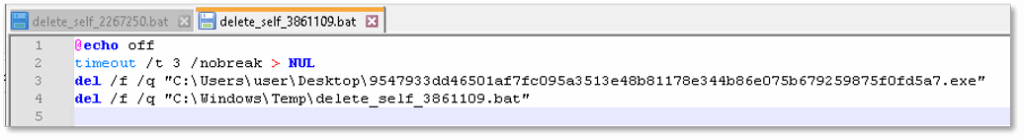
One of the most notable artifacts uncovered was the file “bqt_log.txt”, which contained a detailed log of the ransomware’s operations. The log included evidence of privilege escalation, browser credential harvesting, unauthorized user account creation, termination of security-related processes, and additional malicious actions, providing valuable insight into the ransomware’s operations:
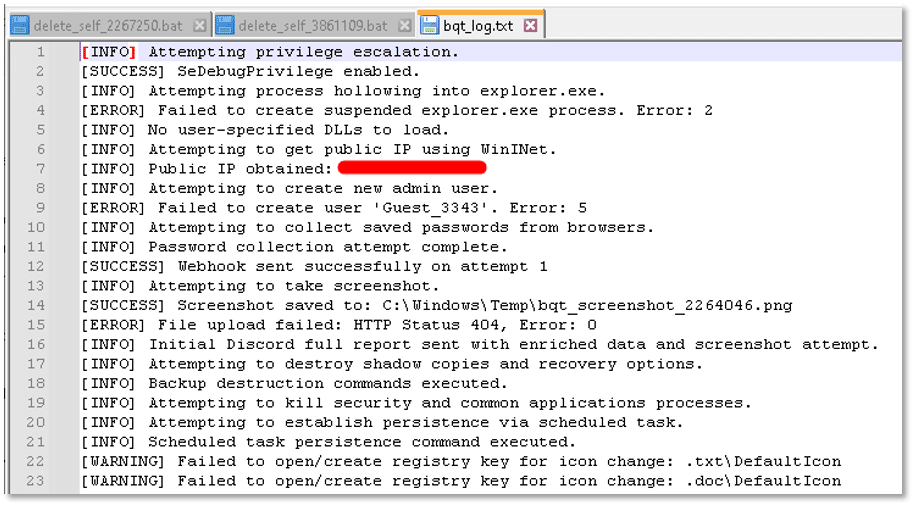
The ransomware set a custom registry value to change the desktop wallpaper:
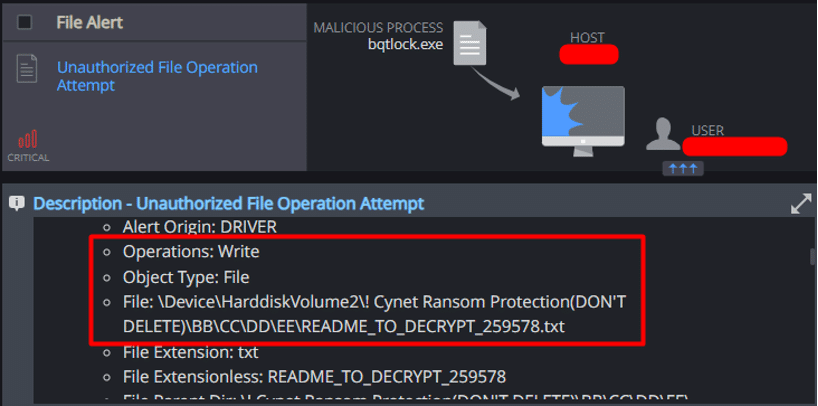
The ransomware created a ransomware note on the desktop, as well as in the folders it attempted to encrypt. Below is the content of the ransomware note:
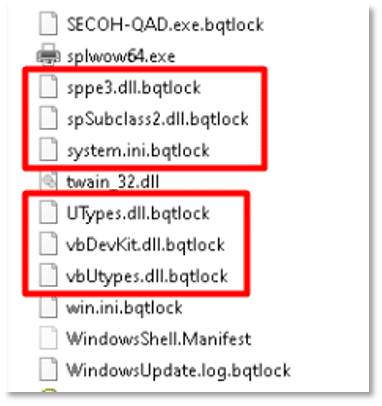
The ransomware concluded its execution by encrypting the host’s files, appending the “.bqtlock” extension to their filenames:
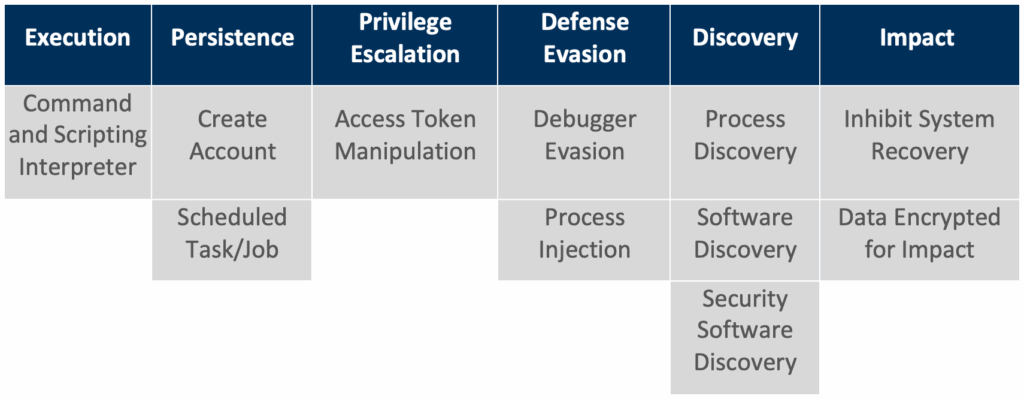
MITRE ATT&CK Tactics and Techniques
Cynet vs BQTLock Ransomware
Note: During this simulated execution, Cynet’s All-in-One Cybersecurity Platform is configured in detection mode (without prevention) to allow the BQTLock Ransomware to execute its full flow. This lets Cynet detect and log each step of the attack.
Cynet can detect and prevent this malware using multiple mechanisms.
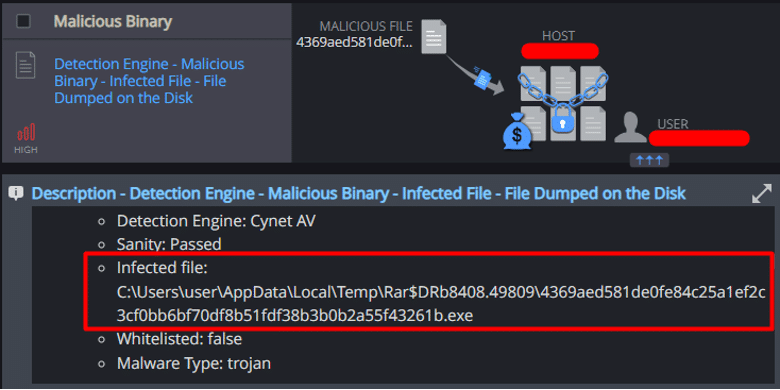
- File Dumped on the Disk
Cynet’s AV/AI engine detects that a malicious file was dumped on the disk or is attempting to run: - Process Monitoring
Cynet detected the attempt made by the ransomware to delete the host’s shadow copies: - Unauthorized Memory Access Attempt
This additional mechanism was also able to detect the shadow copies removal attempt: - Process Monitoring
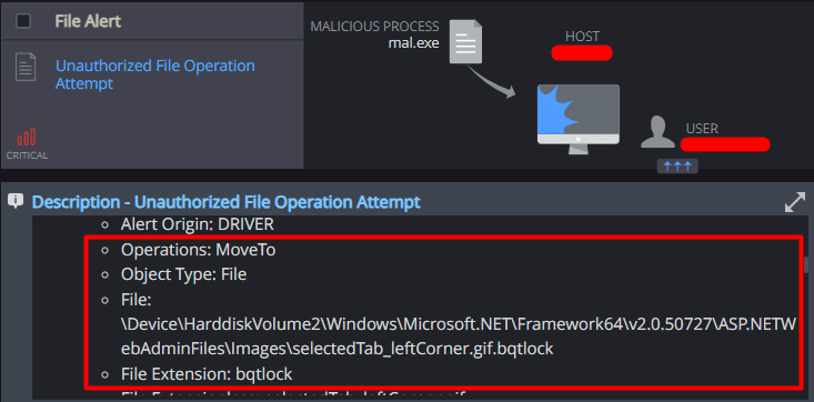
Cynet detected an attempt made by the ransomware to utilize “bcedit.exe” to disable system recovery: - Unauthorized File Operation Attempt
Cynet detected an attempt made by the ransomware to create a ransomware note on Cynet’s ransomware protection folder:
In addition, Cynet detected the actual encryption process and the attempts made by the ransomware to append the “.bqtlock” extension to files: