Charon is a ransomware strain that employs advanced persistent threat (APT)-style techniques to target critical infrastructure sectors, particularly in the Middle East’s public sector and aviation industry. Charon uses multithreading and partial encryption to maximize speed and impact, disables security tools, deletes backups, and appends a unique infection marker to encrypted files. The ransomware accepts command-line arguments to fine-tune its behavior, such as prioritizing network shares or specific paths for encryption.
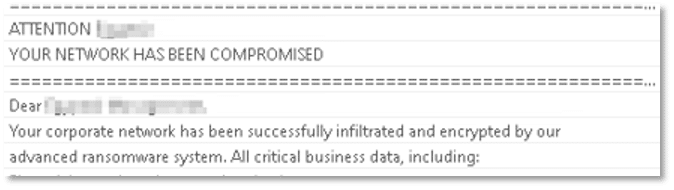
What sets Charon apart is its targeted nature and operational sophistication. Each ransom note is customized to the victim organization, indicating deliberate targeting rather than opportunistic spread. Analysts have noted technical overlaps with the China-linked Earth Baxia group, though attribution remains uncertain. The group employs the double extortion approach where sensitive data is first stolen before encryption of files is initiated, providing the threat actor with greater pressure over the victims to comply with their demands.
Attack chain
The attack starts with DLL sideloading technique, where the legitimate binary “cookie_exporter.exe” masquerading under the name “Egde.exe” is used to load a malicious DLL that was renamed to “msedge.dll”. The malicious DLL decrypts and injects the ransomware payload into a new svchost.exe process. The payload is hidden within an encrypted shellcode stored in a file named DumpStack.log, which undergoes multiple decryption stages before revealing the final executable:
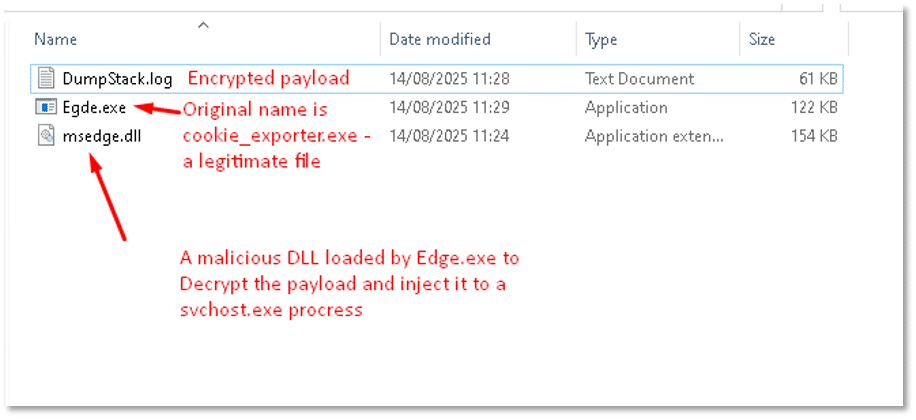
Among the DLLs loaded by “Egde.exe,” one can observe that it also loads the malicious DLL:
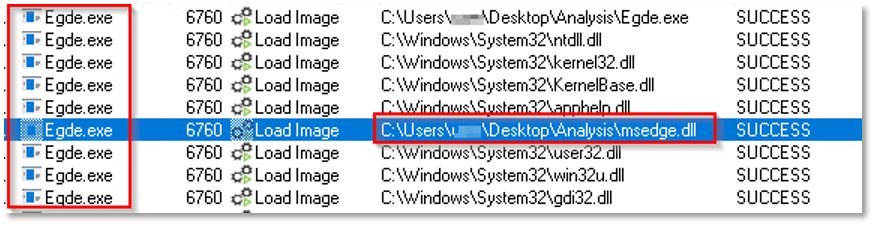
It then initiates the process svchost.exe to inject the decrypted payload into its memory:
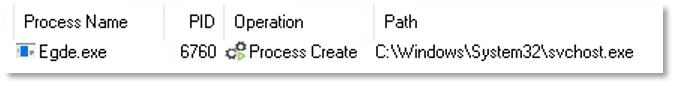
Under normal circumstances, svchost.exe should only be spawned by services.exe. Any other parent process may indicate suspicious or anomalous behavior.
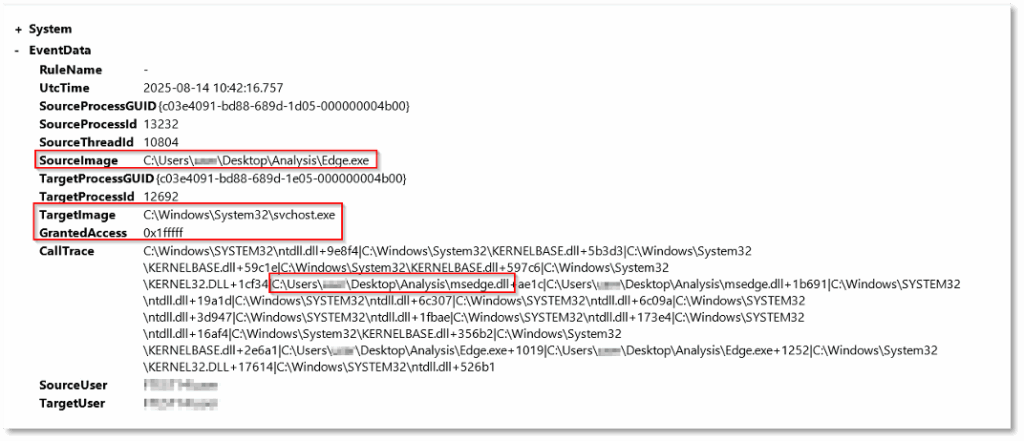
The event indicates that the process “Egde.exe” accessed the memory of “svchost.exe” with high level access rights. The granted access is 0x1FFFFF which includes among others the following permissions that are usually used for process injection:
- ROCESS_VM_WRITE – Allows writing to the target process’s memory.
- PROCESS_VM_READ – Allows reading from the target process’s memory.
- PROCESS_CREATE_THREAD – Allows the source to create threads in the target process.
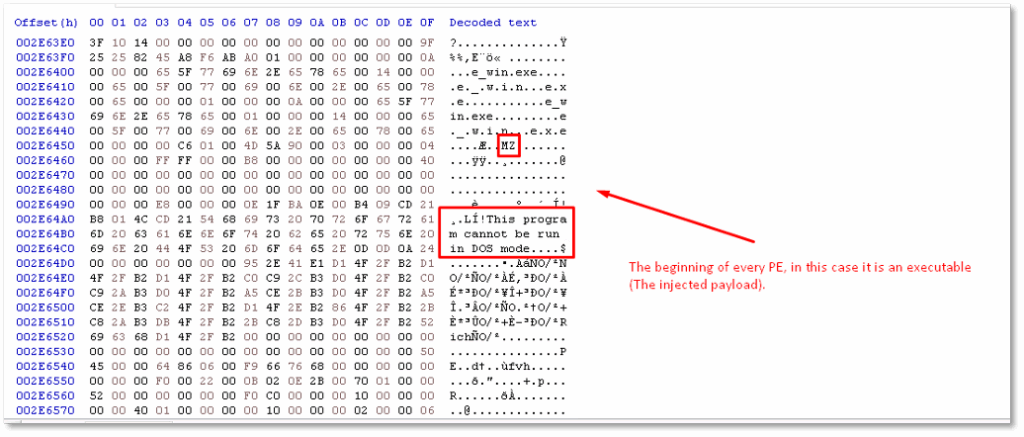
We were able to locate the injected decrypted payload (the actual ransomware) within svchost.exe’s memory and extract it to a file:
Static Analysis
Through static analysis of this file and its strings, we can understand Charon’s functionality and capabilities.
The file may use the “Sleep” API function. This function may be abused by threat actors to delay the execution of potentially malicious commands thus avoiding sandbox detection by triggering their timeout set for file scanning.

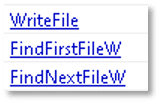
The following imports suggest that the file has the ability to enumerate files, write and move files and to empty the Recycle Bin:


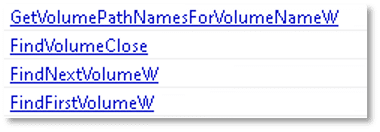
The file can enumerate system volumes:
The file can enumerate running processes and terminating processes:

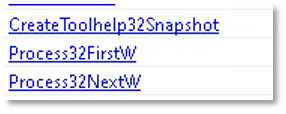
The following API functions suggest that the file may create and control services:
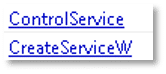
The following strings suggest that the file may use Windows’ “Restart Manager” functionality. Restart Manager is normally used when a file that is currently being used by an application or service is halting an installation or update process. Restart Manager will shut down the offending application or service to allow the installation or update to complete. This can be abused by malware to forcibly terminate applications or services to allow the modification of their used (running) files. In the context of ransomware, this can be used to allow the complete encryption of all targeted files on the host:
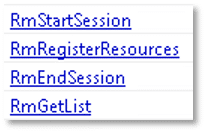

The file may enumerate the network and network shares:
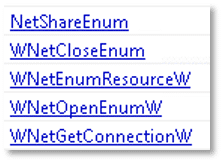
The file has cryptographic capabilities:
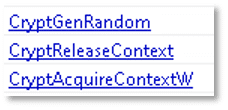
The file may use or manipulate the following processes and services:
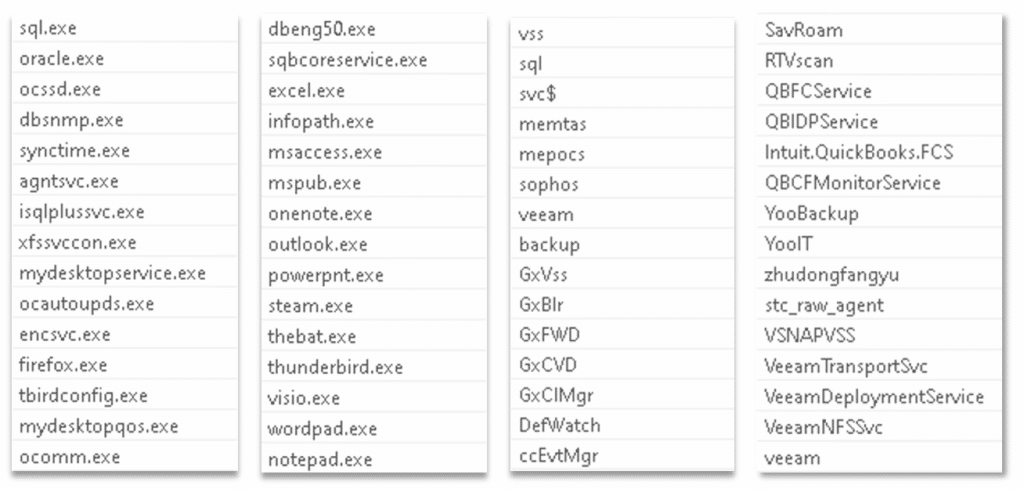
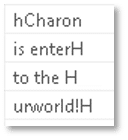
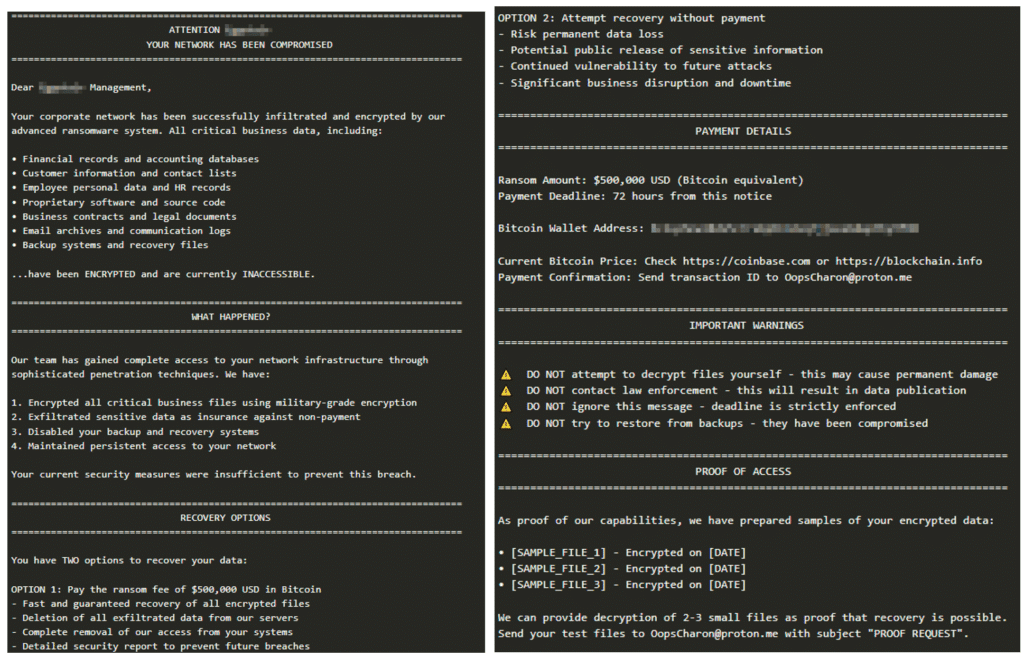
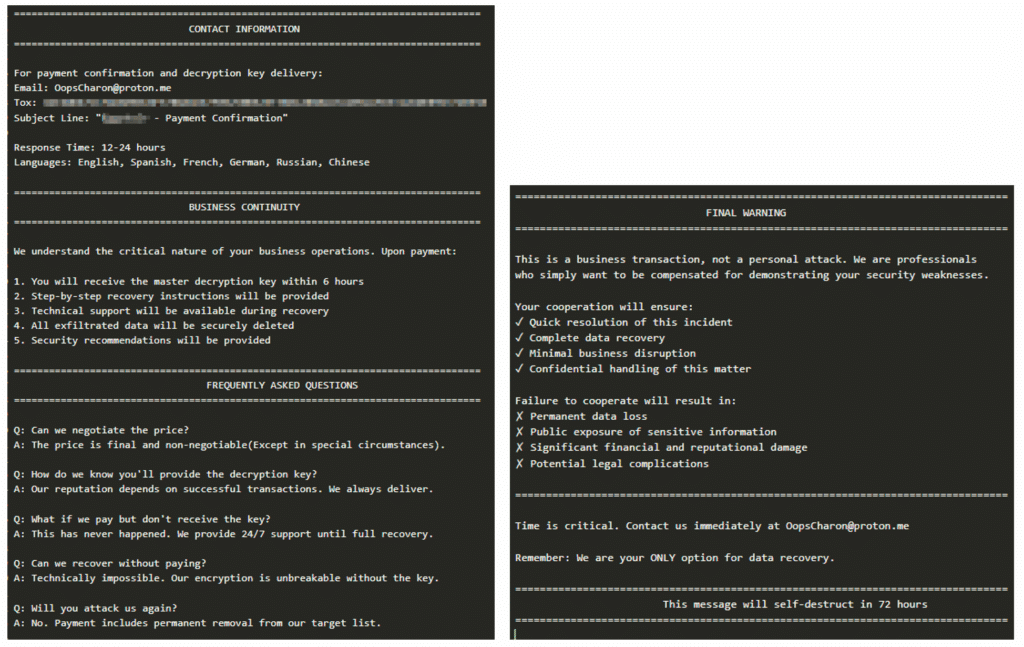
Potential ransom note file:
The ransom note was found in the file’s strings:
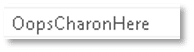
Potential encryption added extension:

Charon related strings:
The file contains an additional, embedded file:

Extraction and analysis of the file reveals that it is related to Dark-Kill, an EDR killer that is publicly available and designed to disable EDR systems, allowing malicious software to operate without being detected or blocked. It works by leveraging a kernel-mode driver to forcibly terminate security processes, including antivirus and EDR agents.
Dynamic Analysis
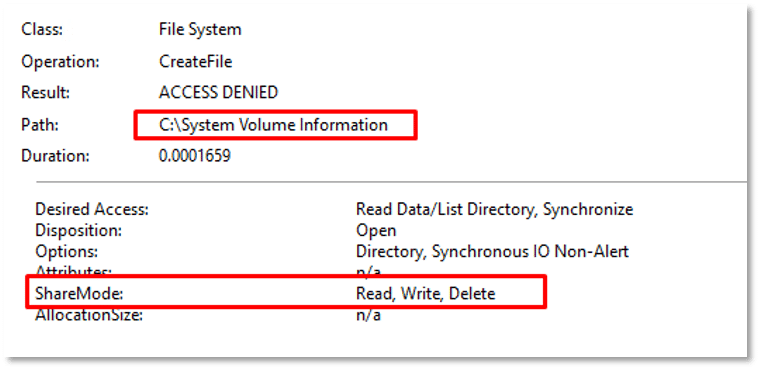
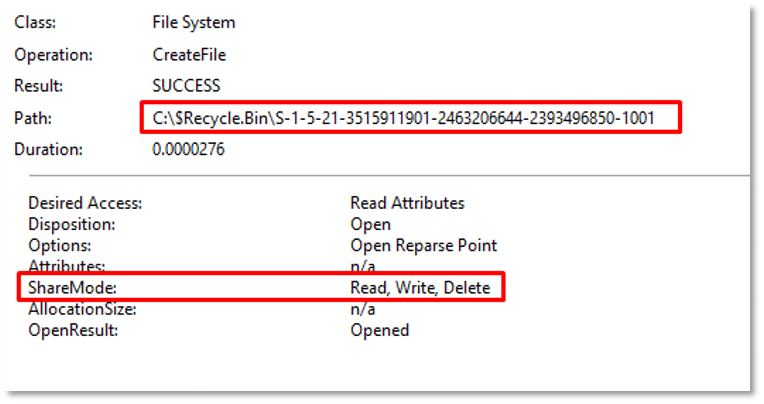
Upon execution, Charon tries to remove Volume Shadow Copies from the host and empties the contents of the Recycle Bin, to prevent recovery of encrypted files. Shadow copies are used by Windows for backups and restore points. Removing them ensures victims can’t easily restore their system:
Shortly after, the process starts encrypting the filesystem. Encrypted files are appended with the extension “.Charon” and an infection mark is being appended the encrypted files:
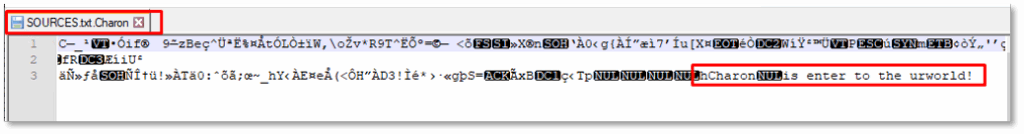
The ransom note file “How To Restore Your Files.txt” is dropped into every affected folder:

The ransom note is personalized for the victim, explicitly naming the company:
Full Process Tree:
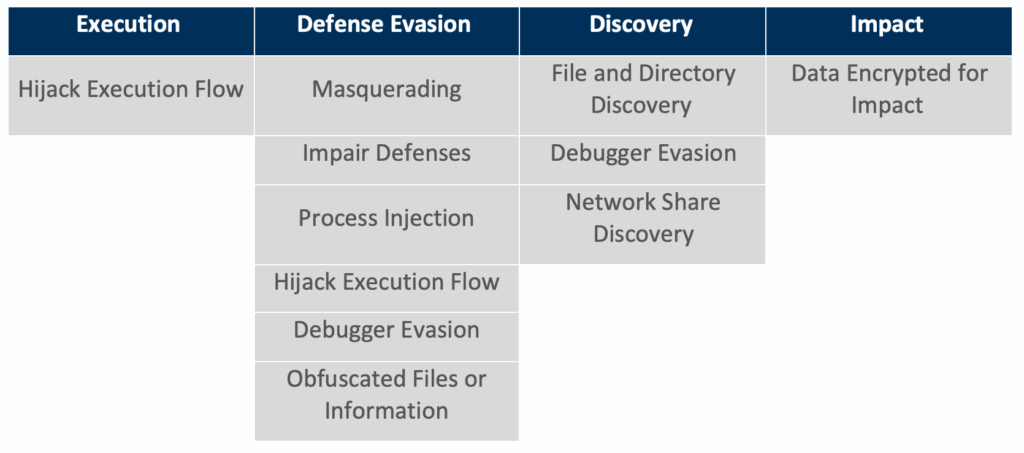
MITRE ATT&CK Tactics and Techniques
Cynet vs Charon
Note: During this simulated execution, Cynet’s all-in-one cybersecurity solution is configured in detection mode (without prevention) to allow Charon ransomware to execute its full flow. This lets Cynet detect and log each step of the attack.
Cynet can detect and prevent this malware using multiple mechanisms.
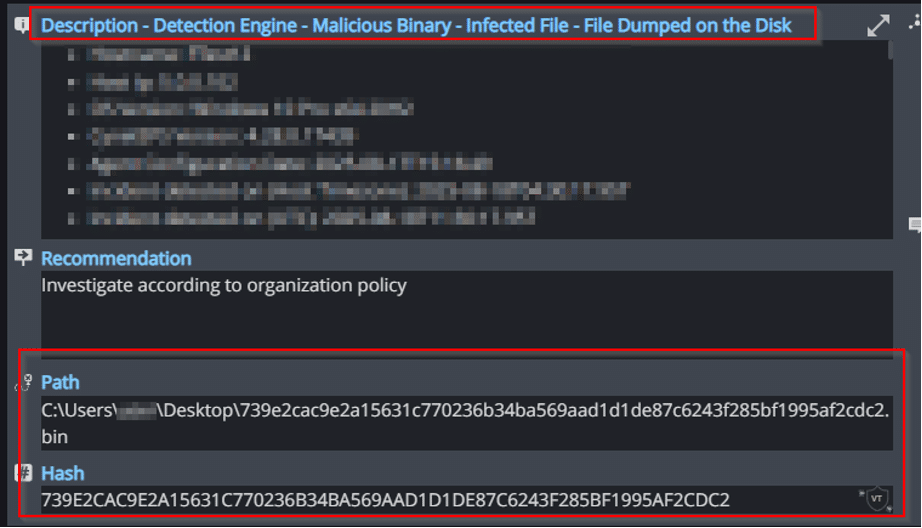
File Dumped on the Disk
Cynet’s AV/AI engine detects that malicious files were dumped on the disk or are attempting to run:

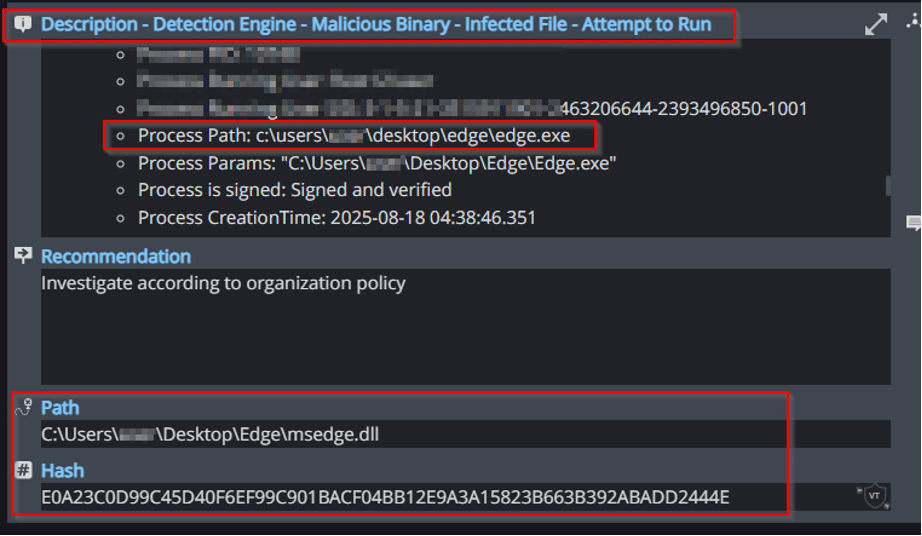
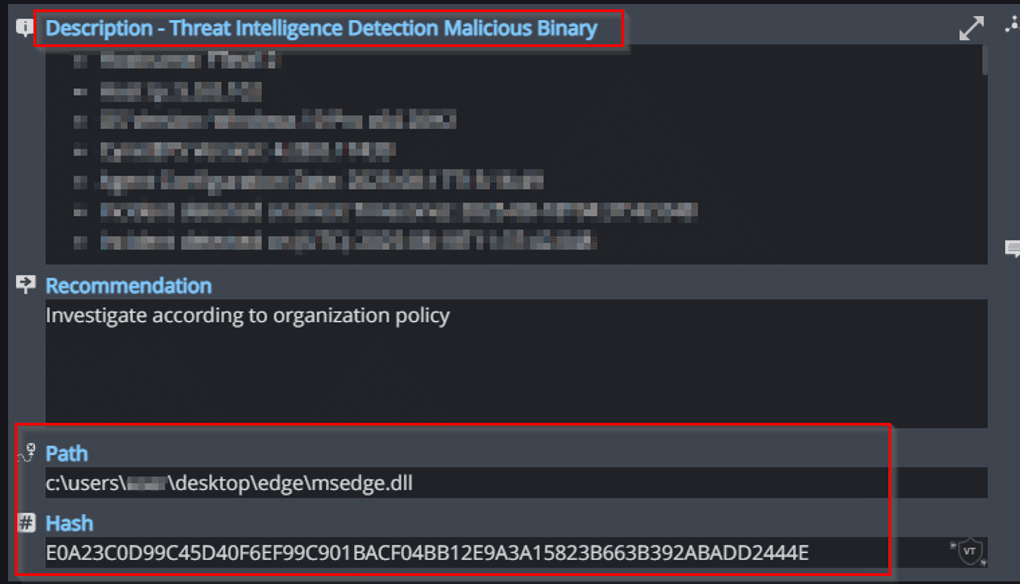
Threat Intelligence Detection Malicious Binary
In addition to Cynet’s AV mechanism, Cynet also utilizes 3rd party cyber threat intelligence data to detect the presence of suspicious and malicious files:
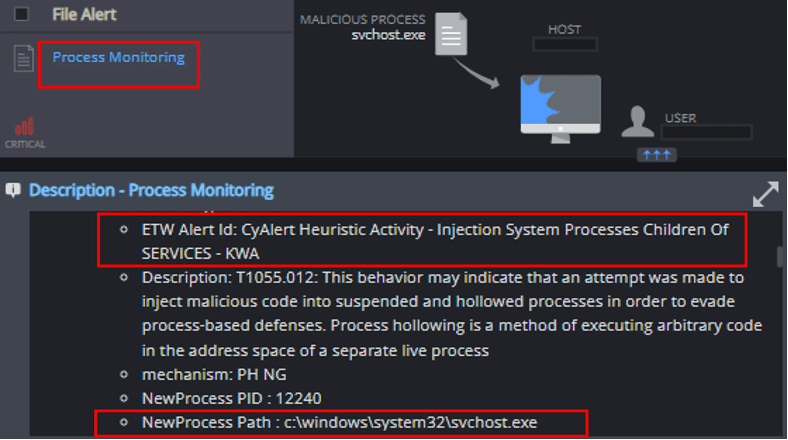
Process Monitoring
This mechanism detects suspicious process activity such as process injection:
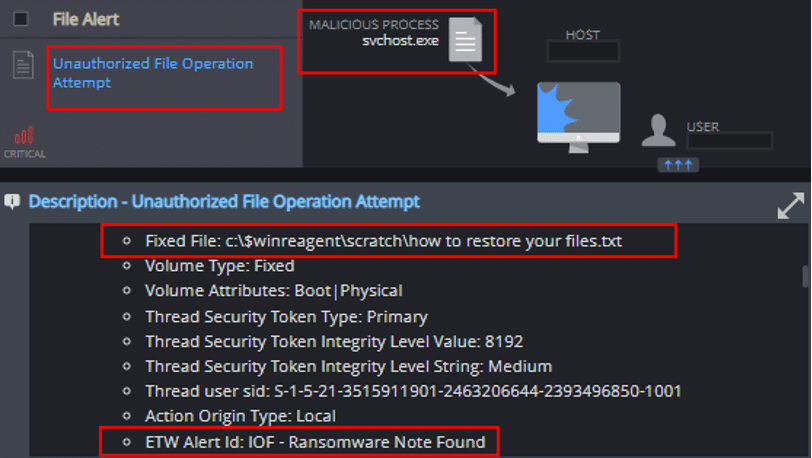
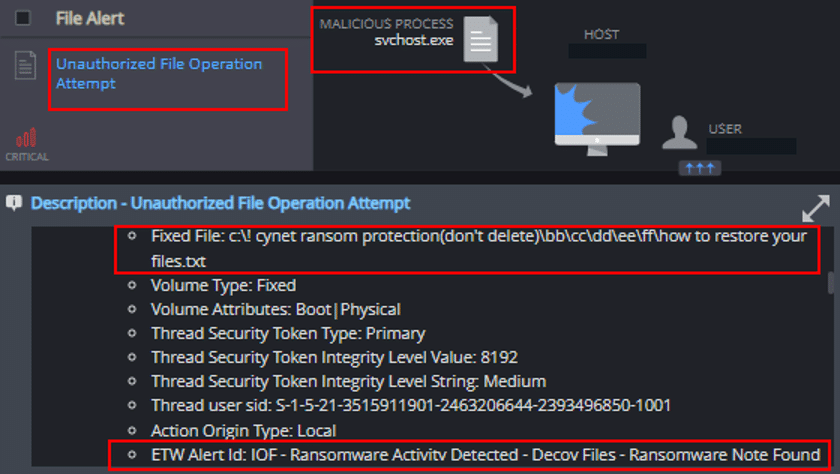
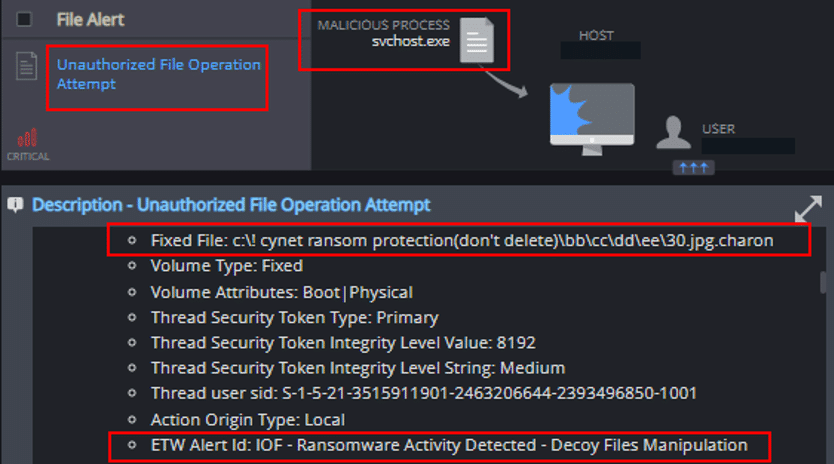
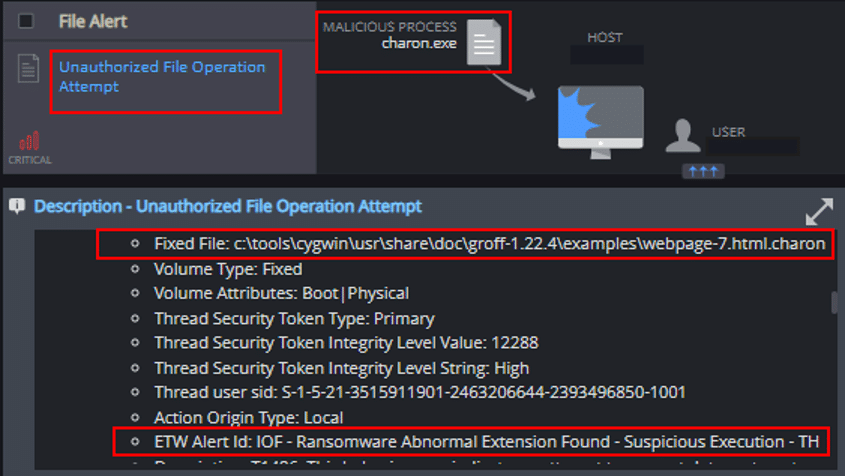
Unauthorized File Operation Attempt
This mechanism detects and reports on attempts to create suspected encrypted files, the modification of Cynet’s Ransomware decoy files, and the creation of possible ransom notes: