FreePBX is a popular open-source web-based GUI for managing Asterisk PBX systems, commonly deployed in enterprise VoIP (Voice over Internet Protocol) infrastructures. Businesses use it to manage their own phone systems, including calls, extensions, voicemail, and customer queues, without licensing a commercial VoIP provider.
A critical-severity vulnerability (CVSS 10.0) in FreePBX was publicly disclosed in August. Tracked as CVE-2025-57819, the flaw stems from insufficient user-supplied data sanitization that allowed unauthenticated attackers to access the FreePBX Administrator interface and then perform arbitrary database manipulation that leads to remote code execution (RCE).
This vulnerability has been observed actively exploited in the wild. Affected organizations have not been named publicly, nor has the exploit been credibly attributed to a specific adversary. However, PBX systems are considered attractive targets by ransomware gangs, initial access brokers, and other fraud groups, based on the potential for voice phishing (vishing), intercepting calls, or pivoting from one compromised system to another.
In this blog, we break down CVE-2025-57819’s exploit chain step by step, charting its escalation from unauthenticated access to SQL injection, and share mitigations that FreePBX advises implementing ASAP.
You are reading an excerpt of a Cyber Threat Intelligence (CTI) Report, delivered monthly by CyOps to Cynet partners and All-in-One customers. Download the full CTI report.
Which versions are vulnerable?
CVE-2025-57819 affects:
- FreePBX 15: versions 15.0 up to (but not including) 15.0.66
- FreePBX 16: versions 16.0 up to (but not including) 16.0.89
- FreePBX 17: versions 17.0 up to (but not including) 17.0.3
How Does it Work?
The model() function in the Endpoint Manager’s ajax.php file fails to adequately sanitize user-supplied input, leading to arbitrary database manipulation and RCE.
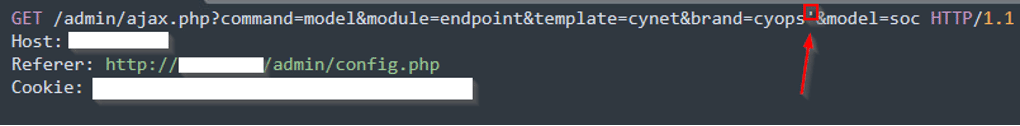
- Request:
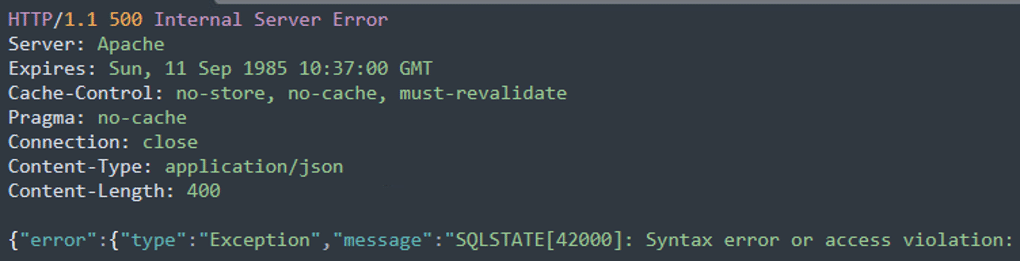
- Response:
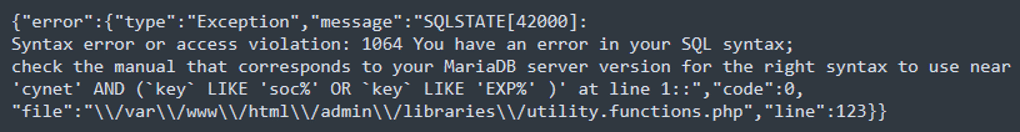
- Error:
The single quote (‘) in the request parameter brand=cyops’ is a classic technique used to test for or exploit SQL injection vulnerabilities. The single quote is used to intentionally break out of the expected string context in a SQL query. If the application is vulnerable, this can cause a SQL syntax error.
However, to successfully perform the SQL injection, an attacker must be able to access /admin/ajax.php, which requires authentication. This is the point where the vulnerability manifests and through which the SQL injection is leveraged.

/admin/ajax.php is the central AJAX dispatcher in FreePBX. It acts as a gateway for handling asynchronous (AJAX) requests sent from the web interface to the backend:
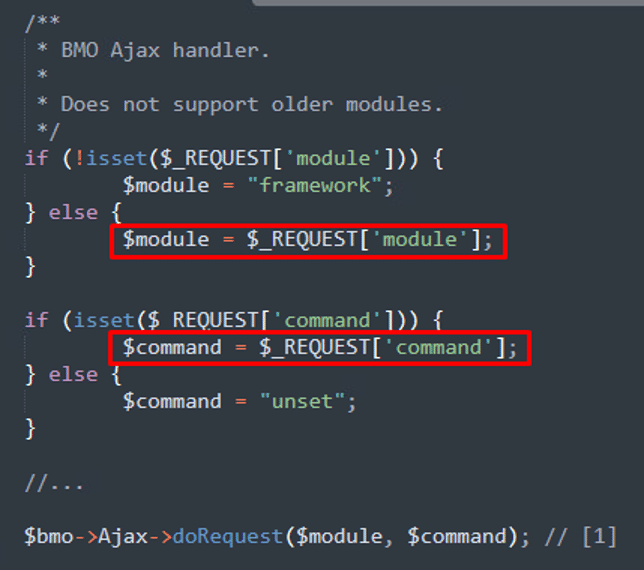
At [1], the code takes the supplied module and command parameters from the request and passes them to libraries/BMO/Ajax.class.php, where they are processed by the doRequest() method. This method is responsible for routing AJAX requests to the correct module and command handler:
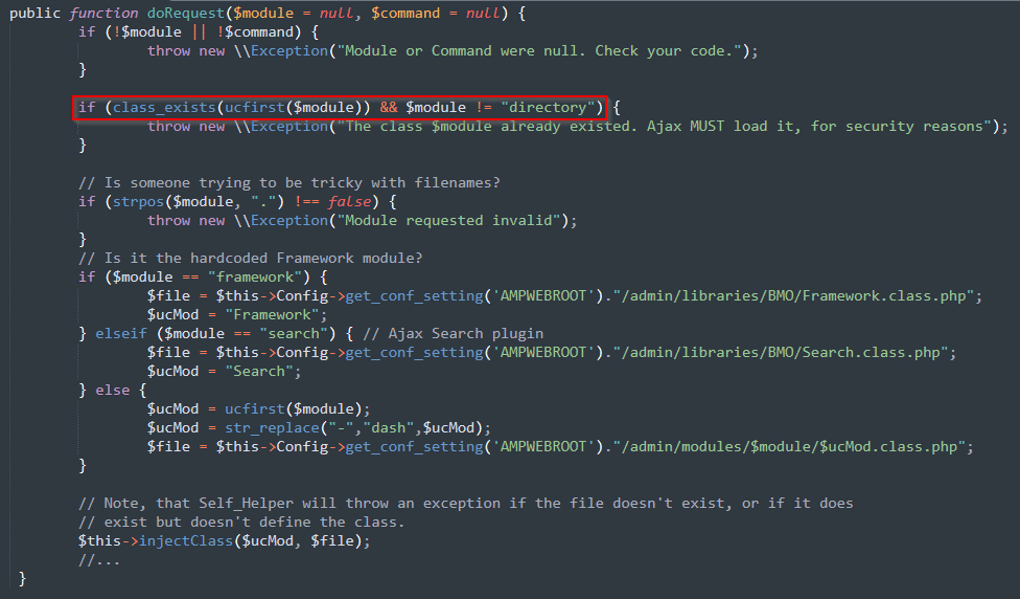
The unsanitized “module” parameter from the user’s request is passed directly into class_exists(). This function accepts two parameters, with the second one being “autoload”:
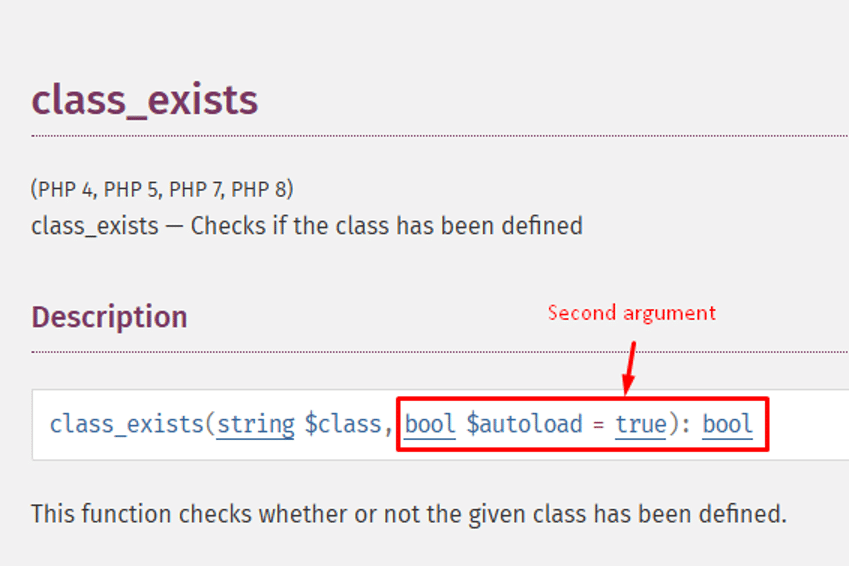
When autoload is set to true, PHP will attempt to automatically load any class name passed to it. Since autoload defaults to true, passing a value to class_exists() causes PHP to attempt loading a corresponding class file from disk, based on the class name derived from the module parameter. This flaw allows not only the loading of classes, but also the execution of static scripts such as admin/modules/endpoint/ajax.php.
When class_exists() is called, the “module” parameter is handed to the fpbx_framework_autoloader() function:
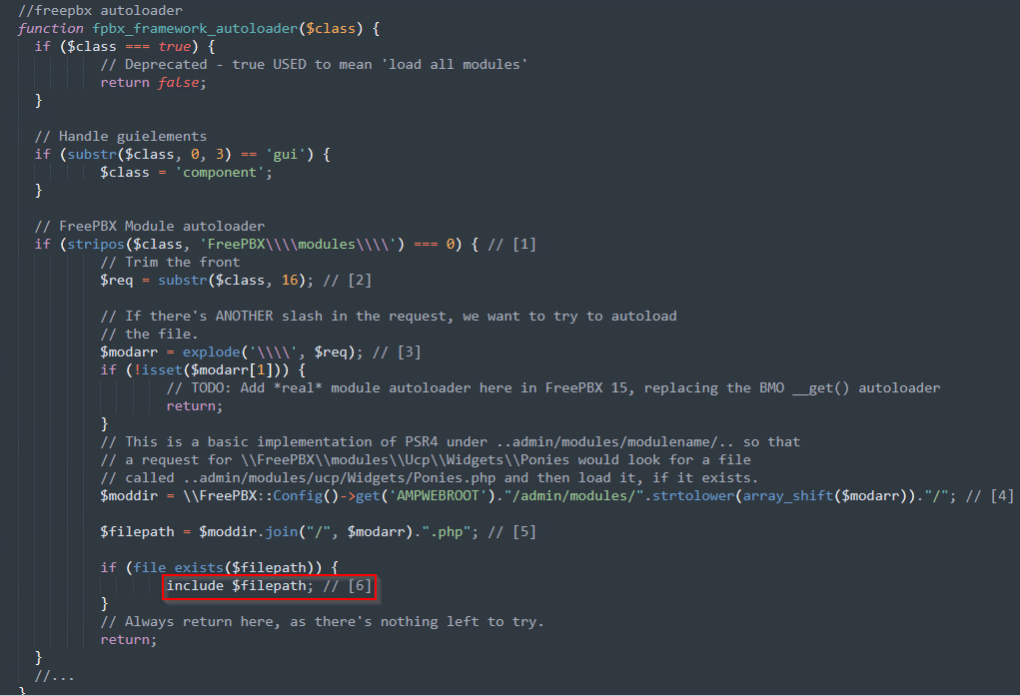
The module parameter goes through a series of transformations and checks that ultimately construct a file path to a PHP script, which is then included and executed by FreePBX. In other words, the class loader allows you to include any file ending with the .php extension from the admin/modules location. Attackers can hit certain module files directly without needing to authenticate.
In this example the same SQL injection attack was performed without authentication:


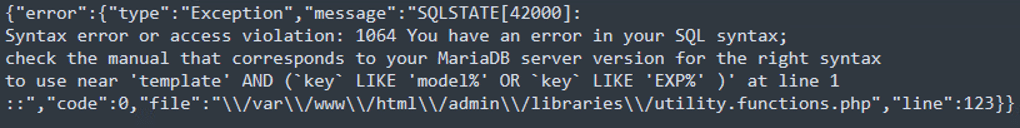
Indicators of Compromise
FreePBX advises users to scan their environments for IOCs including:
- File /etc/freepbx.conf recently modified or missing
- File /var/www/html/.clean.sh should not exist on normal systems
- POST requests to modular.php in web server logs likely not legitimate traffic
- Phone calls placed to extension 9998 in call logs and CDRs are unusual – unless previously configured
- Suspicious ampuser user in the ampusers database table or other unknown users
Recommended Mitigations
FreePBX urges users to upgrade ASAP to one of the following versions:
- FreePBX 15: version 15.0.66
- FreePBX 16: version 16.0.89
- FreePBX 17: version 17.0.3
Moral of the Story
For security teams, vulnerabilities like CVE-2025-57819 are a reminder that even mature, widely used platforms can serve as gateways for costly compromise. One unpatched module or misconfigured admin panel is all a motivated adversary needs to access critical systems expand the scope of their attack. To reduce that risk for their companies or their clients, security teams must extend visibility and protection beyond the perimeter. Environment-wide prevention, access controls, and continuous monitoring can determine the difference between a quick patch and a full-scale breach.
Cynet defends against zero-day vulnerabilities through a multi-layered, behavior-driven approach, rather than relying on known signatures. The All-in-One Platform continuously monitors endpoint memory, processes, and user activity, combining behavioral analytics and machine-learning–based detection to identify anomalous patterns—even when the underlying vulnerability is unknown.
If a zero day is exploited, Cynet capabilities such as sandboxing, static and dynamic analysis, and threat intelligence correlation can detect and block the resulting malware. These protections, combined with automated investigation and response, enable organizations to quickly contain previously undiscovered threats.