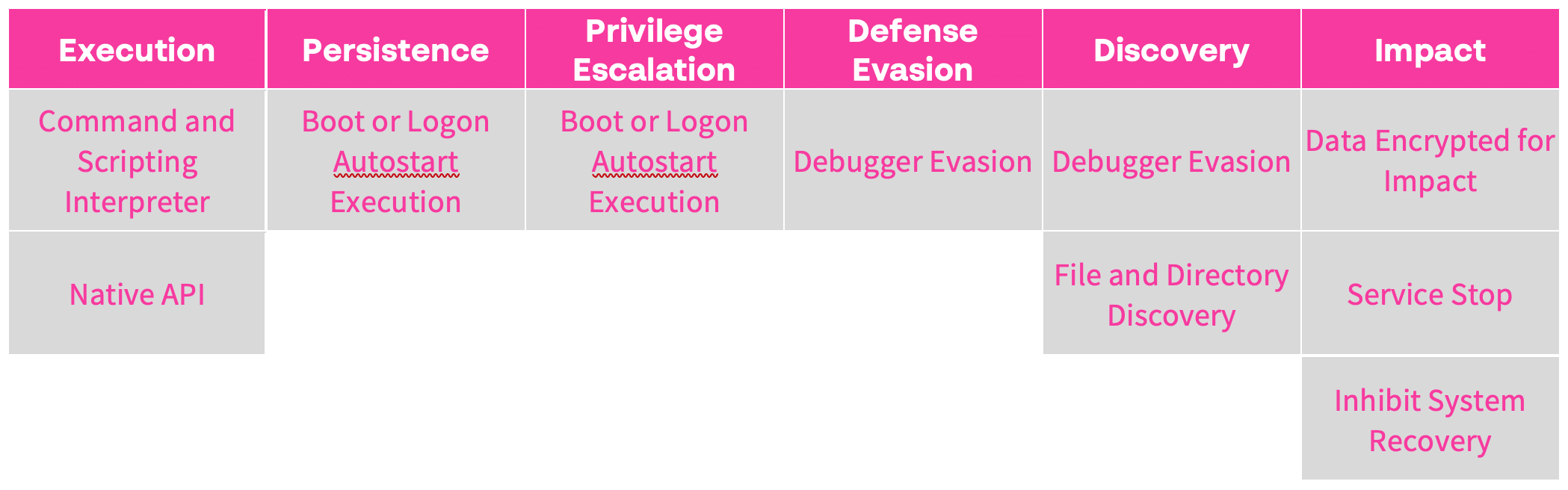
Dynamic Analysis: Hazard Ransomware
A new ransomware variant from the MedusaLocker family, called “Hazard,” was recently observed. After Hazard ransomware encrypts a victim’s computer, the adversary demands payment in exchange for a decryption tool and the necessary decryption keys. The ransom note typically contains instructions for victims to contact the attackers.
It is crucial to recognize that complying with any threat actor demand for ransom payment is inherently risky. First off, there is no assurance that the decryption tool will work or even be delivered as promised. Moreover, such payments can inadvertently incentivize further illegal activities by the newly enriched attackers.
For more, you can review a static analysis of Hazard or see how Cynet stops the threat in this step-by-step breakdown.
Time to dive into our dynamic analysis!
Dynamic Analysis
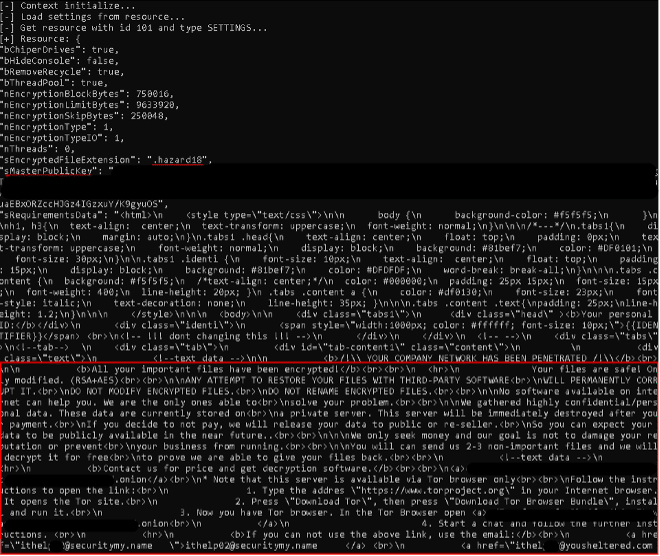
Once executed, the process spawns a command line window detailing many of the actions taken by the process. When initialized, the process sets several configurations, such as the public key used, ransomware extension to be appended to encrypted files, and the ransom note text itself:
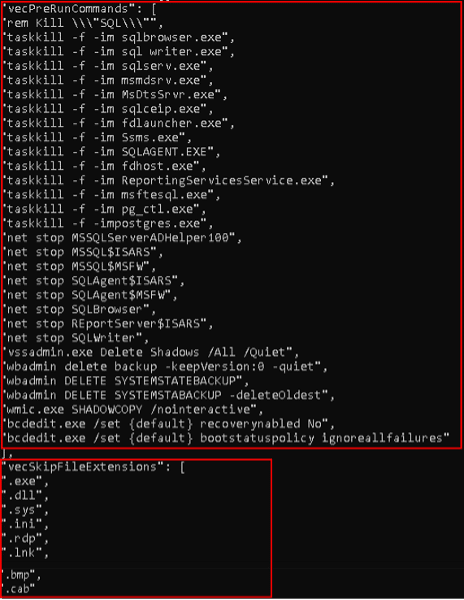
The process then executes commands to ensure as much impact as possible prior to encryption. These include:
- Terminating database services, which ensures the ransomware will be able to encrypt crucial database files.
- Deleting backup files from the host and terminating backup services.
Additionally, the process details the file types and paths it will ignore when scanning for files to encrypt:
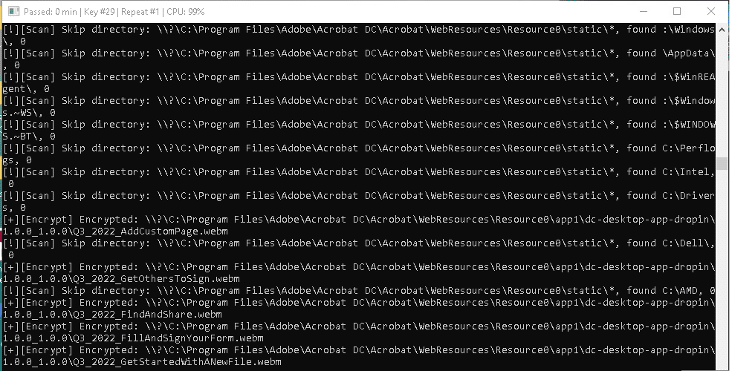
When the configuration is all set, the process initiates the scanning and encryption of the host’s files:
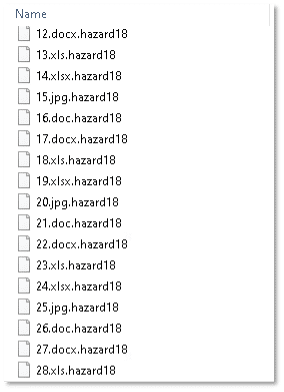
Encrypted files are appended with the extension “.hazard18”:
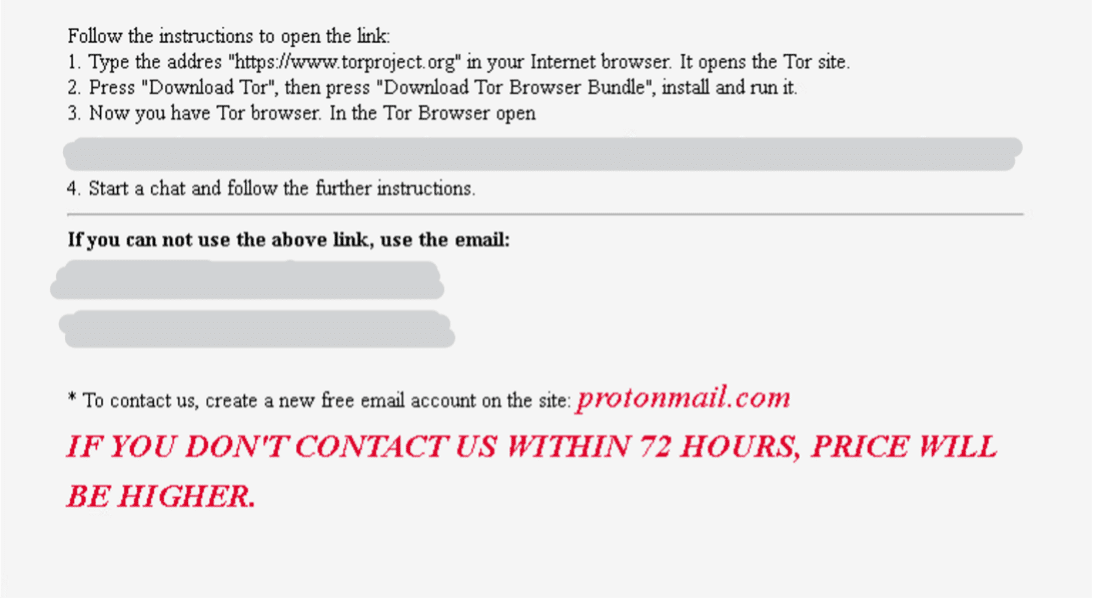
The process also drops a ransom note named “HOW_TO_BACK_FILES.html”:
The note announces the encryption of the host’s files and warns of attempting to decrypt them with 3rd party applications. The threat actor warns that if they are not paid, the stolen data will be sold or released to the public. The note also details how to contact the threat actor to negotiate the amount of ransom to be paid, along with a warning that the price will increase if they are not contacted within 72 hours.
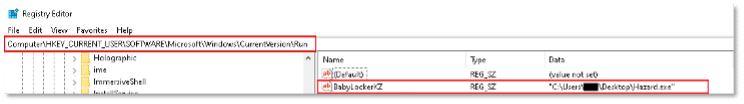
Analysis confirms our initial suspicion (when reviewing the file strings) that the process indeed creates a registry Run key named “BabyLockerKZ” for the current user, targeting the malicious file location to ensure persistence on the host.