Static Analysis: Hazard Ransomware
A new ransomware variant from the MedusaLocker family, called “Hazard,” was recently observed. After Hazard ransomware encrypts a victim’s computer, the adversary demands payment in exchange for a decryption tool and the necessary decryption keys. The ransom note typically contains instructions for victims to contact the attackers.
It is crucial to recognize that complying with any threat actor demand for ransom payment is inherently risky. First off, there is no assurance that the decryption tool will work or even be delivered as promised. Moreover, such payments can inadvertently incentivize further illegal activities by the newly enriched attackers.
For more, you can read a dynamic analysis of Hazard or see how Cynet stops the threat in this step-by-step breakdown.
Through static analysis of this variant and its strings, we can understand Hazard’s functionality. Let’s get started!
Static Analysis
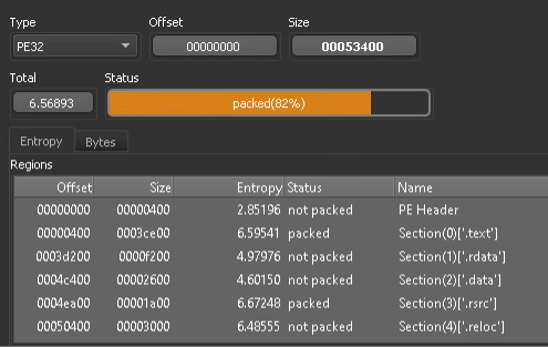
The file’s high entropy suggests that it is packed and will reveal Its full capabilities once executed:
The file’s strings show that the file is capable of creating a registry key:
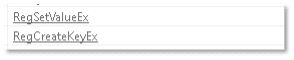
Another string suggests that the file will attempt to establish persistence by creating a registry Run key, to ensure the file will be executed with each logon:
The file may use a Windows API call that queries the existence of a debugger running on the host — most likely to avoid analysis:
The file is capable of encrypting data, as indicated by the following Windows API strings: