How Cynet stops Stealc Infostealer
Below we’ll demonstrate how Cynet detects and prevents Stealc infostealer. For more, you can review our experts’ static analysis this threat.
Obligatory disclaimer: During this execution simulation, Cynet 360 AutoXDR is configured in detection mode (without prevention) to allow Stealc to execute its full flow. This lets Cynet detect and log each step of the attack.
Cynet can detect and prevent the execution of Stealc using two mechanisms.
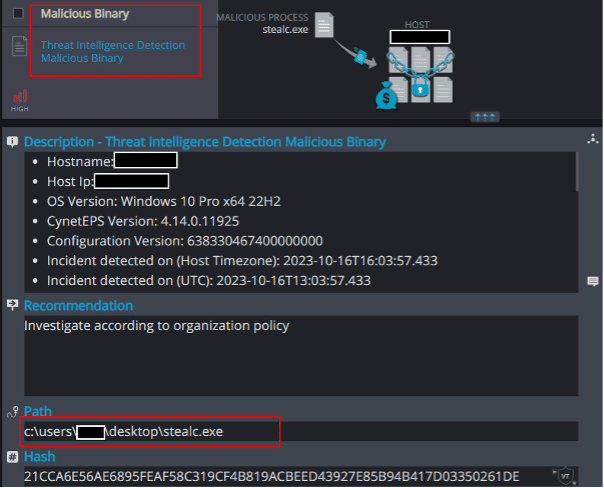
1. Threat Intelligence Detection Malicious Binary
Using Cynet’s extensive threat intelligence database, the creation of the malicious binary on the host is detected:
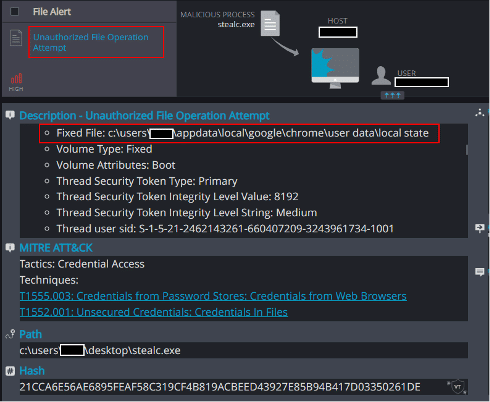
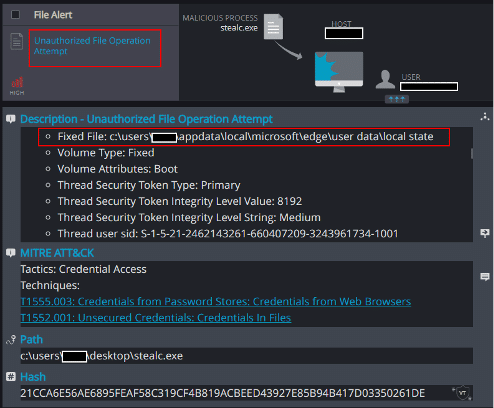
2. Unauthorized File Operation Attempt
Stealc’s attempts to access the host’s sensitive browser data are detected successfully by Cynet: