Static Analysis: Stealc Infostealer
Introduced in early 2023, Stealc is an emerging MaaS (Malware as a Service) infostealer based on the Vidar, Raccoon, Mars and Redline stealers. Stealc focuses on stealing sensitive data from web browser files, crypto wallets (both browser- and desktop-based), as well as account data from apps including Outlook and Telegram, in addition to employee file grabbing capabilities. Similar to most MaaS, the tool is customizable, allowing attackers to pick and choose the data they wish to pull from their victims’ machines.
For more, you can see how Cynet stops Stealc in this step-by-step breakdown.
Through static analysis of this infostealer and its strings, we can understand its functionality. Let’s get started!
Static analysis
Upon execution, Stealc reaches out to its C2 (Command and Control) server, creating a dedicated webpage ID for the machine.
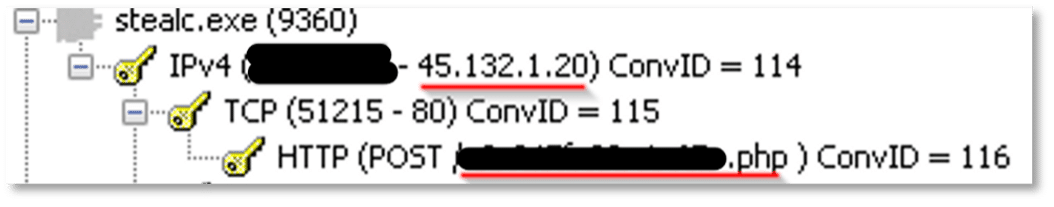
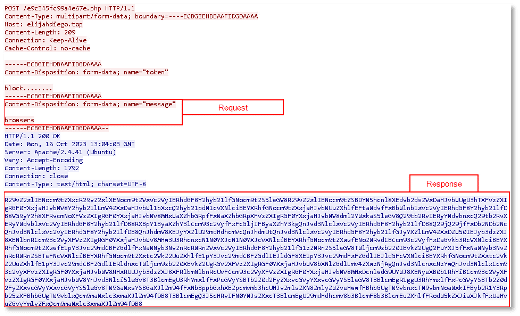
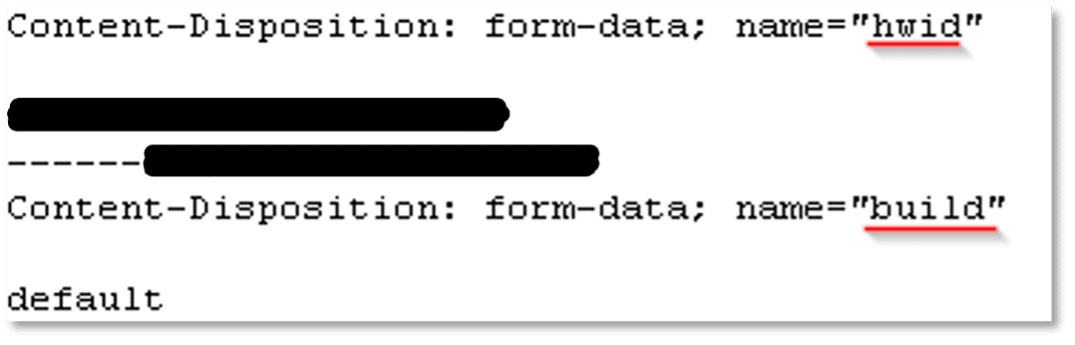
In the initial communication with the C2 server, the host sends out a Hardware ID as well as the current build of the malware. The C2 server later replies with an identifier token, for use with each subsequent web request to the C2 server:
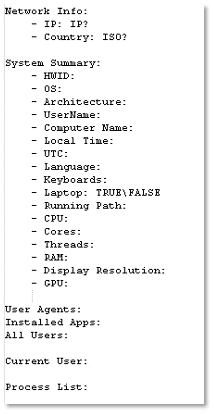
Stealc then enumerates and sends out the host’s system information to the C2 server. This includes the OS, hardware components, localization data, installed applications and running processes:
Then, four web requests are made to the C2 server to pull Stealc’s configuration, one for each type of data it will attempt to steal. The server’s response holds the relevant strings that the malware will seek in the host’s filesystem:
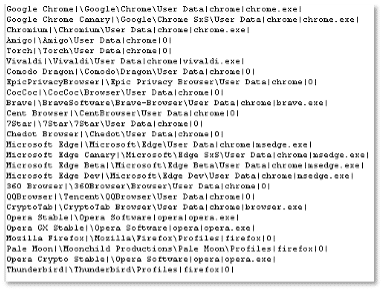
- “browsers” – Listing various browsers and their paths:
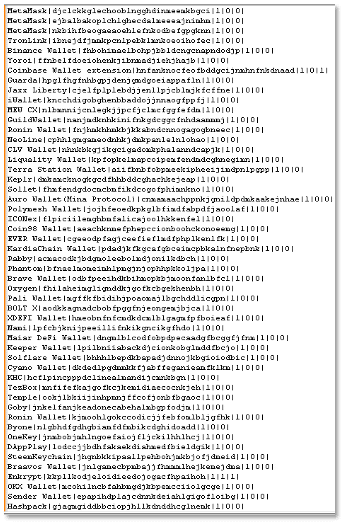
- “plugins” – Listing Crypto wallets browser extensions (add-ons) and their IDs:
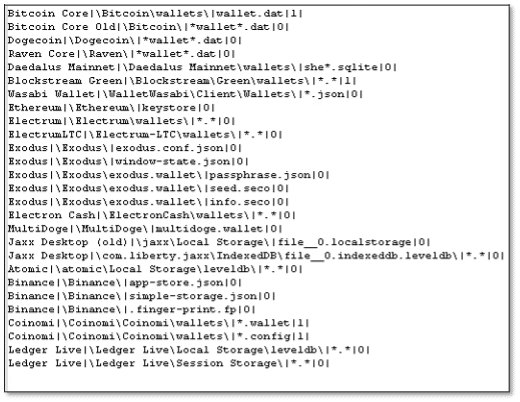
- “wallets” – Listing important paths of various desktop-based crypto wallets:
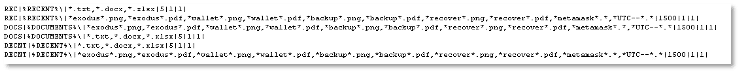
- “files” – Using this configuration, Stealc will grab and exfiltrate any file that matches the provided patterns:
There are some operations that Stealc cannot perform out-of-the-box and require the import of one or more external dll files to complete.
Seven legitimate 3rd party dlls were observed so far being abused by Stealc: sqlite3.dll, mozglue.dll, nss3.dll, freebl3.dll, softokn3.dll, msvcp40.dll and vcruntime140.dll
The dll files are set to be downloaded to the path “C:\programdata\”:
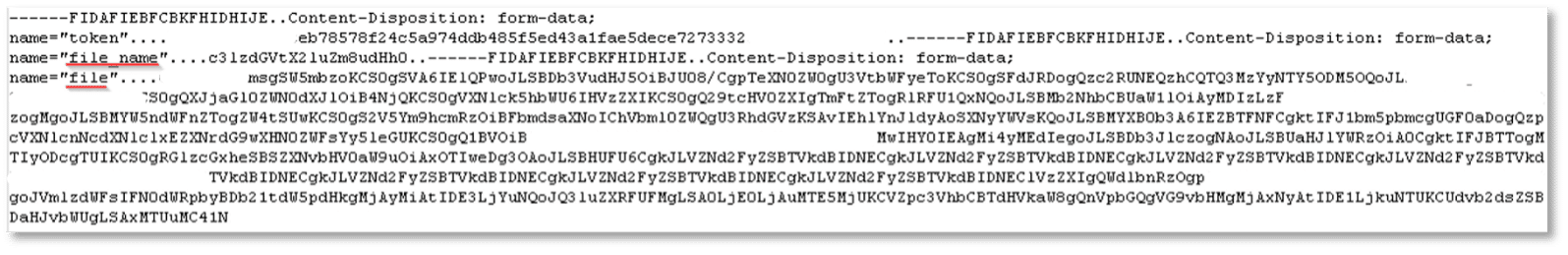
Unlike other infostealers, Stealc does not archive stolen data as a file prior to exfiltration. It will instead send a POST web request for each created file, encoding the data within as base64 strings.
The exfiltrated files are named in the following fashion (examples):
- cookies\Google Chrome_Default.txt
- cookies\Microsoft Edge_Default.txt
- history\Google Chrome_Default.txt
- history\Microsoft Edge_Default.txt
- files\REC\log.txt
- files\DOCS\<application name>\<filename>.TXT
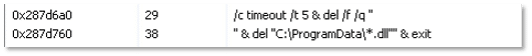
After Stealc finishes its work, a command is executed to delete all traces of itself and its downloaded dll files from the host: