In this article
What Is Endpoint Security? 9 Defensive Layers
What Is Endpoint Security?
Endpoint security is a strategy for protecting endpoint devices such as smartphones, laptops, tablets, and desktops against cyberattacks. Organizations use endpoint security software to protect the devices used by employees for work purposes, including in the cloud or on the company network.
Any endpoint connecting to the corporate network or an organization’s cloud services represents a security vulnerability, potentially allowing a malicious actor to penetrate the network. Cybercriminals often exploit these convenient entry points by installing malware to compromise the endpoint and exfiltrate sensitive data.
Organizations must deploy tools to detect, analyze, block, and contain cyber threats on endpoints. Modern endpoint security solutions are packaged as an endpoint protection platform (EPP) that includes multiple layers of security defenses – including next-generation antivirus (NGAV), firewall, and endpoint detection and response (EDR).
This is part of an extensive series of guides about data breach.
Why Is Endpoint Security Important?
Every organization must have an endpoint security strategy to address the risks presented by local and remote endpoints. Each connected device is a potential entry point for attack, and the challenge has become more complicated with the shift to remote work and an ever-increasing number of endpoints.
Social engineering attacks (e.g., phishing) are rising while servers continue to dominate the asset landscape, representing a valuable target for attackers. A data breach can be very expensive, usually costing millions of dollars. The largest contributor to this cost is the lost revenue from damaged business operations.
Effective endpoint security defends against social engineering and significantly reduces the attack surface of endpoints. It adds multiple defensive layers to prevent common attacks. Even more importantly, it gives security teams the tools they need to identify and respond to attacks that bypass these defenses, reducing the impact of a security breach.
This is part of an extensive series of guides about data security.
What Is Considered an Endpoint?
An endpoint is any device that connects to a network and communicates with other devices or systems.
Below is a list of common examples:
User Devices
- Laptops
- Desktops
- Smartphones
- Tablets
Servers and Workstations
- Database servers
- Web servers
- Development workstations
IoT and Embedded Devices
- Smart thermostats
- Industrial control systems
- Medical devices
Peripheral Devices
- Printers
- Scanners
- External storage drives
Cloud-Based and Virtual Resources
- Virtual machines (VMs)
- Containers (e.g., Docker instances)
- Cloud workloads in platforms like AWS, Azure, or Google Cloud
Endpoints serve as access points to an organization’s network and data. This makes them a critical part of the security strategy, as each endpoint can be exploited by attackers to gain entry, install malware, or exfiltrate data.
How Does Endpoint Security Work?
Deployment models
Most endpoint security solutions use one of the following deployment models:
- On-premises—the solution runs on a central server and agents are deployed on each endpoint connected to the network. The agent tracks and reports endpoint device activity and potential threats to the central server.
- Cloud based—the endpoint security vendor hosts and manages the solution in the cloud. This is much more scalable than a client-server model, and is typically billed on a subscription basis with no upfront costs. It is effective even when the endpoints are not connected to the corporate network.
Security techniques
Endpoint security solutions examine files, processes, and network traffic on the endpoint for indicators of malicious activity. When they detect a threat, endpoint security tools can automatically block it (Next-Generation Antivirus), enrich event data from threat intelligence feeds, and enable security teams to investigate it and respond (Endpoint Detection and Response).
Modern endpoint security solutions use the following techniques to detect and prevent threats on an endpoint:
- Signature matching—identifies malware or threats based on known identifiers, such as file hashes or origin IP addresses.
- Machine learning-based static analysis—identifies malicious scripts and programs by analyzing contained code. This can be done before programs or scripts are run, preventing systems from being infected.
- Sandboxing—isolates files or programs in a secure environment. This enables platforms to execute code or programs and inspect the resulting behavior. This can help security teams identify malware and refine identification methods.
- Allowlists and denylists—blocks access to data, applications, or ports based on predefined lists. Denylists block known threats while whitelists block anything that isn’t approved for access.
- Behavioral analysis—compares endpoint activity to known behavior baselines to identify suspicious events. This enables EPPs to identify novel or dynamic threats.
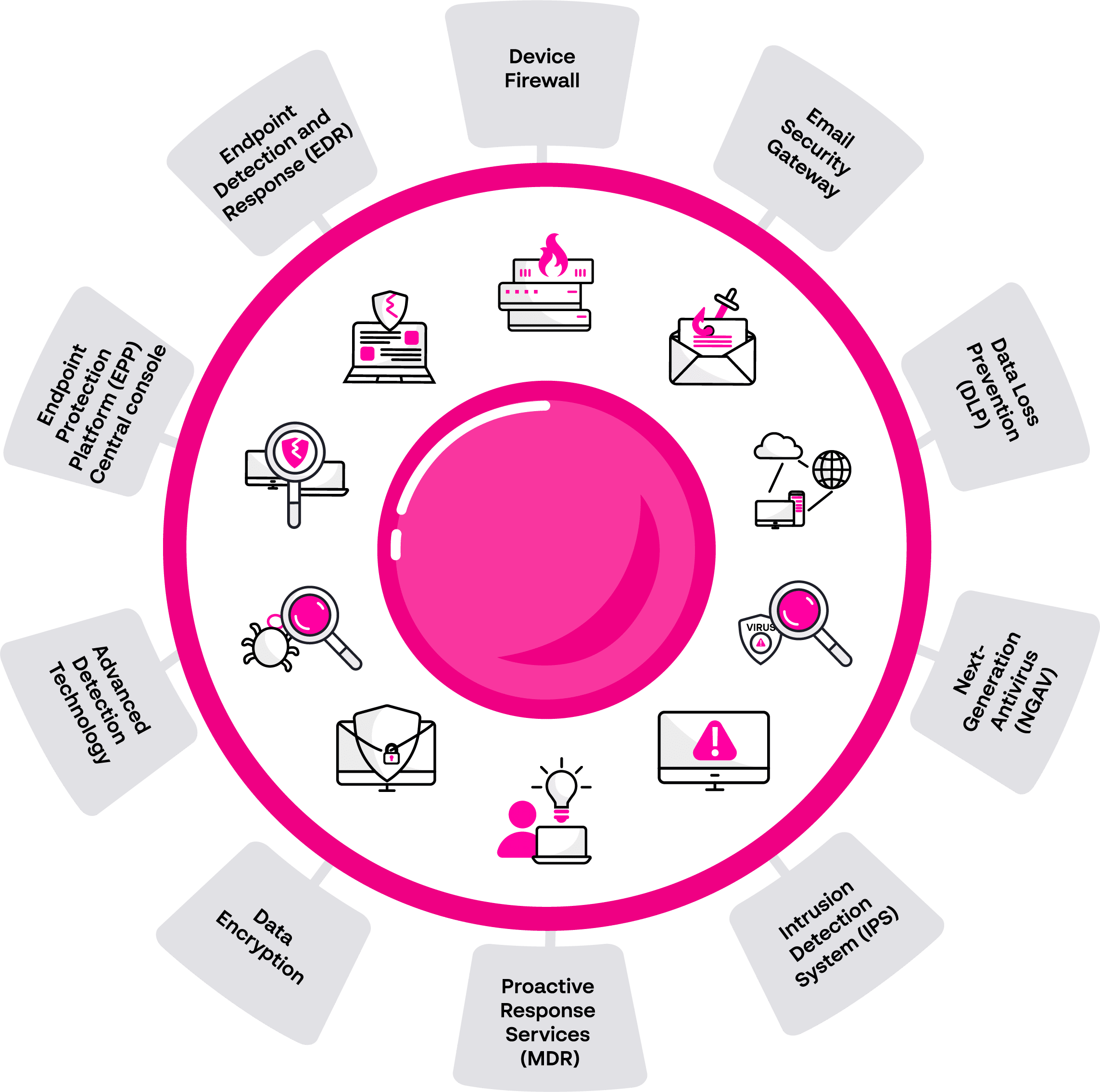
9 Defensive Layers of Endpoint Security
Endpoint protection platforms (EPPs) are tools designed to protect systems from threats. These platforms incorporate a variety of security tooling into centralized controls. Security tooling that is commonly included with EPPs includes:
Endpoint-specific tools:
- Next-generation antivirus (NGAV)
- Advanced detection technologies
- Endpoint Detection and Response (EDR)
- Managed Detection and Response (MDR)
General security tools deployed on the endpoint:
- Email security gateway
- Firewalls and other access controls
- Data encryption and authentication mechanisms
- Intrusion prevention systems (IPS)
- Data loss prevention (DLP) solutions
Below we expand on some of the more important components of endpoint security.
Next-Generation Antivirus (NGAV)
Many attacks are started or aided by malware and NGAV capabilities specialize in neutralizing these threats. In particular, NGAV helps protect your network with:
- Ransomware protection—blocking remote execution of code and the installation and execution of unknown programs, and ensuring data on the endpoint is backed up and recoverable.
- Exploit blocking – advanced and sophisticated attacks may use fileless malware, employing macros, in-memory, execution, and various other fileless techniques. Exploit blocking functionality can detect and block exploits as they occur.
- Advanced threat prevention—true NGAVs use advanced tools and techniques to block malware and fileless attacks and outsmart sophisticated attack techniques. These technologies can include AI and machine learning capabilities like behavioral analytics, adware blocking, deny and allow lists, or attack attribution.
- No need for updated signature lists—ML algorithms analyze large amounts of file data to identify suspicious files in real time. NGAV relies on signatureless malware detection to find and block known and unknown malware threats without requiring updates about malware signatures. It can even protect endpoints disconnected from the cloud.
- Online and offline protection—NGAV enables data processing and decision-making at the endpoint, supporting both online and offline threat prevention. It offers accurate incident detection and response capabilities to ensure that endpoints remain protected across all environments.
Detection Technologies
Attack detection capabilities focus on early and accurate threat identification and include the following:
- File integrity monitoring—tracks actions performed by users and processes and identifies when suspicious actions are taken, such as modifying or deleting files.
- Threat intelligence—information about threats, attack methods, and attack technologies. EPPs can ingest threat intelligence from outside sources and apply this intelligence to threat detection and response.
- Behavioral analysis—applies machine learning to aggregated network and endpoint data to determine normal baselines of activity. These baselines are then used as a comparison to identify if activity is suspicious.
- Vulnerability assessment—scans endpoints for vulnerabilities due to misconfigurations, lack of updates, or insecure code, and recommends remediation.
- Deception—deception technologies act as traps for attackers by appearing to hold valuable data. When triggered, security teams can isolate attackers and monitor their behavior.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) monitors and logs activity on endpoints, detects suspicious behavior and security risks, and enables security teams to respond to internal and external threats.
EDR technology gives security analysts visibility and remote access that allows them to investigate threats in real time, identify the root cause of an attack, contain it, and eradicate the threat.
EDR tools typically provide three key capabilities that can accomplish this function:
- Continuous endpoint data collection—aggregates events such as process execution, communication, and user logins.
- Detection engine—performs data analysis to detect anomalies and malicious activity on endpoints and identify real security incidents.
- Data logging—provides real-time data about endpoint security events. This enables rapid forensic investigation of threats as they happen.
Many organizations are adopting eXtended Detection and Response , an evolution of EDR solutions that helps teams detect and respond to attacks across endpoints, networks, email systems, cloud environments, and more.
Managed Detection and Response (MDR)
Response and remediation capabilities focus on applying detection data, alerting security teams to threats, and automating responses. These capabilities include the following:
- Incident response – MDR service providers investigate alerts to determine if they are real incidents, and if so, MDR experts immediately respond and eradicate the threat. The provider employs various investigation techniques, such as data analytics, human expertise, and machine learning.
- Threat hunting— proactively seeking out threats that have bypassed security measures. Performed by security experts with the assistance of big data analytics, threat intelligence, and centralized visibility of security events..
- Alert triage – various factors impact the priority of security events. MDR providers organize lists of security events to ensure you handle the most critical events first.
- Compliance reporting – regulatory compliance relies on proper security implementations. MDR providers can help meet compliance requirements and demonstrate compliance using reports.
- Log data collection or correlation – some MDR solutions provide comprehensive log management, including automatic collection, aggregation, and extended retention of log data. MDR engineers perform queries against log data sets, extracting useful information for customers.
Tips From Expert
- Integrate endpoint data with a security data lake
Centralize endpoint data in a security data lake for advanced analytics and threat correlation. This setup allows you to apply big data analytics and AI-driven insights to identify cross-environment attack patterns and potential weak points across all endpoints. - Utilize rollback capabilities for ransomware defense
Ensure your endpoint protection solution has rollback features that can reverse unauthorized changes. This allows you to quickly restore systems to a clean state after detecting ransomware, reducing downtime and avoiding costly data recovery processes. - Leverage AI-driven behavioral models for insider threat detection
Deploy AI models specifically designed to detect insider threats by analyzing deviations in user and endpoint behaviors. This helps flag potential threats from compromised accounts or malicious insiders that bypass traditional security controls. - Incorporate threat-hunting playbooks into your endpoint security operations
Develop playbooks for proactive threat hunting specifically targeting endpoints. Regularly execute these playbooks to identify advanced threats like living-off-the-land (LOTL) techniques or dormant malware that might evade automated detection mechanisms. - Automate incident response with adaptive remediation workflows
Design adaptive remediation workflows that change based on evolving threat contexts. For example, automatically escalate an endpoint’s response from quarantine to full wipe and reimage if initial containment fails, ensuring rapid and appropriate action is taken at each stage of an attack.
Endpoint Security vs. Antivirus
Endpoint security and antivirus solutions are often confused but represent different approaches to securing devices.
Antivirus software is a basic security solution designed to detect and remove known threats, primarily malware. It operates by scanning files against a database of virus signatures and heuristics. While effective against traditional threats like viruses and some forms of malware, antivirus tools are often limited in scope. They cannot defend against sophisticated threats like zero-day attacks or advanced persistent threats (APTs) and typically lack broader network security or advanced detection capabilities.
Endpoint security is a comprehensive solution designed to protect all endpoint devices. It integrates multiple layers of defense, including antivirus, endpoint detection and response (EDR), behavioral analysis, and encryption. Endpoint security solutions provide real-time monitoring, advanced threat intelligence, and proactive response capabilities. They address a wider range of threats, such as fileless malware, insider threats, and attacks that exploit vulnerabilities in applications or system configurations.
Key Differences:
| Feature | Antivirus | Endpoint Security |
| Scope | Focused on malware removal | Comprehensive endpoint defense |
| Threat Detection | Signature-based | Behavioral analysis, machine learning, and signatureless detection |
| Response Capabilities | Limited (delete or quarantine) | Advanced (isolation, rollback, automated remediation) |
| Management | Local configuration | Centralized management across devices |
| Integration | Standalone | Integrated with broader security frameworks |
Endpoint Security vs. Firewalls
A firewall is a network security device. It works as a gateway that filters traffic. An endpoint security solution offers various mechanisms to protect against endpoint threats and can include firewall technology.
Here are the two main categories of firewalls:
- Network firewalls – a network firewall runs on network hardware, filtering traffic between networks. For example, it can filter traffic passing between the public Internet and a corporate network.
- Host-based firewalls – a host computer is an endpoint that controls network traffic flowing in and out of machines. A host-based firewall runs on host computers.
Key Differences:
| Feature | Endpoint Security | Firewalls |
| Focus Area | Individual devices (endpoints) | Network traffic and boundaries |
| Threats Addressed | Malware, ransomware, insider threats | Unauthorized access, DDoS attacks, suspicious traffic |
| Scope | Device-specific | Network-wide |
| Common Tools | EDR, NGAV, encryption | Packet filters, proxy firewalls, IDS/IPS |
| Connectivity Requirement | Works offline | Requires network activity |
Endpoint Security vs. Network Security
Endpoint security and network security are both critical components of an organization’s cybersecurity strategy, but they focus on different aspects of protection and operate at different levels.
Endpoint security focuses on securing individual devices—such as laptops, desktops, smartphones, tablets, and IoT devices—that connect to an organization’s network. Its goal is to protect these endpoints from threats like malware, ransomware, and unauthorized access. Endpoint security solutions often include antivirus, endpoint detection and response (EDR), behavioral analysis, encryption, and access controls.
Network security, on the other hand, aims to safeguard the organization’s overall network infrastructure. This includes securing data in transit, preventing unauthorized access to the network, and protecting against attacks targeting network-level vulnerabilities. Common tools include firewalls, intrusion detection/prevention systems (IDS/IPS), virtual private networks (VPNs), and network access controls.
Key Differences:
| Feature | Endpoint Security | Network Security |
| Focus Area | Individual devices (endpoints) | The entire network infrastructure |
| Threats Addressed | Malware, ransomware, local attacks | DDoS, phishing, man-in-the-middle, unauthorized access |
| Scope | Device-specific defense | Network-wide protection |
| Common Tools | EDR, antivirus, encryption | Firewalls, IDS/IPS, VPNs |
| Connectivity | Works even when offline | Requires network connectivity |
Endpoint Security With Cynet All-In-One Cybersecurity Platform
Cynet 360 AutoXDR™ is a holistic security solution that protects against threats to endpoint security and across your network.
Cynet’s intelligent technologies can help you detect attacks by correlating information from endpoints, network analytics and behavioral analytics with almost no false positives.
With Cynet, you can proactively monitor entire internal environments, including endpoints, network, files, and hosts. This can help you reduce attack surfaces and the likelihood of multiple attacks.
Cynet 360 AutoXDR™ provides cutting edge EDR capabilities:
- Advanced endpoint threat detection—full visibility and predicts how an attacker might operate, based on continuous monitoring of endpoints and behavioral analysis.
- Investigation and validation—search and review historic or current incident data on endpoints, investigate threats, and validate alerts. This allows you to confirm the threat before responding to it, reducing dwell-time and performing faster remediation.
- Rapid deployment and response—deploy across thousands of endpoints within two hours. You can then use it to perform automatic or manual remediation of threats on the endpoints, disrupt malicious activity and minimize damage caused by attacks.
Learn more about our EDR security capabilities.
In addition, Cynet All-in-One provides the following endpoint protection capabilities:
- NGAV—providing automated prevention and termination of malware, exploits, Macros, LOLBins, and malicious scripts with machine learning-based analysis.
- User Behavior Rules—detecting and preventing attacks using compromised credentials through the use of behavioral baselines and signatures.
- Deception technology—planting fake credentials, files, and connections to lure and trap attackers, mitigating damage, and providing the opportunity to learn from attacker activity.
- Monitoring and control—providing asset management, vulnerability assessments, and application control with continuous monitoring and log collection.
- Response orchestration—providing manual and automated remediation for files, users, hosts, and networks customized with user-created scripts.
Learn more about the Cynet All-in-One security platform.
See Additional Guides on Key Data Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of data security.
EDR Tools
Authored by Cynet
- [Guide] EDR Security: Protecting the Network From Endpoint Threats
- [Guide] 10 Reasons Your Business Needs Endpoint Protection Software
- [Announcement] Cynet MITRE ATT&CK Results
- [Product] Cynet All-In-One Cybersecurity Platform
Incident Response
Authored by Cynet
- [Guide] What Is Incident Response?
- [Guide] Security Stack Examples & 6 Best Practices for Building Your Stack
- [Guide] Does Your Organization Need a Security Platform?
- [Product] Cynet 24×7 Security Center | Managed Detection and Response (MDR)
Endpoint protection
Authored by Cynet
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response