Unified Endpoint Management: 5 Key Components and Pros/Cons
What Is Unified Endpoint Management (UEM)?
Unified endpoint management (UEM) is a solution to manage a wide array of devices—ranging from desktops, laptops, tablets, smartphones, to IoT devices—under a single management interface. It integrates the functionalities of traditional client management and mobile device management, offering a platform for overseeing numerous endpoints within an organization.
This integration allows IT departments to use a unified dashboard for monitoring, managing, and securing all connected devices. UEM ensures consistent security standards, compliance enforcement, and policy implementations across all endpoints.
By providing a single pane of glass for overseeing end-user devices, UEM reduces complexity, aids in troubleshooting, and improves operational efficiencies within IT environments. The ability to coordinate and enforce security measures and configurations uniformly across disparate device types reduces security risks associated with endpoint vulnerabilities.
This is part of a series of articles about endpoint security
Evolution of Endpoint Management
Initially, organizations managed endpoints through simple desktop management systems (DMS) that focused on desktop computers within the traditional office environment. These systems were for basic functions, such as software installation and troubleshooting, primarily within the Windows OS environment.
As mobile devices entered the workplace, mobile device management (MDM) solutions emerged to handle smartphones and tablets. MDM allowed organizations to apply security policies, monitor devices, and perform remote actions, like locking or wiping data, on mobile devices. However, MDM lacked the capabilities to manage traditional desktops and laptops.
The next evolution, enterprise mobility management (EMM), expanded beyond mobile-specific tasks to include applications and content management, reflecting the increasing need for secure access to corporate data on personal devices. While EMM improved control over mobile devices, it still fell short of providing a unified approach for all device types.
Unified endpoint management (UEM) emerged as the next phase, integrating traditional client management, MDM, and EMM into a single platform. UEM can manage diverse endpoints, from desktops and laptops to mobile devices and IoT hardware. This evolution answered the need for centralized control, simplified management, and consistent security standards.
Related content: Read our guide to endpoint security management
Key Components of UEM
1. Device Management Across Platforms
UEM systems support device management across various platforms, ensuring integration and consistent policy enforcement. From Windows to macOS, Android to iOS, UEM provides a unified interface for managing all device types. This cross-platform capability ensures that users have a consistent experience and that IT departments can manage devices without platform-specific tools.
2. Application Management and Distribution
UEM helps administrators maintain an approved software catalog, enforce application usage policies, and automate updates. It can deliver, update, and maintain applications across all devices. UEM platforms enable application distribution, allowing IT teams to deploy applications remotely to devices, regardless of their operating systems. This ensures that all employees have immediate access to necessary tools and updates.
3. Security and Compliance Enforcement
UEM platforms enforce security policies consistently across all endpoints, ensuring data encryption, device compliance, and threat management are upheld. Centralized control minimizes vulnerabilities through real-time monitoring and automatic remediation. UEM systems regularly audit device configurations and generate reports to support compliance with industry standards and legal requirements, such as GDPR or HIPAA.
4. Identity and Access Management
Identity and access management (IAM) ensures that only authorized personnel have access and that user permissions align with organizational policies. UEM platforms simplify IAM by integrating identity verification processes, creating a centralized system for managing user identities across multiple platforms and devices.
5. Remote Monitoring and Troubleshooting
UEM solutions offer real-time visibility into device performance and status, enabling proactive maintenance and rapid troubleshooting to minimize device downtime. This capability helps maintain the operation of all endpoints. Troubleshooting tools in UEM platforms allow IT professionals to diagnose and fix device issues remotely, reducing the need for on-site support.
Tips From Expert
In my experience, here are tips that can help you better maximize the benefits of Unified Endpoint Management (UEM):
- Implement multi-layered security monitoring: While UEM centralizes device management, layering endpoint detection and response (EDR) tools with UEM provides additional visibility into endpoint behaviors. This multi-layered approach helps to detect anomalies missed by UEM alone, strengthening threat detection.
- Set adaptive policies based on risk level: Configure UEM to apply policies dynamically based on contextual risk, such as device location or network type. For example, restrict certain applications when devices connect to public Wi-Fi, adding flexibility while enhancing security.
- Leverage AI for predictive maintenance: Use UEM’s analytics to predict device issues before they impact users. Machine learning models trained on historical performance data can help identify devices likely to require attention soon, allowing for proactive intervention.
- Use geofencing and time-based access controls: Enable geofencing within UEM to restrict device functionality based on location. This feature, coupled with time-based access, can limit device access to sensitive resources based on when and where it is being used, reducing exposure to risk.
- Automate role-based access management: UEMs often integrate with IAM systems to manage user access, but automating access based on role changes is critical. This ensures that employees only have access to necessary data, immediately revoking access when roles change or they leave the organization.
Benefits of UEM for Organizations
Organizations implement unified endpoint management to benefit from the following:
- Enhanced security: UEM provides controls to mitigate risks associated with endpoint devices. UEM platforms enforce consistent security policies across all devices, deploying updates and patches to prevent vulnerabilities. Automated risk assessments and real-time threat alerts within UEM solutions ensure proactive defense mechanisms against cyber threats.
- Improved risk management: Risk management is reinforced through integrated security features such as encryption, remote wipe capabilities, and compliance auditing.
- Simplified IT operations: UEM optimizes IT operations by centralizing and automating management tasks, leading to cost reductions. By eliminating the need for multiple management tools, UEM simplifies workflows, reducing overhead costs associated with training, licensing, and maintenance. Simplified device configuration, application deployment, and security updates reduce time-to-resolve issues.
- Cost reduction: The consolidation of IT operations through UEM platforms leverages economies of scale. This improves operational efficiency and reduces total cost of ownership for endpoint devices.
- Improved employee productivity and user experience: By ensuring consistent application availability and performance, UEM solutions minimize disruptions and downtime. UEM also simplifies device configurations and updates, reducing user intervention and technical barriers.
- Scalability and future-readiness: UEM provides scalable solutions that adapt to organizational growth, ensuring future readiness. UEM platforms manage an increasing number of devices and users without degradation of performance or management complexity. They incorporate future-ready capabilities such as cloud integration, analytics, and automated updates.
Challenges in Implementing UEM
It is also important to be aware of the potential challenges that organizations may face when implementing UEM:
- Managing diverse devices and operating systems: The wide variety of device types—ranging from Windows and macOS computers to iOS and Android mobile devices—requires cross-platform support and consistent policy application. The complexity arises in maintaining consistent security standards and application availability on such diverse platforms.
- Ensuring user privacy and data protection: UEM solutions must balance strong security measures with respect for user privacy. Achieving compliance with data protection regulations like GDPR, while employing endpoint management solutions, is complex. Organizations must ensure that personal data collection is minimal and transparent.
- Integration with existing IT infrastructure: Organizations often have diverse and complex IT ecosystems, including legacy systems. This may complicate UEM integration efforts, presenting challenges related to compatibility, scalability, and resource allocation.
Best Practices for Successful UEM Deployment
Here are some of the measures that organizations can take to ensure the effectiveness of their UEM deployment.
Define Clear Policies and Objectives
Organizations must establish precise roles, permissions, and security protocols aligning with corporate goals and regulatory standards. Clearly communicated policies guide IT teams and end-users in understanding their responsibilities and operational boundaries.
Setting tangible objectives ensures that UEM deployment supports organizational priorities. Objectives might include improving security, simplifying device management, or enabling remote work capabilities. These targets should be measurable using various metrics.
Prioritize Security and Compliance Measures
Organizations should enforce consistent security protocols, including encryption, authentication controls, and regular patch updates. Risk assessments and compliance checks ensure devices adhere to relevant standards, such as GDPR or HIPAA, minimizing regulatory risks.
Identifying key compliance requirements and integrating them into UEM policies improves protection and governance. Ongoing security training and awareness initiatives further contribute to user understanding and adherence to protocols.
Ensure User Training and Adoption
Training programs ensure users understand UEM functionalities, security policies, and operational procedures. These programs enable smooth adoption and mitigate resistance to change, fostering a supportive user environment.
Developing user-centric training that addresses diverse skill levels aids in broadening acceptance and improves productivity. Continuous support and accessible resources, such as help desks or informational guides, assists users in navigating UEM systems.
Choose the Right UEM Solution Provider
Organizations must assess potential providers based on factors such as scalability, ease of integration with existing infrastructure, and support for diverse device types. A provider’s track record and customer support options are also important considerations.
Aligning the chosen UEM solution with organizational goals and IT strategies ensures consistency. Customizability, security features, and compliance options are critical when evaluating potential solutions.
Regularly Update and Maintain Devices
Consistent software updates and patches are important to protect devices against vulnerabilities and ensure compliance with security policies. Regular device maintenance maximizes performance and extends lifecycle while ensuring alignment with evolving technological standards.
Automated update processes within UEM solutions simplify maintenance tasks, reducing the burden on IT departments and minimizing user disruption.
Complementing UEM with Cynet Endpoint Security
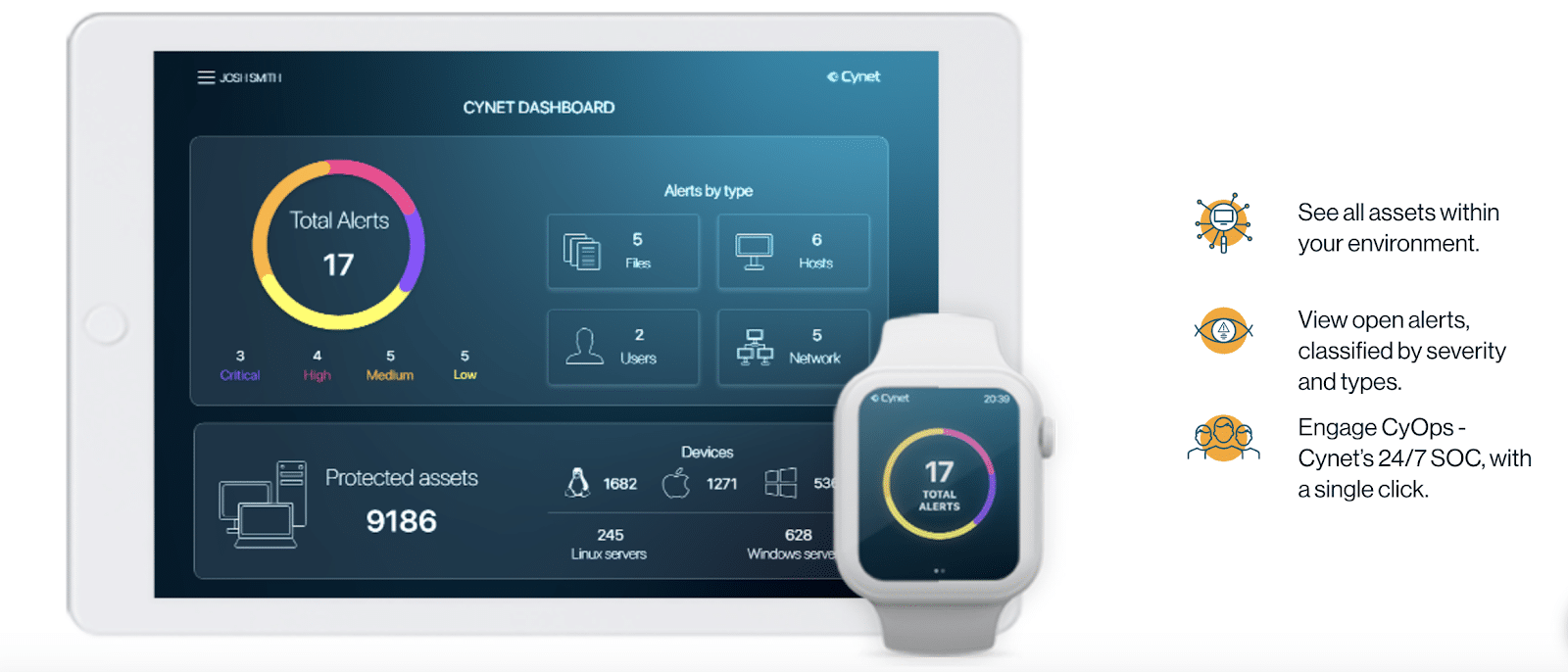
Cynet All-in-One is a holistic security solution that protects against threats to endpoint security and across your network.
Cynet’s intelligent technologies can help you detect attacks by correlating information from endpoints, network analytics and behavioral analytics with almost no false positives.
With Cynet, you can proactively monitor entire internal environments, including endpoints, network, files, and hosts. This can help you reduce attack surfaces and the likelihood of multiple attacks.
Cynet All-in-One provides cutting edge EDR capabilities:
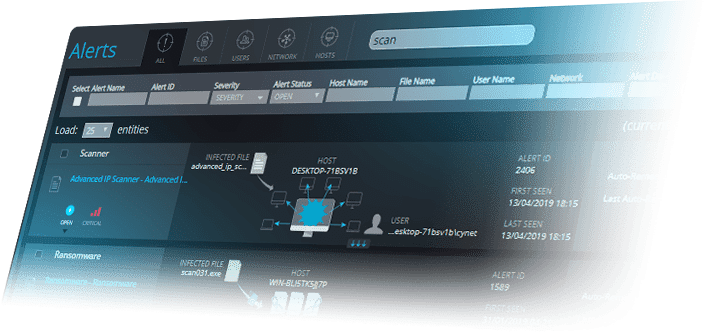
- Advanced endpoint threat detection—full visibility and predicts how an attacker might operate, based on continuous monitoring of endpoints and behavioral analysis.
- Investigation and validation—search and review historic or current incident data on endpoints, investigate threats, and validate alerts. This allows you to confirm the threat before responding to it, reducing dwell-time and performing faster remediation.
- Rapid deployment and response—deploy across thousands of endpoints within two hours. You can then use it to perform automatic or manual remediation of threats on the endpoints, disrupt malicious activity and minimize damage caused by attacks.
In addition, Cynet All-in-One provides the following endpoint protection capabilities:
- NGAV—providing automated prevention and termination of malware, exploits, Macros, LOLBins, and malicious scripts with machine learning based analysis.
- User Behavior Rules—detecting and preventing attacks using compromised credentials through the use of behavioral baselines and signatures.
- Deception technology—planting fake credentials, files and connections to lure and trap attackers, mitigating damage and providing the opportunity to learn from attacker activity.
- Monitoring and control—providing asset management, vulnerability assessments and application control with continuous monitoring and log collection.
- Response orchestration—providing manual and automated remediation for files, users, hosts and networks customized with user-created scripts.
Learn more about the Cynet All-in-One security platform.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response