In this article
- The Need for SIEM Solutions
- Key Features of SIEM Tools
- Notable SIEM Solutions
- 1. Splunk Enterprise Security
- 2. LogRhythm SIEM
- 3. IBM QRadar SIEM
- 4. Microsoft Sentinel
- 5. Exabeam Fusion
- 6. Securonix Unified Defense SIEM
- 7. Elastic Security SIEM
- 8. OpenText ArcSight Enterprise Security Manager
- 9. Sumo Logic Cloud SIEM
- 10. InsightIDR
- How to Choose a SIEM Provider
- Combining SIEM with XDR Solutions
- Security Automation with Cynet
SIEM Solutions: Key Capabilities & 10 Solutions to Know in 2025
What Are SIEM Solutions?
SIEM (Security Information and Event Management) solutions are software platforms designed to improve the security posture of an organization by providing real-time analysis of security alerts generated by applications and network hardware.
The primary goal of SIEM is to provide a centralized view of an IT environment and the security risks it faces, through the collection, analysis, and correlation of logs and data from various sources. SIEM systems are vital in detecting, preventing, and responding to security threats and incidents.
The Need for SIEM Solutions
Organizations face an increasing number of cyber threats, making it essential to have real-time visibility into security events. SIEM tools help by consolidating security data from multiple sources, enabling security teams to detect and respond to threats more efficiently.
One key reason for using SIEM tools is their ability to detect threats that would otherwise go unnoticed. Traditional security tools generate vast amounts of logs, but without correlation and analysis, important security events can be overlooked. SIEM solutions aggregate and analyze this data, helping identify patterns indicative of attacks.
Additionally, SIEM tools improve incident response by providing automated alerts and response mechanisms. This reduces the time required to detect and mitigate threats, minimizing potential damage. They also aid in compliance by generating reports for regulatory frameworks such as GDPR, HIPAA, and PCI DSS, ensuring organizations meet security and audit requirements.
Key Features of SIEM Tools
SIEM tools typically offer the following features:
- Log management and data aggregation: Collect logs from servers, network devices, and applications, allowing for centralized monitoring and management. This streamlines data analysis and aids in detecting anomalies that could indicate security threats.
- Threat detection: Identify potential threats by analyzing the data patterns and activities recorded in logs. SIEM tools employ advanced analytics, including machine learning and rule-based detection mechanisms, to identify suspicious activities that could indicate a security breach or an ongoing attack.
- Automated response: Once a threat is detected, SIEM tools enable rapid response capabilities. They automate responses to common threats and provide alerts and detailed instructions for more complex threats, enabling security teams to act swiftly and effectively.
- Forensic analysis: SIEM systems offer forensic tools that help organizations investigate security incidents after they occur. These tools enable analysts to look through the event logs to uncover the exact sequence of actions that led to the incident.
- Compliance reporting: They automate the generation of reports necessary for compliance with regulations like GDPR, HIPAA, or PCI DSS. This ensures that organizations meet legal obligations and avoid penalties related to non-compliance.
Notable SIEM Solutions
Here are some examples of popular SIEM solutions.
1. Splunk Enterprise Security
Splunk Enterprise Security (ES) is a SIEM platform that focuses on enhancing operational efficiency in security operations centers. It can handle large volumes of data, ensuring visibility across an organization’s digital environment. The platform integrates AI capabilities for dynamic data processing, supporting precise threat detection with contextual insights.
Features of Splunk Enterprise Security:
- Analytics: Enables rapid monitoring, detection, and investigation of threats.
- Curated detections: Offers over 1,500 pre-configured detections, developed by the Splunk Threat Research Team, aligned with major security frameworks such as MITRE ATT&CK and NIST CSF 2.0.
- Risk-based alerting: Implements a risk-based approach to reduce alert volumes by up to 90%, enhancing focus on high-priority threats.
- Unified threat management: Integrates detection, investigation, and response workflows within a single platform, leveraging Splunk’s SOAR capabilities.
- Comprehensive visibility: Provides visibility by ingesting, normalizing, and analyzing data from any source, supported by AI-driven tools.
Source: Splunk
2. LogRhythm SIEM
LogRhythm SIEM is a self-hosted platform designed for quick detection and remediation of security incidents, offering a lower total cost of ownership. It integrates specialized modules, dashboards, and rules that streamline the operational workflow. This SIEM solution aims to help security teams quickly identify and mitigate cyber threats.
Features of LogRhythm SIEM:
- Integrated threat management: Utilizes analytics to detect threats like phishing and MFA fatigue attacks swiftly.
- Visibility across the enterprise: Provides insights across all organizational environments—from endpoints to the cloud.
- Streamlined incident response: Offers a visual analyst experience that consolidates data and activity into a single narrative, making it easier for security teams to understand and respond to incidents.
- Threat intelligence: Incorporates LogRhythm’s Threat Intelligence Service (TIS) which synchronizes with third-party threat data.
Source: LogRythm
3. IBM QRadar SIEM
IBM Security QRadar SIEM is designed to enhance the capabilities of Security Operations Center (SOC) analysts using advanced automation and threat intelligence. This system focuses on accelerating the detection, investigation, and response times to cyberthreats. It integrates multiple layers of AI to assist in alert enrichment, threat prioritization, and incident correlation.
Features of IBM Security QRadar SIEM:
- Risk-based alert prioritization: Employs AI to apply multiple layers of risk scoring to each observable, ensuring that analysts receive alerts for the most critical issues first.
- Sigma rules and threat intelligence: Integrates with the SIGMA community and IBM X-Force® Threat Intelligence, providing actionable insights without the need for additional context.
- User and network behavior analytics: Features analytics that monitor user and network behavior, enhancing the detection of insider threats and network breaches.
- Federated search: Allows analysts to perform searches across data sources, improving the discovery of hidden threats across the security environment.
Source: IBM
4. Microsoft Sentinel
Microsoft Sentinel (formerly Azure Sentinel) is a cloud-native SIEM solution designed to simplify security operations through intelligent security analytics and AI-powered threat detection. It supports SOCs by providing tools for proactive threat detection, investigation, and response.
Features of Microsoft Azure Sentinel:
- Cloud scale data collection: Integrates across all users, devices, applications, and infrastructure, whether on-premises or across multiple clouds, to collect and analyze data.
- Threat detection: Utilizes analytics and extensive threat intelligence from Microsoft’s global network to detect novel threats and minimize false positives.
- AI-enhanced investigation and threat hunting: Leverages AI to aid in investigating threats and hunting suspicious activities.
- Automated incident response: Includes built-in orchestration and automation of common tasks, speeding up the response to incidents and reducing manual efforts.
Source: Microsoft
5. Exabeam Fusion
Exabeam Fusion offers New-Scale SIEM™, an advanced cloud-native platform that integrates capabilities for security log management, behavioral analytics, and automated threat detection, investigation, and response (TDIR). This platform is designed to streamline the workflows of security analysts by automating many manual tasks.
Features of Exabeam Fusion:
- Cloud-native scalability: Provides scalable, centralized storage and intelligent search capabilities for visibility across all attack surfaces, accommodating up to 2M events per second and 100PB of storage per instance.
- Behavioral analytics: Utilizes over 1,800 detection rules and 750 behavioral model histograms to baseline normal behavior and detect anomalies.
- Automated TDIR workflows: Automates the stages of detection, triage, investigation, and response, using machine learning-informed Smart Timelines™ that compile a cohesive narrative of security incidents.
- Integration options: Supports data collection from a range of sources with over 9,500 pre-built log parsers and seamless integration with open source and commercial threat intelligence feeds.
Source: Exabeam
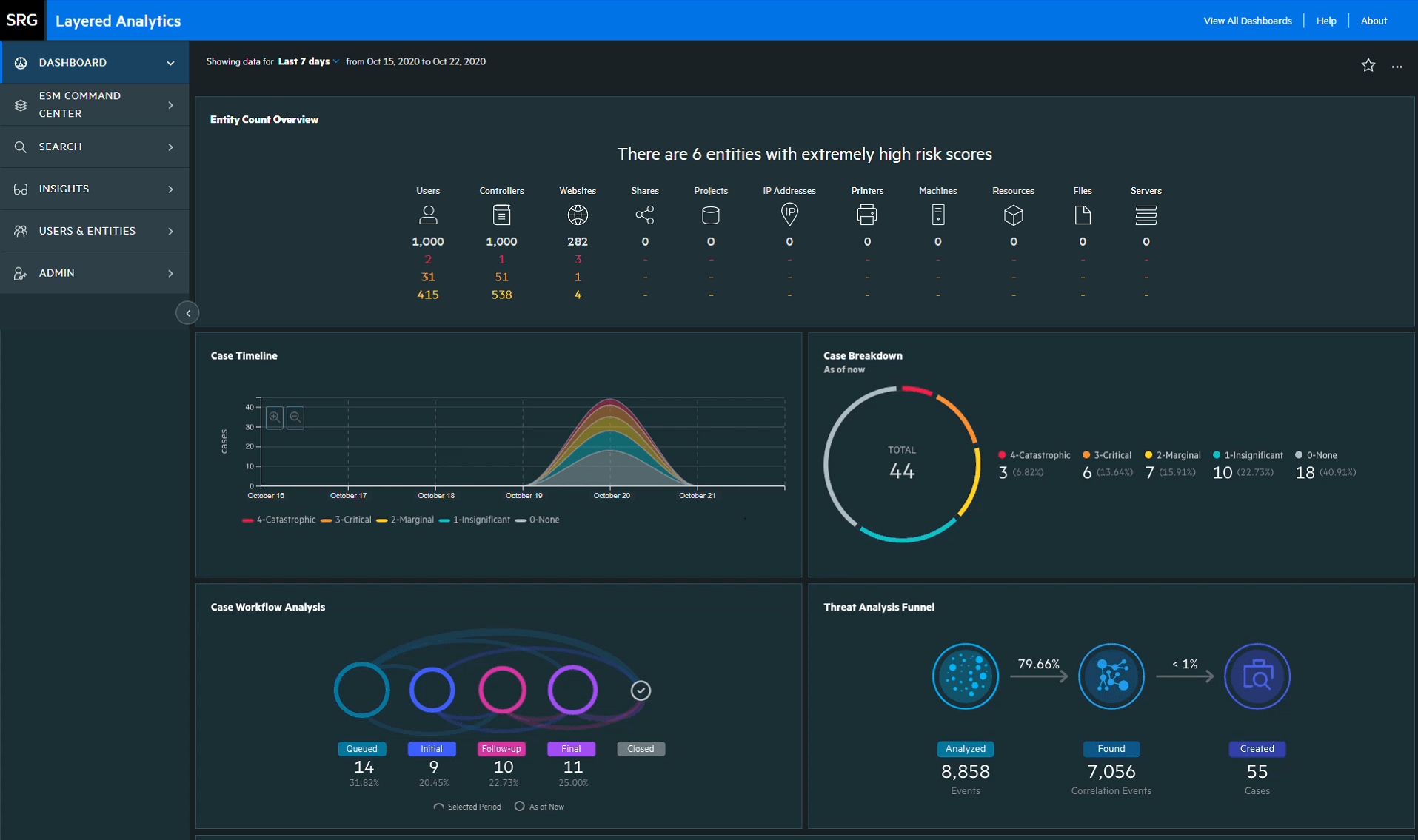
6. Securonix Unified Defense SIEM
Securonix Unified Defense SIEM combines threat detection, investigation, and response (TDIR). Built on the scalable Snowflake Data Cloud, this SIEM solution is intended for modern enterprises facing large data challenges, providing an architecture designed to enhance threat defense capabilities.
Features of Securonix Unified Defense SIEM:
- Data cloud scalability: Utilizes Snowflake’s Data Cloud to offer a scalable data storage solution that can handle extensive data requirements.
- Threat content-as-a-service: Delivers continuously updated threat content sourced from the Threat Labs team.
- Unified TDIR experience: Features a single interface with built-in SOAR capabilities, enabling a streamlined workflow that covers detection, investigation, and response. This integration helps eliminate the need for context-switching among different tools.
- Scalable architecture: Designed to meet the demands of modern data volumes without the complexities or costs associated with traditional SIEMs. The single-tier storage model is optimized for large-scale searches and eliminates performance bottlenecks.
Source: Securonix
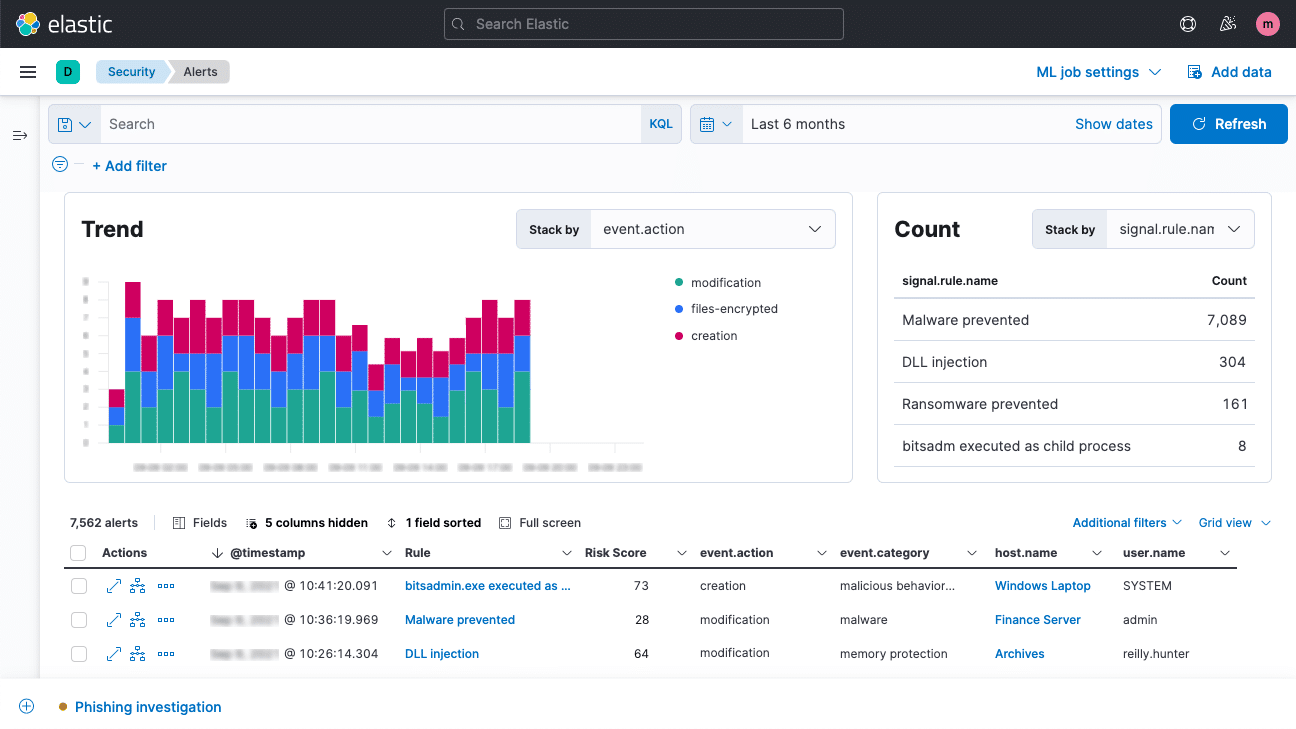
7. Elastic Security SIEM
Elastic Security SIEM focuses on threat detection, investigation, and response by leveraging AI-driven security analytics on its Search AI platform. This approach enables a comprehensive understanding of security threats and faster response times. Elastic Security’s SIEM system optimizes core SOC workflows through generative AI and machine learning.
Features of Elastic Security SIEM:
- AI-driven security analytics: Incorporates generative AI to enhance the capabilities of analysts across all skill levels.
- Data analysis: Provides the ability to handle data at the petabyte scale, performing analysis across different continents and clouds.
- Detection rules: Features detection rules crafted by Elastic Security Labs that are aligned with MITRE ATT&CK®. These rules are shared in an open repository, making them accessible for continuous updating and customization.
- Custom machine learning models: Allows for the creation and implementation of custom ML models to tackle new use cases without the need for data scientists.
Source: Elastic
8. OpenText ArcSight Enterprise Security Manager
OpenText ArcSight Enterprise Security Manager (ESM) is designed for real-time threat detection and response. It combines comprehensive data collection, real-time analysis, and a native SOAR capability, underpinned by a correlation engine. It allows rapid identification and triage of cyber threats, reducing the time from detection to response.
Features of OpenText ArcSight Enterprise Security Manager:
- Real-time threat detection: Leverages a SIEM correlation engine to detect and escalate known threats quickly, analyzing over 100,000 events per second to alert analysts to threat-correlated events.
- SOAR capabilities: Includes a built-in SOAR solution to modernize security analytics, providing out-of-the-box playbooks, incident management, and SOC analytics.
- Scalable and adaptable: Capable of scaling to handle 100,000+ events per second and offering customizable rules and content that can be tailored to meet specific organizational needs.
- Automated threat intelligence: Integrates open-source threat intelligence data automatically through a native feed, ensuring that security teams are always informed about the latest threats.
- Enterprise-Wide Event visibility: Aggregates, normalizes, and enriches data from more than 450 event source types.
Source: OpenText
9. Sumo Logic Cloud SIEM
Sumo Logic Cloud SIEM is designed to provide security analysts and SOC managers with enhanced visibility and streamlined workflows for rapid threat detection and response. It leverages analytics and features to improve the understanding of the scope and context of cyber threats, helping teams to manage and mitigate them.
Features of Sumo Logic Cloud SIEM:
- MITRE ATT&CK coverage explorer: Provides a detailed view of adversary tactics, techniques, and procedures (TTPs) covered by the Cloud SIEM rules.
- Enhanced alert triage: Integrates an Insight Engine that aligns with the MITRE ATT&CK framework, which employs an adaptive Signal clustering algorithm to group related alerts and generate insights.
- User and entity behavior analytics (UEBA): Identifies deviations from baseline behavior for users and entities, assigning risk rankings, and prioritizing investigations with smart Entity Timelines.
- Entity relationship graph: Provides a panoramic visualization to explore connections between entities, enhancing the ability to see the full scope of a cyber breach.
Source: Sumo Logic
10. InsightIDR
InsightIDR from Rapid7 is a SIEM solution designed for the cloud-first era, focusing on scalability, speed, and security coverage for hybrid environments. It supports digital transformation, SaaS adoption, and agile development through cloud-native capabilities.
Features of InsightIDR:
- AI-driven behavioral detections: Utilizes analytics and AI to pinpoint critical, actionable insights, allowing for effective command over the attack surface.
- High-context investigative timelines: Provides detailed timelines that outline attack techniques, impacts, and recommended responses, viewable in an integrated display.
- Expert-vetted threat content: Offers an up-to-date library of ATT&CK-mapped detections, including AI-driven alerts, attacker analytics, and indicators of compromise (IOCs).
- Cloud threat response: Simplifies the response to cloud-based threats with a tailored alert framework that highlights critical alert summaries, impacted resources, and recommended actions.
- Integrated security solutions: Combines capabilities like Endpoint Detection and Response (EDR), Network Traffic Analysis, and User and Entity Behavior Analytics (UEBA) with cloud integrations and embedded threat intelligence.
- Deception technology: Incorporates deception technology to enhance detection and response strategies.
Source: Rapid7
How to Choose a SIEM Provider
Selecting the right SIEM provider requires evaluating multiple factors to ensure the solution aligns with your organization’s security needs, infrastructure, and compliance requirements. Below are key considerations to help guide the decision-making process:
- Deployment model: SIEM solutions come in different deployment models, including on-premises, cloud-native, and hybrid. Cloud-based SIEMs offer scalability and ease of maintenance, while on-premises solutions provide greater control over data. Choose based on your organization’s IT architecture and security policies.
- Scalability and performance: A SIEM solution should be capable of handling the volume of logs and events generated by your infrastructure. Ensure it can scale with your organization’s growth and accommodate increasing data ingestion without performance degradation.
- Threat detection and analytics capabilities: Look for SIEMs that use advanced analytics, machine learning, and behavioral analysis to identify anomalies and threats. Solutions with built-in threat intelligence feeds and support for frameworks like MITRE ATT&CK improve detection capabilities.
- Incident response and automation: Automated response features, such as SOAR (Security Orchestration, Automation, and Response), help reduce manual effort in handling alerts and mitigating threats. SIEMs with integrated incident response workflows enable faster remediation.
- Compliance and reporting: If your organization must comply with regulations like GDPR, HIPAA, PCI DSS, or SOC 2, ensure the SIEM provides automated compliance reporting and log retention policies that meet regulatory requirements.
- Integration and compatibility: A good SIEM should integrate with existing security tools, including firewalls, endpoint detection, identity and access management (IAM), and cloud services. Verify its compatibility with your organization’s technology stack.
- Cost and total cost of ownership (TCO): SIEM solutions vary in pricing models—some charge based on log volume, others on events per second (EPS) or user count. Consider licensing fees, storage costs, and operational expenses when assessing affordability.
- Ease of use and management: A complex SIEM may require extensive configuration and a dedicated security team to manage it. Look for a solution with an intuitive interface, automated workflows, and robust support to ease deployment and ongoing management.
Combining SIEM with XDR Solutions
Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) solutions can work together to provide comprehensive cybersecurity protection. SIEM offers broad visibility into an organization’s IT environment by collecting and analyzing security data from various sources. XDR extends this by integrating endpoint, network, email, and cloud security, providing deeper insights and enabling faster detection and response. Together, SIEM and XDR solutions can enhance incident detection and response capabilities by offering layered security across multiple threat vectors.
Combining SIEM with XDR helps security teams correlate data from disparate systems, uncovering patterns that might otherwise go unnoticed. While SIEM focuses on aggregating logs and providing a high-level overview of the security posture, XDR automates response workflows to streamline threat mitigation. Organizations can benefit from a more efficient incident response process by harnessing the strengths of both tools, reducing the mean time to detect and respond to emerging threats, and improving overall security resilience.
Tips From Expert
- Prioritize high-quality data ingestion: Focus on ingesting high-quality logs and data from relevant sources to avoid overwhelming the system with low-value noise. This ensures your SIEM delivers actionable insights for effective threat detection and response.
- Continuously refine detection rules: Regularly update your SIEM detection rules to stay aligned with the evolving threat landscape. Leverage the latest threat intelligence to ensure your SIEM remains effective at identifying both known and zero-day threats.
- Embrace threat intelligence feeds: Integrate external threat intelligence feeds to enrich your SIEM capabilities. This enables correlation of internal events with global threat indicators, improving the accuracy of threat detection and reducing false positives.
- Automate routine tasks: Utilize automated playbooks within your SIEM to handle routine alerts and common incidents. This frees up your security analysts to focus on more complex and high-priority threats, ultimately enhancing overall SOC efficiency.
- Leverage behavioral analytics: Implement behavioral analytics within your SIEM to proactively detect anomalies that deviate from established baselines. This approach is particularly effective in identifying sophisticated attacks and insider threats that bypass traditional signature-based detection methods.
Security Automation with Cynet
Cynet provides the world’s first Autonomous Breach Protection platform that natively integrates endpoint, network and user attack prevention/detection of XDR with log management and analysis of CLM and automated investigation and remediation capabilities of SOAR, backed by a 24/7 world-class MDR service.
End to end, fully automated breach protection is now within reach of any organization, regardless of security team size and skill level. Most smaller businesses find that Centralized Log Management (CLM) is fully sufficient for their needs while far more affordable and usable than SIEM solutions.
XDR Layer: End-to-End Prevention & Detection
- Endpoint protection—multilayered protection against malware, ransomware, exploits and fileless attacks.
- Network protection—protecting against scanning attacks, MITM, lateral movement and data exfiltration.
- User protection—preset behavior rules coupled with dynamic behavior profiling to detect malicious anomalies.
- Deception—wide array of network, user, file decoys to lure advanced attackers into revealing their hidden presence.
CLM Layer: Log Management and Analysis
- Ingest log data—collect all pertinent log data to uncover threats across your environment
- Data visualization—advanced, targeted data queries pinpoint precursors to cyberattacks and perform forensic analysis
- Threat hunting—uncover evidence of compromised endpoints, systems, and data such as anomalous privileged account activity and anomalous outbound traffic
- Regulatory compliance—generate reports for FISMA, GLBA, HIPAA, SOX, and PCI DSS, for example, that regulatory bodies require.
SOAR Layer: Response Automation
- Investigation—automated root cause and impact analysis.
- Findings—actionable conclusions on the attack’s origin and its affected entities.
- Remediation—elimination of malicious presence, activity and infrastructure across user, network and endpoint attacks.
- Visualization—intuitive flow layout of the attack and the automated response flow.
MDR Layer: Expert Monitoring and Oversight
- Alert monitoring—First line of defense against incoming alerts, prioritizing and notifying customers on critical events.
- Attack investigation—Detailed analysis reports on the attacks that targeted the customer.
- Proactive threat hunting—Search for malicious artifacts and IoC within the customer’s environment.
- Incident response guidance—Remote assistance in isolation and removal of malicious infrastructure, presence and activity.
Simple Deployment
Cynet can be deployed across thousands of endpoints in less than two hours. It can be immediately used to uncover advanced threats and then perform automatic or manual remediation, disrupt malicious activity and minimize damage caused by attacks.
Get a free trial of Cynet and experience the world’s only integrated XDR, CLM, SOAR and MDR solution.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response