We didn’t need a groundhog to tell us that 2026 will continue to be brutal year of identity-based attacks and AI-powered threats.
This month’s threat activity did not hinge on zero-day exploits or noisy brute-force campaigns. Instead, adversaries leaned heavily on trusted platforms, legitimate tools, and predictable human behavior to bypass defenses quietly and at scale. From SharePoint-powered phishing to fake antivirus installers and insider-enabled ransomware, the message is clear: modern attacks succeed by abusing what organizations already trust.
Cynet’s January 2026 Cyber Threat Intelligence Report highlights the most important incidents, vulnerabilities, and malware families shaping this shift and outlines what security teams should prioritize next. No animals were roused from hibernation in the making of this report.
When Trusted Platforms Become the Payload
Threat actors are increasingly turning Microsoft SharePoint into a phishing delivery mechanism rather than relying on suspicious links or attachments. These campaigns often begin with emails sent from compromised but trusted organizations. Victims are directed to SharePoint-hosted links that lead to adversary-in-the-middle credential harvesting pages.
Once access is obtained, attackers quietly create malicious inbox rules to hide replies and maintain persistence. This enables large-scale business email compromise campaigns. Password resets alone are no longer enough. Effective remediation requires session revocation, inbox rule audits, and hardened authentication policies.
Brand Trust Weaponized Through Fake Security Tools
Another campaign exploited brand familiarity by impersonating Malwarebytes installers. Attackers used DLL sideloading techniques to deploy infostealers capable of harvesting credentials and cryptocurrency wallet data. Even security-aware users can be deceived when malicious files convincingly mimic legitimate security software.
Misconfiguration: The Self-Inflicted Entry Point
Researchers uncovered widespread abuse of intentionally vulnerable security training applications such as OWASP Juice Shop, DVWA, and Hackazon. These applications are designed for learning and testing, but attackers gained access because they were deployed with default credentials, excessive permissions, and direct internet exposure.
The issue was not the tools themselves but a lack of deployment discipline. Even large organizations were affected, reinforcing that misconfiguration remains one of the most reliable paths into modern environments.
Vulnerabilities That Demand Immediate Action
The most critical vulnerability observed this month was CVE-2025-64155, a remote code execution flaw in Fortinet FortiSIEM with a CVSS score of 9.8. A proof-of-concept exploit was released the same day the vulnerability was disclosed, and exploitation attempts quickly followed.
Organizations running vulnerable FortiSIEM versions should treat this issue as urgent.
Other high-risk vulnerabilities requiring immediate attention include critical flaws in Oracle Fusion and WebLogic, Zoom multimedia routers, and Cisco Unified Communications products.
Legacy Authentication Still Creates Real Risk
Despite years of warnings, NTLMv1 remains enabled in many enterprise environments. Mandiant demonstrated that Net-NTLMv1 hashes can now be cracked in hours using low-cost hardware. What was once a theoretical risk has become a practical and scalable attack method. Any remaining NTLMv1 usage should be eliminated entirely.
Ransomware Operations Continue to Mature
Law enforcement identified Oleg Evgenievich Nefedov as the leader of the Black Basta ransomware operation. The group has been linked to more than 500 victims and at least 107 million dollars in ransom payments. A large internal chat leak revealed a structured organization that routinely exploits known vulnerabilities for initial access.
Meanwhile, the Scattered Lapsus Hunters collective resurfaced with a ransomware-as-a-service platform called ShinySp1d3r. The group is actively recruiting insiders with privileged access, signaling a shift toward monetizing internal trust rather than relying solely on social engineering.
ClickFix Attacks Turn Confusion Into Compliance
ClickFix campaigns continue to evolve by using fake Windows error screens and trusted web services to manipulate users into executing malicious commands. These attacks rely on urgency and familiarity rather than technical sophistication. Once users are convinced something is broken, they often complete the attack themselves.
Malware Trends Worth Watching
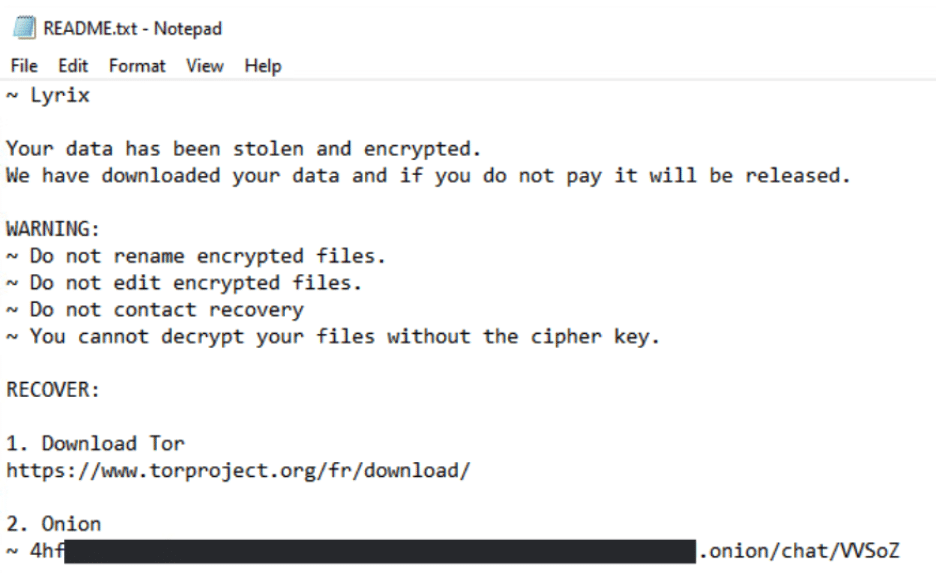
Lyrix ransomware continues to rely on double extortion tactics and aggressively disables recovery options to maximize pressure on victims. The ransomware aims for maximum impact by performing actions to ensure that encrypted files cannot be recovered locally, adding annoyance to an already challenging situation.
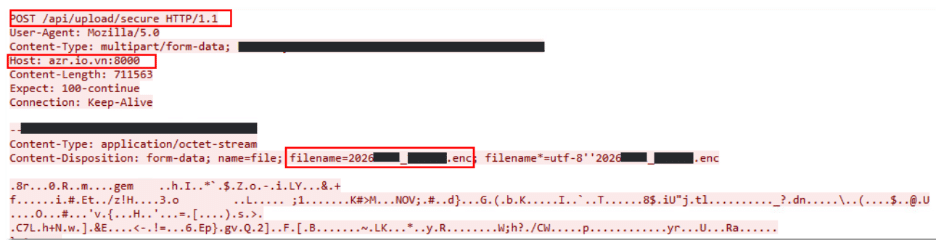
Cattore Stealer masquerades as a legitimate Windows process and targets browsers, VPNs, cloud storage, cryptocurrency wallets, and Wi-Fi credentials. All collected data is exfiltrated directly to attacker-controlled servers without leaving local traces.
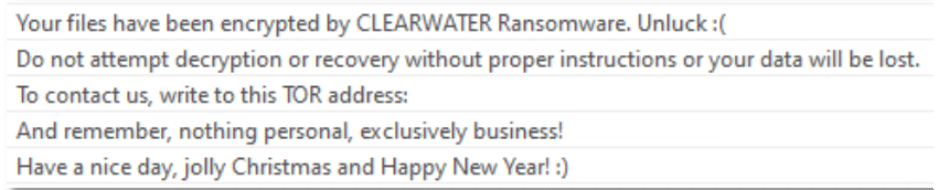
Clearwater ransomware, first observed in January 2026, focuses exclusively on encryption. It deletes backups, disables recovery tools, and avoids public leak sites entirely. Something tells us that the recipients of this ransom note are most definitely not enjoying their new year.
Key Takeaways for Security Teams
Security teams should prioritize patching critical vulnerabilities, especially those affecting FortiSIEM, Oracle, Zoom, and Cisco products. Legacy authentication protocols such as NTLMv1 should be fully disabled. Training and test environments must be locked down and removed from public exposure.
Inbox rules and active sessions should be audited regularly. Browser extensions should be minimized and reviewed. Insider access should be treated as a primary risk vector. User training must keep pace with evolving social engineering techniques, including ClickFix-style attacks.
Our Prediction: Many More Weeks of Malicious Activity Ahead
The January 2026 threat landscape shows that attackers are not bypassing security controls as much as they are abusing trust. Platforms, identities, tools, and people are all being leveraged as entry points.
Defensive resilience in 2026 depends less on adding new controls and more on reducing implicit trust across the environment. Organizations that adapt to this reality will be better positioned to detect, contain, and respond to modern threats before damage is done.


