While much of the world slowed down for the holidays, cybercriminals did the opposite – ramping up operations to capitalize on timing and opportunity. Although coordinated international law enforcement efforts briefly disrupted some activity, attackers largely stuck to proven tactics. Cynet’s November 2025 Cyber Threat Intelligence Report reveals criminals used familiar playbook: abusing trusted software ecosystems, accelerating ransomware operations, and weaponizing stolen credentials at scale. Critical vulnerabilities and exposures (CVEs) continued to compound headaches for security teams, with Samsung devices, Google’s Chrome browser, Fortinet, and Windows systems all reporting new critical vulnerabilities in the same month.
Download the Complete 2025 November Cyber Threat Intelligence Report, powered by CyOps.
Supply Chain Attacks Are Becoming the Primary Entry Point
Attackers are increasingly targeting the software and SaaS platforms organizations rely on for critical operations. In November, major supply chain breaches impacted npm packages, Salesforce-connected applications, and open-source ecosystems. In several cases, attackers abused OAuth tokens, over-permissioned integrations, and poisoned dependencies to move laterally and extract data without triggering traditional alerts.
Even more concerning, researchers uncovered malicious packages containing delayed logic bombs designed to activate years after deployment, demonstrating how supply chain compromises can remain dormant and undetected long after installation.
Takeaway: Third-party risk is now first-party risk. Security teams need comprehensive visibility into integrations, dependencies, and abnormal behavior across their environments.
Ransomware Is Faster, More Destructive, and Harder to Contain
Ransomware activity remained elevated, with manufacturing remaining most targeted sector and the United States the most impacted country (unchanged from our observations in the October Cyber Threat Intel report). New groups and familiar faces are combining data exfiltration, encryption, backup destruction, and anti-forensic techniques to maximize pressure on victims.
Kyber and BlackShrantac ransomware were the stars of this month’s report, leveraging advanced evasion and double-extortion tactics to ensure both operational disruption and data exposure. In the spirit of the season, the BlackSharntac team was even kind enough to leave its calling card for victims in the form of a new desktop wallpaper:

Takeaway: Ransomware defense cannot rely on an endpoint-only strategy. It is a full kill-chain threat that demands prevention across endpoints, identities, IoT devices, and networks.
Infostealers Are Fueling the Entire Attack Economy
Credential-stealing malware continues to underpin ransomware, supply chain abuse, and account takeovers. High-profile breaches last month demonstrated how a single infected endpoint can lead to widespread access across collaboration platforms, cloud services, and internal systems.
November’s report features BBAVPN stealer, another stealer written in Go, not unlike the one we highlighted in the October CTI report. The stealer creates a directory to store stolen browser data, including cookies, browsing history, and saved passwords sends, and sends the stolen data to the threat actor’s Alibaba Cloud bucket.
Takeaway: Stolen credentials remain the fastest path to breach. Speed in detection and containment is critical to interrupting stealers before they exfiltrate data.
AI Defenses Are Now a Target
Researchers also uncovered Echogram, a technique that bypasses AI safety guardrails through adversarial prompt manipulation. As AI becomes more embedded in security operations and business workflows, attackers are actively probing its weaknesses.
Takeaway: AI must be protected and validated like any other critical system, because attackers are already adapting.
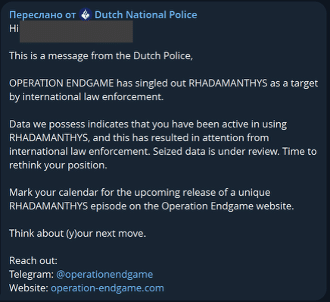
Operation Endgame Thwarts Global Criminal Network
In November, Europol announced the third phase of Operation Endgame, dismantling key infrastructure behind the Rhadamanthys infostealer, VenomRAT remote access trojan, and the Elysium botnet. These malware families were central to global cybercrime operations and responsible for widespread credential theft and system compromise. Authorities also arrested the main VenomRAT suspect in Greece.
The takedown disrupted malware infrastructure that had infected hundreds of thousands of systems worldwide, harvesting millions of stolen credentials. Investigators revealed that operators behind the infostealer campaigns had access to more than 100,000 compromised cryptocurrency wallets, underscoring both the scale and financial impact of these operations.
Launched in 2024, Endgame is an international law enforcement operation led by Europol and the FBI, targeting major cybercriminal rings with the goal of disrupting and dismantling cybercrime ecosystems.
How Cynet Helps Security Teams Stay Ahead
Cynet’s unified cybersecurity platform is designed to detect and prevent emerging threats across the full attack lifecycle. By combining endpoint protection, network visibility, behavioral detection, and automated response, Cynet enables security teams to stop attacks earlier, reduce dwell time, and operate with confidence, even as the threat landscape evolves.



