10 Endpoint Security Solutions to Know in 2025
What Is Endpoint Security?
Endpoint security refers to the strategy of protecting network endpoints—devices such as computers, smartphones, and tablets—from cyber threats. These endpoints act as access points to a network and can be vulnerable to attacks without proper protection.
Endpoint security solutions focus on providing security measures, including network access control, antivirus software, and firewalls, to prevent attackers from exploiting these entry points and gaining access to the network. By implementing endpoint security, organizations ensure devices connected to their network are safe from malicious threats.
Unlike traditional security measures that focus on the network’s perimeter, endpoint security works directly on each device to detect and neutralize potential threats. This approach is especially important as the number of connected devices continues to grow, exposing networks to diverse threats.
Types of Endpoint Security Solutions
Endpoint Protection Platforms (EPP)
Endpoint protection platforms offer security by integrating antivirus, anti-malware, and firewall capabilities into a single solution. These platforms focus on preventing threats by identifying and neutralizing malicious software before it can compromise the device. EPP solutions are used for creating a multi-layered defense, offering baseline security measures.
EPP solutions continuously scan devices for known threats, relying on signature-based detection methods. While effective against many traditional threats, their reliance on known threat signatures and rule-based mechanisms may limit their ability to detect new, sophisticated attacks.
Endpoint Detection and Response (EDR)
Endpoint detection and response solutions provide continuous monitoring and analysis of endpoint activities. Unlike EPP, which focuses primarily on prevention, EDR emphasizes detecting and responding to threats. This is achieved through behavior analysis and threat hunting capabilities that identify deviations from normal activity, alerting security teams.
EDR platforms allow for incident investigation by providing detailed forensics data on threat activities and system changes. This data helps security professionals to uncover the root cause of incidents, enabling faster response and remediation. EDR tools work best when integrated into a broader security strategy that includes threat intelligence and contextual analysis.
Extended Detection and Response (XDR)
Extended detection and response solutions expand upon EDR capabilities by incorporating data from multiple security control layers, including networks, servers, and cloud environments. XDR solutions unify security investigations across different security components, providing a holistic view of the threat landscape, which enables more efficient threat detection and remediation.
By integrating and correlating data from various sources, XDR solutions offer improved threat detection accuracy and faster response times. This consolidated approach helps organizations mitigate complex threats that would otherwise slip through traditional defenses.
Managed Endpoint Security Services
Managed endpoint security services offer organizations outsourced management of endpoint security tasks, providing expertise and resources that may not be available in-house. These services include continuous monitoring, threat detection, and incident response, enabling businesses to focus on core operations while ensuring endpoint security is up-to-date.
These services are suitable for organizations lacking the internal resources or expertise to manage endpoint security independently. By partnering with managed security providers, organizations can benefit from newer security technologies and expert analysis tailored to their risk profile.
Related content: Read our guide to endpoint security management
Key Features of Effective Endpoint Security Solutions
Endpoint security solutions typically offer the following capabilities.
Real-Time Threat Detection and Response
Effective endpoint security solutions should feature real-time threat detection and response capabilities. This enables the immediate identification and mitigation of potential threats, preventing them from inflicting damage. By employing automated tools and analytics, security solutions can quickly detect malicious activities, reducing downtime.
Behavioral Analysis and Machine Learning
Behavioral analysis and machine learning technologies enable systems to identify abnormal behavior that could signify a threat. By analyzing patterns, machine learning models can detect unknown threats without relying solely on signature-based detection, offering protection against novel and emerging cyber threats.
Scalability and Flexibility
As the number of devices and users increases, security solutions must efficiently manage and secure all endpoints without compromising performance. This scalability ensures that security protocols remain effective despite changes in network size or structure. Additionally, flexibility is crucial for adapting to evolving threats and technological advancements.
Integration with Existing Security Infrastructure
An effective endpoint security solution integrates smoothly with existing security infrastructure, providing a comprehensive defense. This integration allows for coordinated threat response, leverages existing resources, and improves overall security posture. Integration ensures that security protocols and data remain consistent across different systems.
Tips From Expert
In my experience, here are tips that can help you better adapt to endpoint security solutions:
- Use behavioral analytics to detect lateral movement: Beyond traditional monitoring, behavioral analytics can identify subtle patterns indicating lateral movement within your network. These early warnings can prevent attackers from escalating privileges or expanding their reach.
- Implement proactive deception techniques: Consider adding decoy files, fake credentials, or honeytokens within endpoints. These deceptive elements lure attackers, helping you detect intrusions and gather intelligence without exposing real assets.
- Leverage AI-driven anomaly baselines for adaptive security: AI models should evolve with new user patterns. Set baseline behaviors and continuously retrain models to identify deviations in real-time, especially during new rollouts or significant changes in operations.
- Prioritize real-time file integrity monitoring (FIM): Real-time FIM can quickly identify unauthorized modifications or access to critical files, including sensitive configurations or system binaries, providing immediate alerts for potential breaches or insider threats.
- Isolate high-risk devices in dynamic micro-segments: Utilize dynamic micro-segmentation to limit the damage of compromised endpoints. This tactic ensures compromised devices are isolated quickly and restrict lateral movement until remediation is completed.
Notable Endpoint Security Solutions and Tools
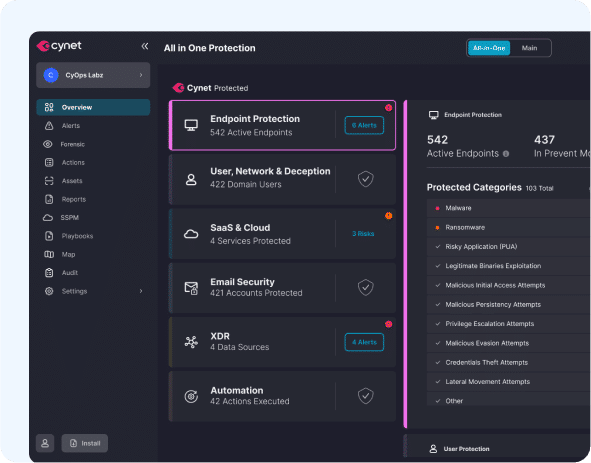
1. Cynet
Prevention features: Next-Generation Antivirus (NGAV) that blocks malware, exploits, LOLBins, Macros, malicious scripts, and other malicious payloads. Zero-day protection using User and Entity Behavior Analytics (UEBA) to detect and block suspicious activity. Asset management, endpoint vulnerability assessments and application control, with auditing, logging and monitoring. Deception technology lures attackers to a honeypot, gathering useful intelligence about attack techniques. Network analytics identifies lateral movement, suspicious connections and logins.
EDR features: Advanced endpoint threat detection predicts attacker behavior based on continuous monitoring of endpoints and behavioral analysis. Searches and reviews historic or current incident data on endpoints to help investigate threats and validate alerts, for faster remediation. Automatic response orchestration and manual remediation of threats on endpoints. Deployment across thousands of endpoints within two hours.
2. CrowdStrike Endpoint Protection
CrowdStrike Endpoint Protection is a cybersecurity solution to protect organizations from threats by securing endpoints. Powered by AI and machine learning, this platform provides protection, detection, and response capabilities. It focuses on preventing breaches through real-time threat analysis and blocking malicious activities at all stages of the attack chain.
Key features of CrowdStrike Endpoint Protection:
- AI-powered threat protection: Leverages AI/ML to detect and block malware, fileless, and zero-day threats early in the attack chain.
- Unified visibility: Provides cross-domain visibility across cloud, endpoints, and identities, helping stop adversaries from moving laterally across environments.
- EDR coverage: Delivers a unified solution for endpoint detection and response, offering real-time protection with minimal false positives.
- Multi-OS support: Ensures protection across all major operating systems, including Windows, macOS, Linux, and ChromeOS, as well as legacy systems.
- AI-driven investigations: Uses AI to accelerate threat prioritization and response, reducing investigation times and empowering security teams.
Source: CrowdStrike
3. ESET Endpoint Protection
ESET Endpoint Protection is an endpoint protection platform (EPP) to secure devices from cyber threats, including malware, ransomware, and fileless attacks. ESET’s global threat detection network, machine learning, and human expertise help deliver multilayered protection across major platforms, including Windows, macOS, Linux, iOS, and Android.
Key features of ESET Endpoint Protection:
- Multi-layered defense: Provides protection at every stage of malware execution (pre-execution, during, and post-execution) to maximize security against diverse threats.
- Cross-platform support: Offers protection for a range of operating systems, including ARM-based devices, with built-in mobile device management for iOS and Android.
- Lightweight performance: Designed for minimal system impact, ensuring protection without compromising device performance.
- Ransomware shield: Adds an extra layer of defense by evaluating application behavior and utilizing Intel threat detection technology to detect and block ransomware attacks.
- Fileless attack prevention: Mitigates threats that exist only in memory by detecting and neutralizing hijacked or malformed applications.
Source: ESET
4. Broadcom Symantec Endpoint Security
Broadcom Symantec Endpoint Security offers a solution to protect all endpoints, including desktops, laptops, mobile devices, servers, cloud workloads, and more. By leveraging technologies like AI-driven management and real-time threat intelligence, Symantec provides a defense against both known and emerging threats.
Key features of Broadcom Symantec Endpoint Security:
- Endpoint protection: Secures a range of endpoints, including desktops, laptops, iOS/Android devices, servers, and cloud infrastructures, protecting against threats.
- Cloud and hybrid deployment: Offers flexible deployment options, allowing organizations to implement on-premises, cloud-based, or hybrid security solutions based on their needs.
- Single agent architecture: Deploys a single agent for endpoint protection, EDR, application control, and isolation, reducing complexity and improving security efficiency.
- Unified management console: Allows real-time visibility and management of all endpoints from a single console.
- Autonomous security management: Utilizes AI-driven security management to continuously assess and improve the organization’s security posture.
Source: Broadcom
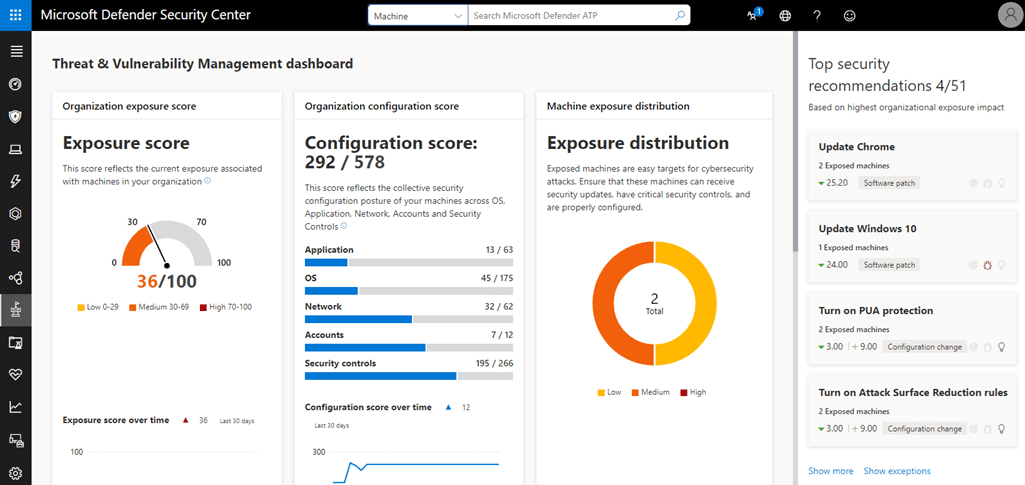
5. Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is an AI-powered endpoint security platform to protect devices across multiple platforms, including Windows, macOS, Linux, Android, iOS, and IoT. The solution combines threat detection, prevention, and response capabilities to block sophisticated cyber threats such as ransomware.
Key features of Microsoft Defender for Endpoint:
- Multiplatform protection: Provides industry-leading security across Windows, macOS, Linux, Android, iOS, and IoT devices, ensuring comprehensive endpoint coverage.
- AI-powered threat detection: Leverages AI to detect and block cyberattacks, including ransomware, enabling faster threat responses.
- Global threat intelligence: Uses Microsoft’s global threat intelligence network to identify vulnerabilities, offering insights and best practices for cyberthreat prevention and mitigation.
- Automatic attack disruption: Automatically disrupts ransomware attacks by blocking lateral movement and remote encryption, stopping threats early in the attack chain.
- Unified security operations: Integrates XDR with security information and event management (SIEM), creating a single platform for security operations.
Source: Microsoft
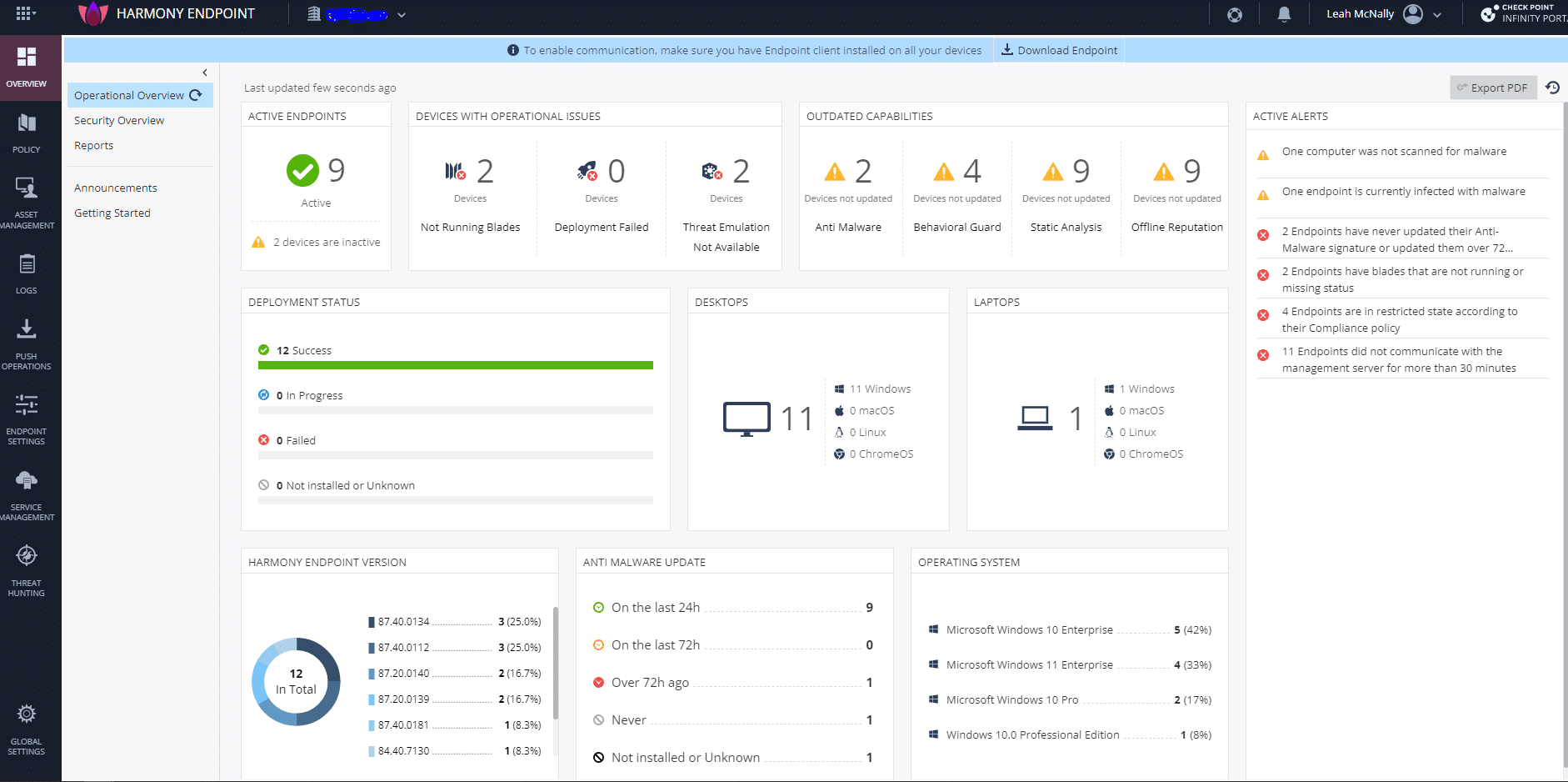
6. Check Point Harmony Endpoint
Check Point Harmony Endpoint is a security solution to protect endpoints from cyber threats. It integrates EPP, EDR, and XDR capabilities into a single, unified client. Harmony Endpoint helps secure remote workforces against ransomware, phishing, and data loss.
Key features of Check Point Harmony Endpoint:
- Single-agent architecture: Combines EPP, EDR, and XDR capabilities within a single agent and management console, simplifying deployment and monitoring across all endpoints.
- Flexible management options: Offers on-premises, cloud, or MSSP management to adapt to different organizational needs and infrastructures.
- Extensive OS support: Provides protection for a range of platforms, including Windows, macOS, Linux, virtual desktops, browsers, and mobile devices.
- Threat intelligence: Utilizes ThreatCloud AI, equipped with over 60 AI engines to provide zero-day protection against emerging threats.
- Ransomware and malware defense: Shields endpoints from ransomware and malware attacks, protecting organizational data from breaches.
Source: Check Point
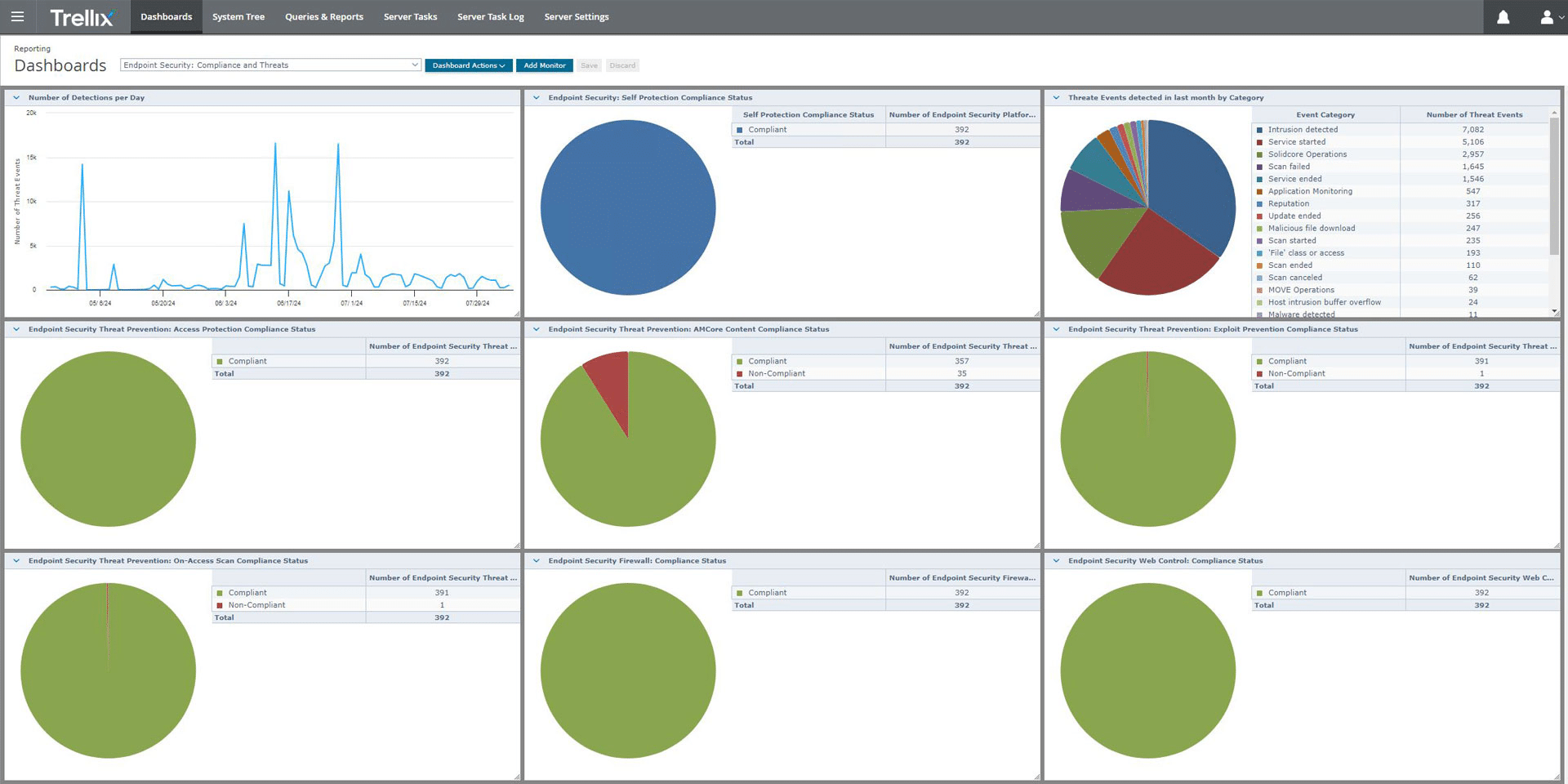
7. Trellix Endpoint Security Suite
Trellix Endpoint Security Suite is a security solution that provides multi-layered protection across hybrid environments. It integrates detection, protection, forensics, and remediation capabilities into a single agent, helping organizations reduce their attack surface, detect threats, and recover quickly from incidents.
Key features of Trellix Endpoint Security Suite:
- Single-agent architecture: Offers attack surface reduction, threat protection, detection, forensics, and remediation through a unified agent across hybrid environments.
- Ransomware prevention: Protects against ransomware attacks with unique remediation rollback capabilities, enabling swift recovery from potential damage.
- AI-enhanced investigations: Allows security analysts to speed up investigations using AI-powered tools that automate threat analysis and reduce manual effort.
- High-fidelity alerts: Delivers accurate, low false-positive alerts through its multi-layered protection stack.
- Simplified management: Reduces operational overhead by providing a single management console to oversee security across diverse systems and environments.
Source: Trellix
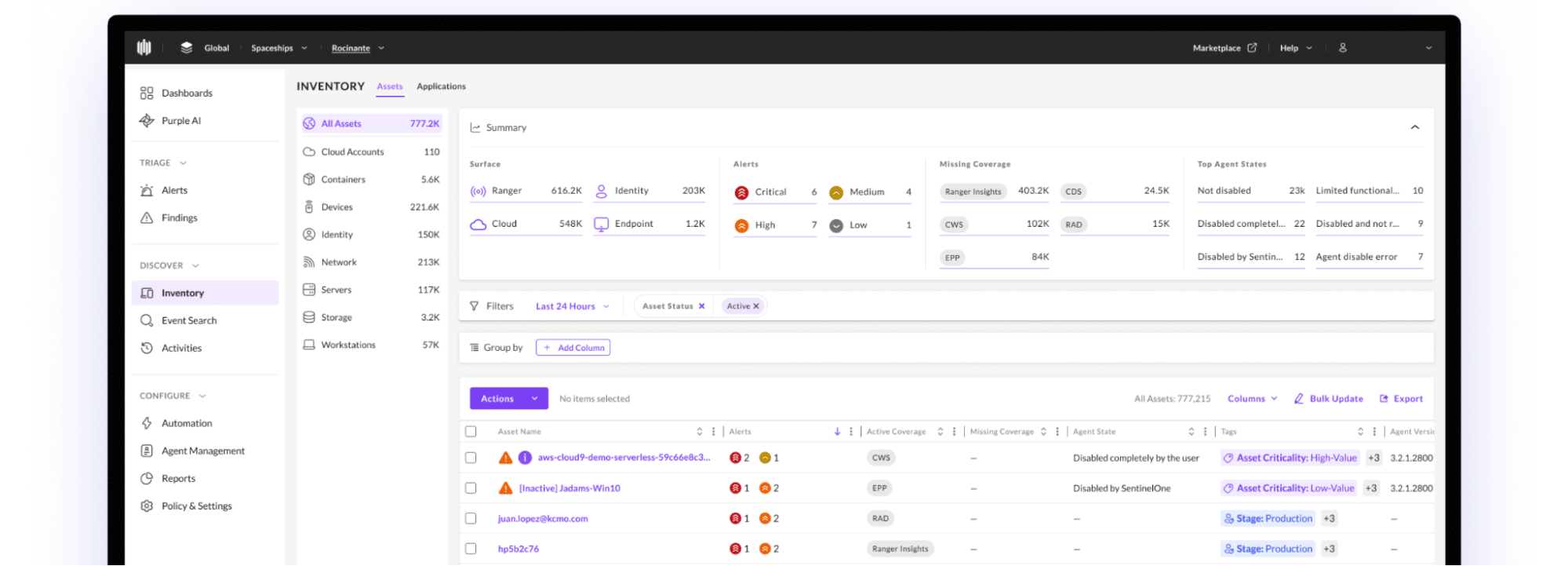
8. SentinelOne Singularity Complete
SentinelOne Singularity Complete is a cybersecurity platform that provides automated enterprise-grade prevention, detection, response, and hunting capabilities across endpoints, cloud environments, and identities. With a unified agent and deep cross-surface visibility, it helps stop known and unknown threats while simplifying security operations.
Key features of SentinelOne Singularity Complete:
- Unified EPP and EDR: Combines next-gen antivirus (NGAV) and enterprise-grade EDR into a single agent.
- Storyline™ technology: Provides in-depth visibility by automatically tracking OS relationships and creating a real-time attack context, allowing for efficient root cause analysis and full understanding of threats.
- Automated threat resolution: Enables one-click remediation to reverse unauthorized changes across devices, eliminating the need for manual scripts.
- MITRE ATT&CK® integration: Maps telemetry to the MITRE ATT&CK® framework, reducing alert fatigue and streamlining threat hunting and incident response for SOC and IT analysts.
- Rogue device and network control: Enhances security with built-in controls for network, USB, and Bluetooth devices, alongside rogue device identification with Ranger.
Source: SentinelOne
9. Trend Vision One
Trend Vision One is a cloud-native security operations platform that integrates attack surface management (ASM) and XDR into a unified console. Designed to strengthen organizational security across cloud, hybrid, and on-premises environments, it provides threat detection, risk management, and automated response capabilities.
Key features of Trend Vision One:
- Integrated ASM and XDR: Combines attack surface management and extended detection and response in one platform, providing security insights across cloud, hybrid, and on-prem environments.
- Risk-centric approach: Offers predictive risk insights with a focus on attack surface management, providing an at-a-glance view of security posture, vulnerabilities, and remediation recommendations.
- Automated threat remediation: Enables automated response to security risks and threats, minimizing manual intervention and reducing the likelihood of successful attacks.
- Coverage: Delivers coverage for internal and internet-facing attack surfaces, detecting vulnerabilities, misconfigurations, and security gaps.
- Threat detection: Uses machine learning and security analytics to detect threats earlier, reduce false positives, and improve response times.
Source: Trend
10. Sophos Intercept X Endpoint
Sophos Intercept X Endpoint is an endpoint security solution to prevent breaches, ransomware, and data loss through protection mechanisms. It combines EDR and XDR capabilities to detect, investigate, and respond to threats in real time.
Key features of Sophos Intercept X Endpoint:
- Prevention-first security: Uses a multi-layered approach with AI, behavioral analysis, anti-exploitation, and anti-ransomware technologies to block threats before they escalate.
- Ransomware protection: Incorporates CryptoGuard to stop malicious encryption in real time and automatically roll back files affected by ransomware.
- Anti-exploitation capabilities: Adds over 60 exploit mitigations beyond standard Windows protection, stopping fileless attacks and zero-day exploits.
- Adaptive attack protection: Dynamically strengthens endpoint defenses when hands-on-keyboard attacks are detected, minimizing the attack surface.
- Central management: Provides a unified, cloud-based management platform with protection settings enabled by default.
Source: Sophos
Conclusion
Endpoint security is critical for protecting the increasing number of devices connected to organizational networks. By implementing strong endpoint security solutions, organizations can defend against a wide range of threats, including malware, ransomware, and fileless attacks. Effective endpoint security ensures that each device is continuously monitored, analyzed, and protected, offering a proactive defense that mitigates risks across all entry points.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response