In this article
Ransomware Removal: How to Recover Your Files and Systems
Ransomware attacks are one of the most devastating cybersecurity threats facing organizations today. They can lock employees out of your most critical files and systems, demand steep payments, and cause significant long-term operational and reputational damage.
In this guide, we’ll walk you through everything you need to know about ransomware. From spotting the early signs of ransomware, to the steps you should take immediately after an attack, to ransomware removal tools, to your options for safely recovering your data, this guide is a must-read for security professionals.
What is Ransomware?
Ransomware is malware that encrypts user data and makes it inaccessible to the victim. The attacker demands a ransom in exchange for decrypting the data. Payment is typically demanded in cryptocurrency and the costs can range between hundreds and thousands of dollars. Even if the ransom is paid, there is no guarantee that the data will be restored.
Ransomware has become more sophisticated over time, requiring more sophisticated ransomware protection methods. While the original ransomware was limited to encrypting a single endpoint, current variants have advanced distribution mechanisms. Modern ransomware encrypts its own code to make reverse engineering difficult and can use offline encryption methods, eliminating the need for communication with a command and control (C&C) center.
What are the Signs that You are Infected by Ransomware?
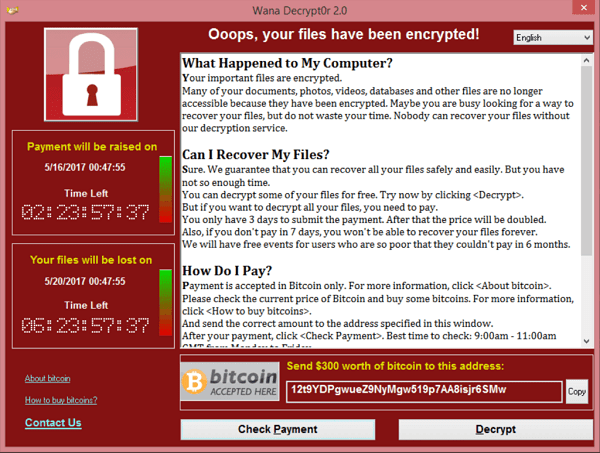
The clearest sign of a ransomware attack is if the system displays a window with a ransom note like the one below. Additional signs include files that are suddenly renamed, encrypted, or locked, or missing files. You might also experience low system performance, disabled security tools, or alerts and communication from programs you didn’t install.
If there is no ransom notice, here a few quick ways to detect if your system is affected by ransomware:
- Scan the system with antivirus – antivirus can detect known types of ransomware unless ransomware has bypassed the antivirus, or the attack is unknown (zero day).
- Check file extensions – your operating system may hide file extensions by default. Show them, and look at your files. If common file extensions like “.docx” or “.png” have changed to random letter combinations, this indicates a ransomware infection.
- Renamed files – if you find files with a different name from the original name you gave them, this can indicate ransomware has encrypted the data.
- Heightened CPU/disk activity – ransomware can cause increased use of system resources. Shut down normal applications and processes and see if utilization is higher than normal.
- Abnormal network communications – most types of ransomware interact with a C&C server, and you can detect this abnormal network traffic using tools like WireShark.
- Encrypted files – finally, if you attempt to open a file and discover that it is encrypted, this is a clear sign of ransomware.
Source: Wikimedia Commons
Ransomware Removal: Immediate Steps
If you’ve been infected by malware, here are some quick steps you can take to remove the malware and prevent further damage:
- Isolate affected systems — immediately disconnect any machines showing signs of infection from wifi and wired networks, to prevent malware from spreading on the network or communicating with command and control systems.
- Identify the infection — you can use a free tool like Cyber Sheriff, provided by Europol and McAfee, to identify the type of malware you are infected with.
- Disable affected accounts and access points – disable user accounts, VPN connections, remote desktop access, and any shared drives that the infected device was using. Malware often uses existing privileges to move laterally inside a network.
- Analyze network traffic – evaluate your firewall, SIEM, or network monitoring tools, and scan for unusual traffic. Look for unauthorized connections, large data transfers, or communication with known malicious IPs and domains.
- Block suspicious IPs, domains, and ports at the firewall or router level.
- Check for lateral movement – review internal network logs, DNS queries, and endpoint detection systems to see if any other machines are showing signs of compromise.
- Patch and harden your network devices – update routers, firewalls, switches and servers with the latest security patches.
- Change all network credentials for routers, switches, Wi-Fi access points, and critical systems.
- Report to the authorities — it is important to report your ransomware attack to the authorities to provide law enforcement agencies with more information about attacks and to help them act against attackers. In the USA you can file a report via the FBI Internet Crime Complaint Center.
- Leverage a specialized Incident Response Service – Incident response services that specialize in investigating and recovering from ransomware attacks can help you hit the ground running. This will allow you to quickly determine how the ransomware infiltrated the organization, find and eliminate all components of the attack, and help you recover your data.
Should You Pay the Ransom?
Most security experts and law enforcement authorities, including the FBI, advise not to pay the ransom in case of a ransomware attack. There are three primary reasons:
- Even if you pay the ransom, there is no guarantee that cybercriminals will decrypt your data
- Some types of ransomware are actually unable to decrypt the data, even if the ransom is paid
- Paying the ransom encourages future ransomware attacks against your organization and others
Tips From Expert
In my experience, here are tips that can help you better protect against, detect, and recover from ransomware attacks:
- Implement advanced endpoint monitoring for early detection
Use Endpoint Detection and Response (EDR) solutions that monitor system behavior for early signs of ransomware, such as sudden file encryption or unusual resource spikes, triggering automated containment measures before the attack spreads. - Monitor for abnormal encryption activity with decoy files
Plant decoy files in strategic locations across the network that ransomware is likely to encrypt first. Monitoring encryption activity on these files gives you early warning of an ongoing ransomware attack. - Use DNS monitoring to detect ransomware communications
Since ransomware often needs to communicate with command-and-control (C&C) servers, monitor Domain Name System (DNS) requests for abnormal activity. DNS filtering can block these connections and prevent key exchanges with attackers. - Apply application whitelisting for critical infrastructure
Implement application whitelisting to ensure that only approved applications can run on critical systems. This makes it more difficult for ransomware to execute, reducing the chance of infection. - Regularly patch systems and applications
Ransomware often exploits unpatched vulnerabilities. Maintain a robust patch management policy to reduce the attack surface, ensuring operating systems, third-party software, and security tools are up to date.
These strategies can greatly improve your organization’s resilience to ransomware and ensure faster detection, containment, and recovery.
What are the Options for Recovering from a Ransomware Attack?
First, identify what type of Ransomware has infected your systems. Here are some of the most common ones:
Screen-locking ransomware
This type of malware locks users out of a computer, sometimes claiming that the computer was locked by the authorities. Another variant is doxware, which threatens to share a user’s public information publicly if a ransom is not paid.
These types of Ransomware are less severe, and you can typically clean them using antivirus software.
Filecoders / encrypting ransomware
This is the more severe type of ransomware that irreversibly encrypts files on a computer. Whether you can remove this type of ransomware depends on the specific malware strain that infected your system.
You typically have three options to recover from an encrypting ransomware attack:
- Decrypt your data — if a decryption tool is available for the ransomware that infected your systems, this is the best option. The No More Ransom Project offers a range of decryption tools that can help you restore access to your files. Unfortunately, not all ransomware encryption algorithms can be decrypted with available tools. These tools also don’t prevent ransomware from activating secondary malware or from deleting data.
- Wipe and restore — with this option, you will lose your encrypted data. Hopefully, you have a backup available from which you can restore your files. If so, you can remove ransomware from your system by simply resetting your device to factory defaults, formatting your hard drives, or deleting your storage instances if in the cloud. Once you have ensured that all data and traces of ransomware are gone, you can restore your systems from backup.
- Negotiate — negotiation is typically a last option for businesses who have no other way of restoring lost access, and is not recommended. However, if you do decide to pay the ransomware, you should know that the ransom fee is typically negotiable. You can negotiate with the attackers using the contact details on the ransomware message. The ransom is typically charged in Bitcoin. Hopefully – although there is no guarantee – after paying the ransom, attackers will allow you to decrypt your files.
How Can You Remove Ransomware from Your Systems?
The steps required to remove filecoders/encrypting ransomware depend on whether you have backed up your files before encryption.
Cleaning Ransomware if You Have Backed Up Your Data
Follow these steps to clean a ransomware infection if you have a safe backup from which you can restore your files.
- Before proceeding, verify that your backup is secure and was not also infected by ransomware.
- Verify that the ransomware malware has been removed – otherwise, it will continue encrypting files after you restore from backup.
- You can use one of these free tools to scan your computer and remove malware: Kaspersky, McAfee, or AVG.
- Recover files from backup.
Cleaning Ransomware if You Do Not Have a Backup
Follow these steps to clean a ransomware infection if you do not have a safe backup of your files, or if backups were corrupted by the ransomware:
- Identify the type of ransomware using Crypto Sheriff from the No More Ransomware project. You will need to provide the email address, Bitcoin account or web address shown in the ransomware message.
- Remove the malware from your system, as explained above.
- Try to decrypt your data. Now that you know what type of ransomware you were infected with, look for a decryptor in the No More Ransomware list of decryptors.
- If you found a decryptor, obtain the key and use it to decrypt the files. This can take some time depending on the type of ransomware, the volume of data and the available system resources.
- If there is no decryptor, contact a security professional and let them try to restore the data.
How Should I Choose a Ransomware Protection Tool?
Having a robust ransomware protection tool in place can help reduce the risk of an attack or the blast radius of one if it occurs. Here’s what to look for when choosing a tool to implement in your systems:
- Advanced Malware Scanning and Detection – The tool should be able to detect both known ransomware strains and zero-day ransomware threats. To do so, it should have the ability to match virus signatures and perform heuristic scanning. For example, the tools should look for unusual encryption behavior or mass file changes and kill the process automatically. This will help prevent ransomware from attacking your systems.
- Quarantine and Containment – Once detected, the tool should isolate suspicious files immediately before they can spread or encrypt more data. It should also automatically block communications with C2 servers, which can be used for issuing additional commands, downloading payloads, or exfiltrating stolen data. This will significantly limit the attack’s ability to escalate, helping contain the threat before it can cause widespread damage or compromise sensitive systems.
- System Rollback and File Recovery – Top-tier ransomware tools can roll back your system or individual files to a pre-infection state. To do so, they rely on features like snapshot technology or continuous backup systems that automatically save clean copies of your files and system configurations. This capability allows you to quickly restore operations without paying the ransom or suffering major downtime, minimizing both financial and operational impact.
- Real-Time Monitoring and Alerts – The tool should alert you the moment suspicious encryption or file manipulation starts. You can decide which action to take depending on the threat. For example, isolating the device, stopping the process, or triggering a broader incident response plan. Fast alerts give you the critical window needed to intervene before ransomware can fully execute its payload and cause irreversible damage.
- Offline and Safe Boot Options – Some ransomware strains will actively block security software when the OS boots up. A solid removal tool should have the option to create bootable recovery media or run in Safe Mode with network isolation. This will allow you to bypass the infected operating system altogether, giving you a clean environment to detect and remove the ransomware before it can defend itself or further damage your system.
- Minimal Performance Impact – Protection tools should run in the background as lightweight processes. If the tool impacts performance too heavily, users may disable or ignore it, leaving systems exposed.
- Post-Incident Forensics and Reporting – After removal, good tools will offer a report on what was affected, how the malware entered, and recommendations to improve future resilience. This helps prevent repeat infections and should also be used for auditing purposes, compliance documentation, and refining your broader cybersecurity strategy over time.
- Updates – Threats evolve fast. Choose a tool from a vendor known for frequent signature updates and patching. This will ensure that your defenses stay effective against the latest ransomware variants, zero-day exploits, and evolving attack tactics.
All-in-One Ransomware Removal and Protection with Cynet
Cynet is an Advanced Threat Detection and Response platform that provides protection against threats, including ransomware, zero-day attacks, advanced persistent threats (APT), and trojans that can evade signature-based security measures.
Cynet provides a multi-layered approach to stop ransomware from executing and encrypting your data:
- Pre-download—applies multiple mechanisms against exploits and fileless malware, which typically serves as a delivery method for the ransomware payload, preventing it from getting to the endpoint in the first place.
- Pre-execution prevention—applies machine-learning-based static analysis to identify ransomware patterns in binary files before they are executed.
- In runtime—employs behavioral analysis to identify ransomware-like behavior, and kill a process if it exhibits such behavior.
- Threat intelligence—uses a live feed comprising over 30 threat intelligence feeds to identify known ransomware.
- Fuzzy detection—employs a fuzzy hashing detection mechanism to detect automated variants of known ransomware.
- Sandbox—runs any loaded file in a sandbox and blocks execution upon identification of ransomware-like behavior.
- Decoy files—plants decoy data files on the hosts and applies a mechanism to ensure these are the first to be encrypted in a case of ransomware. Once Cynet detects that these files are going through encryption it kills the ransomware process.
- Propagation blocking—identifies the networking activity signature generated by hosts when ransomware is auto-propagating, and isolates the hosts from the network.
Learn more about how Cynet can protect your organization against ransomware and other advanced threats.
See Our Additional Guides on Key Data Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of data security.
Incident Response
Authored by Cynet
Object Storage
Authored by Cloudian
- What is Object Storage: Definition, How It Works and Use Cases
- Object Storage vs. File Storage: What’s the Difference?
- Object Storage vs. Block Storage: Head to Head
IoT Security
Authored by Sternum IoT
FAQs
The most obvious sign of a ransomware infection is the sudden appearance of a ransom note demanding payment (often in cryptocurrency) to regain access to your data. There might be more subtle warning signs, like files might suddenly become inaccessible or renamed with strange extensions, system performance might degrade rapidly, or unfamiliar programs might start running in the background.
First, isolate the infected systems immediately. Disconnect them from the network (wired and Wi-Fi) to prevent the ransomware from spreading to other machines or encrypting networked drives. Then, document everything you observe, like ransom notes, filenames, and symptoms. This information can help investigators or IT teams analyze the attack later. If your backups are clean and unaffected, you can start planning a recovery without dealing with the attackers. It’s also important to report the incident to the appropriate authorities.
Preventing ransomware starts with good cyber hygiene. Regularly back up critical data, keep your systems, software, and applications up-to-date with the latest patches, use MFA wherever possible, and limit user access to only what’s necessary for their job roles (the principle of least privilege). In addition, you should deploy endpoint protection tools that include behavior-based detection, monitor network traffic for suspicious activity, and have a solid incident response plan ready.
Anti-ransomware software works by detecting and stopping ransomware before it can encrypt your files. They recognize known strains based on their code and monitor for suspicious activities like mass file encryption, rapid changes to file extensions, unauthorized modifications to backups, or known ransomware behaviors, and immediately stop the offending process.
Free ransomware removal tools can be helpful in some cases, especially for older or well-known ransomware strains. Organizations like the No More Ransom Project provide legitimate free decryptors for certain ransomware types. However, more complex ransomware families require advanced, heuristic analysis to identify and prevent threats.
Even if you manage to delete the malicious files, your system could still be compromised. Ransomware often opens backdoors for future attacks, disables security features, and modifies system files and registries. Without a full system recovery or reinstallation, you could be leaving your environment vulnerable to reinfection or further exploitation.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response



