Last Updated:
April 26, 2025
Incident response is a strategic approach to addressing and managing the aftermath of a cyberattack, also known as a security incident. The goal is to handle the situation in a way that curtails damage, reduces recovery time and costs, and minimizes disruption to the organization. An effective incident response plan can also assist in preventing future incidents by providing insight into the organization’s vulnerabilities and offering a road map for strengthening security measures.
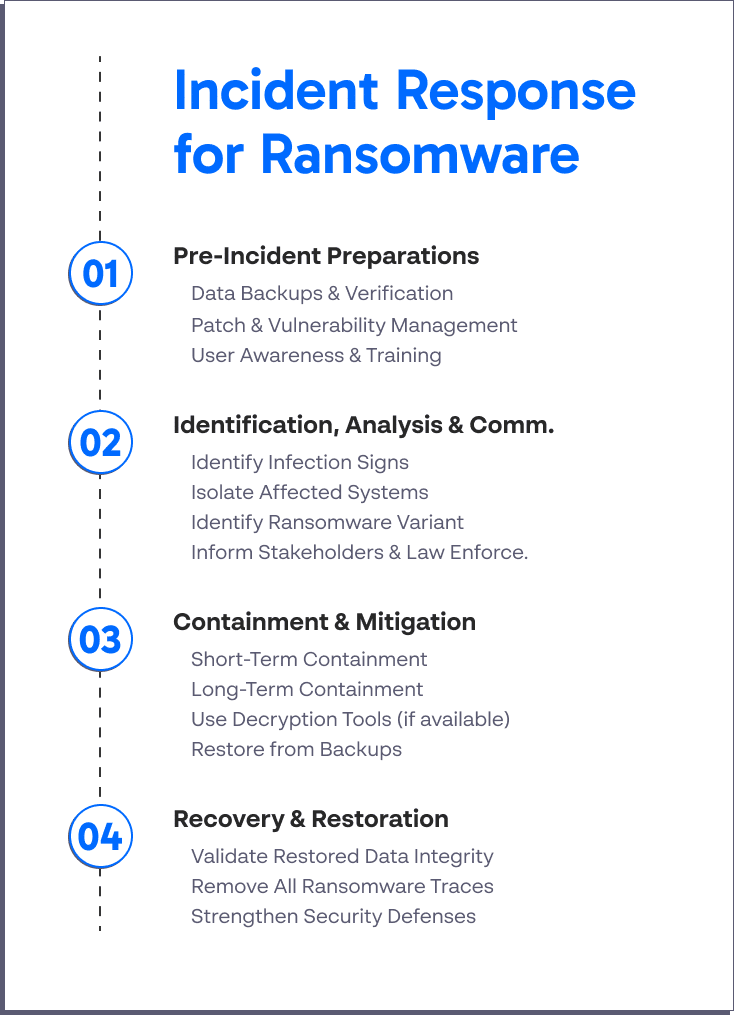
An incident response process can be structured into four key phases:
- Preparation: establishing an incident response team and equipping them with the necessary tools and knowledge.
- Identification: The process of detecting and validating the incident.
- Containment and mitigation: Limiting the scope and magnitude of the incident, and then eliminating the root cause of the incident.
- Recovery: Restoring systems and services to their normal functions, and lessons learned is about reviewing the incident and the organization’s response to it, and making necessary improvements to the incident response plan.
While incident response is relevant to all types of cybersecurity threats, its role becomes even more significant when dealing with ransomware attacks. Ransomware is a type of malicious software that encrypts a victim’s files and demands a ransom to restore access. The following sections will look deeper into the importance of incident response for ransomware and how incident response teams can address ransomware attacks.
The Importance of Incident Response for Ransomware
Ransomware attacks can be devastating, rendering critical data inaccessible and disrupting business operations. An effective incident response plan can help to quickly identify the nature and scope of the attack, isolate affected systems to prevent further spread, and initiate remediation measures to minimize disruption and data loss.
Rapid identification and containment of the ransomware attack are critical to reducing its impact. This requires a skilled incident response team and advanced detection tools that can quickly recognize indicators of compromise. Once the attack is contained, the team can focus on eradicating the ransomware and restoring the affected systems, which is often a complex and time-consuming process.
Stages of a Ransomware Incident Response Plan
Here are the main stages you should include in an incident response plan for ransomware threats.
Pre-Incident Preparations
Regular Data Backups and Verification
One of the most effective proactive measures against ransomware is regular data backups. By ensuring you have a recent backup of your data, you can mitigate the potential loss caused by a ransomware attack. However, simply backing up your data isn’t enough. It’s crucial to regularly verify your backups to ensure they are functional and up to date.
Patch and Vulnerability Management
Another crucial aspect of pre-incident preparations is patch and vulnerability management. Regularly updating and patching your systems can prevent cybercriminals from exploiting known vulnerabilities. Additionally, having a systematic approach to vulnerability management can help you identify potential weak points in your systems before they can be exploited.
User Awareness and Training
User awareness and training play a vital role in your pre-incident preparations. Cybercriminals often exploit human error or negligence to infiltrate systems. By training your users to identify and avoid potential threats, you can significantly reduce the risk of a ransomware attack.
Identification, Analysis, and Communication
Identifying Signs of a Ransomware Infection
The initial stage of dealing with a ransomware attack is detecting the infection. This step can be challenging, as ransomware often disguises itself as legitimate software or files. Some common signs of a ransomware infection include unusual system behavior, such as slow performance, inexplicable data loss, or unexpected system shutdowns.
Isolating Affected Systems to Prevent Spread
Once you’ve detected a potential ransomware infection, the next step is to isolate the affected systems. This step is crucial in preventing the spread of the ransomware to other systems or networks. By isolating the affected systems, you can minimize the potential impact of the attack and buy yourself time to formulate a response.
Identifying the Specific Ransomware Variant
After detecting and isolating a ransomware infection, the next step in your incident response plan is to identify the specific variant of ransomware you’re dealing with. This step is important because different ransomware variants have different behaviors and characteristics, and accordingly, require different response strategies.
For instance, some ransomware variants encrypt data, while others delete it or transmit it to attackers. Understanding these details can help you decide whether to attempt data recovery or focus on preventing further loss or exposure.
If the ransomware variant you’re dealing with encrypts data, another crucial step in your Incident Response plan is to determine the encryption mechanism. This information can aid in the decision-making process, such as whether to attempt decryption or to restore from backup.
Informing Stakeholders
When a ransomware attack is detected, it is critical to inform all relevant stakeholders. This includes management, legal teams, IT staff, and affected users. You need to keep everyone in the loop about what’s happening, what steps are being taken, and what they can do to help. For instance, users might need to change their passwords or avoid certain actions to prevent the spread of the ransomware.
Reporting to Law Enforcement or Regulatory Bodies
After informing internal stakeholders, the next step is to report the incident to the appropriate law enforcement or regulatory bodies. This might include your local police department, a national cybercrime unit, or a data protection authority. These bodies can provide advice and assistance and might be able to track down the perpetrators.
This step is also important for your legal compliance. Certain laws and regulations require businesses to report data breaches within a specific timeframe.
Containment and Mitigation
Short-Term and Long-Term Containment
Containment means preventing the ransomware from spreading further and minimizing its impact on your systems. Short-term containment strategies might involve isolating affected systems, disabling network shares, or blocking certain IP addresses. Long-term strategies could include patching vulnerabilities, enhancing firewall rules, or increasing network monitoring.
Using Decryption Tools If Available
In some cases, it might be possible to decrypt the data that the ransomware has encrypted. This depends on the type of ransomware and whether security researchers have developed a decryption tool for it. If such a tool is available, it can be a valuable part of your containment and mitigation strategy. However, using a decryption tool can be a complex process that requires technical expertise, and it’s not a guaranteed solution.
Restoring from Backups Where Feasible
A crucial aspect of ransomware mitigation is restoring lost data. If you have recent and reliable backups, this can be a lifesaver—you can restore your systems to their pre-attack state and continue your operations with minimal disruption.
However, it’s important that your backups are not infected by the ransomware. You should have a backup strategy that involves regular backup creation, off-site storage, and periodic testing of backup integrity.
Recovery and Restoration
Validating the Integrity of Restored Data
After restoring your data from backups, you need to validate its integrity. This means checking that the data is complete, accurate, and not corrupted. You should also ensure that the restored data doesn’t contain any traces of the ransomware. This might involve running security scans, checking file hashes, or comparing the restored data with original data.
Ensuring All Traces of Ransomware are Removed
Once you’ve restored and validated your data, the next step is to ensure that your systems are thoroughly cleaned of any remnants of the ransomware. This might involve running additional security scans, reformatting hard drives, or reinstalling software. It’s a time-consuming process but it’s essential to prevent the ransomware from reactivating or spreading again.
Strengthening Defenses to Prevent Reinfection
The final stage of the Incident Response process is to strengthen your defenses to prevent a similar attack from happening again. This might involve updating your security policies, training your staff about cyber threats, implementing stronger access controls, or investing in better security tools. Incident response goes beyond reacting to attacks—it involves learning from them to improve your resilience.
In my experience, here are tips that can help you better adapt to incident response specifically for ransomware attacks:
- Develop Ransomware-Specific Playbooks: Create tailored playbooks for different types of ransomware attacks to ensure effective and timely responses.
- Utilize Immutable Backups: Implement immutable backups to protect data integrity and availability in the event of a ransomware attack.
- Leverage Network Segmentation: Segment critical systems and data to limit the spread of ransomware and reduce its impact.
- Prepare for Ransomware Negotiations: Develop protocols for ransomware negotiations, including communication strategies and legal considerations.
- Conduct Regular Testing: Simulate ransomware attacks through red team exercises to test your organization’s response capabilities and identify areas for improvement.
Eyal Gruner is the Co-Founder and Board Director at Cynet. He served as the company’s CEO for nine years, guiding its growth from the very beginning. He is also Co-Founder and former CEO of BugSec, Israel’s leading cyber consultancy, and Versafe, acquired by F5 Networks. Gruner began his career at age 15 by hacking into his bank’s ATM to show the weakness of their security and has been recognized in Google’s security Hall of Fame.
All-in-One Ransomware Protection with Cynet
Cynet is an Advanced Threat Detection and Response platform that provides protection against threats, including ransomware, zero-day attacks, advanced persistent threats (APT), and trojans that can evade signature-based security measures.
Cynet provides a multi-layered approach to stop ransomware from executing and encrypting your data:
- Pre-download—applies multiple mechanisms against exploits and fileless malware, which typically serves as a delivery method for the ransomware payload, preventing it from getting to the endpoint in the first place.
- Pre-execution prevention—applies machine-learning-based static analysis to identify ransomware patterns in binary files before they are executed.
- In runtime—employs behavioral analysis to identify ransomware-like behavior, and kill a process if it exhibits such behavior.
- Threat intelligence—uses a live feed comprising over 30 threat intelligence feeds to identify known ransomware.
- Fuzzy detection—employs a fuzzy hashing detection mechanism to detect automated variants of known ransomware.
- Sandbox—runs any loaded file in a sandbox and blocks execution upon identification of ransomware-like behavior.
- Decoy files—plants decoy data files on the hosts and applies a mechanism to ensure these are the first to be encrypted in a case of ransomware. Once Cynet detects that these files are going through encryption it kills the ransomware process.
- Propagation blocking—identifies the networking activity signature generated by hosts when ransomware is auto-propagating, and isolates the hosts from the network.
Learn more about how Cynet can protect your organization against ransomware and other advanced threats.




