Achieved 100% detection in 2023
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
Cobalt Strike is a tool developed for ethical hackers, but like many other offensive cybersecurity tools, it has fallen into the wrong hands. This powerful network attack platform combines social engineering, unauthorized access tools, network pattern obfuscation and a sophisticated mechanism for deploying malicious executable code on compromised systems. It can now be used by attackers to deploy advanced persistent threat (APT) attacks against your organization.
Compromised by Cobalt Strike?
Cynet is a trusted partner that deploys powerful endpoint detection and response (EDR) security software on your endpoints, combined with advanced network analytics and behavioral analysis. It can help defend, mitigate and eradicate against a wide range of known and zero-day threats, including the Cobalt Strike platform.
Cynet provides CyOps, an outsourced incident response team on call 24/7/365 to respond to critical incidents quickly and effectively.
Cobalt Strike is a commercial penetration testing tool, which gives security testers access to a large variety of attack capabilities. Cobalt Strike can be used to conduct spear-phishing and gain unauthorized access to systems, and can emulate a variety of malware and other advanced threat tactics.
White Cobalt Strike is a legitimate tool used by ethical hackers, which carries a price tag of $3,500 per user, it is also widely used by threat actors to launch real attacks against organizations. Some attackers obtain the trial version of Cobalt Strike and crack its software protection, while others may obtain access to a commercial copy of the software.
Cobalt Strike’s main use is for penetration testing and threat emulation. Penetration testing involves simulating attacks on a network or system to identify vulnerabilities that could be exploited by real attackers.
By emulating advanced threat actors, Cobalt Strike allows security professionals to understand the tactics, techniques, and procedures (TTPs) used by these actors. This understanding can then be used to develop effective countermeasures and enhance the overall security posture of the system or network.
Cobalt Strike’s comprehensive toolkit can execute all stages of the attack kill chain, including reconnaissance, exploitation, post-exploitation, and command and control (C2) operations.
Cobalt Strike is a threat emulation program that provides the following capabilities:
Cobalt Strike comprises several modules and components, each designed to perform specific tasks within a cyber attack or penetration test. Let’s delve into some of these main components.
Beacon is Cobalt Strike’s payload for command and control. It’s a lightweight backdoor that allows the operator to control a compromised system remotely. Beacon is designed to be stealthy, with low network indicators and flexible communication options, making it hard to detect.
Beacon’s capabilities include executing commands, uploading and downloading files, and spawning processes. It also provides a range of in-memory post-exploitation capabilities, enhancing its stealth and persistence on the compromised system.
The Empire payload is a PowerShell-based post-exploitation agent derived from the Empire project, a popular open-source post-exploitation framework.
The Empire payload provides several capabilities, including in-memory execution, a wide range of post-exploitation modules, and integration with various tools and frameworks. It allows the operator to perform activities like lateral movement, privilege escalation, and persistence.
The Web Drive-By module in Cobalt Strike is designed for delivering exploits through web-based vectors. This module allows the operator to host exploit-laden web pages that can compromise the systems of unsuspecting users.
The Web Drive-By module supports an array of exploit techniques, including Java applet attacks and HTA attacks. It also provides advanced options for customizing exploit delivery.
The Malleable C2 module allows the operator to customize the C2 communication, making it harder for defenders to detect the C2 traffic.
With the Malleable C2 module, the operator can modify network indicators, including the request and response formats, URI structure, and session data. This makes C2 communication blend in with the regular network traffic, enhancing the stealth of the operation.
The External C2 module allows Cobalt Strike to integrate with other tools and frameworks. It provides an API that other tools can use to communicate with the Cobalt Strike server. By integrating Cobalt Strike with other offensive tools, penetration testers or attackers can expand its operational scope.
In the hands of a malicious attacker, Cobalt Strike can pose a significant risk to any organization. The platform’s ability to mimic genuine network traffic makes it incredibly difficult to detect, allowing hackers to remain undetected within a network for extended periods. This stealthy nature, combined with its advanced post-exploitation capabilities, makes Cobalt Strike a formidable tool in the hands of cybercriminals.
Cobalt Strike’s ‘Beacon’ payload is a particularly dangerous aspect of the tool. Once deployed, it allows attackers to maintain a discreet presence within a network, carrying out operations while remaining largely invisible to security systems. This facilitates long-term data theft, manipulation, and disruption of network operations.
Moreover, Cobalt Strike is frequently used in tandem with other hacking tools and methods, multiplying its threat potential. For instance, it can be combined with the services of initial access brokers (IAB), cybercriminals who specialize in breaching a network’s perimeter. An advanced threat actor can use an IAB to gain access to a network and then use Cobalt Strike for lateral movement and data exfiltration.
Cobalt Strike servers can be difficult to detect, but older unpatched versions of the software are more visible. You can combine several techniques to identify a Cobalt Strike deployment:
Defending against a Cobalt Strike attack requires a multi-pronged strategy. The tool’s versatility means that it can exploit a wide range of vulnerabilities and use various attack vectors. Therefore, a single defense mechanism is typically not enough. Here are some strategies you can implement.
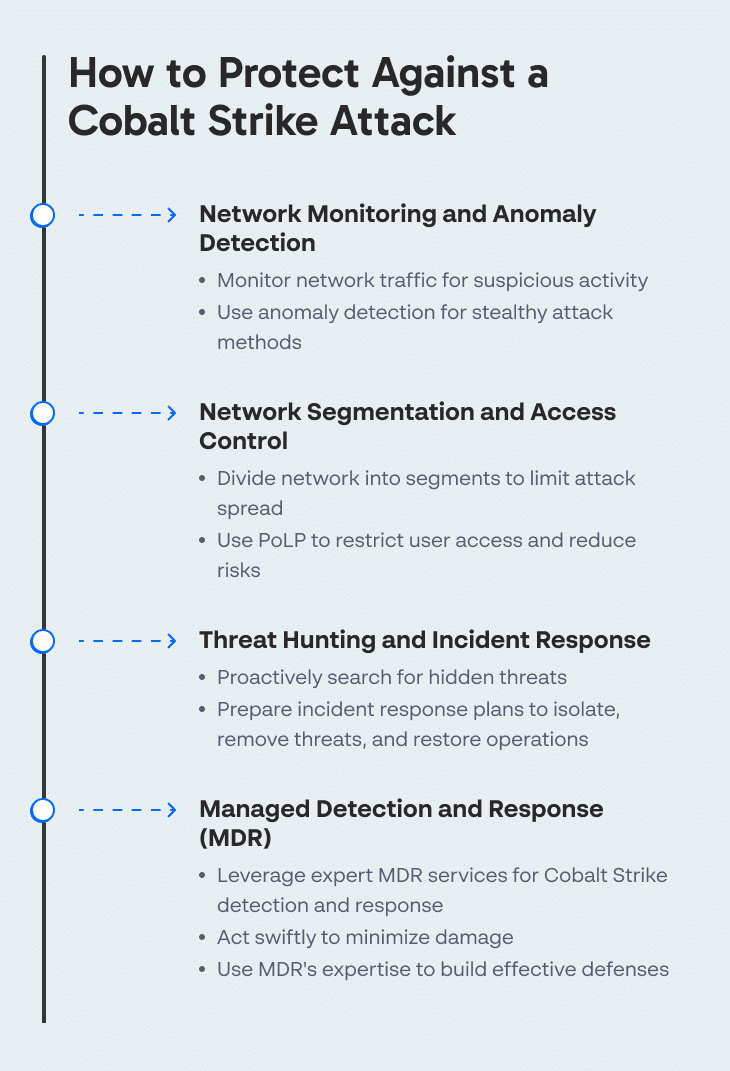
Network monitoring and anomaly detection can provide an early warning of a Cobalt Strike attack. Network monitoring involves keeping a close eye on your network traffic to identify any unusual or suspicious activity (specifically the ports and network patterns listed above). This can help you detect a Cobalt Strike attack in its early stages, before it has had a chance to cause significant damage.
Anomaly detection is a more advanced form of network monitoring. Instead of merely looking for known threats, anomaly detection looks for deviations from normal behavior. This can be useful in detecting Cobalt Strike attacks, as the tool often uses stealthy techniques that may not trigger traditional security alerts.
Network segmentation is another effective defense against Cobalt Strike. By dividing your network into separate segments, you can limit the spread of an attack. If one segment is compromised, the attacker will not be able to easily move to other parts of the network. This can buy you crucial time to detect and respond to the attack.
Access control is the other half of this strategy. By strictly controlling who has access to what, you can reduce the chances of an attacker gaining a foothold in your network. This means implementing a principle of least privilege (PoLP), where users are only granted the minimum privileges necessary to perform their tasks.
Threat hunting involves proactively searching for threats that may have evaded your existing security measures. Given Cobalt Strike’s advanced capabilities, it’s possible for this tool to bypass some defenses. Therefore, regular threat hunting can help you identify any signs of a Cobalt Strike attack.
Incident response is about dealing with an attack once it’s detected. A well-prepared incident response plan can significantly reduce the damage caused by a Cobalt Strike attack. This plan should outline the steps to be taken following a security incident, including how to isolate affected systems, how to remove the threat, and how to restore normal operations.
Managed Detection and Response (MDR) is a proactive approach that combines technology with human expertise. This service goes beyond traditional security measures by actively hunting for threats, managing incidents, and providing rapid response to security events. When dealing with Cobalt Strike, MDR can offer several advantages.
An MDR service can identify the signs of a Cobalt Strike attack, based on the tool’s known characteristics and behaviors. Once detected, an MDR service can provide a swift response to mitigate the damage. Swift action is critical in the face of a Cobalt Strike attack, as the tool can quickly move laterally across a network and escalate privileges.
Lastly, an MDR service can offer expert advice and guidance. Defending against Cobalt Strike requires a deep understanding of the tool and its tactics, techniques, and procedures (TTPs). An MDR provider can bring this expertise to the table, helping you to devise an effective defense strategy.
Cynet 360 is a holistic security solution that can protect against the large variety of threat vectors and attack techniques provided by Cobalt Strike software.
Learn more about Cynet 360.
Search results for: