In this article
6 Ransomware Protection Strategies You Must Know

Ransomware attacks are no longer a matter of “if,” but “when.” And as attackers grow more sophisticated, traditional antivirus tools alone are no longer enough. This guide breaks down six essential ransomware protection strategies every organization should implement today. Whether you’re a small business or a global enterprise, these strategies offer a layered defense to detect, prevent, and respond to ransomware before it causes serious damage. Let’s dive in.
What is Ransomware Protection?
Ransomware protection includes technologies, strategies, and tools that can prevent cybercriminals from performing successful ransomware attacks. This includes proactive security measures, backup and recovery strategies, and technological platforms that can detect and block ransomware.
Sufficient ransomware protection starts with implementing basic security best practices such as strong authentication, malware protection, and network security measures. Organizations can build on this strong security posture by adding dedicated solutions to deter, prevent, and recover from ransomware attacks.
There are three types of solutions that can help protect against ransomware:
- Dedicated anti-ransomware solutions – several ransomware protection products are available, which can protect organizations at the network, file system, and application layer. These tools provide a multi-layered approach to stop ransomware from encrypting data.
- Operating system protections – some operating systems provide built-in protection against Ransomware. Most notably, from Windows 10, Microsoft provides ransomware protection built into the Windows Security command center.
- Decryptors – if you have already been hit by a ransomware attack, and there are no backups, it might still be possible to recover the files. Decryptors are available for some ransomware strains, and if you’re lucky, they might succeed in recovering your data.
Learn more in our detailed guide to ransomware prevention.
Learn more in our detailed guide to anti ransomware.
How Does a Ransomware Attack Work?
Image source: Wikimedia Commons
A ransomware infection usually occurs in two phases:
- Ransomware encrypts files or locks the device—encryption involves scrambling files or a file structure until the data is no longer usable. Most ransomware programs use data encryption methods that victims cannot reverse without using a unique decryption key. This method enables attackers to demand ransom in exchange for a key.
- A ransom note appears on the screen—once the ransomware encrypts the files. A note appears to specify a ransom demand, explaining the sum, mode of transfer, and deadline. Usually, attackers threaten that if victims do not meet the deadline, they will either increase the ransom, delete the files, or prevent any future attempt to decrypt them.
As long as the device is infected with ransomware, attempts to open the encrypted files might result in an error message informing you that the files are invalid, corrupt, or cannot be located.
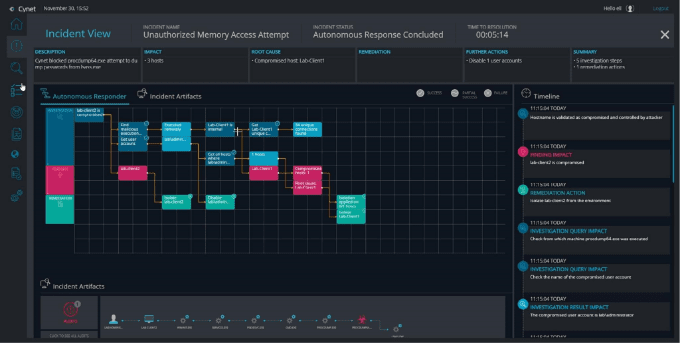
Dedicated Ransomware Protection Solutions
Dedicated Ransomware Protection Solutions
A dedicated security tool can provide holistic protection against ransomware, both at the network, file system, and application layer. One such solution is Cynet All-in-One, an advanced threat detection and response platform that provides protection against threats, including ransomware, zero-day attacks, advanced persistent threats (APT), and trojans that can evade signature-based security measures.
Cynet provides a multi-layered approach to stop ransomware from executing and encrypting your data:
- Pre-download—applies multiple mechanisms against exploits and fileless malware, which typically serves as a delivery method for the ransomware payload, preventing it from getting to the endpoint in the first place.
- Pre-execution prevention—applies machine-learning-based static analysis to identify ransomware patterns in binary files before they are executed.
- In runtime—employs behavioral analysis to identify ransomware-like behavior, and kills a process if it exhibits such behavior.
- Threat intelligence—uses a live feed comprising over 30 threat intelligence feeds to identify known ransomware.
- Fuzzy detection—employs a fuzzy hashing detection mechanism to detect automated variants of known ransomware.
- Sandbox—runs any loaded file in a sandbox and blocks execution upon identification of ransomware-like behavior.
- Decoy files—plants decoy data files on the hosts and applies a mechanism to ensure these are the first to be encrypted in the case of ransomware. Once Cynet detects that these files are going through encryption, it kills the ransomware process.
- Propagation blocking—identifies the networking activity signature generated by hosts when ransomware is auto-propagating, and isolates the hosts from the network.
Cynet All-in-One provides all these anti-ransomware capabilities and more.
Learn how Cynet can protect your organization against ransomware and other advanced threats
Windows 10 Ransomware Protection
The Windows operating system now has built-in ransomware protection as part of Windows Security. This was introduced by Microsoft in Windows 10.
Windows 10 ransomware protection works by only allowing approved applications to make changes to the file system. This can prevent ransomware from encrypting files, but can also interfere with the operation of legitimate applications.
This is why ransomware protection is not enabled by default. To use it, you’ll need to enable it and configure it properly so that existing applications can continue functioning.
To enable Windows 10 ransomware protection:
- Search for Windows Security in the Windows Start menu.
- In the Windows Security sidebar, select Virus & threat protection and click Manage ransomware protection.
- Switch the option Controlled folder access to On. This ensures only applications in the Windows Security allowlist can make changes to files on the operating system.
Decryptors
If a computing system is already infected by ransomware, files have been encrypted, and there are no backups, a last resort is to use decryptors.
There are a range of free decryption tools that are able to reverse the encryption by some types of ransomware. Be sure to use a legitimate descriptor from a source like the No More Ransom Project.
If there is a working decryptor for your ransomware, run it, obtain the key, and use it to decrypt the files. Note that depending on the type of ransomware and available system resources, this can take several hours.
A few important notes about using decryptors:
- Identify ransomware type – before using a decryptor, identify the type of ransomware using Crypto Sheriff. You will need to provide the email address, Bitcoin account or web address shown in the ransomware message.
- Many ransomware types have no decryptor – in many cases there will be no working decryptor for the ransomware strain. In this case, consult with a security professional to see if there are additional ways to restore the files.
- Decryptors do not remove the ransomware – note that decryptors are not enough to clean a ransomware attack from your systems. Ransomware can activate secondary malware or delete your data. Make sure your system is clean from ransomware and all malware before using the decryptor.
What Should You Look for in a Ransomware Protection Solution?
An effective ransomware protection solution can detect, contain, and respond to ransomware threats in real time. Here’s what to look for:
-
- Behavior-Based Detection – Signature-based detection cannot deal with zero-days or identify threats based on pre-attack indicators. A strong solution should use AI/ML to spot suspicious behaviors (like mass encryption or privilege escalation) before the payload detonates.
- Endpoint Detection & Response – EDR or XDR capabilities will provide visibility across endpoints, the network, the cloud, etc. This will allow you to track how ransomware entered, what it touched, and how to isolate the threat.
- Real-Time Prevention & Isolation – The tool should be able to prevent execution of malicious code in real time and isolate infected devices from the network to stop lateral movement. The sooner the incident is contained, the less operational impact it will have.
- Ransomware Rollback or File Recovery – Good solutions offer rollback features that can restore files to pre-attack versions. This allows you to eradicate the ransomware completely or gain access to your important data so you don’t have to pay the ransom. Just be sure to mitigate the exploit the ransomware came through, otherwise you might get attacked again!
- Threat Intelligence Integration – Up-to-date threat intel helps you stay protected against new ransomware variants. It also enables better detection and faster response by correlating indicators of compromise (IOCs) with real-world threats.
- Anti-Phishing and Email Protection – Many ransomware attacks begin with phishing. Choose a solution that integrates email security or partners with your email platform to scan attachments, links, and sender behavior.
- Zero Trust and Access Controls – Built-in zero trust enforcement, based on the principle of least privilege and Just-in-Time (JIT) access, minimizes what ransomware can access if it gets in.
- Incident Response – Clear alerts, automated playbooks, and fast SLAs make a big difference during an attack. The faster your team can respond, the less damage ransomware can do.
- MDR – If you don’t have a large internal team, consider solutions with MDR services that can monitor and act on alerts 24/7. This will help contain the attack quickly.
How Big Is the Ransomware Threat?
Ransomware is a global menace, threatening organizations of all sizes and growing in scope and severity. Here are a few statistics that show the magnitude of the threat:
- How many are affected – according to a recent IDC report, 37% of organizations worldwide were the victim of a ransomware attack.
- Critical sectors targeted – The US Cybersecurity and Infrastructure Security Agency (CISA) reported there were ransomware attacks against 14 of 16 critical infrastructure sectors in the US
- Financial losses – according to Cybersecurity Ventures, ransomware-related costs are expected to reach $57 billion in 2025, and this figure is expected to soar to $275 billion annually by 2031.
- Government involvement – Gartner predicts that by 2025, 30% of governments worldwide will have rules or regulations governing ransomware payments.
Tips From Expert
In my experience, here are tips that can help you better enhance ransomware protection in your organization:
- Deploy application whitelisting for critical systems
Instead of relying solely on antivirus solutions, implement application whitelisting to allow only trusted software to run on critical systems. This prevents unauthorized software, like ransomware, from executing. - Implement endpoint isolation features
Choose EDR or MDR solutions that allow for automatic or manual isolation of endpoints during an attack. This feature quickly disconnects infected systems from the network, minimizing ransomware propagation. - Use canary files to detect ransomware early
Place decoy (canary) files across your network that serve no business function. If these files are accessed or encrypted, it could indicate the presence of ransomware, triggering an immediate response. - Implement file integrity monitoring
Continuously monitor files for unauthorized changes or deletions. Any unexpected alterations in sensitive files may signal the early stages of a ransomware attack, allowing you to respond before more damage is done. - Develop a ransomware-specific incident response (IR) playbook
Create an IR playbook tailored specifically for ransomware attacks. It should include steps like identifying ransomware strains, disconnecting affected systems, and determining recovery paths, such as decryptors or clean backups.
These tips can help you deploy a proactive, layered defense against ransomware, ensuring quicker detection, containment, and recovery from potential attacks.
What are the Most Dangerous Types of Ransomware?
Ryuk
Ryuk ransomware targets large, public-entity Windows systems. It works by encrypting data on an infected system and demanding ransom in Bitcoin. This ransomware appeared in 2018, initially believed to be of North Korean origin, but it is now suspected to be used by Russian criminal groups targeting organizations.
Learn more in our detailed guide to kaseya supply chain attack.
Sodinokibi
REvil/Sodinokibi ransomware encrypts files upon deployment and deletes the ransom request message after infection. The message demands bitcoin, notifying the victim that the demand will double if they do not pay the ransom on time.
REvil is delivered as Ransomware as a Service (RaaS), a model in which code authors develop the ransomware and affiliates spread it to collect the ransom. It was discovered in 2019 and has since become the 4th most distributed ransomware globally, targeting mostly European and American companies.
Netwalker
Netwalker ransomware holds its victim’s data hostage and leaks a sample of the stolen data online, threatening to release all the data to the dark web if the victim does not pay the ransom on time. It was created in 2019 by Circus Spider, a cybercrime group, and later shifted to a RaaS model to operate on a larger scale. It often spreads through phishing emails.
Learn more in our detailed guide to netwalker.
Maze
Maze is a Windows ransomware developed as a variant of ChaCha ransomware. It targets organizations worldwide, demanding a cryptocurrency payment in exchange for the encrypted data, threatening to leak the victim’s confidential data if they refuse to pay.
Maze was discovered in 2019. It is usually distributed through:
- Spam emails, typically through malicious links or attachments like Word or Excel files.
- RDP brute force attacks.
- An exploit kit.
- Through the victim’s client or partner who has already fallen victim to the attack.
Learn more in our detailed guide to maze ransomware.
CryptoWall
CryptoWall ransomware encrypts files and their names and demands a ransom for a decryption key. It typically spreads by phishing and spam emails, hacked websites, malicious ads, or other malware. Cryptowall uses a Trojan horse to deliver malicious payloads. By encrypting file names, CryptoWall increases the pressure on victims, who consequently pay the ransom to get their data back.
Learn more in our detailed guide to wastedlocker.
Locky
Locky ransomware encrypts important files on an infected computer, holding them hostage, delivering a ransom note that demands payment in exchange for the encrypted files. It typically arrived as an email including a Word doc attachment containing the code. Locky was discovered in 2016 and became a significant threat. While Locky is currently out of commission, other variants have emerged.
Learn more in our detailed guide to ragnar locker.
Cerber
Cerber is delivered as RaaS providing attacker licenses that split the ransom between the developer and affiliates. Cerber affiliates can deliver Cerber ransomware to various targets in return for providing the author with 40% of the ransom. The author creates the ransomware in this exchange, and affiliates find targets to distribute it.
Learn more in our detailed guide to lockbit ransomware analysis.
10 Ransomware Protection and Prevention Tips
Here are several ways you can prevent ransomware from striking your organization.
- Actively manage access – restrict access to known users and known legitimate traffic to safeguard your data and applications from encryption. Strong passwords and multi-factor authentication provide added security to prevent bad actors from accessing your systems.
- Centralized management – to deal with the complete range of ransomware threats, organizations must use centralized management procedures and systems. Sensitive information should be categorized, assessed, and properly secured wherever it resides.
- Use anti-malware solutions – block suspicious executable files, and leverage email security solutions to monitor email traffic for malicious messages and block phishing attacks. To address unknown and zero-day malware, including zero-day ransomware, use advanced security technology such as signatureless behavioral analysis.
- Implement centralized patch management – patch all endpoints when vulnerabilities are identified, including operating systems, mobile devices, applications, cloud resources, software, and IoT.
- Protect backup repositories – implement the 3-2-1 rule by keeping three copies of your information, storing it on two distinct media types, and keeping one of these media off-site. It is also important to periodically test backups to ensure they are functional and maintain data integrity.
- Regularly change network credentials for routers, switches, Wi-Fi access points, and critical systems. This helps prevent exploitation due to poor password hygiene.
- Educate users – Help your end users by providing them with the practice and education they need to protect against ransomware attacks. Consistent communication and awareness training will let everyone in your organization know the threat of ransomware and gain familiarity with security approaches. Ensure that your employees know how to report suspicious behavior and understand the importance of timely reporting.
- Establish a disaster recovery plan – to ensure they can completely recover data and applications in case of disaster, organizations must create, test, and uphold practices, tools, and procedures for business continuity and disaster recovery (BCDR).
- Conduct a risk assessment – categorize types of ransomware disasters and create priorities for business continuity and recovery.
- Create an incident response plan – the plan should clarify what to do in the case of a ransomware attack, including determining data sensitivity and disconnecting affected systems from the network to contain the attack.
Related content: Read our guide to linux ransomware.
Learn More About Ransomware Protection
Ransomware Removal: Recovering Your Files and Cleaning Up Infected Systems
Ransomware Prevention: 4-Step Plan to Stop Ransomware Attacks in their Tracks
FTCode Ransomware: Distribution, Anatomy and Protection
Ransomware Detection: Common Signs and 3 Detection Techniques
FAQs
Take a multi-layered security approach that includes both technical and human-centric defenses. This means deploying endpoint protection solutions, keeping systems patched, enforcing strong access controls and backing up data regularly, and segmenting your network. At the same time, educate employees about phishing, social engineering, and suspicious file attachments, since these are among the most common ransomware entry points.
Start with the basics: keep all operating systems, applications, and firmware up to date. Use next-gen antivirus or EDR tools that use behavioral analytics and AI to spot early signs of compromise. Enable MFA wherever possible, especially for privileged accounts and remote access. Beyond tools, implement strong user access policies, routinely audit permissions and external connections, and practice the principle of least privilege. Combine these with a robust employee security awareness training program to help spot phishing attempts, which is the #1 cause of ransomware infections.
Time is critical. First, isolate infected systems to prevent the ransomware from spreading further. Disconnect them from the network immediately. Then, assess the scope of the damage and notify your incident response team or managed security provider. Avoid deleting files or rebooting machines, as this may trigger further encryption or data loss and is important for forensic analysis. Once containment is achieved, initiate your incident response plan. Report the incident to relevant authorities and consult with legal and compliance advisors, especially if customer or sensitive data is involved. Finally, begin recovery using clean backups and conduct a root cause analysis to prevent recurrence.
Modern ransomware protection solutions use a combination of signature-based detection, machine learning, behavior analysis, and threat intelligence feeds. These tools analyze file behavior in real time, looking for suspicious actions such as mass file encryption, unusual file renaming, or attempts to disable security software. Some solutions, like XDR platforms, go further by correlating signals across endpoints, network traffic, and user activity to detect complex, stealthy ransomware attacks. Once detected, they can automatically isolate affected endpoints, block malicious processes, and alert security teams for immediate response.
Organizations should test their ransomware recovery plans at least once a quarter, though high-risk industries may benefit from monthly or bi-monthly drills. In addition, it’s recommended to update the playbook and test your drills every time a major change occurs in the organization, whether a re-org, an M&A, an important release, etc.
Regular software updates patch known vulnerabilities that ransomware actors often exploit. Delaying updates creates a window of opportunity for attackers.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response