Achieved 100% protection in 2024
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
Written by: Eran Yosef, Ben Gold, and Asher Davitadi
In late 2019, the hacker group TA-2101 had used Fallout and Spelevo exploit kits to distribute multiple malwares. The group used emails to target health care related environments around the US. The Maze Ransomware (also known as ChaCha Ransomware) uses RSA and ChaCha20 ciphers for its encryption process and is used was by the attackers to extort the victims for payment, communicating via email – the ransomware generates different payment amounts depending on what the endpoints was used for (home computer, server, or workstation.)
Cynet 360 detects the ransomware in multiple stages of the attack. The detection includes Maze’s binary being dumped on the disk, SSDeep similarity, execution of the ransomware on an endpoint and using Cynet’s heuristic detection to seek file renames and more.
This is part of an extensive series of guides about Ransomware Protection
Cynet 360 protects your environment against this type of attack. This type of attack is detected by Cynet on our protected environment alerting for malicious activities, using the following mechanisms.
Note that the action set for our environment is to alert only, to not interrupt the ransomwares flow, allowing Cynet to detect every step of Mazes Ransomware attack flow.
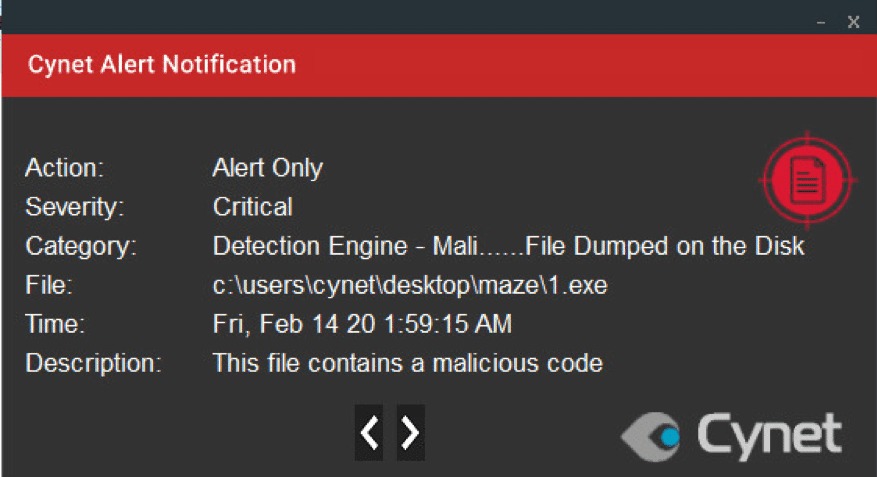
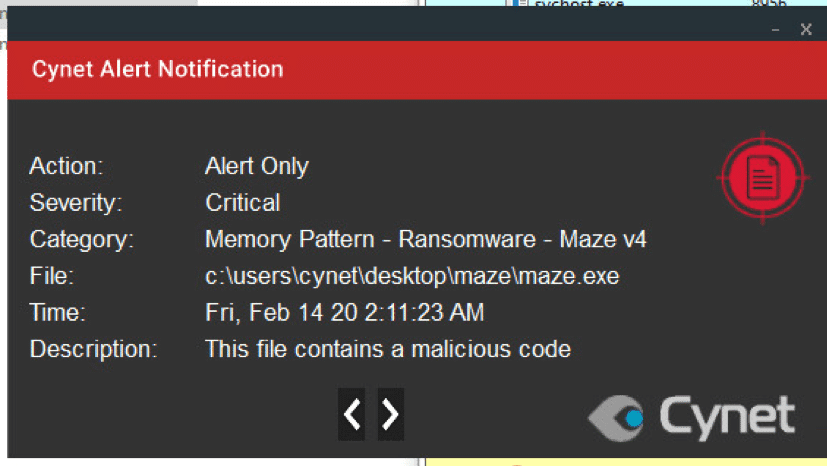
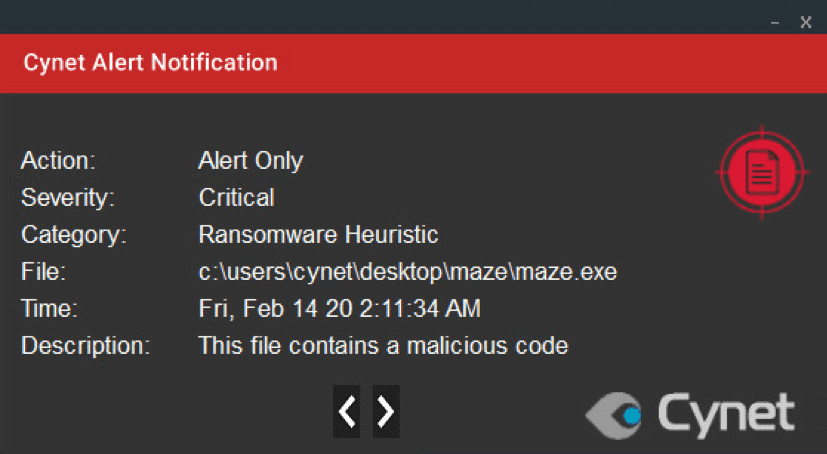
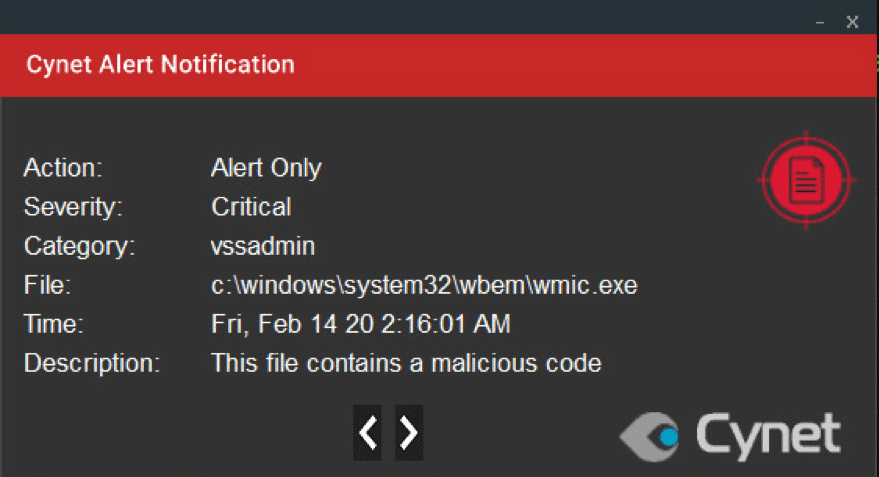
After execution, Maze ransomware renames the encrypts file with a random extension for each file:
Once a computer’s files have been encrypted and renamed, it changes the computer’s background and creates a ransom note at several directories – the ransom notes are named DECRYPT-FILES.html.
The note itself contains an email address to contact the cybercriminals who will provide a decryption tool once the victim sends them the Base64 code which also contains details of the infected host.
The Cynet CyOps team is available to clients 24/7 for assistance with any issues, questions, or comments related to Cynet 360. For additional information, you may contact us directly at:
Phone (US): +1-347-474-0048
Phone (EU): +44-203-290-9051
Phone (IL): +972-72-336-9736
CyOps Email: [email protected]
Search results for: