Achieved 100% protection in 2024
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
Written by: Eran Yosef
njRAT is a variant of jRAT, which is also called Bladabindi; it is a remote access trojan used to control infected machines remotely. Because of its availability and its techniques, njRAT is one of the most widely used RATs in the world – first detected in 2013.
The njRAT trojan is built on the .NET framework. This RAT gives hackers the ability to control the victim’s PC remotely. njRAT allows attackers to activate the webcam, log keystrokes, and steal passwords from web browsers.
Also, Bladabindi gives hackers access to the command line on the infected machine. It allows the malicious actor to kill processes as well as remotely execute and manipulate files. On top of that, njRAT is capable of manipulating the system registry. When a PC is infected, Bladabindi Trojan will collect several bits of information about the PC that it got into, including the name of the computer, operating system number, country of the computer, usernames, and OS version.
Moreover, Bladabindi can target cryptocurrency wallet applications and steal cryptocurrency from PCs. For example, it can grab a bitcoin wallet and access credit card information, which is usually stored in cryptocurrency apps as a way to purchase cryptocurrency.
After infecting a computer, the malware copies into “TEMP,” “APPDATA,” “USERPROFILE.”
It can also copy itself into .exe files, to ensure that it will be activated every time the victim switches on their computer.
The njRAT trojan has a few tricks up its sleeve to avoid detection by antivirus softwares. For example, it uses multiple .NET obfuscators to obstruct its code. Another technique that this malware uses is disguising itself into a critical process, blocking the user’s ability to shut it down, making njRAT hard to remove from infected PCs. Bladabindi RAT can also deactivate processes that belong to antivirus softwares, allowing it to stay hidden. njRAT also knows how to detect if it is running on a virtual machine, which helps the attackers to set up countermeasures against researchers.
For spreading, njRAT can detect external hard drives connected via USB. Once such a device is detected, the RAT will copy itself onto the connected drive and create a shortcut.
This is part of an extensive series of guides about Malware Protection
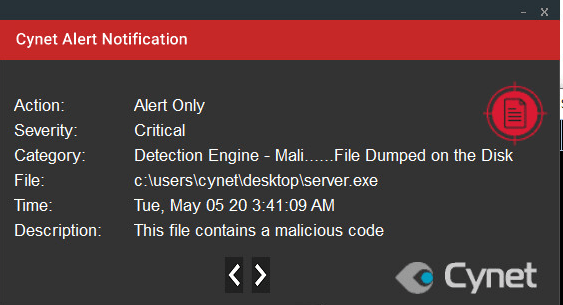
Anti-Virus/AI Mechanism – Detection Wngine
The “Detection Engine” alerts refer to any alert generated by Cynet’s Next-Gen Antivirus or by Cynet’s machine learning mechanism.
This alert triggers when Cynet’s AV/AI engine detects a malicious file that was dumped on the disk.
The alert triggers when Cynet’s AV/AI engine detects a malicious file that was loaded to the memory.
Threat Intelligence Detection – Malicious Binary – Blacklist – Fast Scan Mechanism
This type of alert is based on the Cynet’s threat intelligence database, which contains millions of IoCs. The feed of our threat intelligence database includes third-party information (such as VirusTotal) as well as information derived from attack investigations and pre-defined suspicious patterns and auto-analysis of large, intricate patterns. This alert triggers when Cynet detects a file that is flagged as malicious in Cynet’s internal threat intelligence database.
Malicious Binary – ADT Mechanism
This alert triggers when Cynet detects a file that is flagged as malicious in Cynet’s EPS (endpoint scanner) built-in threat intelligence database. This database contains only critical IoCs (such as IOCs of ransomware, hacking tools, etc.).
Once we first open njRAt, it asks us to choose the port we want the software to listen to. [We selected 4444]
After this, we need to build our “server” file.
We created a .exe file that will open a remote connection to the victim’s machine.
Choose the following:
HKEY_CURRENT_USER\Software\32 characters and digits, you can be sure that is njRAT.
As you’ve entered all the information you want, hit the “build” button, and it creates the .exe file.
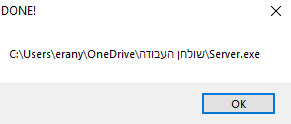
Now, we need to deliver the server file to our victim.
The njRAT trojan uses quite a few attack vectors to infect its victims. For example, the malware is known to target Discord users as part of spam campaigns. Another method is through a compromised website that tricks users into downloading a fake software product update, which in turn installs the njRAT malware to the PC.
Once we deliver njRAT to our victim, and it infected the target device, the malware starts its malicious activity.
A note will pop up in the victim machine and then all the options we will be available to us.
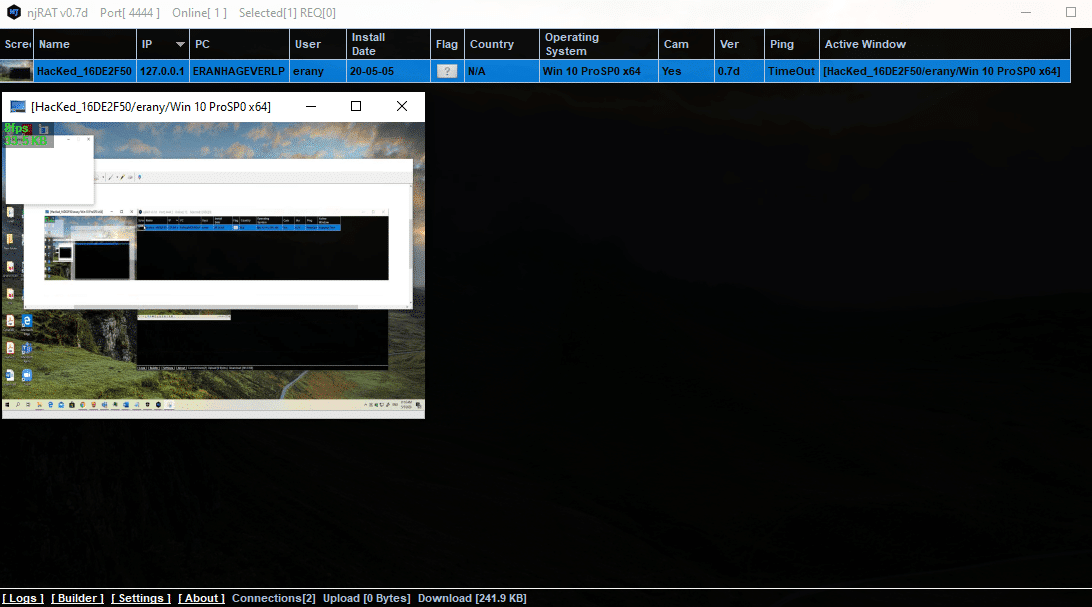
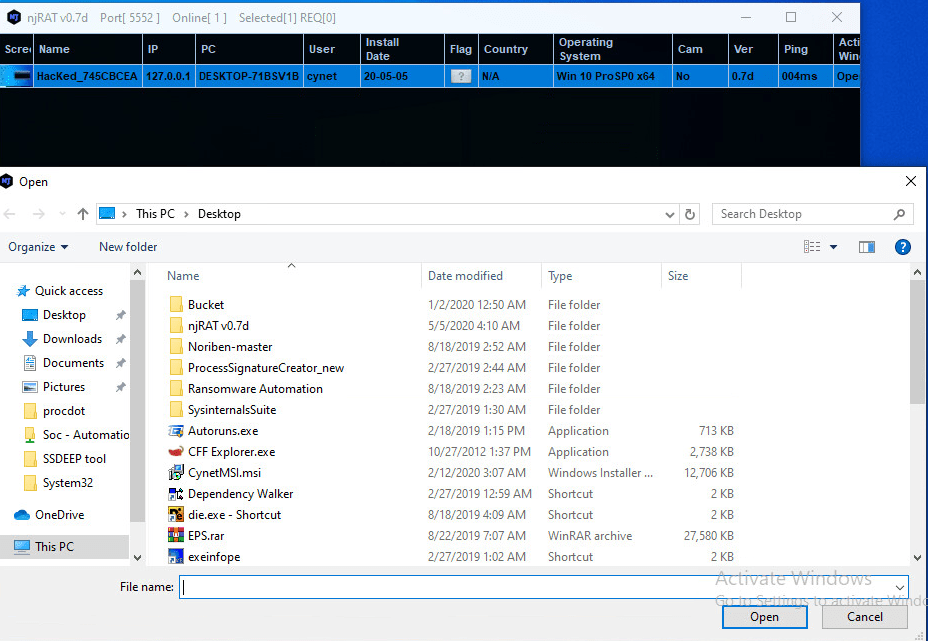
There are a few more options like:
“njRAT is a remote access tool (RAT) that was first observed in 2012. It has been used by threat actors in the Middle East.”
Application Window Discovery
njRAT gathers information about opened windows during the initial infection.
Command-Line Interface
njRAT can launch a command shell interface for executing commands.
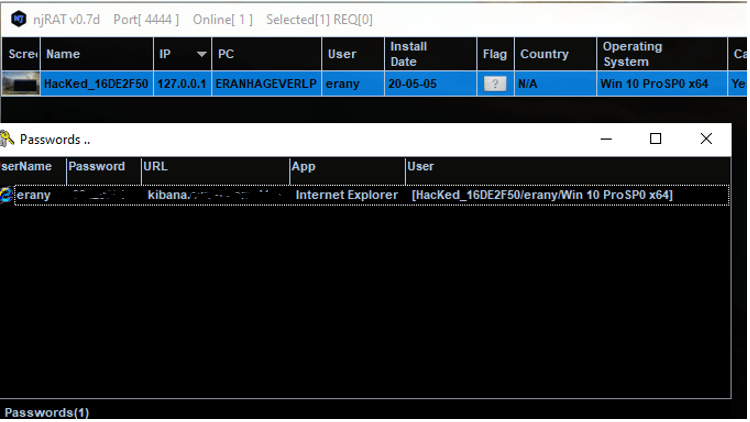
Credentials from Web Browsers
njRAT has a module that steals passwords saved in victim web browsers.
Custom Command and Control Protocol
njRAT communicates to the C2 server using a custom protocol over TCP.
Data Encoding
njRAT uses Base64 encoding for C2 traffic.
Data from Local System
njRAT can collect data from a local system.
Disabling Security Tools
njRAT has modified the Windows firewall to allow itself to communicate through the firewall.
File and Directory Discovery
njRAT can browse file systems using a file manager module.
File Deletion
njRAT is capable of deleting files on the victim
Input Capture
njRAT is capable of logging keystrokes.
Modify Registry
njRAT can create, delete, or modify a specified Registry key or value.
Peripheral Device Discovery
njRAT will attempt to detect if the victim system has a camera during the initial infection.
Registry Run Keys / Startup Folder
njRAT has added persistence via the Registry key HKCU\Software\Microsoft\CurrentVersion\Run\.
Remote Desktop Protocol
njRAT has a module for performing remote desktop access.
Remote File Copy
njRAT can upload and download files to and from the victim’s machine.[1]
Remote System Discovery
njRAT can identify remote hosts on connected networks.
Replication Through Removable Media
njRAT can be configured to spread via removable drives.
Screen Capture
njRAT can capture screenshots of the victim’s machines.
System Information Discovery
njRAT enumerates the victim’s operating system and computer name during the initial infection.
System Owner/User Discovery
njRAT enumerates the current user during the initial infection.
Uncommonly Used Port
njRAT has been observed communicating over uncommon TCP ports
Video Capture
njRAT can access the victim’s webcam.
We have uploaded the “server” file to VT:
njRAT on VT:
| File
SHA256 |
Server-aedb5b5a2dcb788f2474f929173151db8eb6d7489b00c85e7303755cfd7a59ef
njRAT- bf853789b938bdc5da8aaeb52511379a332c7cf238266a21bfcb0318a62e85cb |
To clean up an infected host, it crucial to revert each of the steps taken by the payload of the attack.
• Clean the Registry for any of the manipulated values.
• Delete Malicious Child’s instances from the memory.
• Block Network Traffic to any domain contacted throughout the attack.
• Use Cynet’s built-in remediation options to delete the file and prevent f it from spreading over the network.
• Use Cynet’s built-in remediation option to disconnect the HOST from the network.
• Investigate the incident according to the organization’s policy.
Related content:
Tips From the Expert
In my experience, here are tips that can help you better defend against njRAT (Bladabindi) and similar remote access trojans:
These advanced tactics will help reduce the risk of njRAT infections and improve detection capabilities within your organization.
The Cynet CyOps is available to clients for any issues 24/7, questions, or comments related to Cynet 360. For additional information, you may contact us directly at:
Search results for: