Achieved 100% protection in 2024
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
By: Ben Gold
In the last few months, the Cyber-security world witnessed several security flaws categorized as Critical Vulnerabilities in several Microsoft products. While it’s important to note that the discovery of vulnerabilities in Microsoft software is not something new, the past year was outside the norm. In 2020 alone,
a record-high number of 1,268 Microsoft vulnerabilities were discovered, a 48% increase from 2019.
In this case, however, we are discussing vulnerabilities considered critical and which were discovered in a short period. In this article, we’ll break down several recent Microsoft vulnerabilities in an attempt to simplify them.
This is part of an extensive series of guides about Network Attacks
Microsoft Exchange provides the back end to an integrated system for email, calendaring, tasks, and messaging. Mail servers always keep secrets and Exchange Server is maybe the most well-known mail solution for enterprises and governments over the world. Threat actors actively scan and exploit vulnerable Microsoft Exchange servers that have not applied the most updated security patches. The Exchange vulnerabilities lie in the Client Access Service (CAS), a protocol that is exposed to the public network for enabling users to access their email.
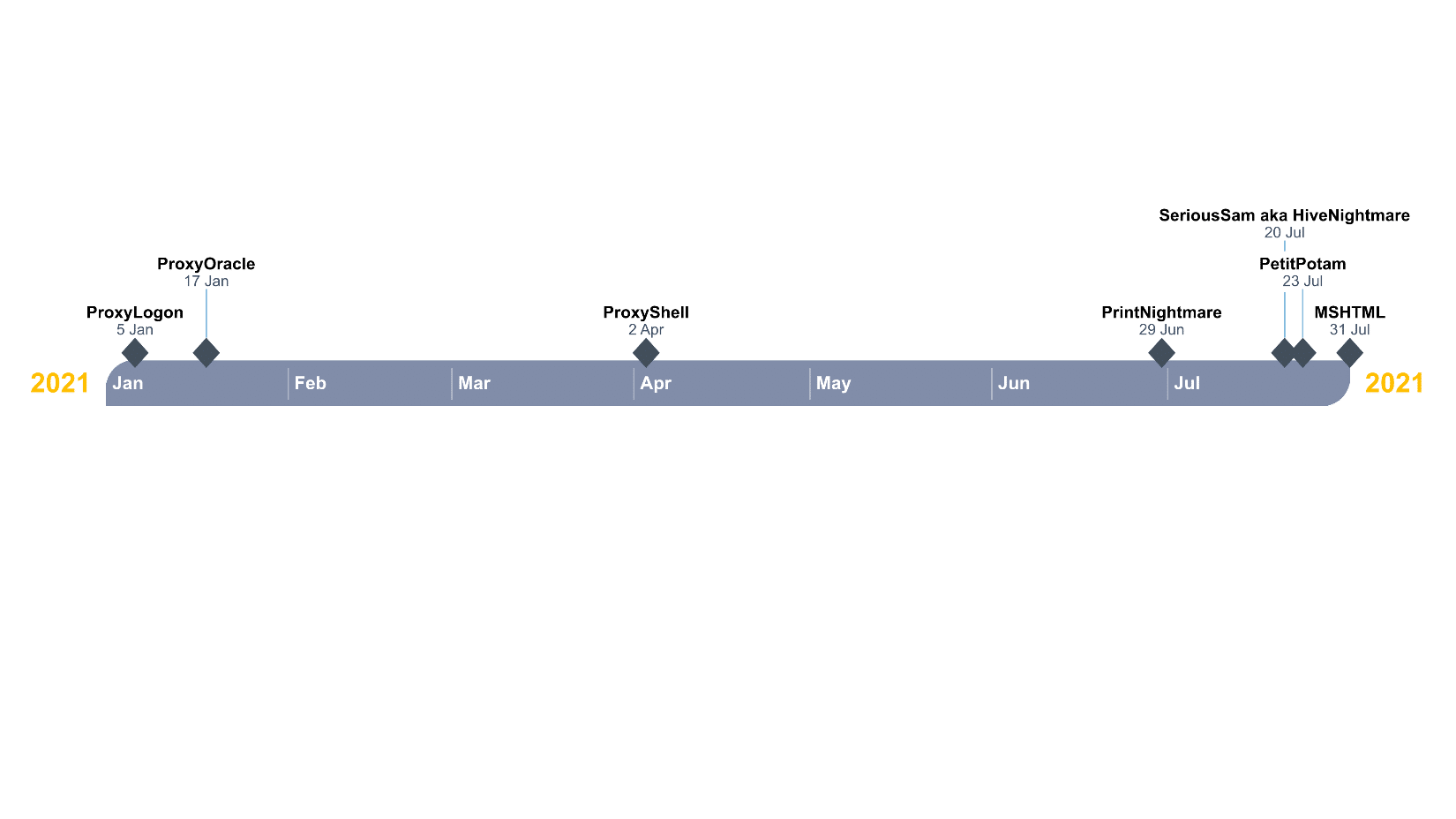
Proxylogon is perhaps the most well-known Exchange Server vulnerability in the world (due to its relation to HAFNIUM and China Chopper) as all on-premises Exchange Servers are vulnerable with just one exposed port.
The ProxyLogon vulnerability gives an unauthenticated threat actor the ability to execute remote arbitrary code on Microsoft Exchange Server through an exposed 443 port.
Though it might sound similar, it is not related to the ZeroLogon vulnerability. It Is called ProxyLogon because the bug exploits the Exchange Proxy Architecture and the Logon mechanism.
Essentially, this is a pre-authentication proxy vulnerability on Microsoft Exchange Server that allows an attacker to bypass the authentication, impersonating an admin and gaining code execution abilities.

ProxyOracle is an interesting Microsoft Exchange Server exploit with a different approach than ProxyLogon. By tricking a user to click malicious link, ProxyOracle allows a threat actor to steal the user’s password in plaintext format. Outlook Web Access (OWA) use form-based authentication to manage user logins. To keep a login state, FBA saves users’ credentials and passwords in their browser’s cookies. Each time a user visits the OWA, Exchange parses the cookies and uses the credentials to log in.
All the cookies are encrypted to ensure that even if a threat actor hijacks an HTTP request, they still would not be able to get your credentials in plaintext format. For that, malicious actors use Padding Oracle, which helps decrypt any user’s cookies.
The ProxyShell vulnerability exists on unpatched on-premises editions of Microsoft Exchange Server and isexploited actively on servers with access to the Internet. ProxyShell lies on the Client Access Service (CAS) which runs on port 443 (usually) on IIS (Microsoft webserver). The frontend (CAS) calculates the backend URL. When a Logon Request is created, Exchange normalizes the request URL and removes the mail address part before routing the request to the backend. Due to this Exchange vulnerability, we can erase part of the URL during the URL normalization and grant an access to an arbitrary backend URL. An unauthenticated threat actor can abuse this vulnerability to execute arbitrary commands on Microsoft Exchange Server simply using an exposed 443 port with Exchange PowerShell Remoting. This lets users send, read, and update mail configurations using the command line.
Print Spooler is a Windows feature which is enabled by default in all Windows editions. The Print Spooler temporarily stores print jobs on the memory of the system until the printer is ready.
From a security perspective, printers in general and Print Spooler in particular have been targeted for exploitation by threat actors for many years. Even the 2010 Stuxnet worm which was used against Iranian nuclear facilities exploited a vulnerability in the Print Spooler to escalate privileges and spread itself over the network. The same Print Spooler vulnerability reinvented itself in 2020 when researchers uncovered a new way to exploit it.
The PrintNightmare vulnerability takes advantage of a function call in the Print Spooler service that allows users to add dll files as printer drivers and later execute them via the SYSTEM.
On June 29, we discovered that the previous Print Spooler patch was insufficient, and even fully patched machines remain vulnerable. The original exploit was edited, making the patch only half effective. Print Spooler is designed to allow clients to update their printers remotely. However, a logic flaw in how it works allows any client to inject their own unsigned dll into the Print Spooler process while bypassing validation or authentication of the file.
The vulnerability occurs when Print Spooler performs privileged file operations improperly. A threat actor that successfully exploits this vulnerability can execute arbitrary code as SYSTEM. They could then install programs, manipulate data, and even create new users with full rights.
The Windows Registry centralizes the configuration database for Windows OS and for applications. The Registry stores information about configurations, parameters, and preferences. On disk, the Windows Registry is not one large file, but rather a set of different files called hives. As it includes the Windows Security Accounts Manager (SAM) database, as well as the SYSTEM and SECURITY hives, it is a popular target for attackers.
HiveNightmare, or SeriousSAM, allows threat actors to retrieve all registry hives in Windows 10 (released after 2018) and Windows 11 with a low-privileged user. It includes data in SAM, which can be used later to execute code as SYSTEM.
The vulnerability exists in the default Windows 10 and 11 configurations which grant all non-admin users to read files on key registry hives. This is an error, as the registry is supposed to be a protected database which can only be accessed by users with administrator privileges. This is because the database contains hashed credentials for every user on a machine. Once they have retrieved the credentials, threat actors use a method known as “pass the hash” which lets them authenticate a remove server with the hashed credentials instead of the plaintext password.
A threat actor who abuses this vulnerability and successfully authenticates to a machine can run arbitrary code with SYSTEM privileges. The attacker would then have full control, which means they can run commands, drop extra payload, spread itself over the network, create new accounts with full user rights, etc.
Microsoft Encrypting File System Remote Protocol (MS-EFSRPC) performs maintenance and management operations on encrypted data that is stored remotely and accessed over a network.
Active Directory Certificate Services (AD CS) is a server role that allows users to build a public key infrastructure (PKI) and provide public key cryptography, digital certificates, digital signature capabilities and other security functionality for their organization.
PetitPotam is a form of NTLM relay attacks that grants threat actors the ability to take over an Active Directory with Active Directory Certificate Services (AD CS) in use. Currently Domain Controllers and AD CS with the default configuration are vulnerable to this attack. It is important to mention that in this case, exploitation requires previous access to a victim’s machine. Instead of exploiting a specific vulnerability, PetitPotam exploits the authentication method in the MS-EFSRPC – a legitimate feature in Windows Server. Abusing this method, the victim Windows host is forced to authenticate against another host, relay NTLM credentials, and allow acquisition of an authentication certificate that can be used to request a Ticket Granting Ticket (TGT) which can lead to domain compromise and can be used by an attacker to elevate their privileges in a domain environment.
ActiveX controls are small program parts that are used to create and execute applications that work over the network via web browsers such as online Office applications. Moreover, applications use ActiveX to share data and functionality through web browsers. This ActiveX vulnerability and many more can be deployed through malicious Microsoft Office documents and are often used in spear-phishing campaigns.
The Microsoft MSHTML Vulnerability is a remote code execution vulnerability that allows an attacker to run arbitrary code on a victim’s machine via ActiveX control usually sent to the victim via spear-phishing.
Based on Microsoft MSHTML Vulnerability, an attacker can craft a malicious ActiveX control to be used by a Microsoft Office document that hosts the browser rendering engine. The attacker would then have to lure the user to open the malicious document. Once the user opens the document, the vulnerability is then exploited, and the attacker can execute arbitrary code. The new zero-day is a critical risk vulnerability in the Trident MSHTML rendering engine.
This exploit uses ActiveX controls and .cpl files and is a highly sophisticated attack. The malicious code is hidden in .cpl files which are used for control panel items but are actually similar to DLL files and can be executed.
Once code is executed, attackers can perform malicious activities such as running commands remotely, dropping extra payload, gaining persistence, etc.
The Cynet Research team are always deploying new detection rules designed to detect and prevent exploitation attempts of those vulnerabilities and additional detections to increase the visibility around it. The CyOps team monitors our customers’ environments 24/7 and will be in contact in case any indicators of those vulnerabilities are detected in their environment. Moreover, the CyOps team reaches all our customers for every vulnerability via external/internal communication. For every vulnerability, the CyOps team provides recommendations for protection and mitigation, along with a guide to mitigate via Cynet Console, Microsoft patching, and Indicators of Compromise if there are any.
Examples:
Cynet mitigation for PrintNightmare vulnerability via Cynet Console using Forensic Policy feature
Cynet mitigation for MSHTML vulnerability via Cynet Console using Custom Remediation feature
Cynet CyOps team is available for our clients 24/7 for any issues , questions or concerns related to Cynet360. For additional information, you may contact us directly at:
CyOps Mailbox – [email protected]
Israel +972 72-3369736
UK +44 2032 909051
US +1 (347) 474-0048
Search results for: