Achieved 100% protection in 2024
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
Written by: Eldar Azan
The COVID-19 pandemic has created a perfect opportunity for cyber-criminals to step up their attacks. Advanced Persistent Threat (APT) groups always seem to leverage crises – such as the pandemic – to create topical campaigns, such as using Coronavirus instructions and attachments to masquerade and hide malware.
These types of attacks have been used to target every type of institution, from banks and financial services providers to government institutions. Most commonly, these attacks use ransomware – including the recently popular Mespinoza, also known as Pysa due to the .pysa extension appended during encryption.
Mespinoza was first seen in the wild around October 2019, used by an unknown APT group. The purpose of the ransomware is to restrict user access to the private or business-critical files in the organization, encrypt these files, and spread the ransomware across the network to encrypt as many files related to the organization as possible.
The attackers demand payments from the victims to retrieve the files which were stolen or encrypted, usually using encrypted emails and the company’s website to contact the victims. Attackers also rely on Bitcoin as the payment method because of its ability to keep anonymous any identities during a transaction.
This is part of an extensive series of guides about Ransomware Protection
Mespinoza was first discovered in October 2019, but its first real large-scale campaign came a year later, in October 2020. Mespinoza (or Pysa) is associated with an unknown French APT group and was successfully deployed in an attack when the group claimed responsibility for a cyberattack on the East London Hackney Council – the local government authority for Borough of Hackney. The Council houses sensitive citizen information and is the billing authority for taxes.
According to security researchers, Mespinoza has successfully stolen important data such as passports, rent bills, crew data, and intelligence information on the security community. The data stolen in successful Mespinoza/Pysa attacks has been leaked on public-facing websites.
Mespinoza or Pysa holds a Python variant of the ransomware that can easily be executed using a Python interpreter.
Unlike other ransomware, Pysa does not delete shadow copies before encryption, which means that backups will provide a viable countermeasure to remediate the attack.
The file’s magic bytes indicate that the file is Portable Executable for Microsoft Windows.
Meta-Data
| MD5 | 83e1ca89bcd55a87f826bc6901ff7f3e |
| SHA-1 | d0db4d232331234f0c430008a4320c0dea993c20 |
| SHA-256 | 4dc802894c45ec4d119d002a7569be6c99a9bba732d0057364da9350f9d3659b |
| Vhash | 055076655d551d15556068z5dhz13z2fz |
| Authentihash | 06c5529542c2879ca08c10ba0daec99afd0a19723d5c3590c36f84d91e70b99b |
| Imphash | b5e8bd2552848bb7bf2f28228d014742 |
| Magic bytes | 4D 5A 90 00 03 00 00 |
| SSDEEP | 12288:HDMUibBYoo+OeO+OeNhBBhhBB7TRU+FR+q1mITXijBs0Fa:jMUiFTTRU+3+qAILOj |
| File size | 500.00 KB (512000 bytes) |
| File type | PE32 executable Win32 EXE |
Additional names:
| svchost.exe | Compiler.exe | sefsretg.exe | 17535.py | Magus3.exe | stgeryh.exe |
First, we verify that the file is an executable and not packed before dynamically analyzing it.
Next, we review the static strings and imports of the file that indicate where to look when dynamically executing:
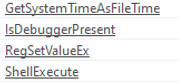
Mespinoza.exe spawns a command-line child process “ShellExecute”, as we suspected from the static analysis.
This command will execute the batch file.
Functionality and Behavior
Much like other ransomware variants, Mespinoza produces two separate lists.
The first list is the whitelist, or the exclude list. These paths will be excluded from the encryption process to allow the victim access to the payment process and the data decryption. The malware won’t encrypt crucial files for the operating system, but will focus on the important data saved on the endpoint.
Exclude:
The second list is the blacklist. This list contains extensions that the malware will target for encryption by adding to the original extension a .pysa extension with encryption. These files won’t be accessible to the user without the decryption key.
BlackList:
Found in the memory strings
Among the first files that the malware encrypts are the debugging tools that exist in the operating system, adding a .pysa extension. This technique can be used by the authors of ransomware to avoid analysis, thus extending the life of the ransomware attack.
The ransomware note usually contains instructions about payment information and consequences if the instructions are not followed.
In every path that the malware encrypts files, a “Readme” note is dropped to the same path.
The ransomware note contains instructions on how to decrypt the data along with email and domain contact details.
Sample Mespinoza or Pysa note:
The purpose of the persistency technique used by the malware is to ensure that the processes will remain able to communicate and that the attack will be completed even if it is interrupted (which means the malware will continue running in the backgrouond even after rebooting and logging back in). This technique could be implemented via known common methods such as Registry Keys, Schedule Task, DLLs Applications, Startup Folders, Process Injections, etc.
In this case, we are witnessing the persistence of the ransomware note.
Changing values on the following registry key using the API call “RegSetValueEx”
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
These registry keys are responsible for displaying messages during the Windows startup.
After rebooting the system we receive the following message:
The next step of the attack is to clean the malware’s tracks. Mespinoza creates a batch script file that is executed in the last phase of the attack.
The batch file is created in the following path:
“C:\Users\user\AppData\Local\Temp\update.bat”
Example of data leaked on a public-facing website is shown below.
Cynet 360 protects your environment against this type of attack by detecting and preventing it from executing its malicious activities on hosts where the Cynet agent is deployed.
Note that our environment action is set to alert only, so as not to interrupt the Mespinoza ransomware flow. This lets Cynet detect every step of the attack.
The attack flow is detected using several detection mechanisms:
Malicious binary – Cynet detects a file that is flagged as malicious in Cynet’s EPS (endpoint scanner) built-in threat intelligence database. This database contains only critical IOCs (such as IOCs of ransomware, hacking tools, etc.).
Attempt to Run – Cynet’s AV/AI engine detects a malicious file that was loaded into memory.
File Dumped on the Disk – Cynet’s AV/AI engine detects a malicious file that was dumped on the disk.
Memory Pattern – Cynet detects when a file is loaded into memory and runs unique memory strings associated with the malware.
Ransomware Heuristic – Cynet detects suspicious behavior which can be associated with Ransomware (such as changing file extensions to “.Lock”).
Additionally, in many cases we have observed a pattern where ransomware targets vssadmin.
Advanced Detection Technology – Cynet detects execution of a command related to vssadmin activity. Vssadmin can be used to delete all the backups on the hosts and can be related to ransomware activity.
(Not related to the sample investigation.)
Learn more in our detailed guide to ransomware prevention.
Learn more in our detailed guide to anti ransomware.
| Type | Indicator |
| Sha256 | 4dc802894c45ec4d119d002a7569be6c99a9bba732d0057364da9350f9d3659b 4770a0447ebc83a36e590da8d01ff4a418d58221c1f44d21f433aaf18fad5a996661b5d6c8692bd64d2922d7ce4641e5de86d70f5d8d10ab82e831a5d7005acb9986b6881fc1df8f119a6ed693a7858c606aed291b0b2f2b3d9ed866337bdbde4dc802894c45ec4d119d002a7569be6c99a9bba732d0057364da9350f9d3659be4287e9708a73ce6a9b7a3e7c72462b01f7cc3c595d972cf2984185ac1a3a4a8327934c4c11ba37f42a91e1b7b956d5a4511f918e63047a8c4aa081fd39de6d98b4b233e87c61c8698e086b376da640c9ab2ecd71c58b1f6a2eceb60b7e1a691f0939ebfda6b30a330a00c57497038a54da359e316e0d6e6e71871fd50fec16a1e2009549452ed6b524b94ed683079ee60c2b9542b1bfd5b9ee42e9161d5e7c848355bd2a57d92e017bdada911a4b31aa7225c0b12231c9cbda6717616abaea30f0014669bc10a7d87472cafc05301c66516857607b920ddeb3039f4cb8f0a50e9662b468135f758a9487a1be50159ef57f3050b753de2915763b4ed78839ead61bb42fe06b3511d512af33ef59baa295b29bd62eb4d0bf28639c7910a65e4ae 425945a93beb160f101d51de36363d1e7ebc45279987c3eaf5e7f183ed0a3776 a18c85399cd1ec3f1ec85cd66ff2e97a0dcf7ccb17ecf697a5376da8eda4d327 5510ae74b7e2a10fdafa577dc278612f7796b0252b7d1438615e26c49e1fc560 1a0ff707938a1399e23af000567806a87fff9b8789ae43badb4d28d4bef1fb81 b1381635c936e8de92cfa26938c80a359904c1d709ef11ee286ba875cfb7b330 |
| Dropped File | C:\Users\user\AppData\Local\Temp\update.bat |
| Domain | Wqmfzni2nvbbpk25.onion/ |
| Emails | [email protected] |
| Ransomware Note | Readme.txt |
| Registry Key | SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
legalnoticetext |
The Cynet CyOps team is available to clients 24×7 for any issues, questions, or comments related to Cynet 360. For additional information, you may contact us directly at:
CyOps Mailbox – [email protected]
CyOps Team Leader – [email protected]
CyOps Manager – [email protected]
Israel +972 72-3369736
UK +44 2032 909051
US +1 (347) 474-0048
Search results for: