Achieved 100% detection in 2023
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
Written by: Eldar Azan and Ronen Ahdut
RedLine stealer was first discovered in early 2020. It is a highly effective info-stealer that targets user’s credentials from installed apps, website browsers, and also information about the host itself(OS, CPU, Antivirus Software used, Etc).
It is offered for sale on telegram and underground forums as “Malware as a service” (MaaS), where the users pay the fee and gain access to the entire infrastructure and run their campaign, combined with support offered for users via a dedicated telegram channel, it is one of the most common info-stealers today.
Over the last month, the Cynet CTI team has engaged with the popular new info stealer called RedLine, In this article, we will cover the RedLine distribution methods, known and less known vectors, and present an overview of its evolution.
Samples of RedLine malware are been uploaded daily to MalwareBazaar(by abuse.ch)
Observing the statistics provided by ANY.RUN, RedLine is the most popular threat in the last month.
This is part of an extensive series of guides about Malware Protection
RedLine stealer logs for sale over XSS Telegram
While the infrastructure is offered for sale, the buyers are mostly responsible for their distribution method. RedLine mainly spreads via phishing emails luring victims to download its payload, but recently RedLine has been seen spreading via Youtube scam videos.
While showing content related to gaming, Bitcoin, or cracking software, a download link will be posted in the description of the supposed program. Users who click the link infect themselves with the stealer.
RedLine as MaaS uses a telegram channel to support their customers:
RedLine Telegram Channel
Here is an example of RedLine output leak data:
RedLine Output
Note that RedLine also reveals hardware and antivirus software data, which could assist attackers in the reconnaissance for a future attack.
Attackers could also search for enterprise emails, further expanding their reach without any action needed.
As mentioned above, RedLine uses a new method of camouflage for bitcoin software along with a false explanation video leading to a download link for RedLine malware:
The links mentioned in the Youtube video lead to a packed RedLine malware that is deployed on the victim’s endpoint:
Packed RedLine Stealer
On top of that RedLine malware is also capable of stealing stored passwords from popular web browsers such as Chrome and Edge.
Chromium-based browsers store encrypted passwords and yet RedLine can decrypt these passwords by impersonating the infected user, RedLine malware will also gather information about “blacklisted” sites which the user declines to save a password for them, this information can be very useful for the threat actors in future attacks.
RedLine logs were obtained by Bob Diachenko a security researcher who locate a server that contains over 6 million RedLine logs.
Some of the stolen data(441,657 logs) were shared with the “Have I Been Pwned” service:
In this case, we analyze the sample from the youtube scam video we mentioned above mapping the sample flow according to the Mitre Attack framework.
Initial access
Can be chosen by the attacker, Redline provides the panel and build maker.
The most common vector used is via phishing, but attackers get creative and upgrade their methods, as seen with the Youtube example given in the article.
Defense Evasion
Obfuscated Files or Information: Software Packing
Redline is known to use a packer to evade signature-based detections, and to harden the malware analysis procedure.
While users can use their desired packer, we have witnessed a high use of the VMProtect packer.
First, the RedLine packed version is a 32bit PE file that contains high entropy and packed sections:
Second, the unpacked version of RedLine is a 64bit PE file that contains high entropy and VMProtection:
Entropy is the measure of randomness in relation to the set of data, it is measured on a scale of 0-8.
The more random the data, the higher the entropy.
This generally suggests a packed file, one that will require a dynamic analysis.
Worth mentioning, high entropy and packed files exist in legitimate processes as well, But usually files with entropy higher than 7.2 are marked as suspicious and are probably packed/obfuscated.
VMProtect is a software that can assist to protect the developer’s code from being executed on a virtual machine which makes reverse engineering quite difficult because of the complicity to read the obfuscated data.
Impair Defenses: Disable or modify tools
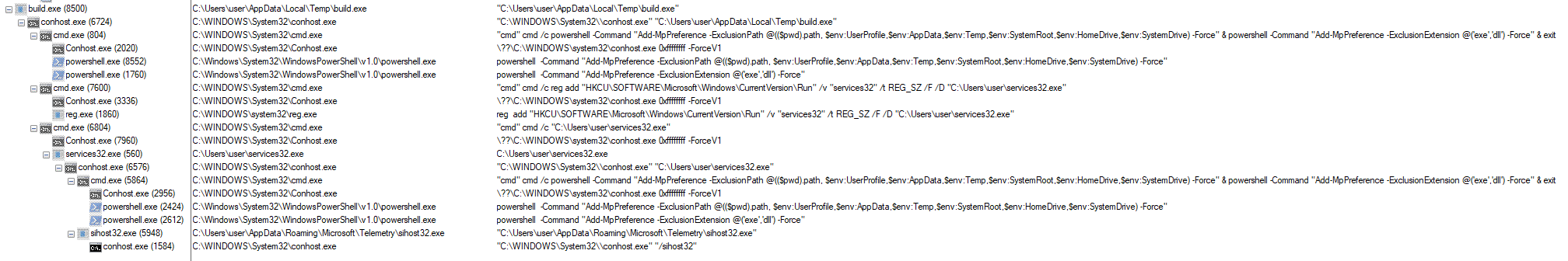
RedLine is using a known method to impair defenses adding directories for exclusions in the Windows Defender Anti Virus, by doing that these folders can be used to execute the malicious activity in addition another command is been executed for specific extensions every executable or DLL file that will be executed from those directories will be ignored by the AV:
Masquerading: Match Legitimate Name or Location
Legitimate names were observed using the names “sihost32.exe” and “services32.exe”:
This is done by the attackers for evading defenses and maintaining a low profile.
Persistence
The purpose of the persistency technique is used by the malware author to maintain the malware foothold on the endpoint and ensure lifeline in case of any interruptions during the execution flow and complete the task after reboot, etc…, This technique could be implemented via known common methods such as Registry Keys, Schedule Task, DLLs Applications, Startup Folders, Process Injections and more.
In this case, we are witnessing the persistence of the RedLine malware in two methods:
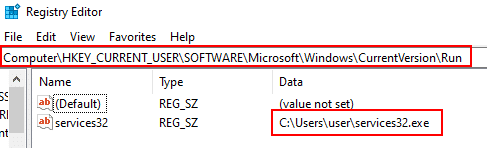
Adding the malware payload to the Run key.
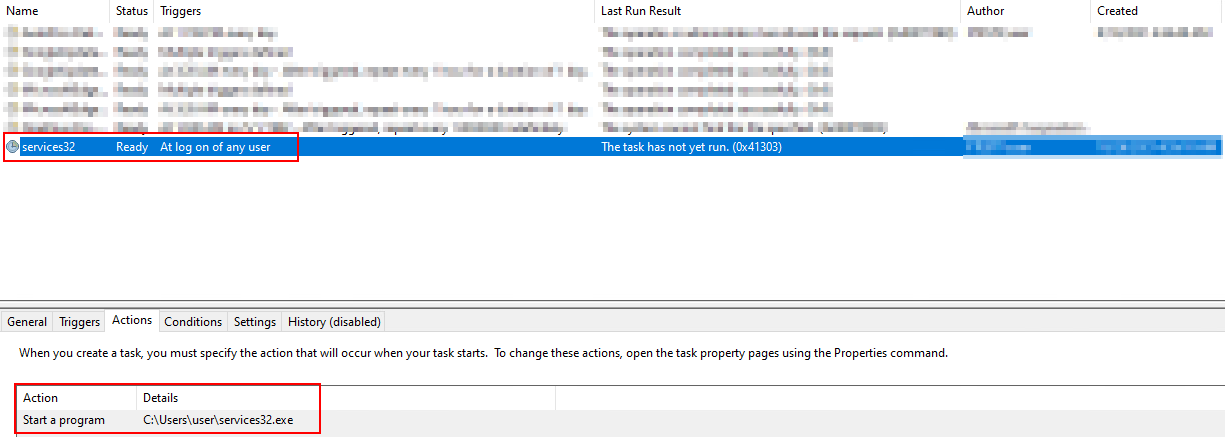
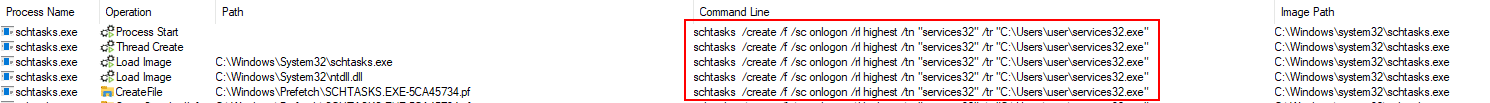
The CyOps team is working around the clock to enhance detections and design new ones by implementing IOCs, memory patterns SSDEEP, etc.
As you can see below we took a sample of RedLine and executed it in our labs.
Note that our environment action is set to alert only, so as not to interrupt the stealer flow.
This lets Cynet detect every step of the attack.
File Dumped on the Disk – Cynet’s AV/AI engine detects a malicious file that was dumped on the disk:
Process Monitoring CyAlert Heuristic Activity – Suspicious Conhost Process
Process Monitoring CyAlert Heuristic Activity – Reg Add Run Key Persistence
RedLine telemetry data by Cynet360
Besides the Cynet360 detection mechanism, Cynet360 offers a File Monitor feature that can collect forensic data and monitor files within the system.
Persistency registry key added through command-line utility:
PowerShell execution commands to impair defenses:
As mentioned earlier, Redline offers high availability for anyone who is willing to pay for it, with a support bot on telegram and a vast network of users, Redline is one of the most common MaaS available.
Cracked versions started also to appear online, this has strengthened Redline’s usage by non-paying users as well, with the option of running the malware without the need to pay for it- resulting in a higher than already Redline user.
To better understand Redline, we wanted to try it ourselves.
We were able to retrieve a cracked version of the infamous stealer from an underground forum:
With it, we can get a better understanding of how it behaves, its features, and its effectiveness.
The cracked version offers a glimpse into Redline’s Panel from the attacker’s point of view, after successfully installing and executing it, we are greeted with the following :
Redline’s operator panel:
As seen above, Redline offers more than just information theft, browsing the different modules we can see :
Loader tasks:
We can see that the loader module offers more advanced post-infection capabilities such as:
Redline comes with an informative guide both in English and Russian, in it we can see RunPE’s capabilities:
The user guide also provides examples for each loader capability, RunPE’s example:
Apart from simply downloading and running a file on an infected host, Redline offers process injection capabilities, making it much more than just a stealer.
The Builder module allows the attacker to make desired builds of the malware:
According to the guide, users can make different builds for different targets, this way they can better differentiate the output from each infected host/group.
Settings:
Under the setting section, users can choose which stealer modules will be active, as well as supply desired files and domains that are targeted:
Loader Tasks Dive
As mentioned above Redline is offering more tasks options that can be modified before the creation of the builder.
Open link
One of the tasks that Redline offer is to deploy any site on the victim endpoint, this task will launch the site by the builder:
As expected when the builder is executed the site is opened by the default web browser on the machine:
This capability can be used for credentials theft or to perform other malicious content.
Command Line
One of the most powerful tasks the Redline control panel has is the command-line utility which can be used for Remote Code Execution(RCE) which can be configured easily by these steps:
As excepted once the builder executes we received an output:
Redline has evolved from “just” a stealer, into a fully capable botnet.
Its characteristics, price, availability online, online\offline(detailed FAQ readme file) support, has made Redline the number one stealer currently active.
Unlike large threat actors who usually don’t share their tools, Redline is available to everyone willing to pay( or find the cracked version), this gives enormous power to the users.
Some Redline users have a habit of sharing the most recent logs on underground forums, attackers can use those logs to infiltrate networks using the compromised credentials.
All of the mentioned above makes Redline shine in the threat landscape, and due to the analysis presented above, Redline steps up and earns its place next to the top threats In todays threat landscape.
Search results for: